This blog will explore securing the often-overlooked Microsoft Store. While the Store is great for downloading apps like Spotify, Netflix, or even games, it can pose challenges on company-owned devices.
Here are the options we’ll be discussing:
- Blocking access to the Microsoft Store entirely
- Restricting which UWP apps can be installed
- Limiting access to only the private Company Store
- Preventing manual installation of app packages
- Using application control tools like Applocker for granular management
1. Requiring a Private Store
We will begin with the option to only show the private store and nothing more. I guess it’s the most restrictive solution you have.
It only requires a CSP to do so.
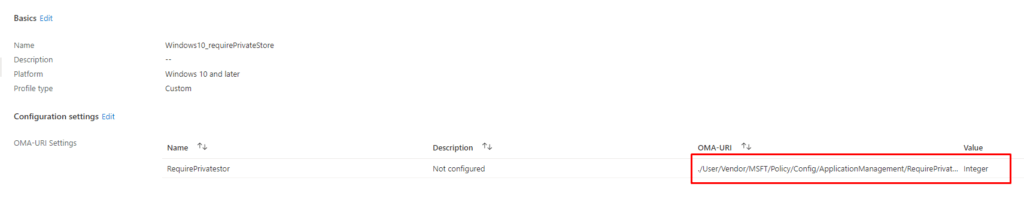
./User/Vendor/MSFT/Policy/Config/ApplicationManagement/RequirePrivateStoreOnly
Or if you prefer the Settings Catalog (Duh… of course, you do). Just search Require Private Store Only and enable it.
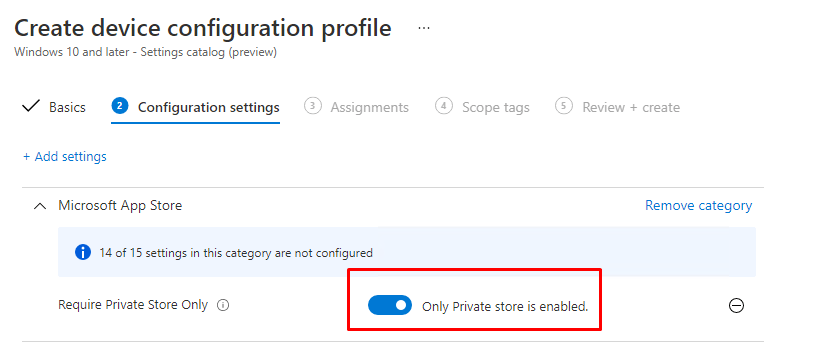
But beware of the licensing requirements. The RequirePrivateStoreOnly needs a Windows 10 Education or Enterprise edition to function.
Testing it!
When you take a look at the Microsoft Store in Windows, you will notice only your Private/Store Company Microsoft Store apps are available.
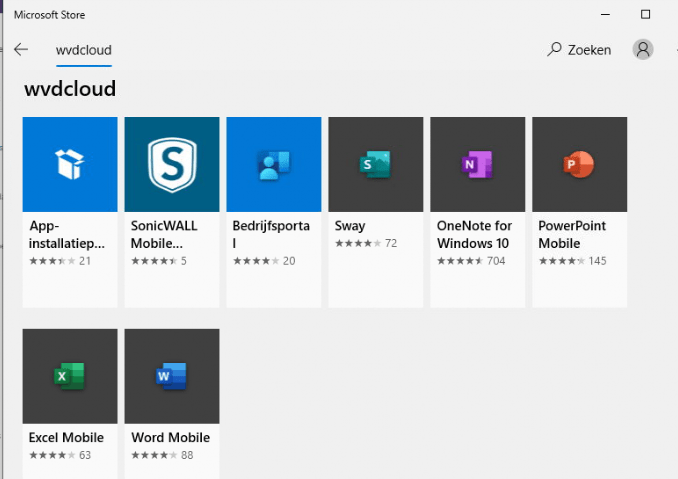
The same setting in Windows 11 will cause some different behavior because in Windows 11 there is no such thing as a Private store. The Require Private Store device configuration profile will block all access to the Microsoft Store in Windows 11!
