Protecting your devices with Microsoft Defender ASR rules is best practice, but ensure you know the caveats. The sun was probably shining when you configured your ASR rules! After deciding to use Solarwinds to monitor your devices, you pushed the agent to your endpoints. Then suddenly, the weather changed…
I will divide this blog into multiple parts
1.Win32App installation issue
If you are using Solarwinds/ N-able as an additional RMM tool, you probably configured a new Win32App with the Win32 App Packaging Tool. So did we!
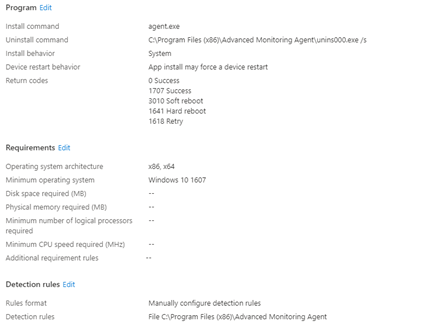
I guess, like everyone else, we were using Autopilot pre-provisioning. We configured this Solarwinds app as a required app because we wanted that app to be installed before the device was shipped to the customer. But sometimes (randomly), we ended up with an Autopilot Red Screen telling us there was a Time out.
So we wiped the device and started monitoring C:\Program Files (x86)\Microsoft Intune Management Extension\Content\Incoming folder to watch for new installs. And there it was! But nothing happened after the installation file was downloaded. There was no MSI installer progress, nothing… Which is a bit weird as i was expecting to have some more information being mentioned in the Intune Management Extension appworkload.log
2. Troubleshooting the Problem
When you need to start troubleshooting, you must take a good look at the Management Extension log and start digging around, just like I showed you in this blog below! It will guide you through each step of the ESP!
https://call4cloud.nl/2021/05/imecache-attack-of-the-cleaner
After searching the part mentioning the Appication detection rules, we noticed the app was not installed (false). But we were still missing some information about “the why” it wasn’t detected after installation. Okay so the Intune management log didn’t showed us what happened, I guess we need to look further!
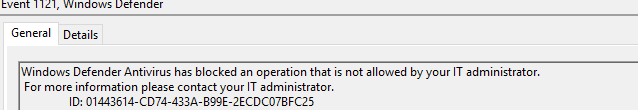
Looking closer at some other event logs, especially the Windows Defender event log, showed us some warnings—a lot of them! As shown below, there are many nice Attack Surface Reduction (ASR) events 1121 within the Windows Defender operational log, mentioning that Windows Defender Antivirus has blocked an operation that is not allowed by your administrator. For more information, please contact your it administrator.
3. Defender ASR Rules
So one of the ASR rules is specifically blocking your installation. But which of the ASR rules did it? Which of you made me look at all the logs?
When googling the ID 01443614-cd74-433a-b99e-2ecdc07bfc25 it showed us it was actually the id for the ASR rule “Block executable files from running unless they meet a prevalence, age, or trusted list criteria”
So after noticing the 01443614-cd74-433a-b99e-2ecdc07bfc25 ARS rule was to blame, we changed the ASR setting in Intune to ensure that one was disabled. After disabling that ASR rule, Solarwinds was installed without any issue.
Another possibility is to exclude the incoming path from the ASR rules, but for now, I just turned off the Block executable files from running unless they meet a prevalence, age, or trusted list criteria rule. That one did more harm than good!
Conclusion:
Even a small setting like an ASR rule could prevent new Win32 App installations on existing and new devices. When deploying new devices, this setting could be or could not be a problem because sometimes the Application was already installed successfully before the ASR device configuration could kick in.
Looking at the Windows Defender log is a good thing to remember when troubleshooting Win32 app Installations. Windows Defender could be blocking something you didn’t expect!

Personally, I think it’s a little weird Solarwinds their device Agent is blocked by ASR but deploying Chocolatey is no problem at all?

