Last Updated on March 11, 2022 by rudyooms
This time a simple blog, about WPA, not to be mixed up with Wifi Protected Acces. I will be talking about the Windows Performance Analyzer (WPA) and how you could use it to get some insights into (as an example) Autopilot Self-Deploying mode.
I will divide this blog into multiple parts
- How to download WPA and how to use it
- Configuring logging on the client
- Starting /Stopping Logging
- Opening the WPR file in WPA
1.How to Download WPA and how to use it
When you need to deep dive into a problem it could really help you when you understand the whole flow of it. I did the same with Autopilot and using WPA was part of it.
https://call4cloud.nl/category/attestation-and-compliance-series/
And this blog below was kinda the start of it all, so please make sure you also read this one!
So when you want to get some more information and logging, Event Tracing will come knocking on the door. When using Event Tracing for Windows (ETW) you are enabling kernel or application event logging. But logging it one, but we still need to make sure we can read it!
Luckily these specified events can be exported to a nice ETL (Event tracing Log) so you could make sure you have every in place to start some troubleshooting.
So please download the tool first
https://go.microsoft.com/fwlink/p/?LinkId=526740
But before we can use the WPA tool, we need to have the ETL file… otherwise we have a nice tool without data. How are we going to facilitate this?
With the use of the Windows Performance Recorder (WPR) tool! This tool extends the Event tracing for Windows it talked about earlier. When we are using the WPR tool we can enable the recording of the events and export them to a nice ETL file
2. Configuring logging on the client
Like I showed in the first part, we need to make sure we enable logging on the client with the use of the WPR tool. So how are we going to do this?
I will show you how to do this when you want to troubleshoot the autopilot flow. So to do this, just open a nice new system cmd when you are almost ready to go to start provisioning the device (shift + f10)
Now we need to start the recording. So let’s start recording… right? You can do so by entering this command: wpr -start filename.wprp
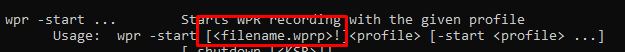
Looking at the screenshot above, when we want to start recording we need to select the wprp file. The wprp file is a Windows Performance Recorder Profile. In this XML profile, we can define what we want to record.
So first take a look at how we could build it.
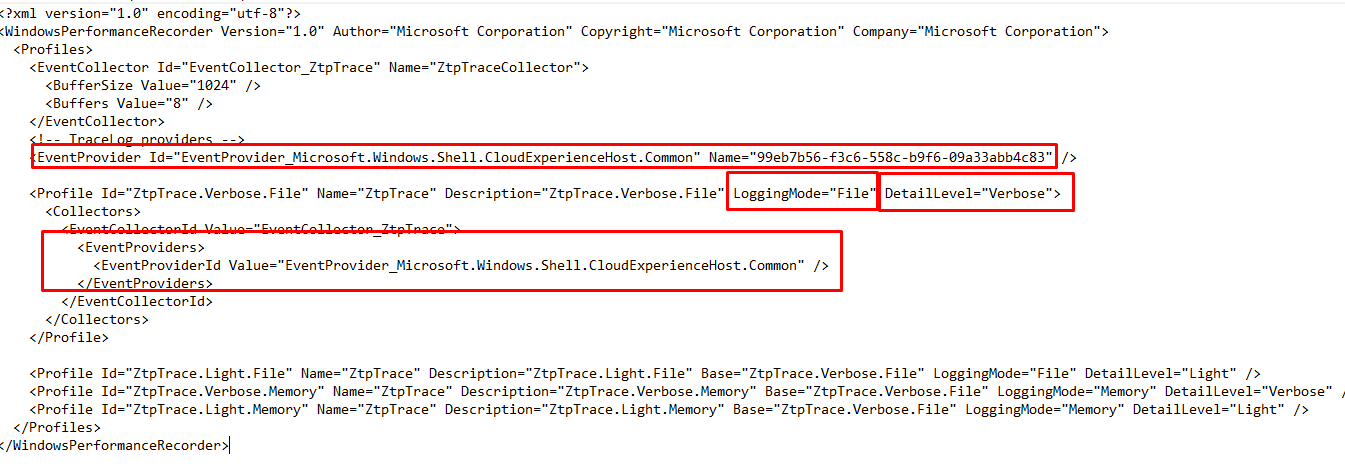
Looking at the above picture we need to define some settings, like the logging mode, the DetailLevel (Verbose… because we want to see everything). But we also need to define the profile itself and in it, we need to define the EventProviders and the ProviderID we want to use.