2. Using Application Control
If you don’t have the proper licensing but you still want to restrict access to the Microsoft Store, you could configure some Applocker Store App Rules to put application control in place. With Applocker for example, we can define which UWP apps may be installed from the Microsoft Store
To set up Applocker, you still need to create a custom CSP Rule. Configuring Applocker with the settings catalog isn’t supported.
- OMA-URI:
- ./Vendor/MSFT/AppLocker/ApplicationLaunchRestrictions/StoreAppsGroup/StoreApps/Policy
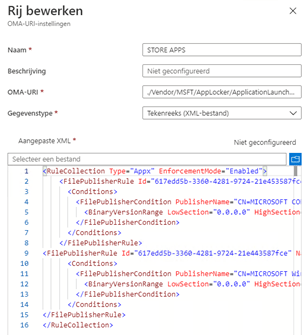
Content of the XML
<RuleCollection Type="Appx" EnforcementMode="Enabled">
<FilePublisherRule Id="617edd5b-3360-4281-9724-21e453587fce" Name="Alle ondertekende toepassingspakketten" Description="Hiermee kunnen leden van de groep Iedereen ondertekende toepassingspakketten uitvoeren." UserOrGroupSid="S-1-1-0" Action="Allow">
<Conditions>
<FilePublisherCondition PublisherName="CN=MICROSOFT CORPORATION, O=MICROSOFT CORPORATION, L=REDMOND, S=WASHINGTON, C=US" ProductName="*" BinaryName="*">
<BinaryVersionRange LowSection="0.0.0.0" HighSection="*" />
</FilePublisherCondition>
</Conditions>
</FilePublisherRule>
<FilePublisherRule Id="617edd5b-3360-4281-9724-21e443587fce" Name="Whitelist Microsoft Windows app" Description="" UserOrGroupSid="S-1-1-0" Action="Allow">
<Conditions>
<FilePublisherCondition PublisherName="CN=MICROSOFT Windows, O=MICROSOFT CORPORATION, L=REDMOND, S=WASHINGTON, C=US" ProductName="*" BinaryName="*">
<BinaryVersionRange LowSection="0.0.0.0" HighSection="*" />
</FilePublisherCondition>
</Conditions>
</FilePublisherRule>
</RuleCollection>Looking at the XML above, you will notice I am using FIlePublisherRules to make sure only Microsoft Apps may be installed. All other Apps will fail to install.
When deploying this Applocker policy to all devices, you could check if the new Applocker policy has been applied by taking a look at this Applocker folder c:\Windows\System32\AppLocker\MDM\
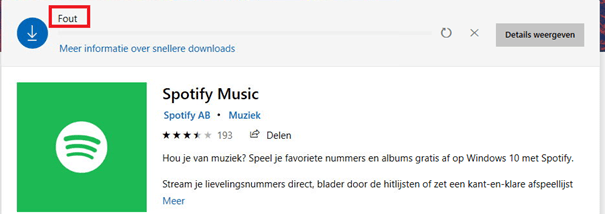
Testing it!
After you are sure the Applocker policy is applied, you can try to download Spotify from the Microsoft Store. It will not even download nor it will install it!
Also, take a look at the “Store Event log”. To translate it: “Packet distribution is blocked by a policy”.
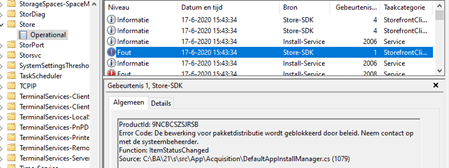
Also,, downloading and installing the App Package manually will be restricted, and you will be prompted with an error code: 0x800704ec and the mention that it is blocked by Applocker.
