This huge blog will be about deploying Quality Updates, the Update Health Tools, and an alternative method to deploy the Windows Quality Updates with proactive remediations within an hour!
Of course, with the latest Printer Nightmare issue, we needed to update some devices quickly. Even with the update installed, you are still vulnerable, and you will have some issues with label printers with this update. But that’s not what this blog is about.
1. Introduction
By creating a Windows quality update preview policy, you can expedite the installation of the most recent Windows security updates as quickly as possible on devices you manage with Microsoft Intune.
Expedited updates can be deployed without pause or edit your existing monthly servicing policies. With expedited updates, you can speed up the installation of quality updates like the most recent Printer Nightmare Update or another out-of-band (OOB) security update for a zero-day flaw.
To speed installation and expedite updates, use available services, like Windows Notification Services (WNS) and push notification channels. These services will deliver the message to devices that there’s an expedited update to install. This process enables devices to start the download and install of an expedited update as soon as possible without having to wait for the device to check in for updates.
So how does it work, I will try to explain it step by step.
- We will start by creating a Windows Quality update (expedite)policy profile in Intune to start deploying/expedite the Windows Quality Update.
- When the expedited policy is created, it will be processed by the Windows Update for Business Deployment service.
- After the policy has been processed by the WUfB-DS , WNS will make sure that the Microsoft Update Health Tools will receive the expedite policy.
- In the policy you created earlier, you configured the expedite restart deadline and triggers. Windows Update will honor these settings and will configure them.
- The policy will also trigger Windows Update on the endpoint to discover Updates for the endpoint.
- After scanning for updates, the update you specified in the expedite policy will be downloaded and installed.
- On the device, Windows Update will prompt the client to restart their device exactly like you configured it to within the deadline settings earlier.
- The Microsoft Update Health Tools will monitor the update progress and will report back the status with the use of telemetry (More on telemetry later)
- When the status is reported back, you can monitor it in Intune. The Windows Update settings on the device itself are changed back to those that were previously configured in the WuFB update ring. Isn’t that nice?
2. Configuring the Quality updates
Before I configure the quality updates, we need to make sure the Windows update rings are set to the semi-annual channel.
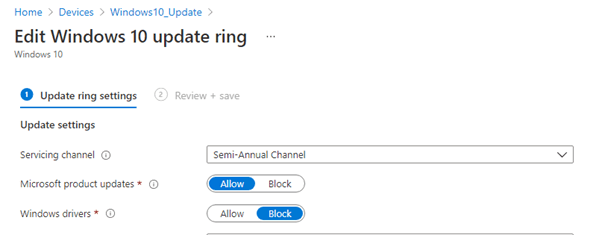
Because expedite simply doesn’t support additional channels (at this time)
Now I am sure, the quality updates are going to be deployed to the devices I started with by creating a quality update profile. It’s very easy to do… just create a quality update profile and select the correct update “Expedite installation of quality updates if device OS version less than“
you want to deploy and target the correct group.
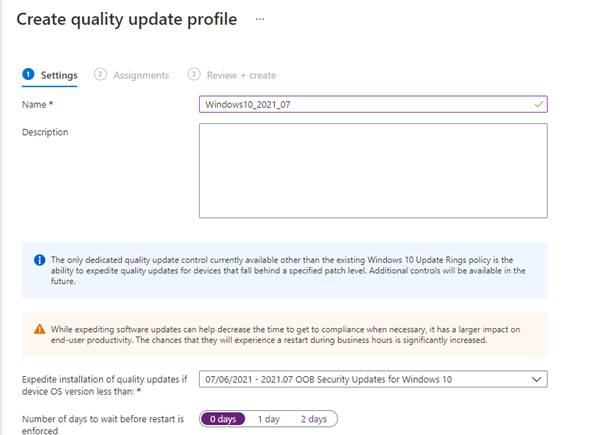
With this setting, you can select how soon after installing the update a device will automatically restart to complete the installation. You can select from zero to two days. The automatic restart is canceled if a device manually restarts before the deadline. This setting isn’t enforced if an update doesn’t require a restart.
3. Monitoring the Expedited updates
As mentioned in the Expedite Update flow, we could monitor the progress of the Quality updates we have configured by opening Intune –> Devices –> Monitor.
