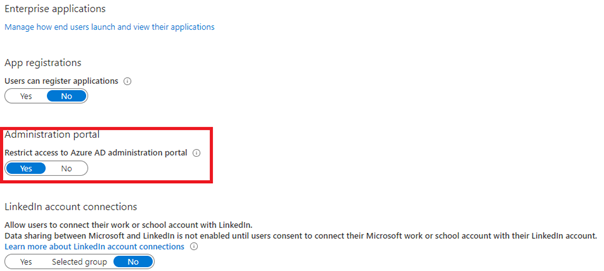
Reconnaissance is the first phase in hacking. It’s a systematic approach to gathering information about your target. It’s up to you to prevent access to the Azure AD administration portal.
It’s very easy to implement within the GUI. Search for the Azure AD/user settings, you’ll find the option to restrict access.
Alternatively, you could add this to your tenant enrollment scripts:
login-azurermaccount
$context = Get-AzureRmContext
$tenantId = $context.Tenant.Id
$refreshToken = @($context.TokenCache.ReadItems() | where {$_.tenantId -eq $tenantId -and $_.ExpiresOn -gt (Get-Date)})[0].RefreshToken
$body = "grant_type=refresh_token&refresh_token=$($refreshToken)&resource=74658136-14ec-4630-ad9b-26e160ff0fc6"
$apiToken = Invoke-RestMethod "https://login.windows.net/$tenantId/oauth2/token" -Method POST -Body $body -ContentType 'application/x-www-form-urlencoded'
$header = @{
'Authorization' = 'Bearer ' + $apiToken.access_token
'Content-Type' = 'application/json'
'X-Requested-With'= 'XMLHttpRequest'
'x-ms-client-request-id'= [guid]::NewGuid()
'x-ms-correlation-id' = [guid]::NewGuid()
}
#Restrict Admin Portal Users
$url = "https://main.iam.ad.ext.azure.com/api/Directories/Properties"
$contentpart1 = '{"restrictNonAdminUsers":true}'
$content = $contentpart1
Invoke-RestMethod –Uri $url –Headers $header –Method PUT -Body $content -ErrorAction Stop
When a naughty user wants to access the Azure ad portal, the setting you defined kicks in.
But I am not done yet!!! Please read part 2 of this blog as I still need some other stuff to be addressed
Conclusion
It’s one of the most important (and forgotten) settings in the Azure AD. Prevent the first hacking phase with just one simple setting. In my opinion, no standard user needs to have access to the Azure AD portal.


One thought on “The Azure AD portal strikes back”