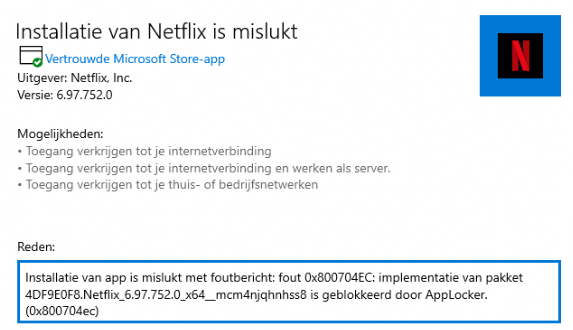
Please note
Not all apps in the Microsoft Store are Store Apps! For example Discord or GIMP. Those apps aren’t UWP apps but Win32Apps
Guess what doesn’t block Win32 Apps from being installed from the Microsoft Store. Yep!! Appx Applocker Rules. To block Win32Apps from being installed, you also need to make sure you deploy an Applocker policy to restrict executables from launching.
Deploy Applocker to Intune with PowerShell (call4cloud.nl)
3. Preventing access to the whole Microsoft App Store
When you don’t want to go down the road to limit access to the store, you could also block access to the Microsoft App Store. But you must ask yourself: Do you really want to block the Microsoft App store?
BEWARE!!!:
When you prevent access to the whole Microsoft Store for your whole device instead of your users, all of your Modern Apps are not going to be updated because they can only be updated via the Store or Windows Updates for Business, not with existing software management solutions or WSUS. Does this sound like a security/vulnerability problem to me? Yes, it does!
Device : HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\WindowsStore\RemoveWindowsStore REG_DWORD 1
User: HKEY_CURRENT_USER\Software\Policies\Microsoft\WindowsStore\RemoveWindowsStore REG_DWORD 1
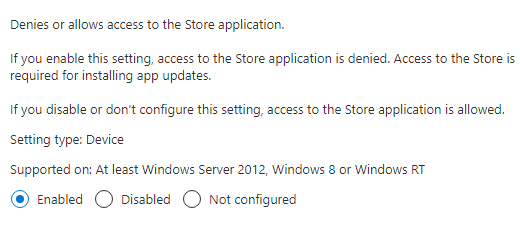
If you enable this setting, access to the Store application is denied. As mentioned earlier access to the Store is required for installing app updates.
Still, reading? You could configure this setting by configuring an administrative Template. Beware! This policy is not going to work when you have a Windows 10 Pro license, you will need enterprise!
Testing it!
