This time a very short blog about an Intune Settings Catalog profile and the Error Code 65000. After reading a question about an issue with disabling the News and Weather Feed on the Microsoft Technet forum I decided to dedicate a blog to it.
Error 65000 with Settings Catalog – Microsoft Tech Community
1. The 65000 error
So If you don’t know the answer immediately, test it yourself! I made sure I configured the same News and Weather feed setting inside my test tenant. After I created the new policy, I manually synced the two devices to determine if I would end up with the same error. After the sync was completed, I got 1 working device and 1 with the same Deployment Status Error.
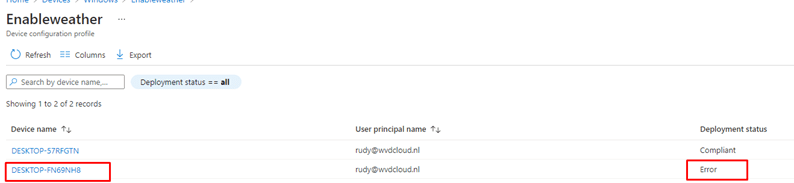
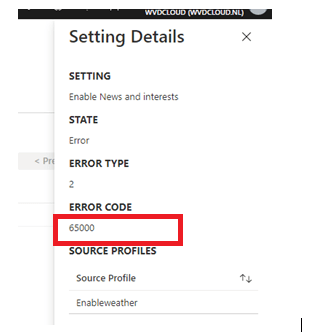
The screenshot above gives us the error code 65000. So what does this mean? Did searching Google for Error code 65000 not show anything useful? Let me get my shovel to start some troubleshooting!

2. Troubleshooting
When you need to start troubleshooting, we normally need to take a look at these 2 logs.
- Intune Management Extension log (IME)
- DeviceManagement-Enterprise-Diagnostics event log
So which one do we need If we need to troubleshoot Intune Device configuration profiles? Correctly answered, we need to take a look at the devicemanagement-enterprise-diagnostics event log! The Intune Management Extension log file is a perfect place to start when troubleshooting other stuff like application deployment failures.
Let’s open MMC and add the DeviceManagement-Enterprise-Diagnostics Event log. Sync the device from the Intune portal and monitor the event log.
Within a few minutes, you will be getting some more information. Please note that sometimes Error 404 could give you some misleading information like I am showing below
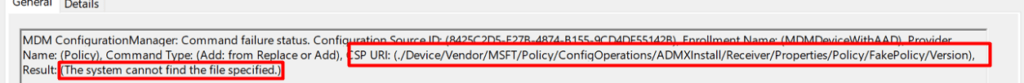
Looking at the error “The system cannot find the file specified” it looks like it telling us it couldn’t find the ConfigOperations/ADMXInstall/Receiver/Properties/Policy/Fakepolicy/Version but in reality, (to quote an MS engineer) “The “FakePolicy” policy was created to detect if a certain patch is present on Windows, and will be removed automatically once we’re sure most machines are ready to consume the new ADMX versioning feature”
So, here is a piece of quick advice: when you notice this FakePolicy error, just skip it! Let’s dig further as we have more 404 errors to look into
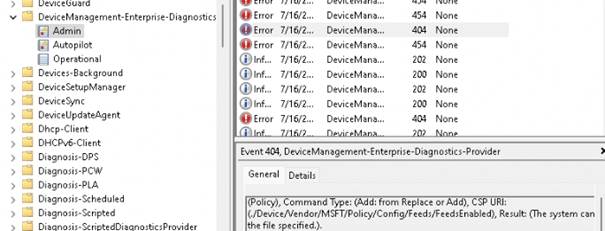
As shown above: The system cannot find the file specified. So what does this mean? It looks like it’s missing something… but what? The first place to start would be (in my opinion) the registry. So I did because I could compare 2 devices.
