A couple of months ago, I had a conversation with a company that wanted to start with Entra Hybrid Join. I needed to convince them to skip the HAADJ and just go full Entra, aka Cloud-Native. One important part of that conversation was the need for drive mappings until they could move the data to SharePoint.
At first, I showed you how to configure those Intune drive mappings in the Deliver Us from Hybrid blog. I decided to remove that part and dedicate a unique blog to it so that both of these blogs could get the attention they need.
Let’s look at what I needed to come up with to convince the customer to go Cloud Native and still use some network drives by using the Drive Letter ADMX!
1. Intune Drive Mapping ADMX
How will we mount or remove drive letters to our on-premises file servers when we have not yet migrated the data to SharePoint? Are we going to map some old-fashioned drive letters using PowerShell? I guess everyone has deployed Adminless and Applocker, and of course, you made sure your Applocker policy will block PowerShell for regular users. What do we do now?
Assuming we all have the Azure Ad connect requirement in place to get SSO from our AADJ devices to our on-premises environment let’s go forth!
In some older blogs, I showed you how to ingest some ADMX templates to configure additional settings, so why not do the same for the drive mappings?
The only thing you will need is the Drive mapping ADMX and ADML file, which you will find here:
To make sure we can configure some drive letters on our device, we have two options at our disposal
- Intune Import ADMX
- CSP
1.1 Intune Import ADMX
With the latest update to Intune, we now have the possibility to upload our own ADMX to Intune.
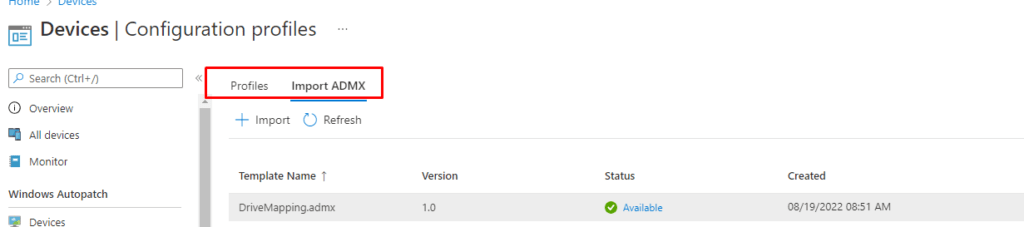
As shown above, you need to click on Import ADMX and select the ADMX and the ADML file you got from the zip file
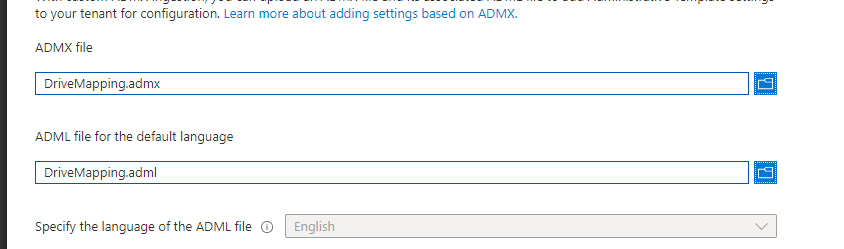
If importing/uploading the ADMX is giving you a failure, as shown below, you will need to take an additional step
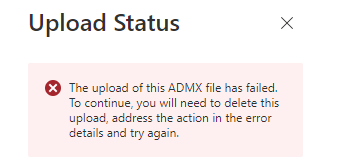
When this upload error occurs, you will probably need to import Windows.Admx first, as I am mentioning here:
ADMX Upload Error: Missing Microsoft.Policies.Windows ADMX (call4cloud.nl)
1.2 CSP Option
Of course, when we don’t want to use the new wonderful feature to import the ADMX we could also configure a good old CSP to make sure the ADMX is imported
OMA-URI: ./Device/Vendor/MSFT/Policy/ConfigOperations/ADMXInstall/DriveMapping/Policy/DriveMappingAdmx
Data Type: String
Value: content of the drivemapping.admx file
2. Adding the Drive Letters
Now we have added the required ADMX with a CSP or the new “ADMX Import” functionality in Intune, we need to configure some more settings to make sure we can map a drive letter on the device itself. Just like with the ADMX we also have two options available
- Imported Administrative Templates
- CSP
2.1 Imported Administrative Templates
After we have uploaded our ADMX and ADML files to Intune, we can create a new device configuration profile. To do so, we need to choose the “template” option on Windows 10 and later platforms.

