In this updated guide, we’ll explore effective strategies for blocking access to administrative tools such as Regedit (Block Regedit), the Command Prompt (Block CMD), and PowerShell (Block PowerShell). We’ll break down multiple methods, including detailed information on the specific Configuration Service Provider (CSP) policies that help secure your environment against unauthorized access to these critical tools.
1. Applocker
Applocker remains one of the most robust methods for locking down administrative tools, particularly in environments where security is a top priority. It allows you to define which users or groups can run specific applications, making it an excellent choice for preventing access to CMD, Regedit, and PowerShell.
For those unfamiliar with Applocker, you can refer to my detailed guide on automating Applocker using PowerShell, where I walk through the setup process:
Applocker à la minute – Call4Cloud PowerShell Automated
This approach remains one of the most robust methods to lock down these tools, especially in environments where security is a top priority.
2. Prevent Access to Administrative Tools (Settings Catalog)
With the latest updates to Windows 11 and Windows 10, blocking CMD and other administrative tools has become more streamlined. Microsoft has continued to enhance the Settings Catalog, making it easier than ever to secure your environment.
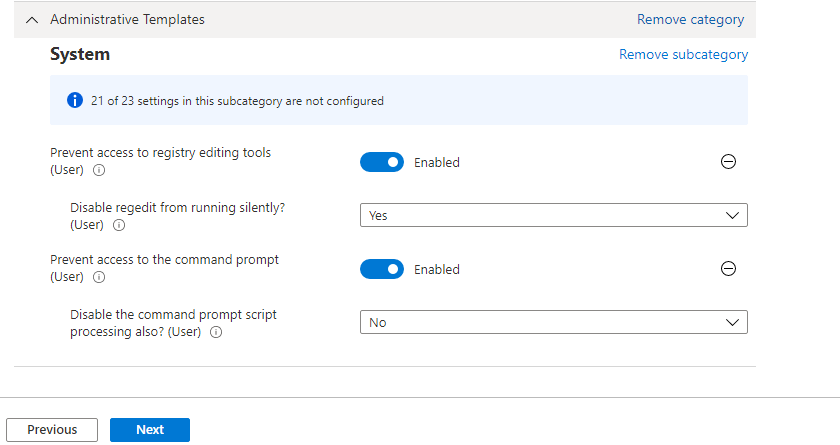
You can now configure these key settings through the Settings Catalog in Intune or Group Policy, leveraging the following CSPs:
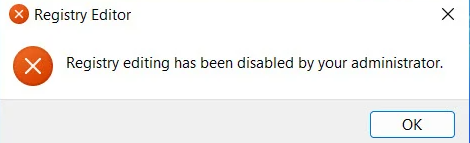
- Prevent access to registry editing tools: This is controlled via the
RegEditToolsCSP. Specifically, you can configure theADMX_ShellCommandPromptRegEditTools/PreventAccessToRegistryEditingToolspolicy to block access to Regedit
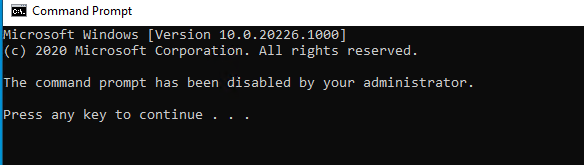
- Prevent access to the command prompt: To block CMD, the
ShellCommandPromptCSP is used. The policyADMX_ShellCommandPromptRegEditTools/PreventAccessToCommandPromptcan be set to ensure that users are unable to open CMD
These settings are now available in the Windows 10 and Windows 11 Settings Catalog, making them accessible to all users, not just Windows Insiders. These options provide a straightforward way to block access to these tools, significantly reducing the risk of unauthorized changes to system settings.
3. Don’t Run Specified Windows Applications (Settings Catalog)
While blocking CMD and Regedit is crucial, preventing access to PowerShell.exe is equally important. The “Don’t Run Specified Windows Applications” setting in the Settings Catalog allows you to block PowerShell, among other applications.
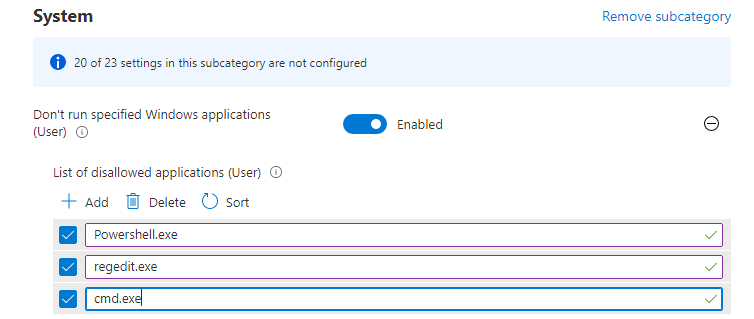
This setting leverages the ApplicationManagement CSP, specifically the ADMX_ShellCommandPromptRegEditTools/DisallowApps policy.
Here’s how it works:
- Block PowerShell: To prevent users from running
PowerShell.exe, you can addpowershell.exeto the list of disallowed applications within theDisallowAppsCSP
This setting, initially available to Windows Insiders, has now been rolled out broadly, making it a vital tool for administrators. With the introduction of Windows 11 and continued updates to Windows 10 (including the 21H2 update), these capabilities are now more accessible than ever. Enforcing this policy will trigger a clear notification to users, making it evident that the operation is restricted—an improvement over the more generic notifications seen with older methods.