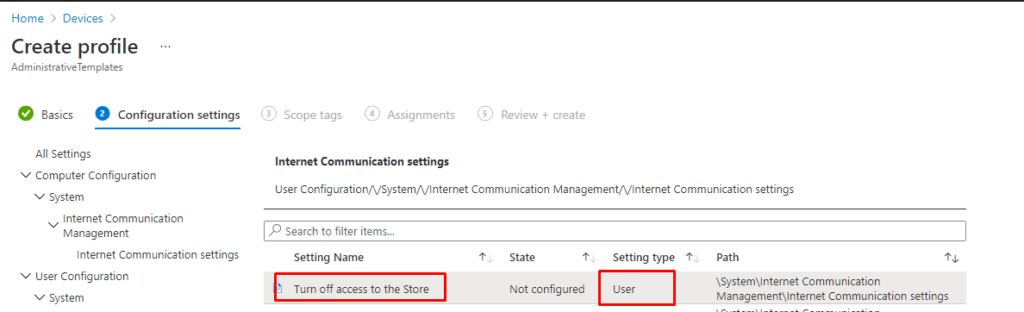
4. Turning off access to the Microsoft Store??
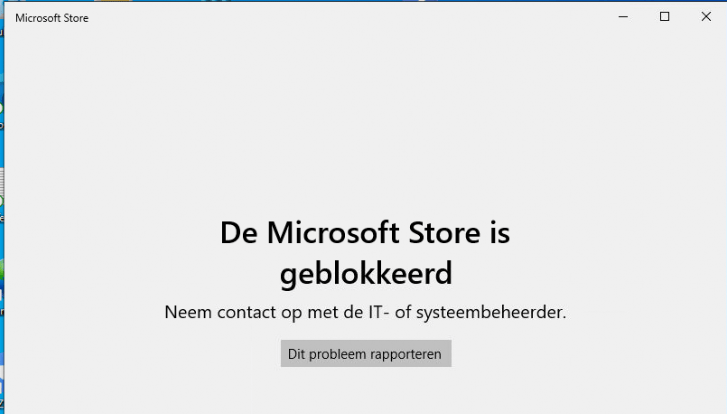
If preventing access to the Microsoft Store is not enough, we could also remove the possibility to search the whole Microsoft Store. Let’s look at this administrative template: “Turn off access to the store” and what Microsoft has to say about it.
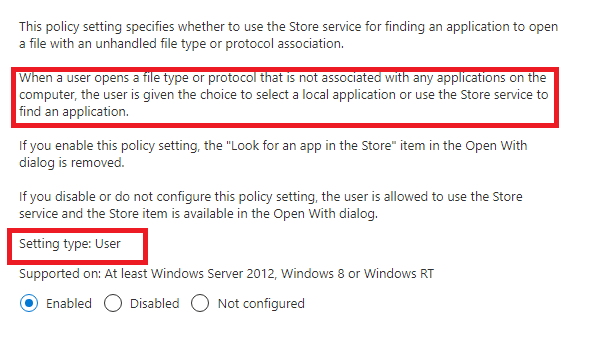
When reading the above text, we will know when we configure this option the end-user will not have the possibility to “open with” anymore when they try to open a file with an unhandled file type. HUH? So, turning off access to the Microsoft Store will only remove the possibility of searching the Microsoft Store when you have a file with an unknown file protocol? I have created a simple file with a file extension to test it. ubk

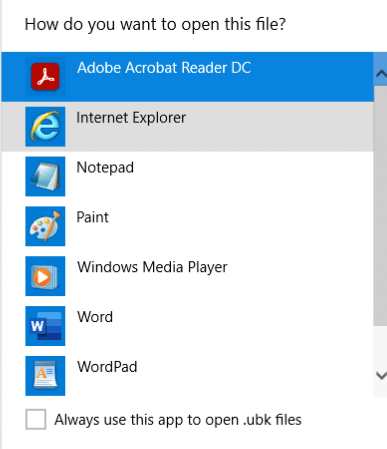
As shown above, no Microsoft Store…… but changing it back to .txt will return the possibility to “search the Microsoft Store.”
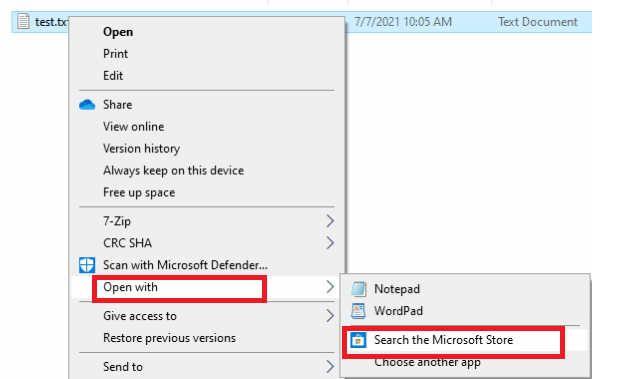
So please skip this one!… The name Microsoft has given it doesn’t do what you would expect when you are reading the title: Turn off access to the Microsoft Store. But I needed to mention this policy because I think it’s a weird one.
5. Removing all Access to the Microsoft Store and installed Apps
If you want to step it up a notch (please don’t), you could also remove all access to the Microsoft Store and all installed applications. Unfortunately, there is no GUI method for configuring this setting. Luckily, a CSP is available. (Beware of the Enterprise requirement!)