When scrolling down the list of templates, we notice a new preview template has been added. As shown below, we need to select the “Imported Administrative Templates (Preview)” template.
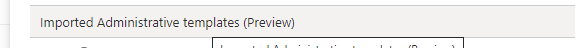
After we select this new template, we can start configuring all the drive letters we would like to mount by selecting the proper drive letter and configuring the remote path!
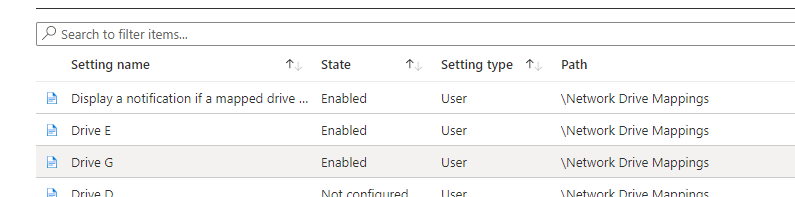
2.2. CSP
When you want to add drive mappings with the CSP option, you could create a new CSP, as shown below.
OMA-URI: ./user/Vendor/MSFT/Policy/Config/DriveMapping~Policy~DriveMapping/Drive_H
Data Type: String
Value: <enabled/>
<data id="Drive_H_RemotePath" value="\\fileserver\fileshare"/>
While waiting for the custom-made policy to apply, look at the registry to check if you already can find the ADMX policy inside the HKLM\Software\Microsoft\Policymanager\Admxinstalled registry key
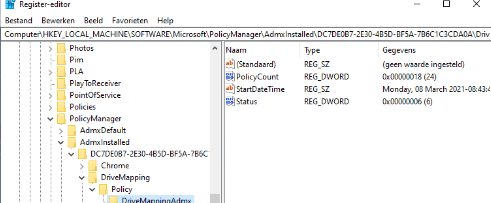
As shown above, the ADMX Intune drive mapping is installed without any problems, and within a few minutes, the drive mapping itself started showing up in the registry. HKLM\Software\Microsoft\Policymanager\Current\SIDId
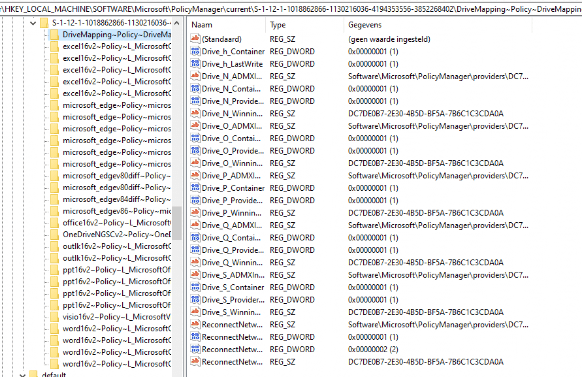
After logging off and logging on again, the drive mappings popped up and were ready for use.
2.3 Removing the Drive Letters with a CSP
When you want to remove some of the Drive Letters, please make sure you change “Enabled” value to “Disabled” instead of removing it or changing it to not configured.
OMA-URI: ./user/Vendor/MSFT/Policy/Config/DriveMapping~Policy~DriveMapping/Drive_H
Data Type: String
Value: <disabled/>
<data id="Drive_H_RemotePath" value="\\fileserver\fileshare"/>
Why? I guess it’s all about the tattooing issue still exist
https://call4cloud.nl/2021/03/the-device-with-the-dragon-tattoo
3. Solving the Red Cross and Disconnection Warnings
Okay, we have our drive mappings, but what about the disconnection warnings and the red crosses? Let’s fix it.
