This short blog will explain why users don’t need admin permissions to delete public desktop icons.
1. Introduction
When it comes to managing devices within an organization, many people assume that Azure AD users need local admin permissions to perform various tasks. However, this isn’t always the case. In fact, there are numerous tasks that users can accomplish without requiring elevated privileges. Let’s explore a few of these tasks:
- Restarting Services: Users can restart services without needing local admin permissions, making it unnecessary to grant them elevated access.
- Installing Applications: Installing necessary applications can be done without admin rights, ensuring a secure and controlled environment.
- Read more: [The PowerShell Win32 App Express – Call4Cloud]
- Installing Printer Software: Users can install printer software without administrative access, simplifying device management while maintaining security.
- Read more: [Company App: Unchained – Call4Cloud]
- Installing Printer Drivers: Even the installation of printer drivers can be handled by non-admin users, reducing the need for elevated permissions.
- Read more: [Birds of Printer Drivers – Call4Cloud]
Given these capabilities, it raises the question: are there any other tasks that genuinely require users to have admin permissions? As we delve deeper into this topic, it becomes clear that the need for admin rights is often overestimated, and a more secure, restricted access model can still empower users effectively.
2. The Issue
When deploying software to your endpoint, it’s common for a shortcut to be created in the public desktop folder: C:\Users\Public\Desktop. This folder is shared across all users on a device, making it a potential clutter point.
This can be frustrating for users who prefer a clean and personalized desktop. They may want to remove desktop icons they didn’t create, but without local admin permissions, they encounter challenges. When attempting to delete a desktop shortcut, they’re met with a User Account Control (UAC) prompt, and without the proper permissions, they cannot proceed.
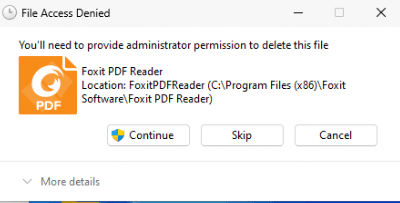
While several methods exist to remove desktop icons in the background, a more straightforward solution would be to allow users full control over the public desktop folder in Windows 10 and Windows 11.
3. Fixing the Public Desktop permissions!
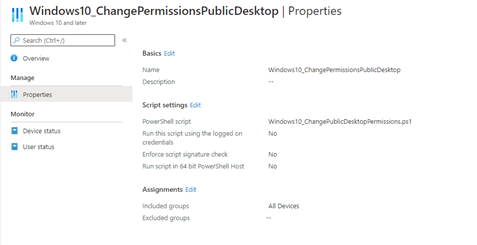
To assign the proper permissions, we are going to create a very simple PowerShell script and deploy it to your devices. This script would change the permissions for the public desktop and ensure that the shortcuts in this folder inherit the same permissions.
$path = "C:\Users\Public\Desktop"
$acl = Get-Acl $path
$user = New-Object System.Security.Principal.SecurityIdentifier('S-1-5-11')
$rule = New-Object System.Security.AccessControl.FileSystemAccessRule ($user,"Modify", "ContainerInherit,ObjectInherit", "None", "Allow")
$acl.SetAccessRule($rule)
Set-ACL $path $acl
PLEASE NOTE. This sid “S-1-5-11” represents the Authenticated Users sid. You could change “S-1-5-11” to fit the proper user group!
When this PowerShell script is deployed to your devices, your users will be able to delete the icons they don’t want and will stop complaining at your desk.
Conclusion:
As I have said many times before, there are absolutely no reasons why your users need admin permissions on their devices. With this script, you can circumvent one reason. Of course, you can also use this script to change permissions on other folders. But beware!!! Do not change permissions in the folders you allowed Applocker to run applications from.



I get the following error when trying to test this script. I am launching powershellISE as admin and running the script.
Error:Exception calling “SetAccessRule” with “1” argument(s): “Some or all identity references could not be
translated.”
At line:3 char:1
+ $acl.SetAccessRule($rule)
+ ~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : NotSpecified: (:) [], MethodInvocationException
+ FullyQualifiedErrorId : IdentityNotMappedException
I Just noticed i copy pasted the dutch translation of everyone 🙂
SO you need to change the “iedereen” to “everyone” . I also changed the blog
Thank you, very useful.
Just for changing the IP to access other networks I already need admin permissions.
Thank you, very helpful! I’ve just optimized it a bit so language doesn’t matter anymore (and I think “modify” permission is sufficient):
$path = “C:\Users\Public\Desktop”
$acl = Get-Acl $path
# S-1-5-11: Authenticated Users (SID)
$user = New-Object System.Security.Principal.SecurityIdentifier(‘S-1-5-11’)
$rule = New-Object System.Security.AccessControl.FileSystemAccessRule ($user,”Modify”, “ContainerInherit,ObjectInherit”, “None”, “Allow”)
$acl.SetAccessRule($rule)
Set-ACL $path $acl
Thanx.. defining the sid of like I did with changing the acl on task schedules is always better.
https://call4cloud.nl/2022/01/updating-apps-a-new-era/
I guess I totally forgot I didn’t used it with this blog, thanx for reminding me 🙂 I updated the blog
Very good idea to give user access instead of manage icon by icon.
I am currently try this.
It works for an already enroll pc. I need to try for a new enrollment.
Thanks for the tip.
I arrive often on your blog and I thinks it’s my first commentary. So thanks for your shares. 😉
Do you have a RSS flow on your site? I didn’t find it.
Hi,
of course I have
https://call4cloud.nl/feed/
Perfect. Thanks. I add your site in my Netvibes. 😉
I’ve used a similar script in the past, but they lose permission to edit public desktop after a week or so, will this
Hi,
I guess we could always use proactive remediations to detect and fix those permissions if needed?