In this blog, I’ll be talking about using DLP in combination with sensitivity labels and device protection. A perfect addition to labeling your data with sensitivity labels. Labeling your data […]
Things to block in Denver When You’re an IT Admin
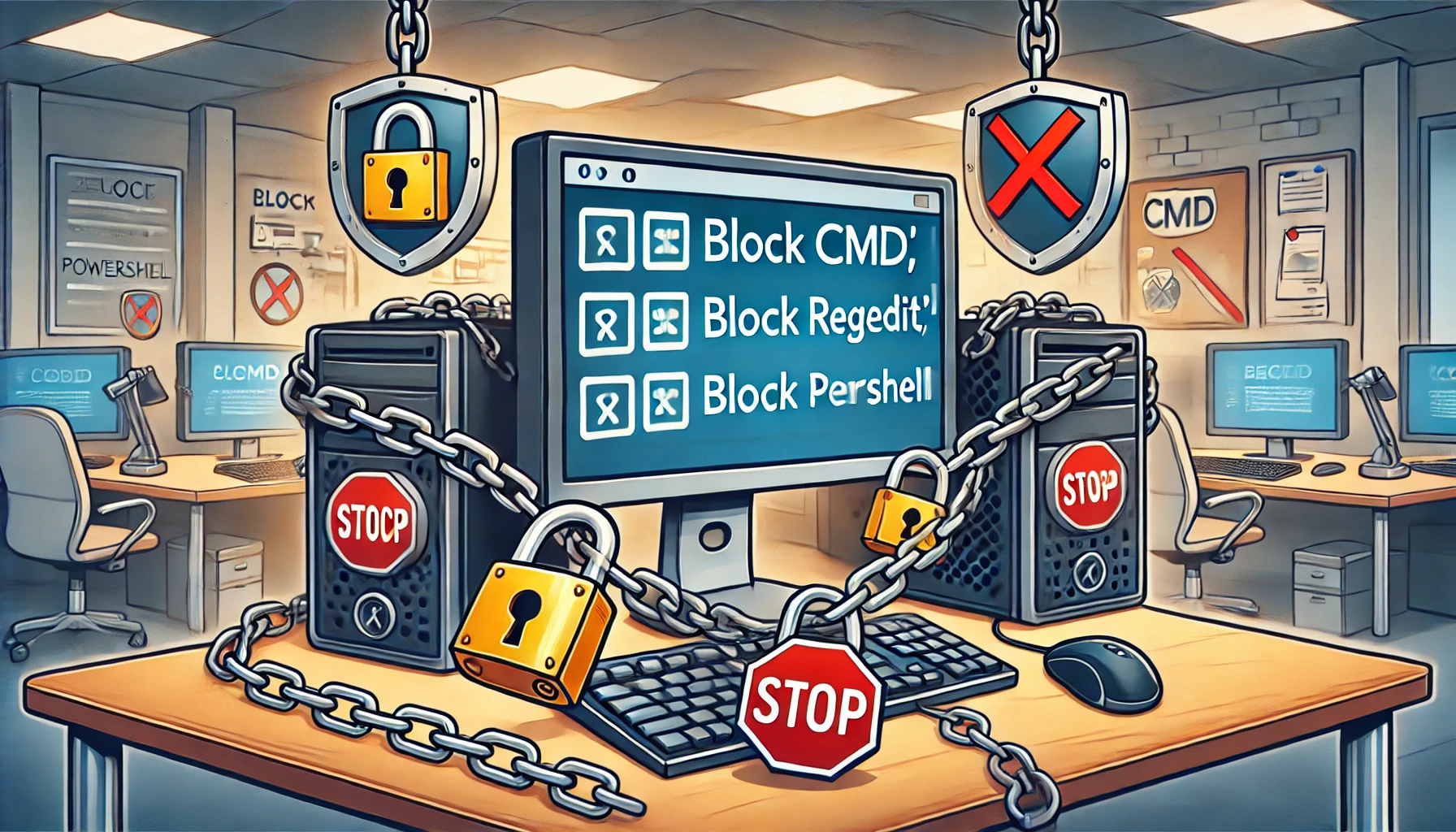
In this updated guide, we’ll explore effective strategies for blocking access to administrative tools such as Regedit (Block Regedit), the Command Prompt (Block CMD), and PowerShell (Block PowerShell). We’ll break […]
Interview with the ASR rules
Protecting your devices with Microsoft Defender ASR rules is best practice, but ensure you know the caveats. The sun was probably shining when you configured your ASR rules! After deciding […]
The Men who stare at the AppLocker event log
In this blog, we’ll delve into the curious interplay between AppLocker, MSI installers, Intune, and event logs. We’ll explore how to configure and monitor AppLocker policies, the limitations imposed by […]
Reservoir update logs
Making sure your devices are up to date with the latest Microsoft updates is one of the key pillars of hardening your endpoints. Updating your devices through Intune is a piece of cake. […]
What Happened to Monitoring External Access to Your Office 365 Data?
Some time ago I wrote a blog about securing your data in which I described that this is only the first step in making sure your data is safe. I will […]
The Fellowship Of Group Labelling
Labelling your data with sensitivity labels is the way to go. Confidential data within your organization needs to be labelled with a proper sensitivity label. You can do this manually […]