3.1: RestoreConnection
Please make sure you also add this CSP to make sure you don’t get any reconnection warning
OMA URI: ./user/Vendor/MSFT/Policy/Config/DriveMapping~Policy~DriveMapping/ReconnectNetworkDrivesWarning
Value: <disabled/>
Another possibility would be to deploy a PowerShell script to the devices with this content
New-ItemProperty -Path HKLM:\SYSTEM\CurrentControlSet\Control\NetworkProvider -Name RestoreConnection -PropertyType DWord -Value 0 -Force
3.2. Solving the Red Cross/Disconnection issue
Sometimes, you could end up with this red cross error. It looks like you can’t open the drive letter.
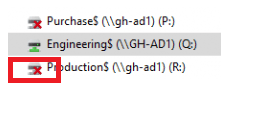
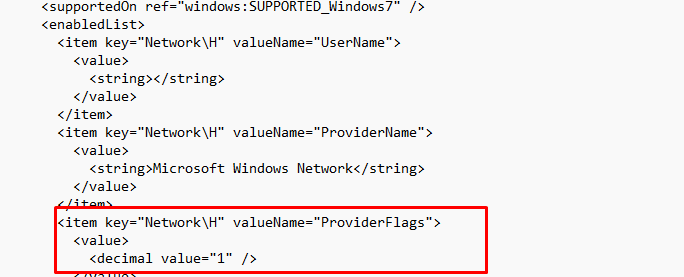
To solve this stupid issue, you must ensure the Network Drive ProviderFlags is set to 1. This “key” controls the recovery of network shares. When stored in the registry, your drive mappings will use Server Message Block (SMB) version 1. Again, there are 2 options to configure this setting.
If you have opened the ADMX file, you will notice I already have added these “ProviderFlags” for you! So you won’t have to.
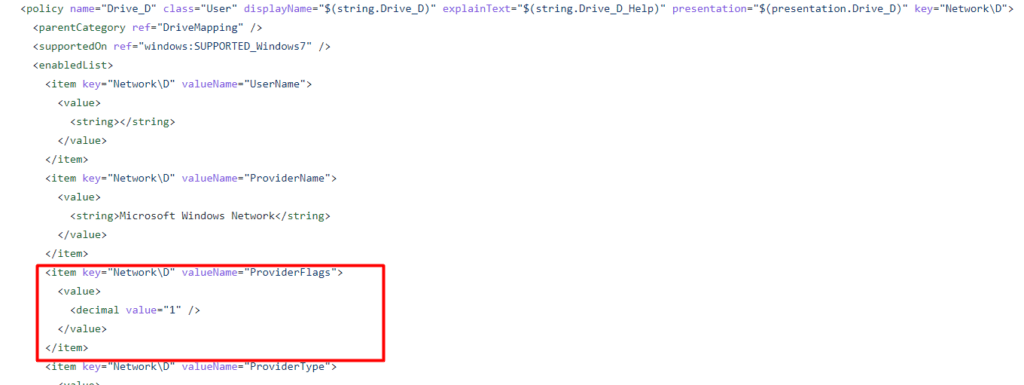
Please Note: It’s enabled by default, if you want to disable it please change the “Value” back to 0
Again, another possibility would be to create a PowerShell script to change this registry key. You will need to make sure it’s targetted at the HKCU
REG ADD “HKCU\Network\P” /v “ProviderFlags” /t REG_DWORD /d “1” /f
(change the P to one of the drive letters you are experiencing the issue with)
4. Making the Drive Letter Names more Beautiful
Totally forgot to mention this part. Looking at the drive label names… it doesn’t really look that nice, does it?
If you want to specify a nice name for it, we need to open the registry first and browse to:
HKCU\Software\Microsoft\Windows\CurrentVersion\Explorer\MountPoints2
You will notice, that all of your configured Drive Letters you define in the Drive Mapping policy show up here.