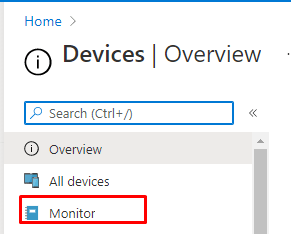
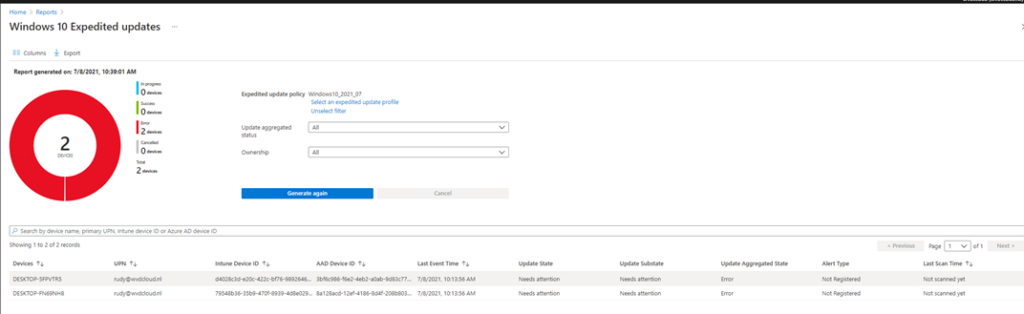
After opening the Monitor section, please select the Windows Expedited updates option and select the profile you created earlier.
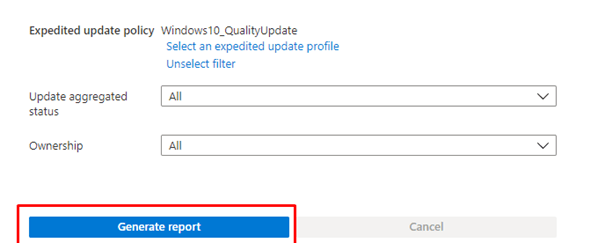
Click on Generate a report to get the Windows Expedited update report
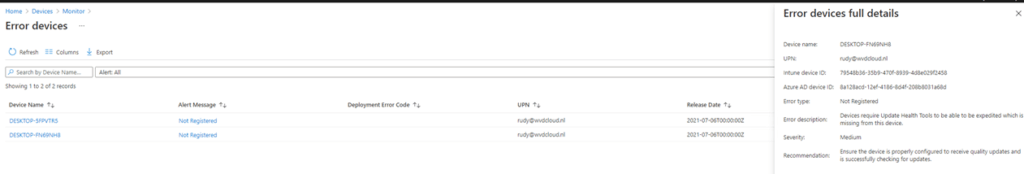
Let’s take a look at why it’s failing. You can do so by clicking on the “Not Registered” alert message
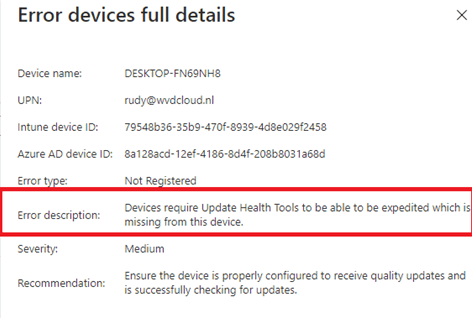
As shown above, the Update Health Tools, AKA Expedite client, is missing. These are necessary to deploy quality updates.
You could also check the same report by opening the reports option and selecting Windows Updates –> Reports
4. The Update Health Tools
Now that we are pretty sure these are missing, we need to know what they are. The Update health tools (Expedite client ) are necessary and, of course, a prerequisite when you want to start deploying the Quality Updates in Intune. So we need to make sure this update is already installed before the expedited updates can work.
This update includes files and resources that address issues affecting Windows update processes that may prevent important Windows updates from being installed.
These improvements help ensure that updates are installed seamlessly on your device and improve the reliability and security of devices running Windows 10.
If you want to read more about the Update Health Tools, you can visit this Microsoft website. It has information about the KB4023057 update
KB4023057: Update for Windows 10 Update Service components (microsoft.com)
5. Detecting the Update Health Tools
There are many different methods to determine if the health update tools (Expedite client) are installed; I am going to mention a few of them
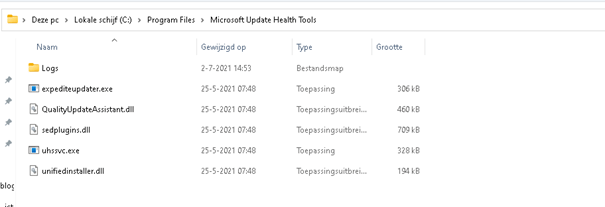
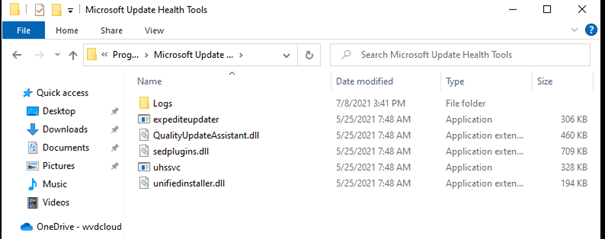
1. Update Health Tools Folder
When the Microsoft Update health tools (Expedite Client) are correctly installed, a folder (Microsoft Update Health Tools) must be inside the program files folder, as shown below.
