Introduction: Enhancing Your Intune Troubleshooting Toolkit with Fiddler
Troubleshooting issues in Microsoft Intune can be challenging, especially when you’re dealing with complex configurations like conditional access policies, device settings, update management, and compliance rules. Misconfigurations or unexpected behavior can lead to significant disruptions, making it crucial to have effective tools and methods available. In this blog, I’ll show you how to use Fiddler, MDM, and PowerShell to diagnose and resolve issues within your Intune environment, giving you the insights needed to keep your systems running smoothly.
1. Capturing HTTPS Traffic for Troubleshooting
When troubleshooting Intune or any other cloud services, capturing HTTPS traffic can provide invaluable insights into what’s happening behind the scenes. To do this effectively, we’ll use Fiddler,a web debugging proxy that logs all HTTP(S) traffic between your computer and the internet.
Step 1: Capture HTTPS Connects
Start by downloading and installing Fiddler from Telerik’s website. Once installed, select “Capture HTTPS Connects” and “Decrypt HTTPS Traffic” to ensure all HTTPS traffic is decrypted in Fiddler. After selecting the option, make sure you allow the Proxy Certificate to be installed.
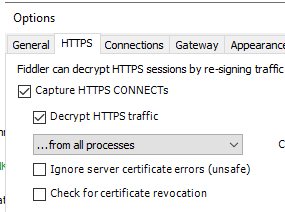
This step is essential, as without decrypt HTTPS traffic enabled, you won’t see the necessary details for troubleshooting.
Step 2: Monitoring Intune Traffic
With Fiddler set up, let’s test it by configuring a Conditional Access rule! Open the Intune web portal and create or modify a Conditional Access rule, device configuration, or other Intune settings. As you save changes, Fiddler will capture the traffic between your browser and the Intune service.
Switch to Fiddler and review the captured data, focusing on the “Inspectors” tab where you can view the traffic in text or raw format.
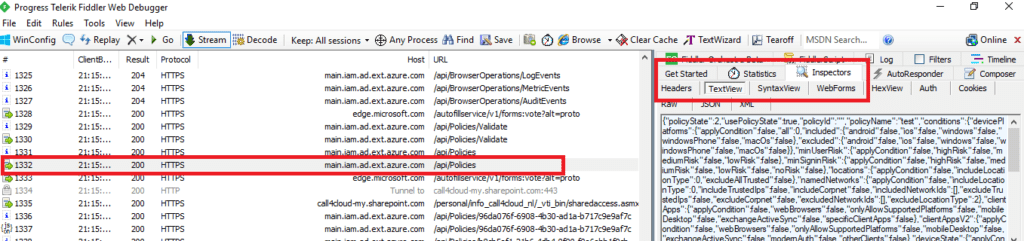
This information can reveal whether the requests are being sent correctly, whether there are any unexpected errors, or whether specific settings are not being applied as intended.
A good example of how I used Fiddler to troubleshoot an issue in which the EPM agent wasn’t getting installed is this one
MMP-C Discovery failed | No valid Endpoint | EPM (call4cloud.nl)
If I didn’t had Fiddler in place, it would be hard to to know the proper and bad flow
2. Basic Fiddler Tips for Effective Troubleshooting
Before diving deeper into troubleshooting, it’s important to configure Fiddler correctly to avoid missing any critical information.
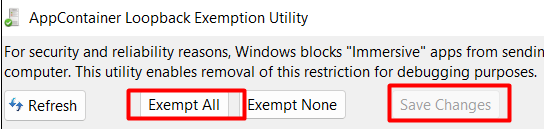
- Exempt Immersive Apps: Ensure that immersive apps are exempted from HTTPS decryption to prevent them from being blocked. This is important for maintaining app functionality while troubleshooting.
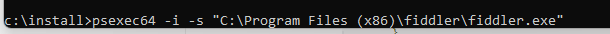
- Running Fiddler as System: If necessary, you can run Fiddler as a system process using Psexec, though in most cases, capturing traffic as the user should be sufficient.
- Automatic Log Export: Configure Fiddler to automatically export logs every minute. This ensures that you have a complete record of traffic, which is essential for post-incident analysis.
- Redirect all traffic to Fiddler: Don’t forget to redirect all traffic to Fiddler. You can do so by entering this command: netsh winhttp set proxy 127.0.0.1:8888
3. Capturing MDM Traffic for Intune Troubleshooting
One of the more complex aspects of troubleshooting Intune is dealing with MDM traffic. Often, when you attempt to capture this traffic, you might encounter errors related to client certificates.
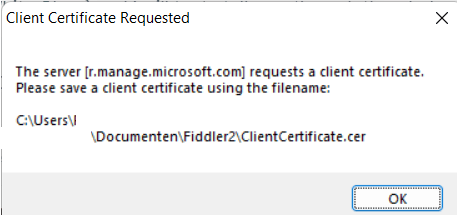
As shown above, Fiddler tells us that Client Certificate Requested for the server r.manage.microsoft.com. Here’s how to work around these issues.
Option 1: Exclude Specific Domains
To avoid errors when capturing traffic, you can exclude certain domains like manage.microsoft.com and r.manage.microsoft.com from HTTPS decryption. While this will prevent errors, it also means you won’t capture traffic from these domains, limiting your ability to troubleshoot certain issues.

