Last Updated on April 7, 2022 by rudyooms
In one of my last blogs, I showed how you can set up multiple App protection profiles to make sure your managed and unmanaged IOS devices could receive the correct app protection policy.
In my opinion, you need to make sure you lower the security bar for the Managed/MDM Enrolled devices by changing the App Protection policies. You really don’t want well-behaved employees who enrolled their own devices, become angry about the security barriers, and find another way to share the data.
I updated this whole blog because I noticed some settings were not clear to everyone (even me!) so here we go
I will divide this blog into multiple parts
- What could happen?
- What’s the cause?
- What options do we have?
- Policy Managed Apps with OS sharing
- Policy Managed Apps with Open-In/Share filtering
- Configure Restricted Apps
- Some side notes when using the OS sharing policy
1. What could happen?
Here is a very good example of what could happen when you did not lower the bar:
One of the employees has their IOS mobile device enrolled into Intune and of course, the App protection policies were applied. After a few days, he receives an email to make a simple payment. He opens the link in Microsoft Edge policy managed app to start making the payment. Normally the user could click on “Pay” to open the Rabobank payment app which was already installed on the device.
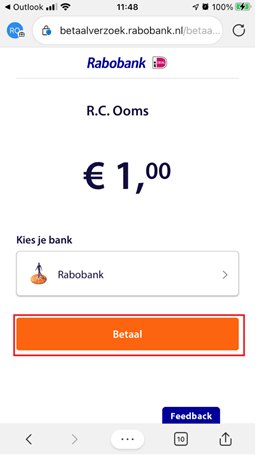
But now, after the device was enrolled and received the app protection policy, the pay now button was not opening the Rabobank app any longer. So what’s happening
2. What’s the Cause?
This is all because you made sure it was not possible to send data to other apps except policy-managed apps.
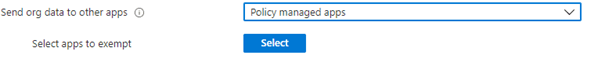
When you configured this option, you can only transfer data to any other policy-managed app. Please beware (this was my pitfall) that you could still send data to an unmanaged app, but the data will be encrypted and unreadable by the unmanaged app.
The public app must be targeted with an app protection policy. You probably can guess it, the Rabobank app can’t be targeted. As this app doesn’t support the core App Protection Policy settings
Supported Microsoft Intune apps | Microsoft Docs
3. What Options do we have?
So what options do we have, are we going to exempt apps?
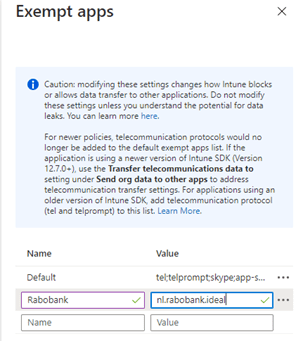
Maybe changing the setting to all apps but changing it to all apps? Changing it to “All Apps” is not secure at all!
Or should we choose a happy medium? With this option, we are going to make sure MDM-enrolled devices can transfer data to managed apps and protected apps.
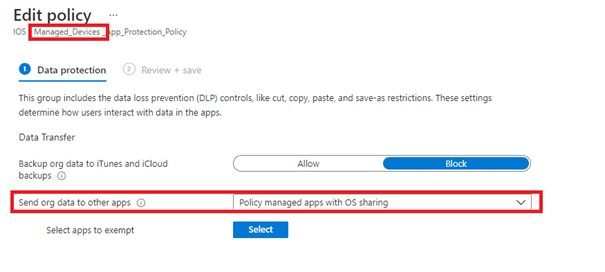