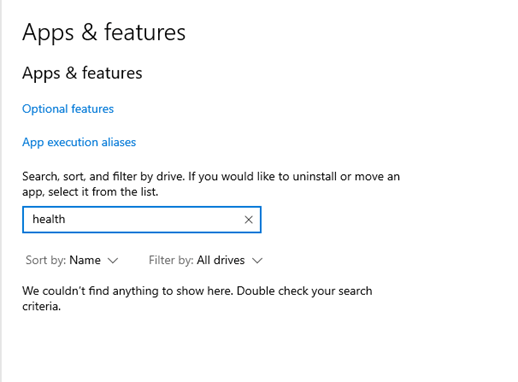
2. Apps and Features
Another possibility to check if the Expedite Client is installed would be to simply open “app and features” and search for health. As shown below, because it wasn’t installed, there were no results.
3.PowerShell
Powershell is also a very good option for determining if the expedite client is installed. Just launch Powershell and copy-paste this command:
Get-WmiObject -Class Win32_Product | Where-Object {$_.Name -match “Microsoft Update Health Tools”}
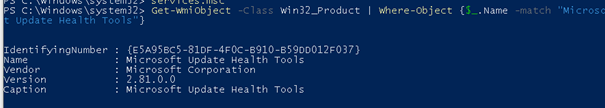
The results will let you know if it is installed or not. In the example above, it was installed!
6. Installing the Update for the Health tools Manually?
When you have some time to spare, and you need to install the Health tools because you need them and they are missing for some reason, you could open Edge and browse to: Catalog.update.microsoft.com
On this Catalog Update website, start searching for KB4023057
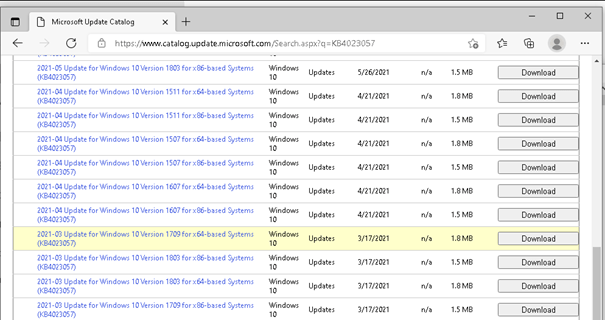
But where is my 21h1 version? I tried to download the latest to just see what happens…
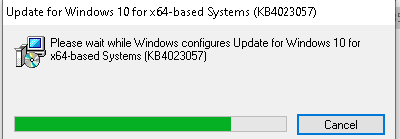
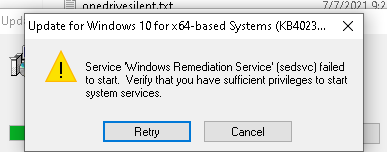
Instead of the Health update folder, a “rempl” folder is created?
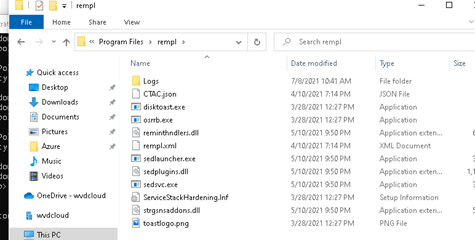
When it’s not working, it’s always a matter of RTFM. You know what it stands for…. So I did….
Okay… so downloading the update from the catalog won’t work? Are we going to ask all employees to check for updates manually?
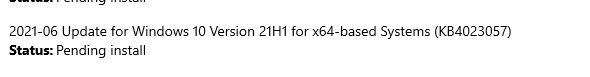
As shown above, when the check for windows updates function is not removed as I have shown below…this could be an option? Not for me.
