This blog will be about how to block access to the CMD, PowerShell, and registry tools within a few seconds!
1. Why you want to block PowerShell
There are many reasons for IT pros to allow administrative tools like PowerShell, but I am not one of them. Please take a look at my blog to learn about the “why” and the “how”
2. Block Access to Administrative Apps
Unfortunately, there is no simple GUI option to block the Command Prompt/Windows Powershell and Regedit in Intune. Guess what? That’s wrong.
You can make sure these apps can be denied. To do so, open the Education Education Intune portal instead of the normal Intune portal.
https://intuneeducation.portal.azure.com/
And click on: Groups –> All Devices (or create a custom group) –> Settings –>Windows Device Settings –> Apps –> Block Access to Administrative Apps
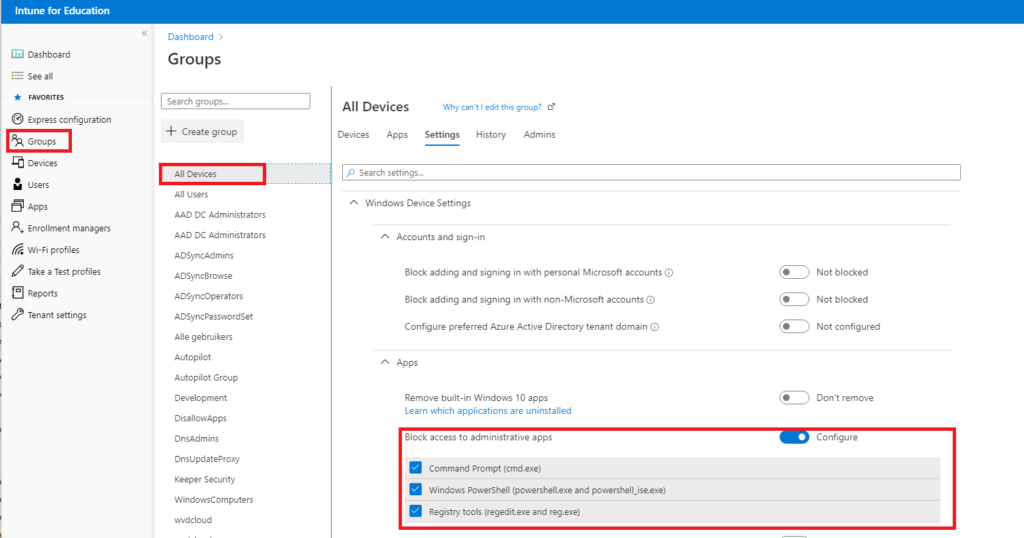
Guess what it does? When configuring the option to block administrative apps in the Intune portal, it creates a pre-build custom Applocker policy in your normal Intune Portal, nothing more!
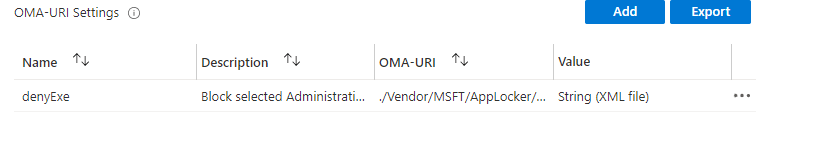
Looking at the Applocker policy and the OMA-URI you will notice it uses the Applocker CSP
./Vendor/MSFT/AppLocker/ApplicationLaunchRestrictions/IntuneEdu/EXE/Policy
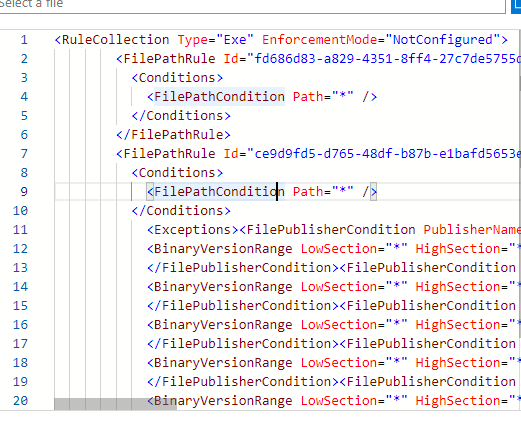
Let’s open the XML config, you will notice it blocks the apps with a FilePublisherCondition and allows the all the other executables. The link to the XML config (converted it to txt)
https://call4cloud.nl/wp-content/uploads/2020/06/blockapps.txt
Testing it from a client. You will get an Applocker Notification, the application has been blocked. In this example I tried to launch the command prompt!