Let’s take a very good look at this policy.
4.Policy Managed Apps with OS Sharing
Policy Managed apps with OS Sharing are designed to be used for managed/enrolled devices. It makes sure you can send corporate data to both protected apps and also allows file transfers to apps that are managed by Intune. When you add the IOS app and make sure the IOS app is assigned as required or made available, the app will be managed by Intune.
But please make sure you have read this part before continuing
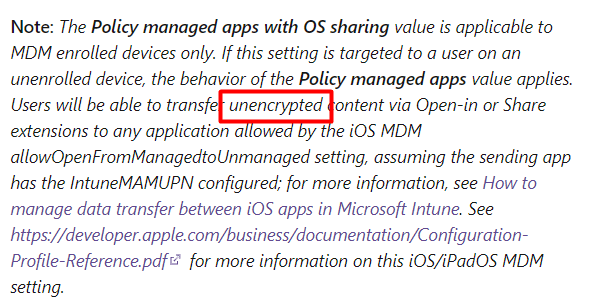
Unencrypted!!! When you did not read the MS docs (like I did in the beginning…) you might believe when you configured “Encryption” to “Require” you are good to go.
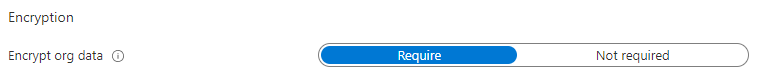
(Please make sure you always configure this option!)
Think again. So resume when using MDM enrolled devices and you configured the IntuneMAMUPN key your data will be sent to other apps, unencrypted!! Luckily when using BYOD devices, the device would receive that same policy but will revert back to “Policy Managed apps” and will make sure the data is encrypted.
You can check it out for yourself when you have a BYOD device, by sending org data to Dropbox and try to open it with notepad.
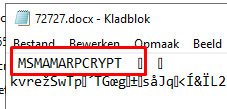
Intune will encrypt the data before it exits the app and the document will have a nice new header: MSMAMARPCRYPT
So when using “Policy Managed Apps with OS sharing” on MDM enrolled devices, please make sure you secure your MDM enrolled devices.
5. Policy managed apps with Open-In/Share filtering
I guess I am still not done, as we still need to take a look at some other App protection options. Now we have learned that when using the Policy Managed App Protection policy you could still send the ORG data to other apps (even when it’s unreadable/encrypted)
So if we want to make sure your users could only see the Policy Managed apps we talk about earlier, we need to choose the “Policy Managed apps with Open-In/Share filtering” This will make sure the data is encrypted and can be transferred to other MDM managed apps.
6. Configure the Restricted Apps
Okay so we are making sure the security bar is somehow lowered… but now we need to make sure Dropbox or Whatsapp is not going to work on your MDM-enrolled devices. Of course, you could lock down the App store on supervised devices but I am going to show you 2 other options you have.
1. Using a Compliance Policy
When you want to make sure your MDM enrolled devices are safe, you could create a compliance policy to make sure your devices aren’t compliant anymore when Dropbox is installed. A quick howto:
- Open the App store website on a Windows device and search for the dropbox app. Copy the Id after the app name

