This blog will be about some misunderstandings when you are using Conditional Access and requiring App Protection and/or Approved apps.
Every organization has BYOD users, these users want to have access to the company data from that same device. You want to make sure you are not only managing the devices, but you also need to manage the apps.
Some time ago I explained how you could allow managed and unmanaged devices and how to make sure App protection policies are configured for each deployment!
But let’s go further with The App protection policies and Conditional access because Microsoft Teams does support App protection policies but it really does not go hand in hand with the Conditional Access “Require app protection policy”.
Grant controls in Conditional Access policy – Azure Active Directory | Microsoft Docs
EDIT 14-12-2021
Before this update
Require App Protection Policy
These are the apps that support require app protection grant access policy
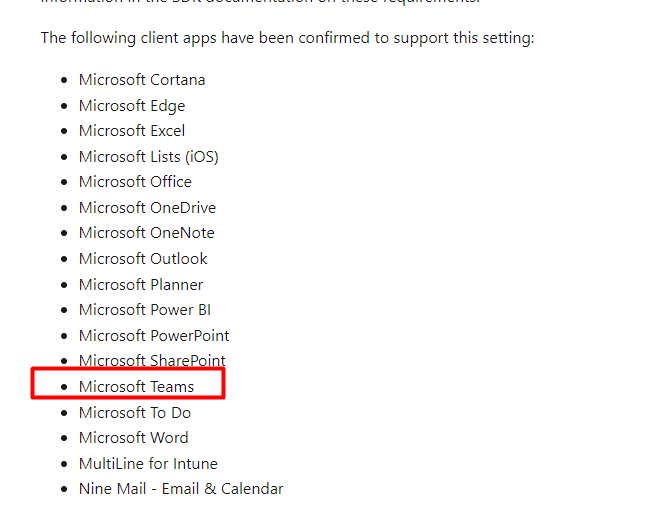

And now! Microsoft Teams is removed from this note!!!
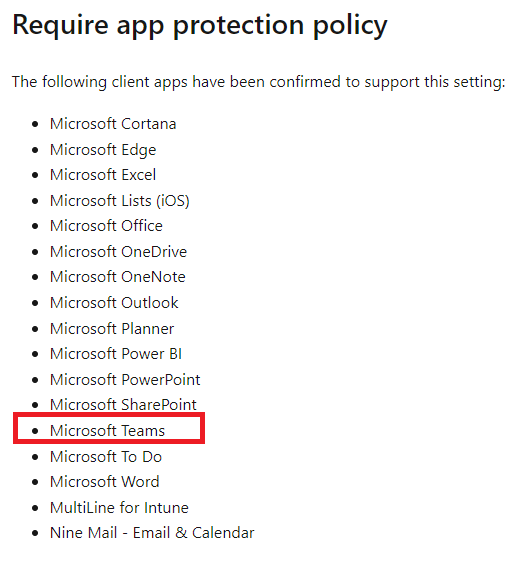
Require Approved Client App
These are the apps that support require approved client app grant access policy.
Now we know which apps do support and do not support app protection and have seen Microsoft Teams only support the approved app policy, I want to show you the flow of how this app protection access control works.
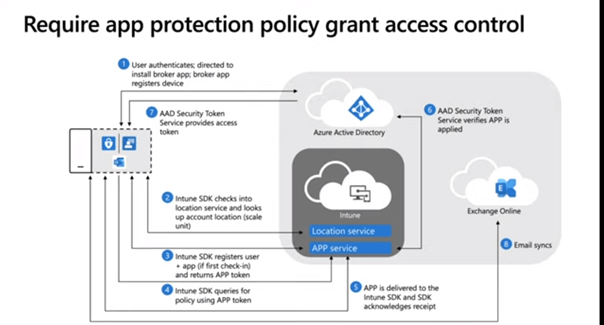
So, Instead of requiring App Protection, we could only require an approved client app as shown in the blog I mentioned earlier?
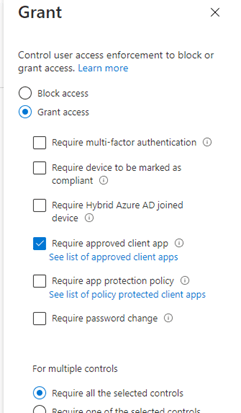
But what, if there is a way better method so you could require an App Protection policy, and when it does not support App Protection, it will just require Approved Apps? I guess it’s very simple, just switch the button!
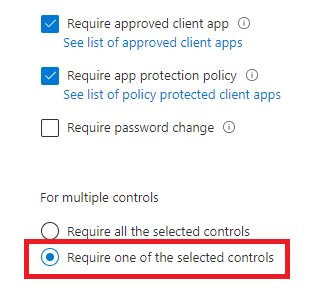
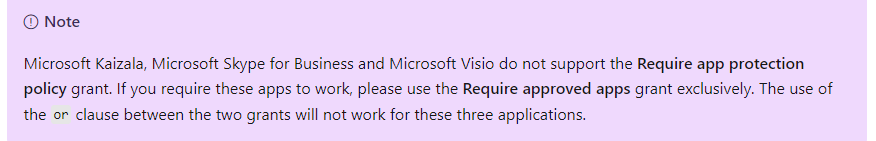
You need to include both of the access grant controls with an or operator. As shown earlier, Microsoft Azure is aware of which app support and does not support each grant access control.
So if an app like Outlook which supports app protection authenticates, the “require app protection” access grant policy will comply and when an app does not support “require app protection” policy but is on the approved app client list, the grant access control will be applied.
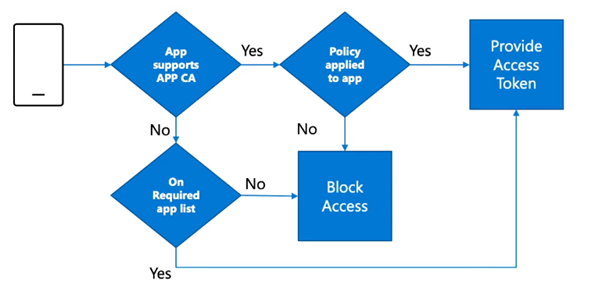
After we enabled the Conditional rule, we installed the Teams mobile App from the Company App portal. After a minute we received the first notification:

After we pressed installed, within a few seconds the Teams app was installed and ready for login. After we selected the proper account, we received another prompt to secure the app. At this point, App Protection kicks in.
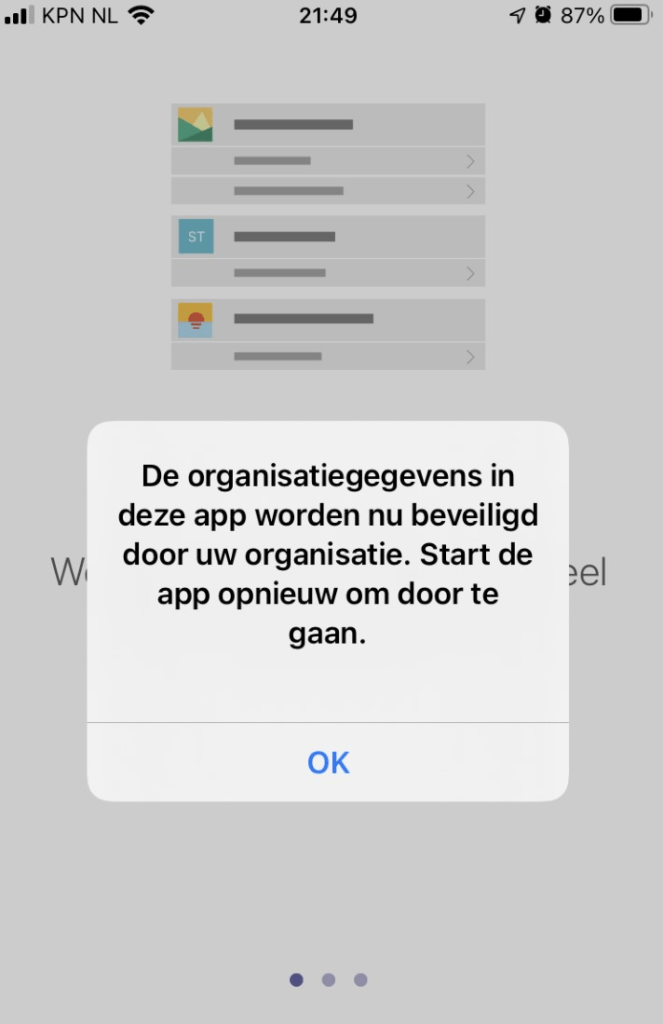
After I closed teams and opened it again, it worked and the App protection was applied.
Conclusion:
With a simple “OR” you can make sure, Teams will use the Approved Client app grant access policy even when Microsoft is telling us it does not work? Maybe a better word would be: supported?
Scratch that! As with the update of this blog today, Microsoft Teams hasn’t been noted anymore in this note: “The use of the OR clause between the two grants will not work for these three applications.”


Thing to note. Teams is now listed under the “Require app protection policy”, and has been removed from the disclaimer.