One was working, the other one was giving the 65000 error. Open the registry and open the hklm\software\microsoft\policymanager\default folder
Normally, when you need to define some settings, the corresponding folder in the policymanager\defaults needs to exist. So let’s check out the device which is giving us the 65000 error
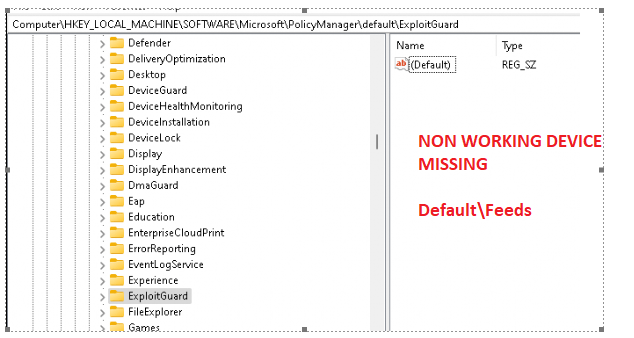
As mentioned earlier I also got a working device. Let’s open the registry on the working device and compare them!
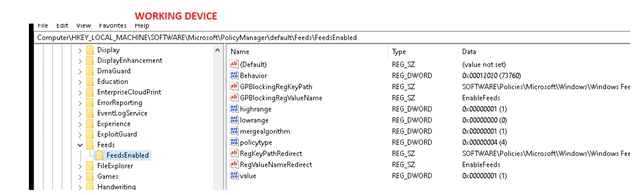
As shown above, the working device has the required registry keys configured. But why doesn’t it exist on that other device? Normally all working Windows build-in ADMX settings (not ingested ADMX files) should be available inside the c:\windows\policydefinitions folder
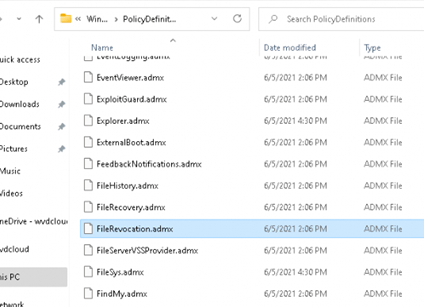
As you probably noticed in the picture above, the Feeds.admx file doesn’t exist. I can tell you a very long story or just explain it.
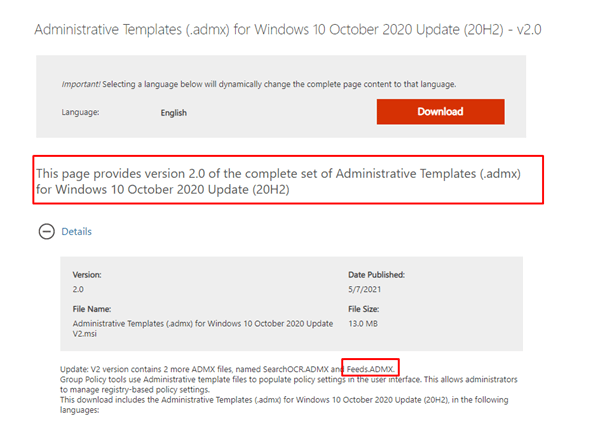
So you need to make sure your devices are up to date (check part 3) so they have the latest ADMX files installed. Otherwise configuring settings in Intune will not be enabled on your devices because it’s just missing the information on how to do so!
And if you are still experiencing these kinds of errors, please make sure you install the KB5005101 update.
This update will enable over 1400 new mobile device management (MDM) policies. With them, you can configure policies that Group Policies also support. These new MDM policies include administrative templates (ADMX) policies, such as App Compat, Event Forwarding, Servicing, and Task Scheduler.
3. A Licensing Issue?
When talking on the TechNet Forum and looking at the shared Event log, we determined that something else was going wrong on his devices.
MDM PolicyManager: Policy is rejected by Licensing, Policy: (FeedsEnabled), Area: (Feeds), Result:(0x82B00006) Unknown Win32 Error code: 0x82b00006.