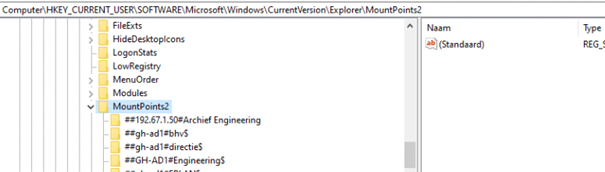
I decided to export them first
I opened the export reg file and added the _LabelFromReg with a nice name to each mountpoint.
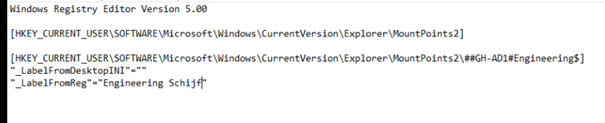
When you are blocking PowerShell you can deploy this reg file to your device by using this trick, you could even create proactive remediation to be sure the drive letters are always having a nice description.
If you don’t block PowerShell, it’s a lot easier of course. Just create a PowerShell script that is deployed to the user context
reg add “HKCU\Software\Microsoft\Windows\CurrentVersion\Explorer\MountPoints2\##servername#sharename” /f /v “_LabelFromReg” /t REG_SZ /d “NewLabel”
You will need to change the server name and share name to the value you have seen in the registry key
Result:
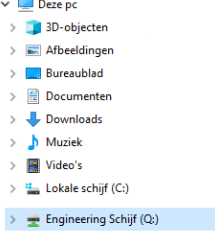
5. How to deal with those weird characters!
Of course, we all know that sometimes we could have some weird characters in our shared name. Luckily, spaces are not one of them, but unfortunately, the & is. Like an example “\\fileserver\engineering & research”. So, how do you deal with that? Luckily we could also add those in the CSP
& –> &
So let’s take our example and change the CSP, so it is going to work
\\fileserver\engineering & research6. Home Shares and the %username%
When you still need to map some drive letters to your on-premises file server, for the time being, you maybe need to map a drive letter for the user’s home folder.
I guess we all know the variable to make this happen when your home folders look like this \\fileserver\homefolders\rudyooms. When running the login script/GPO in the user context the variable to do so is %username%
But unfortunately this “could” be hard to do with the ADMX, unless you add something to each element

To make sure you can use the %username% you will need to add this expandable=”true” to each element in the ADMX you ingested!
Please Note: You could end up in a situation in which the devices suddenly start showing the Home drive to be connected to a SYSTEM folder instead of the user folder!
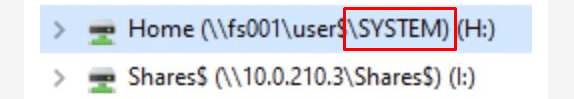
Luckily in the ADMX, I showed you, I already changed the ProviderFlags to 1. When you run into this issue, please check out the ProviderFlags value in your ADMX
7. Sharepoint Drive Mapping
I did some tests to see if it would also work when you want to map a drive letter for a SharePoint site, but unfortunately, it doesn’t (yet?) map the drive letters with the web protocol, so I needed to change some stuff… Go read the blog
https://call4cloud.nl/2021/05/drive-letters-the-demon-barber-of-sharepoint-street
8. Drive Mappings gone missing!
I guess I also need to add this part, as we have seen this happening from time to time. Let me tell you the issue first.
After migrating the data to SharePoint, we ensured we configured the existing values to be disabled. For 90% of all devices, this went totally okay! no problem whatsoever but on 10% of the devices, all the drive letters were missing.
After expecting everything we noticed that these users were made local admin by the local it department before. That’s totally not okay! Somehow the drive mapping didn’t show up in the explorer session of the user. It’s all because of UAC. Luckily Microsoft has a good article about this issue
Mapped drives are not available – Windows Client | Microsoft Docs
So for now we created the DWORD EnableLinkedConnections with the value of 1 in this reg key to fix it at this moment.