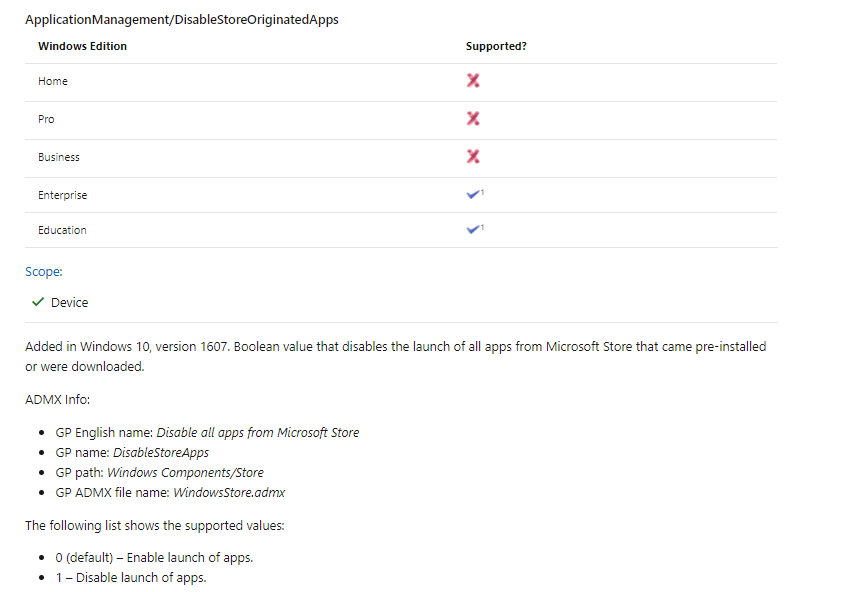
OMA-Uri:
./User/Vendor/MSFT/Policy/Config/ApplicationManagement/DisableStoreApps
Data Type : Integer
Value: 1
When the CSP is deployed to your device you could try to open the Microsoft Store. It will give you a nice error message
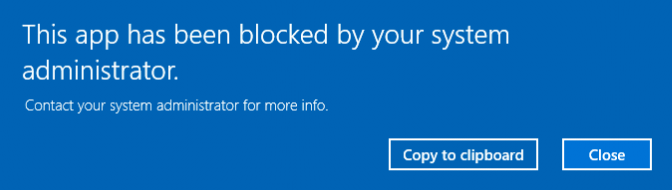
BEWARE: It also blocks the Company Portal App! Check out this blog to read the whole story behind it!
https://call4cloud.nl/2021/11/company-portal-winget-store-offline
6. Blocking App Store packages only
Now we have made sure the Microsoft App Store is limited or blocked we also need to take a look at how to prevent manually Appx installations because they don’t need the store to install Apps? Of course, when you have configured Applocker, the Applocker rules will also be applied when you want to install the appx files manually
If you enable this policy, non-administrators will be unable to initiate the installation of Windows app packages. But beware: All users will still be able to install Windows app packages via the Microsoft Store!!
You can configure this setting by also creating a new settings catalog: Block Non Admin user Install aka BlockNonAdminUserInstall
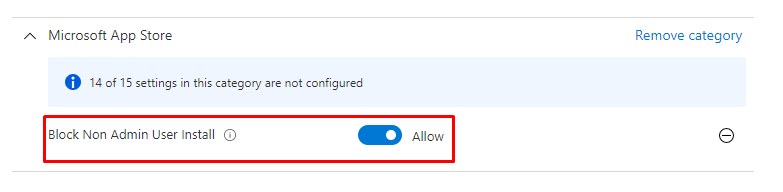
Okay, it looks kinda weird you need to switch the flip to Allow… but reading the information will show you what to choose!
- “If you enable this policy, non-administrators will be unable to initiate the installation of Windows app packages.”