So it really looks like this Settings Catalog Policy is only supported on Windows 10 Enterprise/Education devices? Even when the Microsoft Documentation of the CSP is telling us it is supported on Windows 10 Pro devices
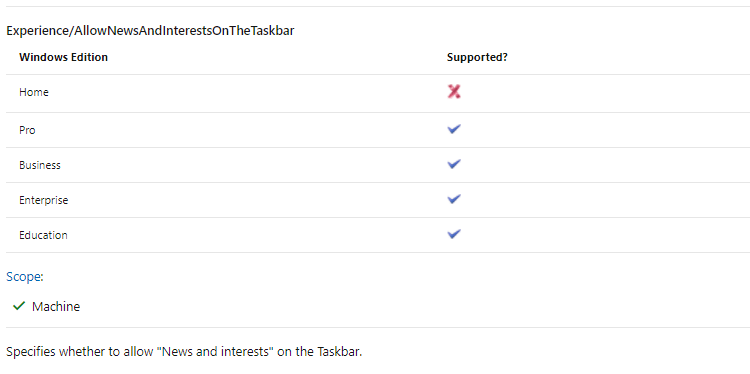
But I guess it all depends on which Windows 10 build version you are using. A lot of settings aren’t supported on Windows 10 20H2 in combination with Business licenses. A lot of these settings catalog features will only be available in 21H2!
Please Note: Even when the applicability filter is removed, you could still run into some issues when your device has the Business SKU instead of the Pro SKU. I am describing it in this blog below
https://call4cloud.nl/2022/06/cve-2022-30190-and-the-city-of-thousand-solutions/#part3
4. Windows 10 or Windows 11
This blog was written while Windows 11 was not yet globally used. Today I got a response to that same question from the TechNet community.
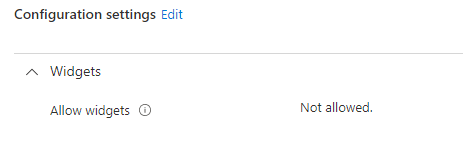
This response immediately intrigued me as I had not noticed this issue with Windows 11. After looking at the question, I quickly realized that when you need to remove the News and Weather feed in Windows 11, you will need to disable the damn Widgets! You could do this manually by flipping the switch, as shown below.

Another possibility would be to use Winget to install the Windows web experience pack with this PowerShell Winget oneliner!
winget uninstall “windows web experience pack”
When you have Windows 10 and Windows 11 devices, you want to make sure each Settings catalog profile arrives at the proper device. Otherwise, you don’t want to end up with Device configuration policy errors in Intune.
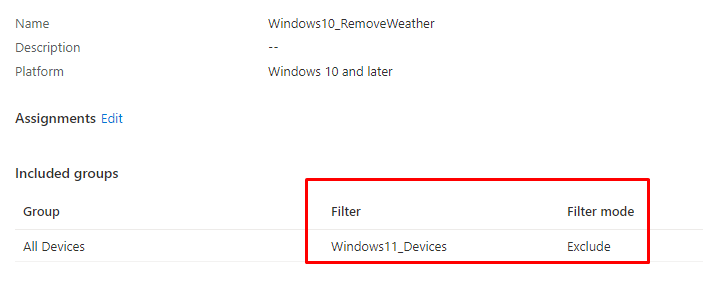
Filters…Filters…Just use those wonderful filters!!!!! Let’s create a filter, as I am showing below.