Option 2: Use the Intune Client Certificate
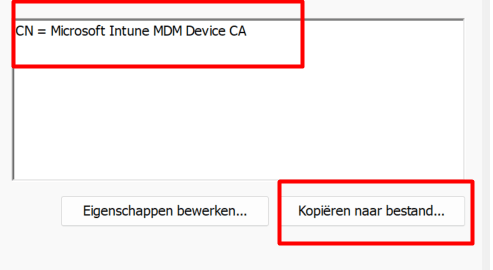
A more comprehensive approach involves exporting the Microsoft Intune MDM device certificate. This certificate is essential for secure communication with Intune, and by configuring Fiddler to use it, you can decrypt and capture the MDM traffic.
- Export the Certificate: Open the local computer certificate store and export the Intune MDM device certificate to a file (e.g.,
ClientCertificate.cer).
- Configure Fiddler: Place the certificate in the
%username%\documents\fiddler2folder and restart Fiddler. This setup allows Fiddler to decrypt and capture MDM traffic, giving you a clearer view of what’s happening between the client and Intune.
Please note, this trick will only work when you have started Fiddler as a user. When you execute Fiddler as a system, you can guess what’s missing: the system document folder. Besides the missing document folder, we also want to define some more URLs and redirect each URL to it’s own certificate. So, how do you do this?
Open the Fiddler Script editor by clicking on “Rules” and “customize rules”
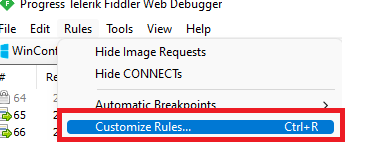
Add this part to the “static function OnBeforeRequest(oSession: Session)” part.
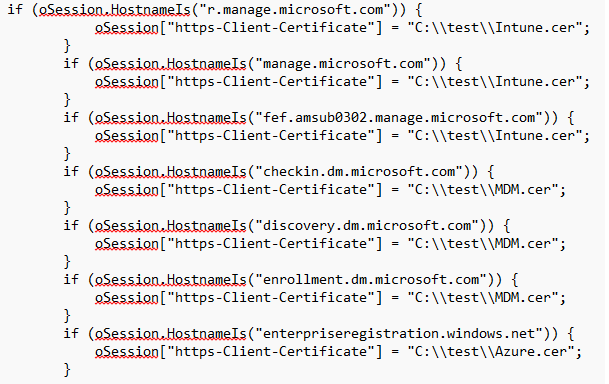
if (oSession.HostnameIs("r.manage.microsoft.com")) {
oSession["https-Client-Certificate"] = "C:\\test\\Intune.cer";
}
if (oSession.HostnameIs("manage.microsoft.com")) {
oSession["https-Client-Certificate"] = "C:\\test\\Intune.cer";
}
if (oSession.HostnameIs("fef.amsua0702.manage.microsoft.com")) {
oSession["https-Client-Certificate"] = "C:\\test\\Intune.cer";
}
If you want to prevent the decryption of put request, you could add an additional rule:
if (oSession.oRequest.headers['Method'] == 'PUT') {
// Disable decryption for PUT requests
oSession["x-no-decrypt"] = "true";
}Please ensure you change the fef.amsua0702.manage to your own URL or use a wildcard.It should look like this:
4. Troubleshooting Microsoft Store Apps with Fiddler
Fiddler isn’t just for capturing MDM traffic—it can also be used to troubleshoot issues with Microsoft Store apps. Whether you’re trying to identify problems with app downloads or deployment, Fiddler can help you see the underlying traffic.
Capturing Microsoft Store Traffic
- Exempt Microsoft Store: Just like with MDM traffic, ensure the Microsoft Store is the only app exempted to reduce unnecessary traffic capture.
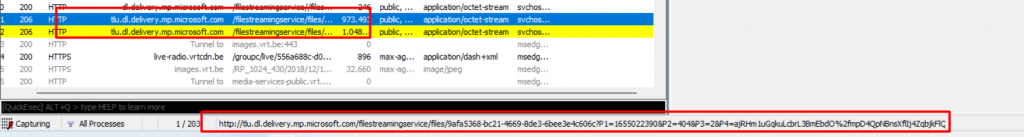
- Monitor App Downloads: Start an app download from the Microsoft Store and switch to Fiddler to capture the traffic. Look for URLs related to the download, such as
http://tlu.dl.delivery.mp.microsoft.com, which can give you insights into any issues with the download process.
Conclusion
Fiddler, MDM, and PowerShell are powerful tools for troubleshooting and resolving issues within your Intune environment. By capturing and analyzing HTTPS and MDM traffic, you can identify misconfigurations, resolve errors, and ensure that your Intune deployments are functioning as intended. Whether you’re dealing with Conditional Access rules, device configurations, or app deployments, these tools will help you get to the root of the problem quickly and effectively.


Hey Rudy,
I’m trying to get this working to proxy Intune sync traffic and not having any luck. Does the private key have to be included in the “Microsoft Intune MDM Device CA” certificate for this to decrypt traffic? Every tool I’ve tried says the private key is not exportable.
Thanks!
Hi, when i need to decode the intuen traffic with fiddler (proxy) i only need to export the certificate. The private key is notexportable any longer and is not needed
I must be doing something else wrong then. Thanks for helping me avoid that rabbit hole!
Note that this:
if (oSession.oRequest.headers[‘Method’] == ‘PUT’) {
// Disable decryption for PUT requests
oSession[“x-no-decrypt”] = “true”;
}
Does not really work. In order to detect that this was a PUT request, you’ve already had to decrypt the traffic.