Are you having issues when you are trying to create some Intune Enrollment Restrictions, or is the option to create the enrollment status page greyed out? If that’s the case, you will need to read this blog because there is a big chance the MDM Authority is not configured correctly!
1. Introduction
Today, I was called in to investigate a weird problem. A colleague tried setting up Intune for a new Microsoft 365 customer. In a normal situation, we do this by launching our deployment scripts, but this time, a new colleague wanted to see which steps need to be taken to enroll a customer in Microsoft 365.
Everything was going fine until the enrollment restrictions part. Enrollment restrictions must be configured to prevent personally owned devices from being enrolled or block Android device administrators.
If you want to read more about the difference between Personal and Corporate Devices and how you can enroll them, read this blog
MDM vs. MAM | Personal vs. Corporate Intune Devices
2. The Issues
If you read the blog I mentioned above, you will know that when you use Autopilot, it’s always smart to block the possibility of enrolling personally owned devices. By blocking the possibility of enrolling personal devices, you are making sure only corporate devices can be enrolled!
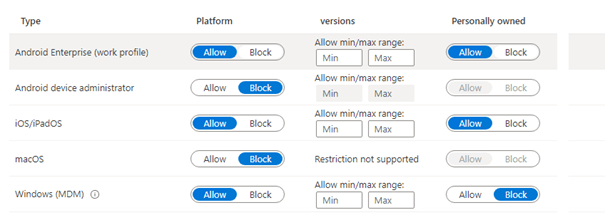
But was the option to edit the policy, as shown below, missing? I was like: Huh? Did I lose my sight?
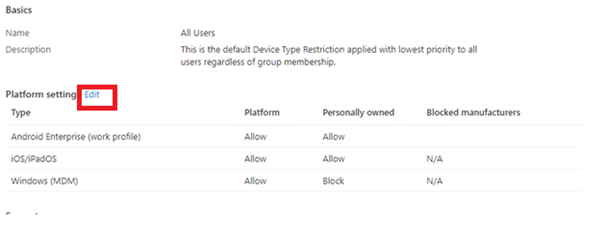
Okay? Also, it seems there is no option to edit the existing policy? I was curious about what else was broken, so let’s try to create a new enrollment restriction policy.
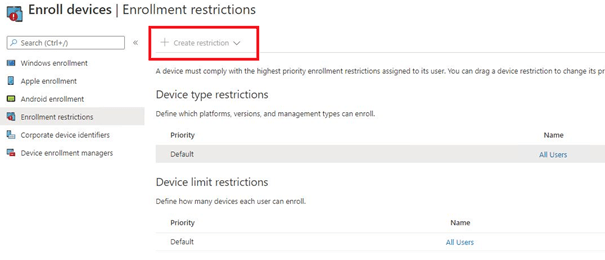
As shown above, the “create restriction” is greyed out? It’s becoming weird! When trying to change or try to create an Enrollment Status Page (ESP) the button to do so is also greyed out.
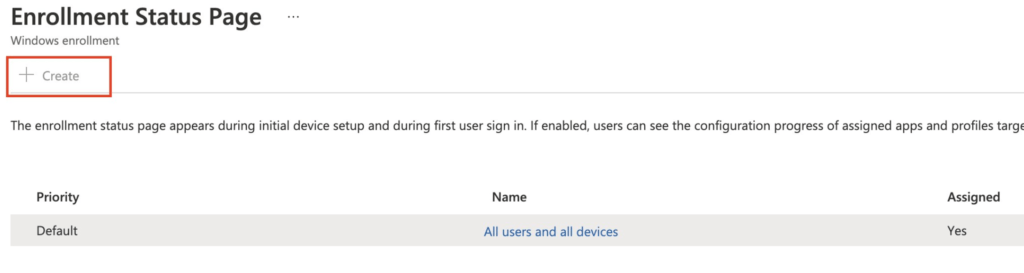
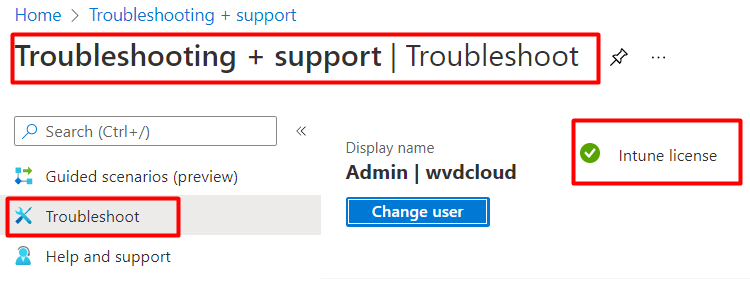
Okay…. some weird stuff is going on, that’s for sure! First, I checked to see if I had the proper license to do so. As shown below, the admin user was licensed to use Intune. So what’s next?
3. Checking the MDM Authority
After spending a few minutes on Google, I discovered that the MDM authority needs to be configured under Mobile Device Management Authority. Without this option, creating or editing an enrollment restriction policy is impossible.
If you want to know which MDM authority is configured, please open the Tenant Administration to check your the Tenant Details.
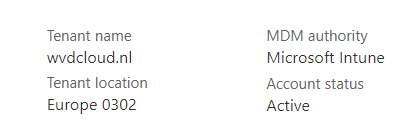
It should be set to Microsoft Intune, as shown below
Let’s see what Microsoft has to say about how this needs to be configured.