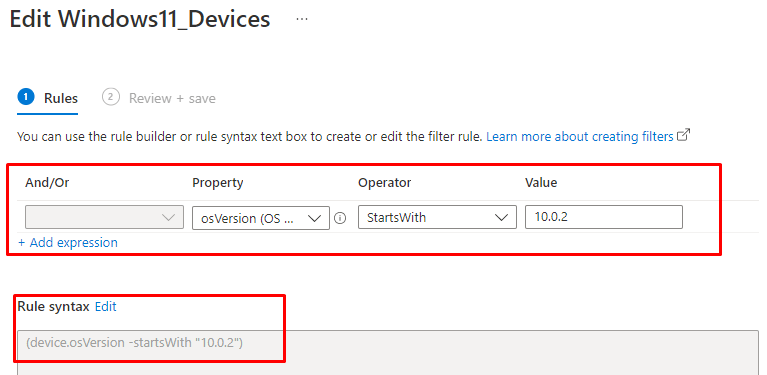
After this Filter has been created, you could change your existing Windows10_DisableNewsAndWeather policy to ensure you are “excluding” Windows 11 devices with the Filter above!
Now we are sure, this policy will only target Windows 10 devices, let’s create an additional Device configuration policy to disable (not allow) those evil widgets!
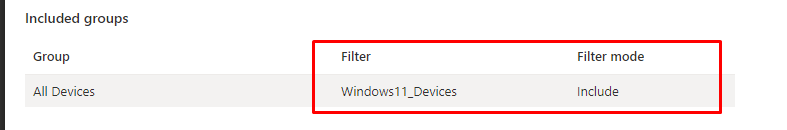
Just like we did with the Windows 10 policy, we are going to use a filter, but this time we are making sure the filter mode is set to “Include” instead of “Exclude”
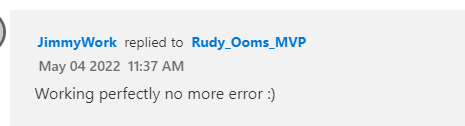
After changing these Device configuration policies you will notice it just works!!! no more errors
5. ADMX Ingestion flow Bug?
In the troubleshooting part, I explained why the ADMX must be on the device for the setting to apply successfully. Sometimes, ingesting an ADMX can cause weird behavior.
The device will normally perform the ADMX ingestion BEFORE applying the policies but sometimes it just doesn’t. As shown below the ADMX ingestion is done AFTER applying the Device configuration policy
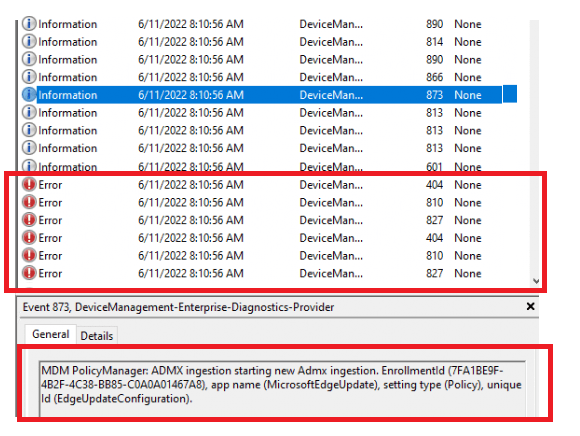
Luckily when the device performs a sync again all is fine and the setting will be applied successfully. So when noticing this behavior, just perform another sync! I guess good old Mike has us covered again!
6. Windows Pro Vs. Windows Business SKU
We also need to be aware of some differences in the SKUs because sometimes, even when it should be working on Pro, it doesn’t mean it also works for Business, even though the Microsoft Documentation tells us otherwise!