Set-ItemProperty -Path “HKLM:\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System” -Name “EnableLinkedConnections” -Type DWord -Value 1
Please Note: If this option arrives at Intune, I will update the blog
Conclusion:
Apparently, after talking to the wonderful Mark Thomas, He was the one who wrote the initial ADMX. So respect and hats off! He did an amazing job writing the initial ADMX in the first place.
In one of the blogs I am working on, I will explain how you could create the ADMX yourself… Creating a new ADMX with a simple HCKU register setting will be just a matter of minutes

When going full cloud, there is still a possibility you will need to make sure your users could access the old-school file servers. As I showed in the deliver us from the Hybrid blog, you can do so with SSO. But why not provide your users a nice drive letter until you can move all the data to OneDrive/SharePoint?



Hi Rudy, great article, thanks. There’s just one thing holding me back from using this. How do i make sure a user loses the drive mapping when he is removed from a group? Without making this manual proces which will be prone to error?
Hi,
Normally we also configure the opposite setting (multiple configu CSP’s) to disable/remove that drive mapping and assign it to a group with at that point no one In it. So each drive mapping to remove has a separate policy and assigned to a group
So when a user doesn’t need that drive letter anymore, we remove the user from the main csp and add him/her to one to remove it… It will cost you some time to set it up at first… but onceconfigured, you only need to remove and add the user to a group
Great article! Very nice solution. There’s only one thing that didn’t work: if the user manually delete the drive map, after restart, the drive map will not appear. Do you know any way to force the reconnection?
I do have an additional question. What if you want to push a network drive mapping, but it needs to be hidden?
Thats a good one… need to check if thats possible
Hi Rudy,
I am using your blog article to distribute a few drive letters. I have found out that when using a variable, the drive letter is not connecting at logon. It shows the toast notification that not all drives are able to connect. The drive stays disconnected until you click on it once.
This behavior changes when replacing this variable with the username inside HKEY_CURRENT_USER\Network\U -> Remotepath. So, I am thinking of making a PowerShell script to replace the %username% variable.
Do you have seen this behavior and perhaps have a workaround?
Hi.. Normally it should work, did you also read the part in the blog mentioning those red crosses?
We also experience this issue and the ProviderFlags are set to 1. So at every logon it shows as disconnected until clicked.
Same here. Provider flag being set to 1 does not make a difference.
Really nice and clever solution.
If I’m following up you’re using the new features for AzureAd only to get a kerberos ticket from adconnect?
What’s the advantages vs using a script with remediation or a script wrapped in a win32 with proper custom detection?
Hello Rudy,
Great article, i’ve waited so long for this.
One question, we are in a transition between AD en AAD, when all data is migrated to SharePoint/Teams we want to remove the mappings, how can we arrange this?
When importing into intune, i get the error namespaces Microsoft.Policies.Windows does not exist and must be uploaded before?
I have no idea where even to begin.
Do you have the same issue with this admx
https://call4cloud.nl/wp-content/uploads/2022/08/DriveMapping.zip
or this one
https://call4cloud.nl/wp-content/uploads/2022/02/DriveMapping.zip
They both give the same error.
Error Details
ADMX file referenced not found NamespaceMissing:Microsoft.Policies.Windows. Please upload it first.
Thanks for the help.
Hi… Thats odd… I tested it multiple times from different devices in different tenants. Did you tested it with only 1 tenant or?
I am noticing the same error… working on a blog with the fix
Rudy,
Any update on the fix for the issue “ADMX file referenced not found NamespaceMissing:Microsoft.Policies.Windows.”
Thank you
Yep… this blog https://call4cloud.nl/2022/10/the-school-for-admx-import-and-evil/
The fix is simple – the ADMX policy is missing its dependencies. You must first upload windows.admx/adml (e.g. from a DC at C:\Windows\PolicyDefinitions\). If you open the drivemapping admx, you’ll see this mentioned on line 4.