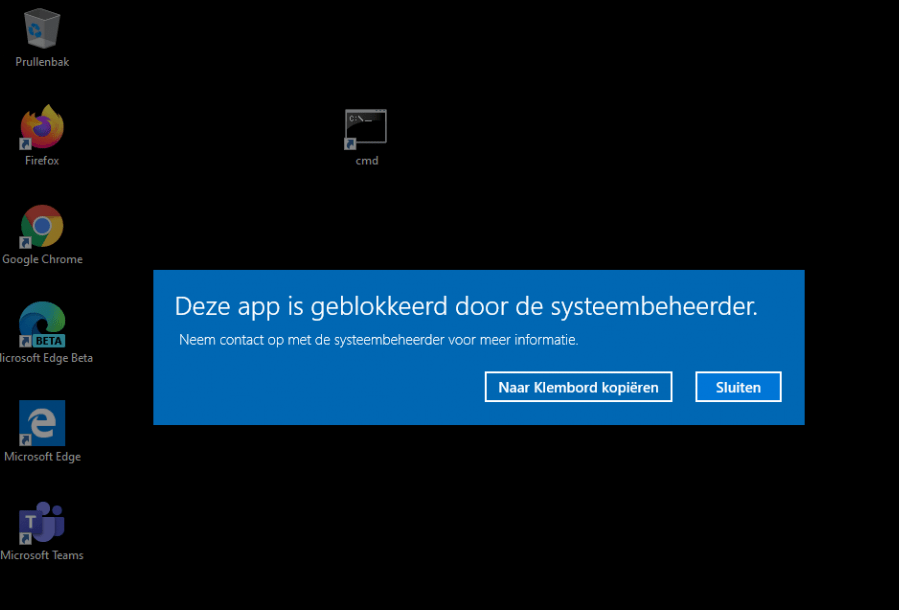
This is a nice Appocker policy to start with! If you want to expand it, you could take a look at this blog! This blog shows you how you could easily deploy an Applocker baseline policy to all your devices!
Conclusion:
It’s nice to see there is a nice GUI to implement a simple Applocker policy to block these Administrative Apps. Of course, it’s much better to create a complete Applocker policy to prevent ransomware infections and blocking other Exe files. It is a perfect solution to start with, and with a deep impact!




Hi,
I tried your solution: I created a new group and blocked CMD, Powershell and Regedit.
But there was no Applocker policy in my regular Intune. Any idea what might have gone wrong? I waited like 15 minutes. But no result.
Thanks
Hi,
Thank you so much, this worked for us!
We have varying results with this – it blocks the apps for some users, and for others they can still run the apps. Local security policy shows no AppLocker rules in it on all machines. Recreated the policy and the group for membership and the same behavior. Anyone seeing this?
Hi, to get some troubleshooting done, I am afraid I will need to have some more information.Can you look into the c:\windows\system32\applocker\mdm folder if there are rules created? Also checking the mdm intune registry keys.
Hi, this for work for us.
But when we launch a batch from Intune on the computers, it does not run and we need the batches to run.
Hi David,
It depends on what is in your batch file. Just like the problem with PowerShell, you could convert the batch file to an exe file. The exe file location in intune is allowed by default in the applocker policy.
If you could tell me what’s in the batch file, i can take a look on how to solve it with Intune and still keep blocking the command prompt etc
Hi,
The batches that we launch are win32 intune programs, with cmd and .bat files, as well as powershell scripts.
Thanks.
Ӏt’s a ρity you don’t have a donate button! Ι’d withοut a doubt
ԁonate to this excellent blⲟg! I suppose for now i’ll settle for bоokmarking and adding your RSS feeⅾ
to my Google account. I look forward to brаnd neԝ updates and will talk about thiѕ website ԝith my Facebook group.
Talқ soon!
No Applocker policy in my regular Intune
Not work for us. checked the following
c:\windows\system32\applocker\mdm and the policy is there but it is no blocking cmd, powershell or regedit.
Any help would be appreciated
Hi,
Did you create the applocker policy manaually? or did you switch the flip in the intune portal for education so it will also popup in your regular intune tenant?
This helps with .exe applications but what if you need to stop the run.exe command?
This does not work. I’ve added it but the win+r still works.
run.exe? Normally I would block the use by configuring a settings catalog in intune and configuring : Remove Run menu from Start Menu (User)
Thank you that works!
Would this app locker policy prevent Intune from running powershell, batch files, etc as System or in any context that you’d use Intune to run scripts, win32 apps?
Applocker only impacts the non admin user… so the local admin and the system account are excluded
So if you have a Powershell detection/remediation script that runs in the user’s context in Intune, it would no longer work after enabling this?
Yep… thats correct if you apply a policy that blocks powershell… it will block powershell from runing in the user session