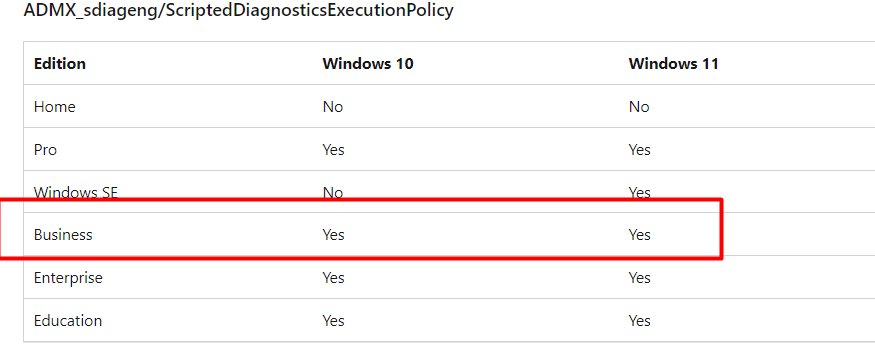
The above ScriptedDiagnosticsExecutionPolicy is one of those that could be failing you. I am also mentioning it in the blog about dealing with the “Follina” bug
CVE-2022-30190 | Follina | MSDT.exe | Applocker | Intune (call4cloud.nl)
Summary of the blog: Microsoft is aware of this issue and they are working on a fix!. Hopefully, it will be fixed in the near future!
7. Edge/Office ADMX
I guess I am still not done, as you could also run into some weird rare issue in which the Intune build-in Edge ADMX could give you the same issue.
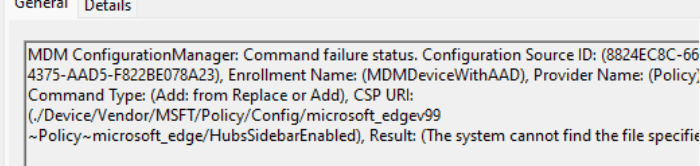
This registry key (microsoft_edgev99) and the ADMX should be automatically delivered by the ADMXInstall CSP so that later on, the specific settings can be deployed
./Device/Vendor/MSFT/Policy/ConfigOperations/ADMXInstall
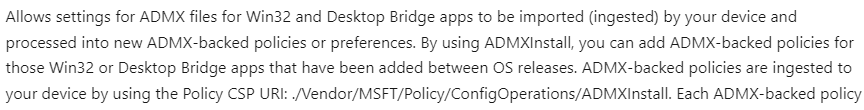
But sometimes, it just doesn’t work as you expected, and you will end up with a device without that Policymanager\Admxinstalled registry key
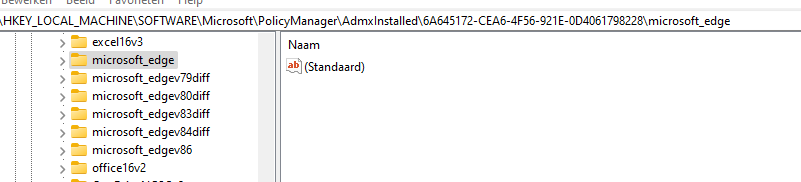
Besides this missing registry key, the ADMX would also be missing from the Ingestion folder : c:\programdata\microsoft\policymanager\ADMXIngestion
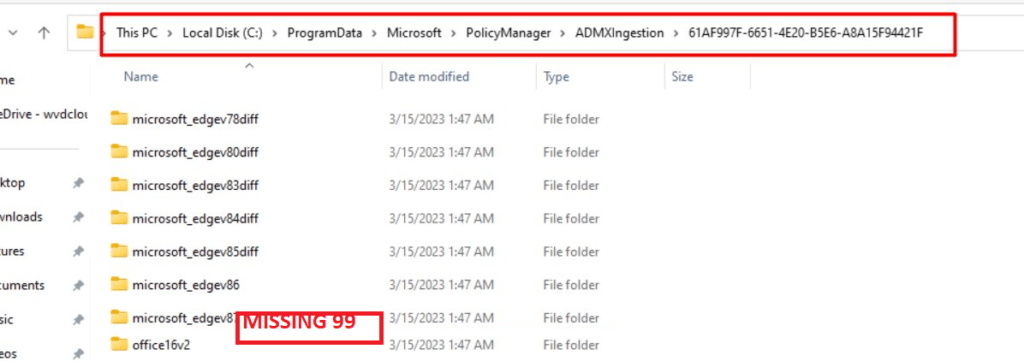
If you have spent a fair amount of time waiting and you want it to fix it now get yourself a copy from the ADMX and the registry key I mentioned from a working device and place them on the not working device…
1) KEY_LOCAL_MACHINE\SOFTWARE\Microsoft\PolicyManager\AdmxInstalled\GUID\microsoft_edgev99 2) C:\ProgramData\Microsoft\PolicyManager\ADMXIngestion\GUID\microsoft_edgev99
8. Excluding Policies
If you have a question… just post it on Reddit. So did he!