Rudy, this is a fantastic blog article and I was able to get a device to successfully map a network drive using Intune. However I am struggling how to write this as a remediation task. Would you have any insight into this?
Hi.. which part of it do you want to move a pro active remediation task?
What would be great would be to query active drive letters as a current user, then if the drive letter doesn’t exist make sure to map that network drive once again. Perhaps I am over thinking it, I just get worried if drive letters disappear for my clients 😉
Thanks,
Ted
Rudy,
It would be great to have a remediation task that would look for a mapped network drive. If the path exists, don’t do anything. However if it doesn’t exist, map the network drive. Is this possible or are remediation tasks only within system context?
Thanks,
Ted
Hope someone can help.
At first thanks for the nice tool and the good tutorial.
I have a Synology
I make a Connection from synology to my AzureAD
My Azure-user can map drives with their Azure-User-Account
I added the Mappings.admx an test it – the Test-drive is mapped after a reboot – but the user need to type his username and passwort.
is this normal at the first mapping?
I understood it so that he device-configuration is made with user credentials so i think that users did not need their username and passwort for mounting the drives
To have sso, that device should have been aadj (nas)
Hi Rudy
Applied the ADMX, configured the shared drive via Imported Administrative Templates. Did sign out and signed back in but unable to see the drives. Any ideas please?
Is the user a local admin on the device?
Hey I am having the same issue. And yes I am a local admin and trying to deploy to my own device
Hi Rudy,
Bit of a strange one for you. I work in a school and we have a server that is designated for the students with two drives being mapped when they logon, one just a general shared area and the other being the students home folder. Using DriveMapping the map to the general shared area works fine, no issues with this at all but the map to the students home folder always ends up showing the red cross irrespective of what I do, I have even entered the relevant registry update for the drive letter we use and I still get the red X. Obviously if I click on the mapped drive it browses it without any problems so I cannot lie, I’m very confused as to why I still get the X, any ideas?
Cheers
I have the same issue. No matter what I do, the drives still have the red X. They work fine, just X every time user logs in. NBD, I think people pretty much know to just click them, and they’ll gain access
Or better yet, they’re not the using on prem file servers anymore! That would be ideal.
i don’t seem to be able to get this to work at all. I see the registry entries where they’re supposed to be, but no drives ever map. I had to go the CSP route to get the ADMX ingested b/c simply creating an admin template from the imported ADMX never got me through that first gate.
What group do I apply your “Imported template” config profile to? I’ve tried device and user groups.
My config :
Azure AD services is activ. There is no local AD server.
The On-prem file share server is connected to an S2S VPN and is a device in AD. Devices in the same network as the on-prem server can easily connect.
When working from home, the clients use an AZURE VPN client and they can ping the on-prem server on the DNS name.
After deploying the admx en mapping with CSP are the drive letters available.
At the first connection time, there is a request for a user and password. After entering the same username and password as the current user, the connection is established. And you can browse the folder.
After a reboot, i received the error “Microsoft Windows Network: The local device name is already in use. The connection has not been restored”
What did i do wrong?
I have the same issue. How did you resolve it?
Is there any way to do this with a custom Username and Password for authentication?
Problem ist that the AzureAD Users are not able to authenticate the drive connection, so we use a local user for that.
We have created an EDS (Entra Domain Services) environment that works perfectly fine, even with Azure AD joined devices.
We have a scanner that stores scans which is accessed using a local account on it. Entra domain services looks like it would do it, but also looks overly complicated. Do you have a way to add the local credentials to credential manager?
Is there an option for the “Use first available” drive letter?
We have multiple teams all with a the same letter mapped but a different path.
If someone works in both teams they get both shares but the second one gets the next letter automaticly.
Manually keeping a list of who gets what letter and share is impossible, it’s thousands of people and dozens of combinations of teams.
Did you every find a solution to this?
Hi Rudy,
I have deployed this in my lab. It works perfect.