So let’s check them out, should we? Open PowerShell and fire up this command
$EventSession = [System.Diagnostics.Eventing.Reader.EventLogSession]::GlobalSession;
$EventProviderNames = $EventSession.GetProviderNames();
$EventProviderNames;
But what should we configure when we want to record the autopilot flow? Where to find them? When I am looking at these event providers I am missing a lot …. And I mean a lot!
Because when troubleshooting Autopilot you need to enable some nice EventProviders like Microsoft.Windows.Shell.CloudExperienceHost.Common or Microsoft.Windows.Shell.CloudDomainJoin.Client to get some good logging. But again… they are missing in the list I got back with the use of PowerShell
So if we don’t get them back with PowerShell I will give them to you!
<EventProvider Id="EventProvider_Microsoft.Windows.Shell.CloudExperienceHost.Common" Name="99eb7b56-f3c6-558c-b9f6-09a33abb4c83" />
<EventProvider Id="EventProvider-Microsoft.Windows.Shell.CloudExperienceHost" Name="d0034f5e-3686-5a74-dc48-5a22dd4f3d5b" />
<EventProvider Id="EventProvider-Microsoft.Windows.Shell.CloudDomainJoin.Client" Name="AA02D1A4-72D8-5F50-D425-7402EA09253A" />
<EventProvider Id="EventProvider-Microsoft-Windows-AAD" Name="4DE9BC9C-B27A-43C9-8994-0915F1A5E24F" />
<EventProvider Id="EventProvider-Microsoft-Windows-User Device Registration" Name="23B8D46B-67DD-40A3-B636-D43E50552C6D" />
<EventProvider Id="EventProvider-Microsoft.Windows.DeviceManagement.CertificateStore" Name="4f50731a-89cf-4782-b3e0-dce8c90476ba" />
<EventProvider Id="EventProvider-Microsoft.Windows.Shell.AADJCSP" Name="724a3824-7387-449a-825e-b135f2ca4c57" />
<EventProvider Id="EventProvider-Microsoft.AAD.AuthHelper" Name="146273bc-a4bd-4565-ab02-63eb97a7eb20" />
<EventProvider Id="EventProvider-Microsoft.AAD.CloudAp.Provider" Name="74d91ec4-4680-40d2-a213-45e2d2b95f50" />
<EventProvider Id="EventProvider-Microsoft.AAD.BrowserCore.Provider" Name="e552c41-40cd-4877-9b60-f243f9a855ab" />
<EventProvider Id="EventProvider-Microsoft.AAD.TokenBrokerPlugin.Provider" Name="bfed9100-35d7-45d4-bfea-6c1d341d4c6b" />
<EventProvider Id="EventProvider-Microsoft.AAD.WamExtension" Name="7b1ae42d-b4f2-414d-9c97-913f19049964" />
<EventProvider Id="EventProvider-Microsoft.Tpm.ProvisioningTask" Name="470baa67-2d7f-4c9c-8bf4-b1b3226f7b17"" />
<EventProvider Id="EventProvider-Microsoft.Tpm.HealthAttestationCSP" Name="a935c211-645a-5f5a-4527-778da45bbba5" />
<EventProvider Id="EventProvider-Microsoft.Tpm.DebugTracing" Name="3a8d6942-b034-48e2-b314-f69c2b4655a3" />
<EventProvider Id="EventProvider-Microsoft.CAndE.ADFabric.CDJ" Name="acc49822-f0b2-49ff-bff2-1092384822b6" />
Okay… so now we have the WPA tool installed, we know about the WPR tool, we know about the fact we need to define a wprp file to do so and which EventProviders we need. So take a look at the wprp file
https://call4cloud.nl/wp-content/uploads/2021/11/autopilot.zip
3. Starting /Stopping Logging
Okay, let’s sum it up.