Intune AV Policy Error 65000 : Intune (reddit.com)
He was experiencing the same error, 65000, as mentioned in this blog. The funny thing was that the: “excluded paths” was not giving him issues only the “excluded Processes” setting.
After some messages sent back and forth, I asked him to remove the setting that was giving him the error from the existing Antivirus Endpoint Security Policy
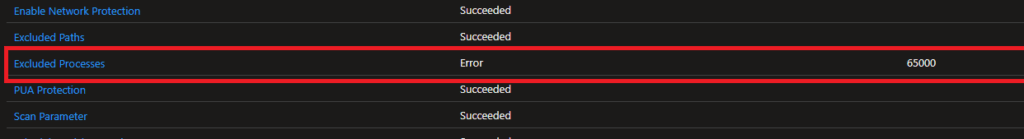
After removing the “excluded Process” and dedicating a separate Antivirus Exclusion policy to it the error 65000 was gone!
Conclusion:
Knowing how to troubleshoot is necessary so you can come up with a good answer in no time. But then again, a lot of settings inside the settings catalog are telling us you need to have the insider preview installed so why not give us a little hint about this one?
I guess error 65000 just means Windows doesn’t know what SYNCML was trying to accomplish which could be caused by a lot!




Thanks, appreciate this. Indeed MS take the biscuit with each change/update of the OS. Some things work today and stop tomorrow. Just got a 65000 error and this came in handy.
Rudy – I’ve noticed that this error definitely happens due to missing the admx-injested file. Intune appears to try to apply the settings before the admx-injestion occurs (in a separate payload). So the order is in reverse. After awhile though, Intune will re-try the settings and then they will work since the ADMX is now there.
Hi… true… noticed the same a while ago… but totally forgot to add it to the blog 🙂 … will update it today.. thanx for bringing it up
Thanks for your blog post. It help me for a windows 11 pc.
Too bad we have to block widgets and not just shitty msn news.
Nice to hear :)… hehe msn news… always lovely 😛
I’m seeing this issue while trying to configure OneDrive KFM with Intune. Even though I see event 873 in the event logs, but it never seems to come down. My test system is Win10 21H2 Enterprise. I’m about to update to 22H2 and see what happens.
Well, after updating to Win10 22H2, I’m not seeing the 404 and 873 errors about the OneDrive policy, but it’s still not bringing the ADMX down, or configuring OneDrive.
So the onedrivengsc isnt listed here? Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\PolicyManager\AdmxInstalled\ and also nothing in the
Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\PolicyManager\current\device\
Did you targetted devices or user settings?
So, it’s gotten interesting. I’ve tried targeting both user and device, but the most recent attempts have been device. I tried turning un-assigning the policy for a few hours, then re-assigned it. Prior to this, the OneDrive taskbar/tray icon was blue with a not config/not signed in slash, but was gray while the policy was off. Also, during all this, Teams did not automatically sign in. After I re-assigned the policy, Teams auto logged in and then OneDrive signed in automatically.
I did a fresh start on this system, and left the policy assigned to my test device group. And thus far, the settings haven’t taken effect, even though they show as applied in Intune. No more 65000 errors. I do see OneDriveNGSC in both registry locations. (I am currently doing Hybrid Join, but moving toward AADJ).