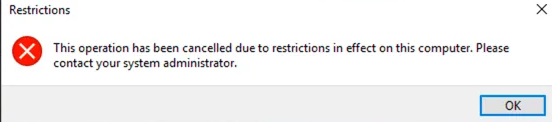
As shown above, when trying to open powershell we will get the message: this operation has been cancelled due to restrictions in effect on this computer
To verify that this policy is in place, you can check the following registry key:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\PolicyManager\current\sid\ADMX_ShellCommandPromptRegEditTools\DisallowApps
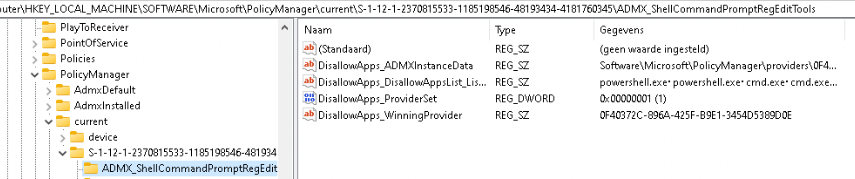
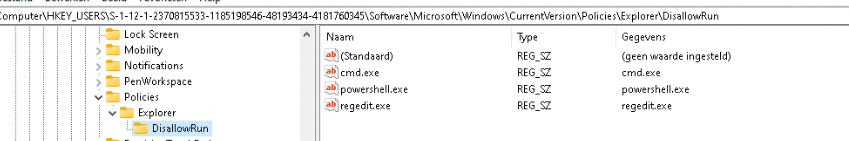
This key will confirm whether the policy effectively blocks the specified applications. With that key in place, the DisAllowRun policy with the process you configured is also configured in the Policies\Explorer\DisAllowRun for the current user.
4. Proactive Remediations
Proactive Remediations is a powerful feature that can be used for various tasks, including blocking access to CMD. Here’s a quick rundown of how to set it up.
Detection Script:
powershellCopy codeNew-PSDrive HKU Registry HKEY_USERS | out-null
$user = get-wmiobject -Class Win32_Computersystem | select Username
$sid = (New-Object System.Security.Principal.NTAccount($user.UserName)).Translate([System.Security.Principal.SecurityIdentifier]).value
$key = "HKU:$sid\Software\Policies\Microsoft\Windows\system"
$val = (Get-Item "HKU:$sid\Software\Policies\Microsoft\Windows\system")
$Timer = $val.GetValue("DisableCMD")
if ($Timer -ne 1) {
Write-Host "CMD is not blocked!"
Exit 1
} else {
Write-Host "CMD is already being blocked"
Exit 0
}
Remediation Script:
powershellCopy codeNew-PSDrive HKU Registry HKEY_USERS | out-null
$user = get-wmiobject -Class Win32_Computersystem | select Username
$sid = (New-Object System.Security.Principal.NTAccount($user.UserName)).Translate([System.Security.Principal.SecurityIdentifier]).value
$key = "HKU:$sid\Software\Policies\Microsoft\Windows\system"
$val = (Get-Item "HKU:$sid\Software\Policies\Microsoft\Windows\system") | out-null
$reg = Get-Itemproperty -Path $key -Name DisableCMD -erroraction 'silentlycontinue'
if (-not($reg)) {
Write-Host "CMD registry key was not created, creating it now!"
New-Item -path "HKU:$sid\Software\Policies\Microsoft\Windows" -name "System" | out-null
New-Itemproperty -path $Key -name "DisableCMD" -value "1" -PropertyType "dword" | out-null
exit 1
} else {
Write-Host "CMD Registry key configured to 1"
Set-ItemProperty -path $key -name "DisableCMD" -value "1" | out-null
Exit 0
}
Once configured, this setup will block CMD for regular users.
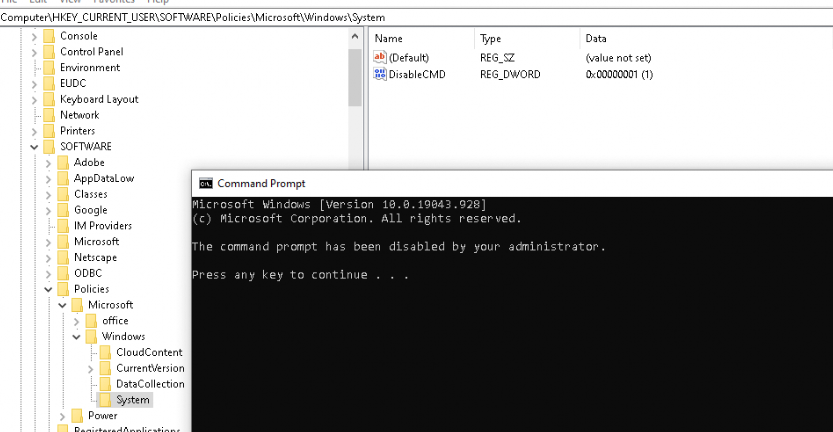
Luckily when running it as the local admin user, running CMD is not restricted!
Conclusion
In this blog, I’ve shown you several methods to block CMD, Regedit, and PowerShell. While Applocker remains my preferred choice for comprehensive control, the Settings Catalog provides a quicker and more flexible option, especially for blocking specific executables. As always, choose the method that best fits your environment’s needs.



Hello,
Thanks for this! Does the settings catalog still grant access to admins to use admin tools?
It depends on how you target it.. but when using a dedicated local admin user it shouldn’t target that one.. But I would rather deploy applocker so you can do the same…. but applocker ways ways better…
Thanks. This helped me block PowerShell on your end points