7. Installing the Health tools automatically
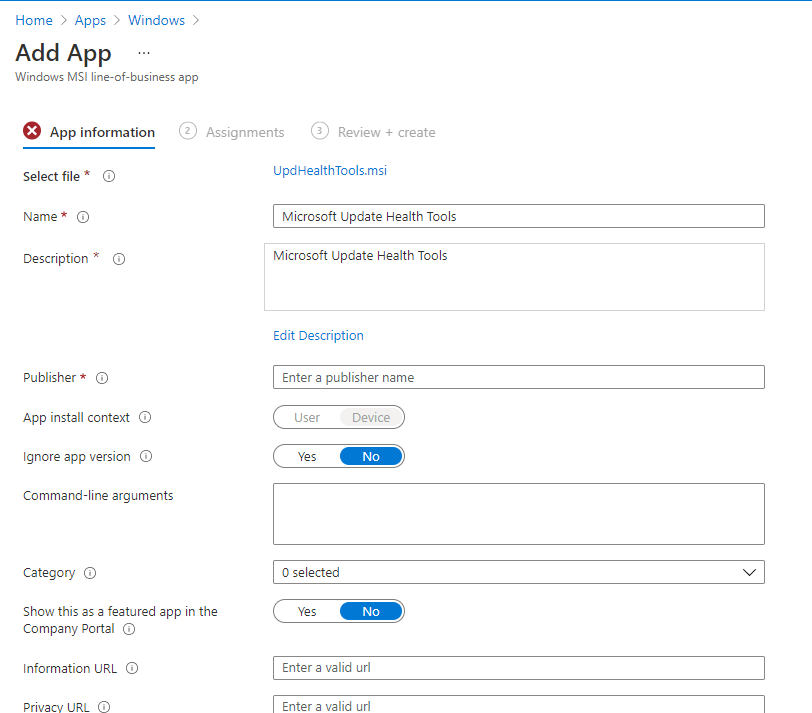
You could also download the Health Tools (Expedite client) manually!!
Download Unified Health Tools from Official Microsoft Download Center
It contains a simple MSI that you can select and upload to Intune… It’s way much easier now!
But if you are still interested in learning how to do the same with a PowerShell script, keep reading!
With my first attempt trying to install the update with the PSWIndowsupdate module, I forgot the most important thing… test it before you deploy it!!
This was my first PowerShell script
Install-PackageProvider NuGet -Force
install-module pswindowsupdate -force
install-windowsupdate -kbarticleid KB4023057 -force
But of course, this failed. So I needed to test the script execution without Intune. To do so, I downloaded the Psexec tool first and ran the script in a system context.
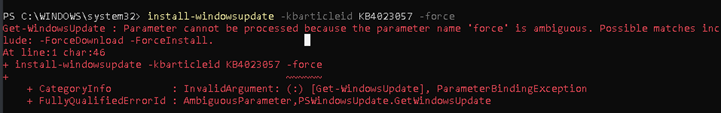
I totally forgot to check if the pswindowsupdate module was accepting the -force argument… Shame on me…
So I changed it a little bit and added also some logging to it and deployed the PowerShell script to Intune
Try {
Install-PackageProvider NuGet -Force
install-module pswindowsupdate -force
install-windowsupdate -kbarticleid KB4023057 -acceptall
}
Catch {
$_ | Out-File C:\temp\errors.txt -Append
}And after manual sync, the PowerShell script was executed without any problem, and the Update Health tools were installed perfectly!
8. Waiting for the Quality Update status
Now everything was good and after some waiting, waiting, and coffee… The update status changed to “Pending” and “Validating”
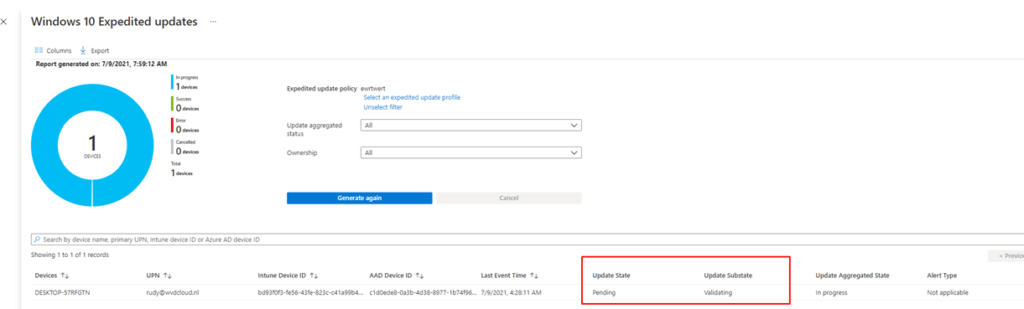
When looking at the official Microsoft documentation, they tell us this: “The Device has been added to the policy in the service, and validation that the device can be expedited has begun.”