Almost sounds like an existing lingering domain gpo is giving you issues… what happens when you try to do the same but this time with an aadj device? so we an rule out any issue with haadj
I was thinking along the same lines, and re-provisioned another device to AADJ. Initially, saw the same issues, but realized Win10 was very out of date. Updated it to 22H2, and OneDrive did finally sign in automatically, but the rest of the KFM config has not applied. Even after several manual syncs from both the client and portal side, and multiple reboots. Kind of wondering if I need to separate the auto sign in to its own policy, and have the rest of KFM in another.
I imported to Intune and applied to a device a GPO backup that denies read/write to removable disks. The error 404 shows up in the eventvwr, with the error “./User/Vendor/MSFT/Policy/Config/ADMX_RemovableStorage/RemovableDisks_DenyRead_Access_1”.
The ADMX file “RemovableStorage.admx” does exist in the C:\Windows\PolicyDefinitions on the target machine, and the “RemovableDisks_DenyRead_Access_1” configuration can be found inside that file (among other configurations from the same file that are also reporting the same error).
Any clues on what may be happening?
I had the same issue with Excluded file type. I fixed it by putting each excluded file type on a seperate line. So instead of x|y|z I did:
X
Y
Z
And then it worked.
In case anyone needs this.
Thank you for this publication because this error has appeared on several devices monitored from Intune MEM. greetings https://www.enieto.com
Hi, i got this issue but cant find what is missing because there is no ADMX file for this. The problem i got is with the /LocalUsersAndGroups/Configure. I got many machines upgraded, all in the same build, and it works fine in 20/200 devices. I checked those items in the regedit, and its present in both machines (the one that works and the one that fail). The Account protection configured only ADD(replace) some users in the localAdmin Group.
It should be easy, but cant find why its failing. Any idea?
hello
we have this problem with applying 365 office apps security baseline.
Is there a solution for the admx-injestion ?
is that setting done by another parameter?
i’ve waited for 3 days and all settings in the baseline give error 65000
thank you
I also had a same issue for Edge policy where Admx is missing. So, injected admx from a working machine through custom OMA-URI and deployed to test devices and it got success after ran a sync.
./Device/Vendor/MSFT/Policy/ConfigOperations/ADMXInstall/microsoft_edgev80diff/Policy/microsoft_edgev80diff
I see it got updated in registry as well so no need to copy and deploy the registry from working device.
Will target to the 1000+ devices to see how it goes :).
Thanks,
Bala
life saver Rudy, Could you guide, I see in my case ADMx edge & feeds.admx files and related files are missing
How to target to the devices ?, by default these should apply on enrollment right ?
Hello,
I work in financial sector and we had exactly the same issue describe in point 7: Edge / office admx ingestion problem.
This drive me totally crazy for month and we finally found the root cause :
All settings related to office had 65000 error status. On the workstation side, we clearly got 404 ID in event viewer : file specified cannot be found.
We found a workaround where we duplicate configuration profile affected and assign to new AAD group that contains users reported in error. But once we assigned the policy in production though Policy Set, ADMX ingestion issue appeared again.
And that was the problem … POLICY SET ! Once we remove Policy Set feature for assignment and directly target policy though classic policy assignment, no issue reported.
Policy Set feature still in preview, maybe that’s the point. I don’t know how this can cause admx ingestion problem. However, I do not recommend using this feature in production environment.
I’d like to add that since this article seems to be referenced often, I too was having the 65000 error message; but as it turns out – it was because some of the usernames and groups that were part of the policy had been disabled; resulting in the accounts not being able to resolve on the local endpoint. So in other words. check that the username(s) and/or group(s) you are using are licensed, enabled, and valid.
Hey, I created a filter for the Windows 10 policy to disable Feeds, with an extra filter to exclude Windows 11 devices. The 6500 error is gone now for user accounts, but not for system accounts. Do you have any idea how I can fix this for system accounts too?
Thanks a lot, this was a very helpful blog. I’m having this issue related to some other InTune policies on Windows 11 Pro.
Hello
we got the same error code to one of the “User Rights” policy “Allow Local Log on” . And due to that user is not able to login the system with any account. Let me know how to fix it