*We have the WPA tool
*We have the Wprp file
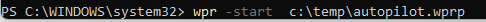
I guess it’s now time to start doing some logging. That’s just plain easy, just use this command to start recording
wpr -start c:\temp\autopilot.wprp
If you are done and you received the nice green screen after the white glove, you can use this command to stop recording and export the output to a nice log file! Please don’t forget this step, otherwise, you will miss the ETL file
Wpr -stop c:\temp\autopilot.etl
4.Opening the ETL file in WPA
Now we have the so much needed ETL file, let’s fire up WPA and open the ETL file, start with double-clicking on the “generic events” so you will end up with this screen
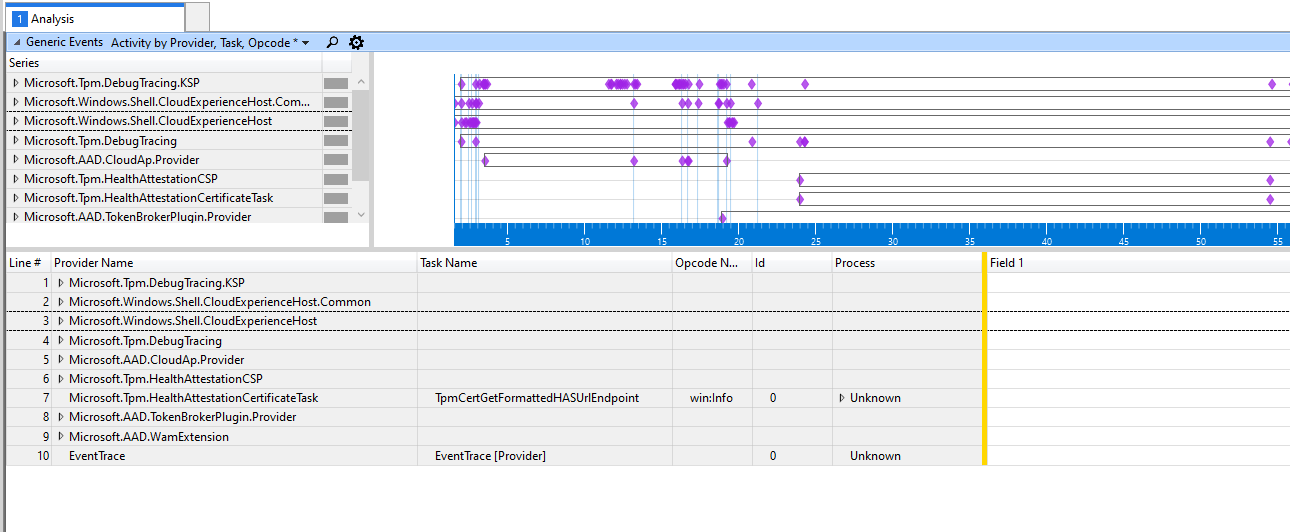
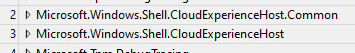
The most important ones to check out would be these 2
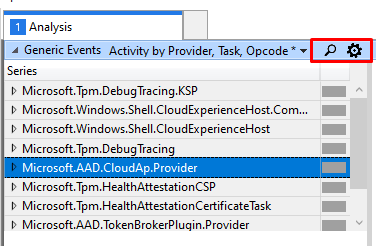
If you want to be sure you are not missing stuff, please click on this settings button first
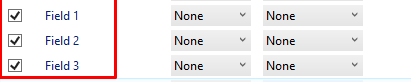
And make sure you enable those 3 fields
Now expand some Provider Names and take a look at the task names inside of them
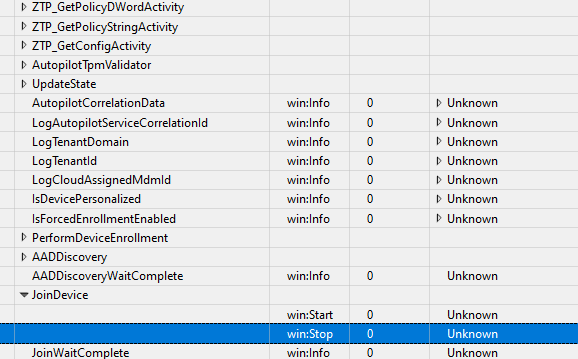
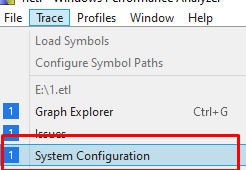
If you want to calculate the time when something happened you can check the exact start time of the log file by clicking on the system configuration button
Conclusion:
Knowing how to troubleshoot a device could come in handy when you run into weird issues.. of course, you could also use it when you are just curious about how some stuff works! Now let’s check it out for yourself!