Just 1 question
When I make a network mapping manually using (net use) , the ProviderType gets the hex value 20000 or 131072 dec
When I make a network mapping using the admx , the ProviderType gets the hex value 2000 or 8192 dec
Is this meant to be 2000 or could it be a typo?
thanks,
Tom
Hi Rudy, this is great stuff, thanks so much. Any way to have a drivemapping only present when a user is in the office? We disallow SMB over our VPN, so would be best to not have the driveletter present at all when out of the office.
Anyone seen this issue?
“S:\” is unavailable. If the location is on this PC, make sure the device or drive is connected or the disc is inserted, and than try again. If the location is on a network, make sure you’re connected to the network or Internet, and then try again. If the location still can’t be found, it might have been moved or deleted.
The strange thing is a just see the network drive, i get this message when i try to copy files to it.
Hi, I’m trying to import the admx and adml files into intune but it fails with
The upload of this ADMX file has failed. To continue, you will need to delete this upload, address the action in the error details and try again.
Error Details
ADMX file referenced not found NamespaceMissing:Microsoft.Policies.Windows. Please upload it first.
Does anyone know how to correct
https://call4cloud.nl/2022/10/admx-when-nature-calls/
Found the answer from another Blog post by Rudy and confirm it works
https://call4cloud.nl/2022/10/admx-when-nature-calls/
Hi, great work with this
I’m finding an issue where if – after a successful mapping – the user right clicks and disconnects the drive it doesn’t get remapped?
HI tehre
I am having issues mapping my drive through to \\servername\%username%$ – i have tried the instructions above but cannot get it to connect to the share using this address
What are the requiremnet for AD Connect, would you be able to elabarte here please.
“”Assuming we all have the Azure Ad connect requirement in place to get SSO from our AADJ devices to our on-premises environment let’s go forth!””
I have deployed this custom ADMX with a couple of drive letters, however now I want to change the path to one of them.
Is there a special sequence such as disabling the drive in Intune first, or do I simply update the path?
Thanks!
Did you figure this out?
Hi Rudy.
Great article but still got one problem, everytime the user logon the pc en click on the drivemapping the popup screen apears to fill in the network credentials and password. Is there a solution for it? (3.1 and 3.2 won’t solve the problem)
TIA,
Harmen
I assume the requirements are met to implement this with sso? (azure ad connect/entra connect) to make sure the onpremises password hash of the users are the same on the entra joined device?
Yes it is.
When I fill in the network credentials and click save de mapped drive connects after a reboot. But when the password change of the user the network credentials screen pops up again.
You shouldnt need to fill in the creds…. if you are using azure ad connect, you will have sso… but if youare using windows hello… yeah you will need to make sure you enable cloud trust also….
And please make sure that if connected over a VPN you add the IP address pool for the VPN to the Named Locations as Trusted IP ranges in Conditional Access. Also Trust your office LAN IP ranges if no VPN is always on.
Is the .admx file supposed to have ProviderFlags twice? One is set to 1 and one is set to 0 for each drive letter.
Hello colleagues,
Even this thread is a bit old but still popular 🙂
I hope someone could help me in the following scenario:
For some reason the removing network drive mapping doesn’t work for me.
I tried it on few Windows 11 machines and the outcome is the same – drives stays mapped and visible in Explorer.
The registry values (Computer\HKEY_CURRENT_USER\Network\) were set to NULL strings or 0 rather than deleting them.
https://i.imgur.com/LgNrAgy.png
Also it doesn’t work if I have a manually mapped network drive, which I need to remove (substitute) with another UNC path.
Thanks in advance!