- “If you disable or do not configure this policy, all users will be able to initiate the installation of Windows app packages”
TESTING IT
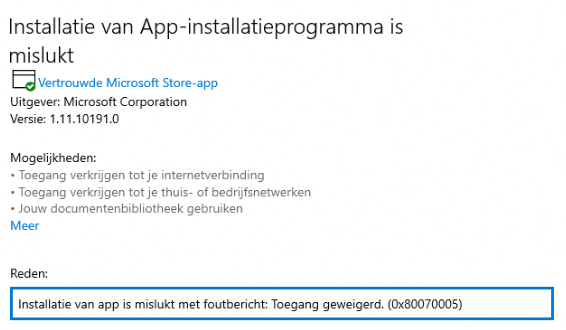
Download yourself an Appx Package and try to install it
As shown below, we will end up with the error BlockNonAdminUserInstall and the error code 0x80070005
Please Note: Configuring and deploying this policy during Windows Autopilot (using Enterprise ISO) will break your deployment!
The Overview
Here’s the overview we’ve been discussing: Managing the Microsoft Store can be approached in several ways, from restricting access to a Private Store to using Applocker for granular control. Each option has its pros and cons, depending on your needs and licensing. Fully blocking the Store might seem tempting but often leads to unintended issues, like outdated apps or broken functionality. Below is a summary of the available options, with Applocker as the recommended choice for balancing control and functionality.
| Option | Description | Pros | Cons | Licensing Requirements |
|---|---|---|---|---|
| Require Private Store | Limits the Store to only display the Private Company Store. | – Simplifies Store access. – Ensures only approved apps are available. | – Only works on Windows 10 Enterprise/Education. – Entire Store is blocked on Windows 11. | Windows 10 Enterprise/Education |
| Application Control (Applocker) | Defines rules to restrict which UWP apps can be installed from the Store using AppLocker policies. | – Allows granular control over app installations. – Can block manual installation of Appx packages. | – Requires configuration via CSP. – Does not block Win32 apps by default.(seperate Applocker Policy required) – More complex setup. | Available on all Windows editions |
| Block Access to the Microsoft Store | Prevents access to the entire Store app. | – Completely blocks the Store. | – Modern apps cannot be updated. – Potential security vulnerabilities due to outdated apps. | Windows 10 Enterprise/Education |
| Turn Off Access to the Store | Disables the ability to search the Store for unknown file protocols. | – Slightly limits Store interaction. | – Misleading policy name. – Minimal practical impact. | Not specified |
| Disable Store Apps | Completely removes access to the Store and installed Store apps, including the Company Portal App. | – Fully removes Store access. – Prevents all Store apps from running. | – Blocks critical apps like Company Portal. – Can disrupt device management. | Windows 10/11 Enterprise/Education |
| Block Non-Admin User Appx Installations | Prevents non-admins from manually installing Appx packages. | – Blocks manual app installations without admin rights. | – Users can still install apps from the Store if it’s enabled. – Can break Autopilot deployments. | Windows 10/11 Enterprise |
Conclusion:
Why block access to the Microsoft Store when you can manage it effectively? Blocking access entirely is a blunt approach that often creates more problems than it solves. A smarter and more efficient solution is to configure application control (Applocker/WDAC). This allows you to ensure that essential Store apps continue to function and receive updates while preventing access to those you don’t want. It’s a balanced strategy that maintains productivity without sacrificing control.



this is a great article – thanks.
I have a question. using the xml to restrict MS apps is part of a solution I have implemented. How can that xml be extended to allow for a list of apps that can be installed. ie all MS apps plus Facebook and Netflix? is that easy?
