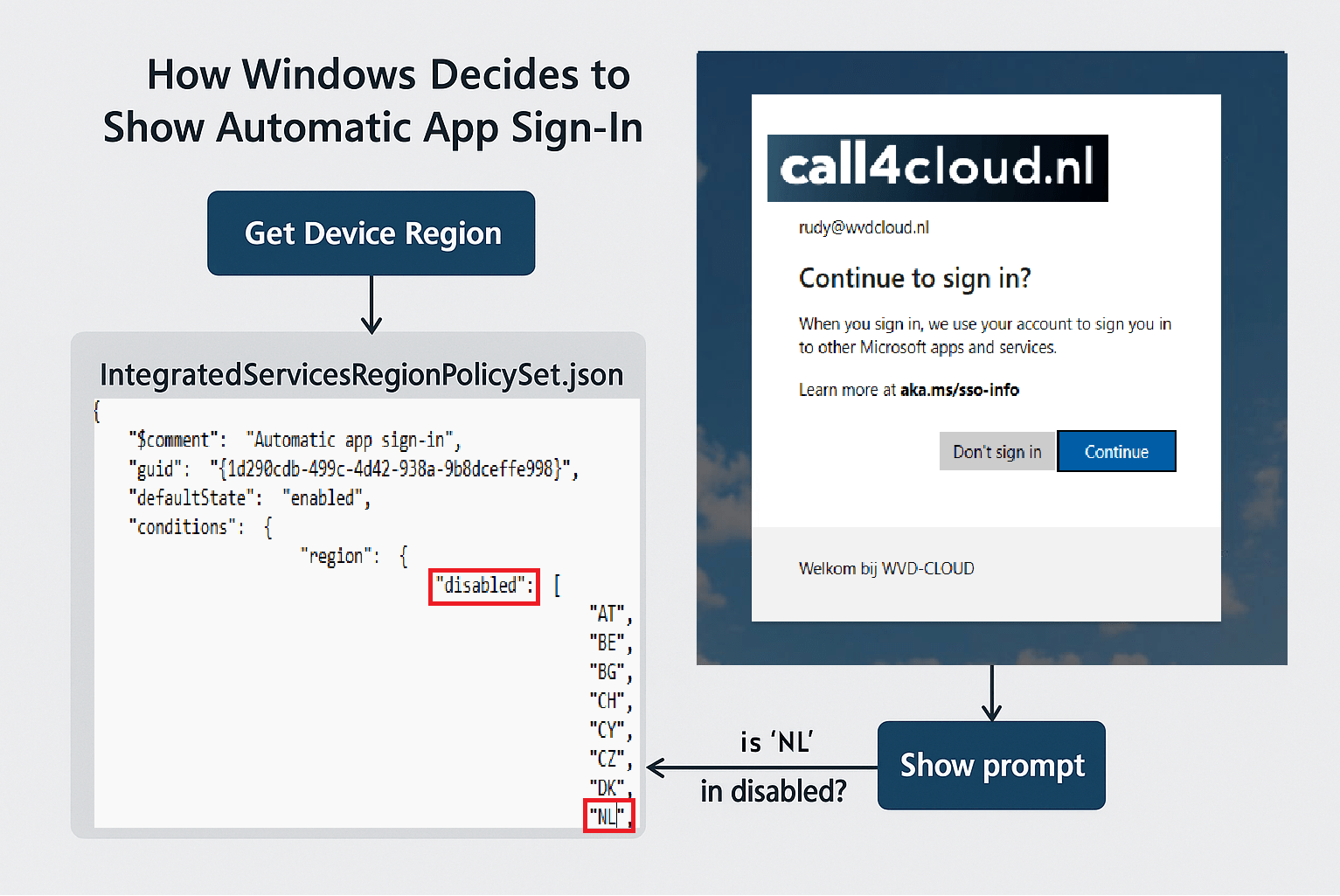
In this blog, we will examine how a recent big Windows change was introduced to meet Digital Markets Act (DMA SSO Compliance) requirements. This change forced devices into a stricter Device SSO authentication flow. As a result, many users were unexpectedly prompted with a Continue to sign in screen instead of experiencing silent single sign-on.
The “Continue to Sign in Prompt” That breaks the SSO
In this blog, we will examine why Windows shows the “Continue to sign in?” prompt when launching apps like Edge or Company Portal for the first time
Declarative Device Management with Intune
How Microsoft / Intune is shifting to Declarative Device Management (DDM) by using the declared configuration service
Why Using a DEM Account for Windows Autopilot is a Bad Idea
In this blog (not technical this time…sorry), we’ll explore why Microsoft does NOT support Device Enrollment Manager (DEM) for Autopilot, the problems it causes, and the better alternatives to use […]
Device Query for Multiple Devices, Device Inventory, and Single Device Query: Connecting the Dots
If you’ve ever tried troubleshooting a single device, you know how useful tools like Single Device Query can be pretty helpful. It’s fast, accurate, and gives you the live(near real-time) […]
The ShadowAdminPairs: A Deep Dive into Administrator Protection
Learn how the Administrator Protection feature in Windows 11 uses the ShadowAdminPairs key to map ENTRA user SIDs to local admins
Dual Enrollment / MMP-C Light for Workplace Joined Devices?
Explore WorkplaceJoin_DualEnrollment, dual enrollment for Workplace Join devices, and the role of MMP-C Light in shifting Intune policies
Kung Fu MMP-C Onboarding
This blog will show how I onboarded multiple Microsoft 365 Tenants to the new MMP-C infrastructure (Microsoft Management Platform – Cloud) and explain why this is going to be huge! […]
MDM / Intune policies moving over to MMP-C
This blog will focus on how Wi-Fi and VPN resource access policies are being transferred (Authority change) from the old-school MDM stack to the MMP-C Infra (MDM to MMP-C),
Troubleshooting the Properties Catalog Error 2147749902:
Troubleshooting error 2147749902 (WBEM_E_INVALID_NAMESPACE) isn’t always straightforward. What started as a simple Intune error turned into a Device Inventory deep dive involving an empty SQLite database, a failing Device Inventory […]