Regards,
Andriy
Hi Rudy, Thanks for the great blog post – old but still very valid and helping us out loads. One thing I may have misunderstood is the OMA URI settings which contain a tilde in them like this one:
./user/Vendor/MSFT/Policy/Config/DriveMapping~Policy~DriveMapping/ReconnectNetworkDrivesWarning
My setting:
OMA-URI Settings
Name: ReconnectNetworkDrivesWarning
Description: Disable ReconnectNetworkDrivesWarning
OMA-URI: ./user/Vendor/MSFT/Policy/Config/DriveMapping~Policy~DriveMapping/ReconnectNetworkDrivesWarning
Data Type: String
Value:
Do I have the data type wrong?
Or am I supposed to be replacing this DriveMapping~Policy~DriveMapping with some unique values from my deployment or how is it supposed to work.
Currrently this is throwing up an error for all deployments of the setting.
Setting error
SETTING
ReconnectNetworkDrivesWarning [./user/Vendor/MSFT/Policy/Config/DriveMapping~Policy~DriveMapping/ReconnectNetworkDrivesWarning]
STATE
Error
SOURCE PROFILES
Source Profile
Drive Mapping – ReconnectNetworkDrivesWarning Off
ERROR CODE
0x87d1fde8
Many thanks for your help on this one.
Andy
Hi, how would you manage the access to the drives, would you have to create multiple ADMX Config Profiles per department?
G- All users have access
H – HR
J – Finance
K – HR & Finance
L – Developers
Whilst I could map all drives to all users, they obviously would not see any folders due to permissions, but I assume they would have a long list of drives they couldn’t access?
I assume the only way round this is to create various ADMX Config files that allocate the correct drives based on Entra ID groups which have the correct users from the correct departments in those.
Hi Rudy,
I am using a REG file to import the labels at startup. This is to ensure that they remain static and won’t change when the network drive changes/re-apply etc. However, I cannot get it working with the %username% variable to map a label to the appropriate homedrive of a user (the key is MountsPoints2\the exact username). The cmdlets of Windows Registry simply do not allow the user of variables in the key name (only in values using _EXPAND_SZ).
Do you have any thoughts on this or have seen this before?
Kind regards,
Toine
I am strugging to get this going using the %username% field which is making it pretty hard fo rme to progress. I have followed all the instructions as listed in this article but with no success.
Hi.. so we are 1000% sure the providerflags or/and extendable true is configured?
This was a great help in getting drives deployed via InTune on PC’s with no mapped drives. I am having somewhat of an odd issue that I can’t seem to figure out though. For example, if I have drive Z: mapped to \\fileserver1\folder1 and I want to change the policy to point Z: to \\fileserver1\folder2 – it will fail to re-map. Any fix for this? Has anyone else had this issue?
Hey Rudy,
We have the same ADMX Intune Config Policy deployment for our drives, and it works for the most part. But recently we’re seeing weird issues such as:
– Connections show, but then display the error ‘the local device name is already in use’
– Connections don’t show in File Explorer, but are present in the Registry ‘Network’ location and Mountpoints2. Also show when you go to Map Network Drive, you can see the drive there.
Have you found what causes these issues?
Amazing work as always!
Hey, since Administrative Templates are not working anymore, how is this done via settings catalog? I’m somehow not able to find the settings, even though I have imported the admx files correctly.
Hi Rudy,
Thank you for writing this. I’m thinking of ways to implement drive mapping across my devices at work via intune. This looks like a great solution except I’m concerned about you mentioning this is SMB 1. Unfortunately if that’s the case, it would be too risky for me to deploy. Is there any way for this to work with newer SMB protocols?
Thanks,
Con
Does %username% include the domain such as:
user@company.com
or it is just the username:
user
Because I need it to be the latter, just the username.
Hello, is this method still the “best” method to add drivemappings through intune?
Unfortunately, using the Admin template has been retired in Intune. This did work well for our sister company for a couple of years; however, we’re no longer able to utilize this method. We switched over to using a remediation script as a permanent fix, I have some references for the base version of that script below.
I think you are mixing up 2 things.. yes admin templates are going to be retired… but.. Imported Administrative templates (Preview) not 🙂 (which is used for the folder drive mapping)
would be weird that they were ditching the import admx feature 🙂