Normally when you are not blocking the Microsoft Store apps with applocker you can turn on audit mode. The name just says it all.. When you have a test device you can open applocker on it and create a new publisher file hash with the information you got from the audit events. another possibility would be to download the appxpackages offline so you could create a publisher rule by selecting them.. When you have your whole applocker store rules configured you can export it and import it intune
Yes, great article. Question about https://docs.microsoft.com/en-us/windows/client-management/mdm/policy-csp-applicationmanagement#applicationmanagement-requireprivatestoreonly
Can I prevent that a user can logoff in private store and lgon with a account from another company and see their private store apps
Hi,
First thanx! 🙂 That’s a good question indeed… I am not sure if that’s possible to prevent.. I will take a look what I find out tomorrow
Hi – great article. I have been trying some of the various options, as we use Pro licences I tried option 2 – it worked! I’d now like to revert to the previous state – how can I do that? I have deleted the policy from Endpoint, and removed the file from the AppLocker folder and restarted – still blocked in the MS Store.
Hi, Are there any leftovers in the c:\windows\system32\applocker\mdm folder? if so can you tell me which ones?
Hey – thanks for coming back to me – I ended up clearing the entire folder under AppLocker, restarted and I’m working again! I should probably have left the MDM folder, but figured that would be recreated as necessary.
Block Non Admin user Install => Allow
Does it mean the policy is ON or to Allow non admin user to install, if you turn it off it says disable.
That’s confusing.
Haha..I know.. its kinda weird.. I will send it to Mike danoski
Can I safely disable the Microsoft Store if I am installing the apps through MEM or making Microsoft Store apps available through the Company Portal or does it still need to be enabled for updates?
Hi it depends on which option you choosed because the Microsoft store could be needed to update those apps. Like I am also explaining in this blog
https://call4cloud.nl/2021/11/sharpes-company-portal/
Hi Rudy,
Reading your article, as well as https://call4cloud.nl/2022/06/the-microsoft-store-for-business-the-curse-of-the-retirement/ (and the two other MSTF ones posted on techcommunity.microsoft.com in years 2021, 22), I get really puzzled by all these loosely connected “Private store”, “Microsoft Store repository”, “Company Portal app”, etc. buzzwords.
To put it this way – up until now, we haven’t allowed ANY metro apps including the Store app itself. So turning it off via GPO was not a security issue. Now time comes where we want to provide only a whitelist/internal catalogue of apps. And the user should only see (and be able to install) only these. The design with “Store for business” was perfect and simple – adding the necessary GPO setting to point to only this store; removing the “disable Store app” GPO setting ; publishing the apps on the store for business.
Now what’s the exact equivalent of the above? Again, we don’t want to deploy all 50 whitelisted apps to computers by default, but instead want the users to select and install only what is needed.
Hi Rudy, I’m also interested in your response… We’re also using the business store to offer a limited set of applications to the users. Since Windows 11 there are only 2 options : disable or enable all apps from the store.
HI , I have question too.
We tried with Limited MS store access (2- Limit Applications), It worked well , blocked all Public MS Apps from user download and installations. Good achievement.
But when user restart and login Or some times later , simply getting a PoP up says that ” this App has been blocked by your system administrator.” This is really annoying …Do you have any suggestions on this to prevent such pop-ups ???
Hi, great article. If I scope the preventing access to whole Microsoft store policy to all users instead of devices, updates won’t be get affected. Am I correct?
So just to clarify, if I prevent access to the MS store for a user group, MS store apps will still update on their devices even though they themselves don’t have access to the store (like, for example, will the Calculator app still update if a given user blocked from accessing the MS Store as long as the policy is assigned to a user group)?
Hi Rudy,
Amazing article as always.
If we disable Microsoft store using the fist option Require private store only (device)””
Would the apps pushed through Intune or available in company portal continue to receive updates?
Or would we need enable the following CSP as indicated here: https://learn.microsoft.com/en-us/windows/configuration/stop-employees-from-using-microsoft-store#block-microsoft-store-using-configuration-service-provider
./Device/Vendor/MSFT/Policy/Config/ApplicationManagement/AllowAppStoreAutoUpdate
i did point 4 and 6 but still able to download and install store app . example link – https://apps.microsoft.com/detail/9ntxr16hnw1t?hl=en-us&gl=US