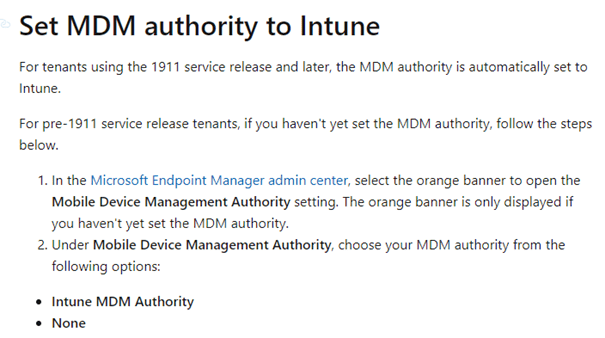
But within this tenant, no orange banner was shown. The possibility of enabling it to be configured within the Entra Portal and open Intune is obviously gone, as this old Portal is depreciated. Let’s take a look at some options to fix it
4. The PowerShell Fix
Let’s start with the PowerShell option! I quickly realized this configuration is part of our deployment script. So I opened our Tenant deployment script… and there it was, at step 2A: Configure Intune as MDM authority.
# Connecten naar msgraph (install-module microsoft.graph.intune)
Connect-MSGraph
$mdmAuth = (Invoke-MSGraphRequest -Url "https://graph.microsoft.com/beta/organization('$OrgId')?`$select=mobiledevicemanagementauthority" -HttpMethod Get -ErrorAction Stop).mobileDeviceManagementAuthority
# Intune Instellen als MDM Authority
if($mdmAuth -notlike "intune")
{
$OrgID = (Invoke-MSGraphRequest -Url "https://graph.microsoft.com/v1.0/organization" -HttpMethod Get -ErrorAction Stop).value.id
Invoke-MSGraphRequest -Url "https://graph.microsoft.com/v1.0/organization/$OrgID/setMobileDeviceManagementAuthority" -HttpMethod Post -ErrorAction Stop
}
I fired up a PowerShell prompt and copy-pasted the script. After refreshing the enrollment restriction page, the options to create or edit the restrictions were instantly available.
But as ms-graph ain’t working anymore, you need to use the: Microsoft.Graph.Identity.DirectoryManagement module
Import-Module Microsoft.Graph.Identity.DirectoryManagement
Set-MgOrganizationMobileDeviceManagementAuthority -OrganizationId $organizationIdLet’s also take a look at some alternative methods to configure the MDMAuthority if you don’t want to use PowerShell
5. Graph Explorer
Using Graph Explorer, we can still configure the MDM authority by setting the setmobiledevicemanagementauthority . To do so, we first need to fetch the Organization ID
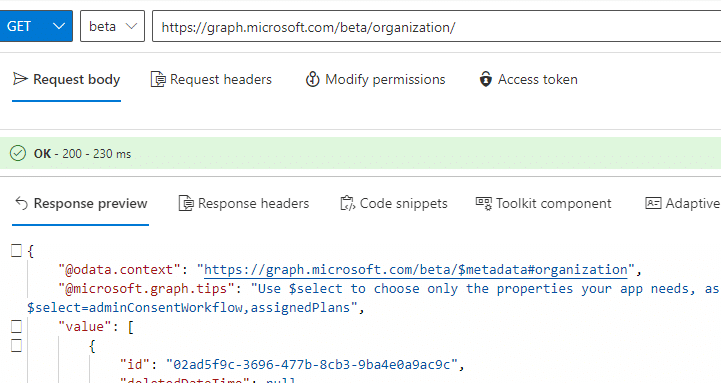
Now we have the Organization ID, we can use that ID and add it in the graph uri: https://graph.microsoft.com/v1.0/organization/(ID)/setMobileDeviceManagementAuthority
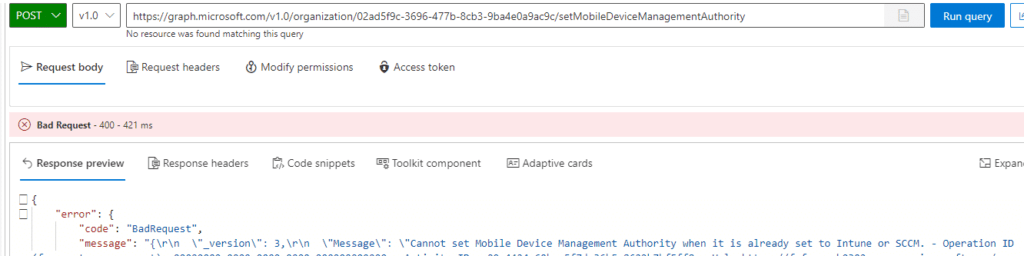
As shown below, when the MDM authority is already been set to Intune or SCCM it will error out.
6 .The Magic Link
If you don’t want to fire off that PowerShell script or use Graph Explorer, you could also just click on one of these 2 links below to set Intune as the default MDM.
Migration evaluation – Microsoft Intune admin center
https://intune.microsoft.com/#view/Microsoft_Intune_Enrollment/ChooseMDMAuthorityBlade
That’s easy right?
Conclusion:
I say this quite a lot, but automating your processes will ensure all options are configured with no human errors. Of course, you will need to make sure everyone knows what the script does, only firing up a PowerShell script with no background knowledge is stupid.




Hi Rudy,
Was able to tweak this from Azure Portal. Please see if hat helps.
Kind Regards,
The API does not work anymore fyi – returns a server-side serialization error
Hi Rudy,
Thanks for the effort, but seems like it is not working anymore, can you give an updated script working with the latest version of sccm and intune.
Thanks and Regards,
Kamran Kazmi
Hi, I updated the blog and added some possible other methods to setyp the mdm authority
Thanks very much for your help Rudy, I used the magic link and I was able to configure my MDM authority. Really appreciate you sharing your knowledge!