- Copy paste the id into: https://itunes.apple.com/lookup?id=’idyoucopiedinstep1′
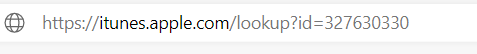
- Open the text file and search for “bundleid”. Copy the next after the:

*Create a compliance policy and add the “Bundleid” to the restricted apps part
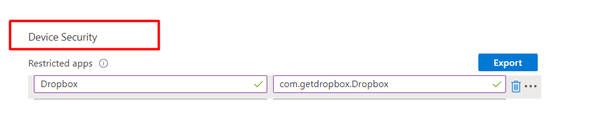
When you have added the restricted apps, please do not forgot to configure the “actions for noncompliance” because you do want the device to be noncompliant immediately after a restricted app has been installed
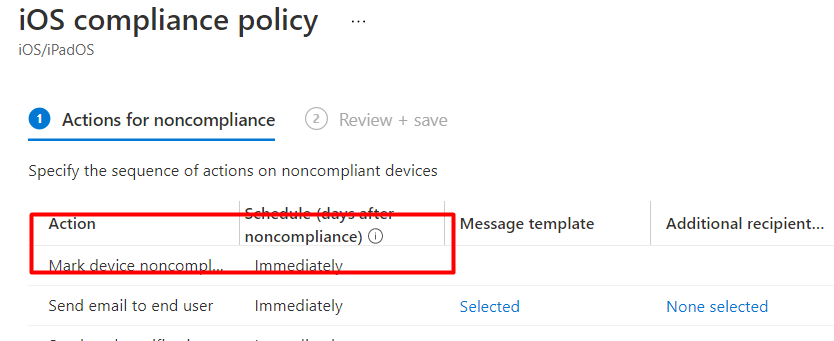
Of course, you will need to have a conditional access rule to enforce devices to be compliant. So if this app gets installed, the device isn’t compliant anymore and loses access to the data
2. Using Defender ATP and MCAS (My favorite one!)
You will need to have MCAS and Defender ATP implemented and deployed to your IOS devices! I am not going to show you those steps… only how to block it. First we need to open MCAS and make sure we have enabled the “Microsoft Defender for Endpoint Integration”
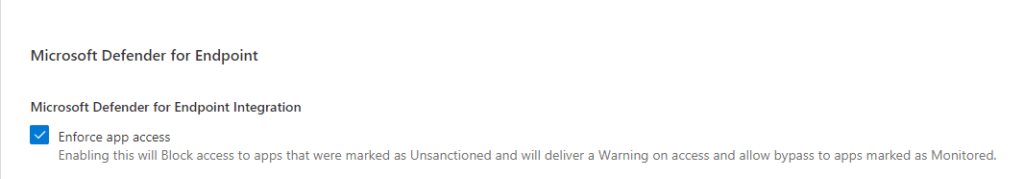
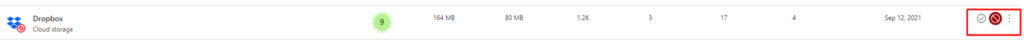
Now let’s search for the dropbox app and “unsanctioned” it! like I show below
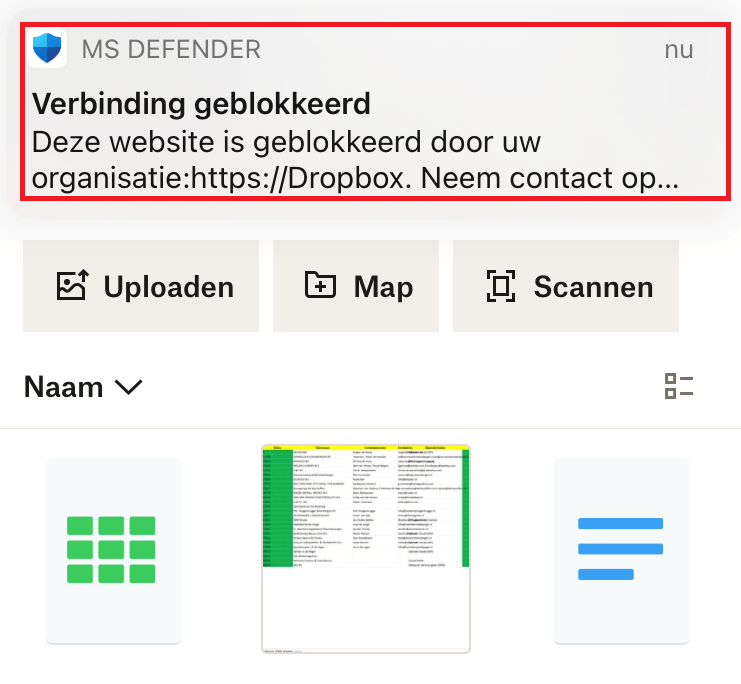
Now let’s take a look at what happens on your mobile phone… It will be blocked as it should!
7. Some side notes when using the OS sharing policy
After some tests with the OS sharing App protection policy, we noticed when the App was already installed on the device sometimes the end-user needed to open the company portal and needed to click on “install” (we also configured the app as available) otherwise the app would not show up in the management profile and app protection would still block it.
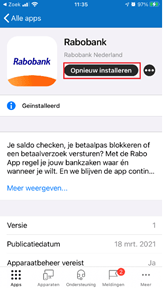
You can check which apps are managed by Intune on a device by going to Settings > General > Device Management > Select Management Profile > Apps.
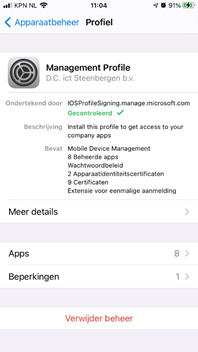

As shown above, we made sure we installed the Rabobank app from the company portal and after a while, it shows up in the management profile and we could finally pay the bill.
Conclusion:
- MDM Enrolled IOS? please use Policy Managed App’s or Open-In/Share Filtering to make sure your data is encrypted and safe, otherwise please make sure you have configured other protection methods
- Please always require encryption!

Lowering the security bar for your enrolled devices could create a better user experience and will make sure your users are happy and there will be no shadow it. But like I showed you earlier… your data Is unencrypted, so please only use this option when it’s necessary. If you don’t need it please make sure you configure it to Policy managed apps with Open-In/Share filtering

Hello there. Great article as always.
Section 4 solved it for our managed devices. But we have alot of unmanaged devices with policy managed apps. Is it possible to do this with unmanaged devices?