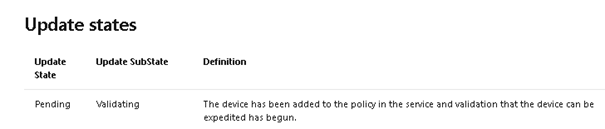
So… it begins?

But after a nice night of sleep, it still says the same thing, and looking on the device, it still hasn’t been installed, it was still pending/waiting to be installed.
I was expecting a nice toast notification, as shown below, with a notification I need to restart my device!
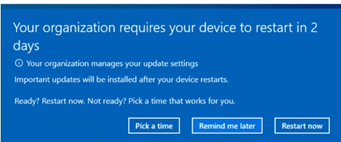
9. Troubleshooting
But for now… nothing. What to do next? We are going to take a look at some requirements and how we could get some more information about what’s happening.
Licensing Check:
When you want to make use of this service, you will need to have the proper license.
As I mentioned in the summary, you must have been licensed for: Windows 10 Enterprise E3 or E5/Windows 10 Education A3 or A5/Windows 10 Virtual Desktop Access.
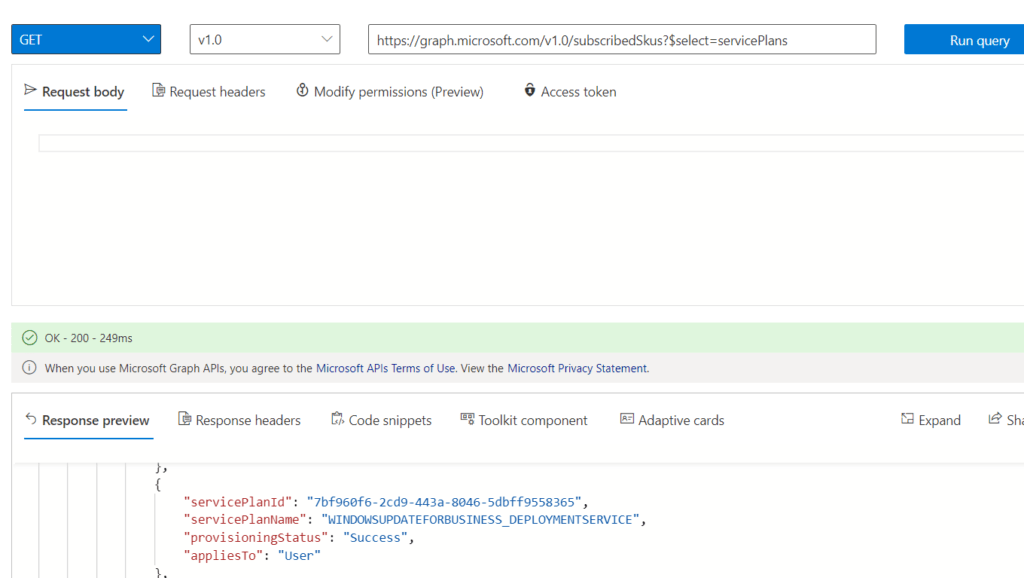
The best way to check if you are licensed? Graph! Open Graph explorer and enter this URL: https://graph.microsoft.com/v1.0/subscribedSkus?$select=servicePlans and click on “Run Query”
As shown below, when you are licensed, the windowsupdateforbusiness_deploymentserivce needs to be in the list. If it’s not there, your tenant does not have the correct license!
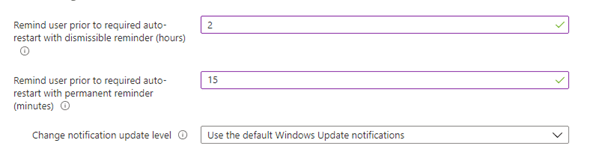
Notification Level:
To be sure I didn’t disable the notification update level, I checked the Update ring again. As shown below… “use the default Windows update notifications”
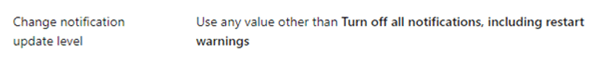
Again, making sure the notification update level is configured correctly is one of the requirements:
Telemetry settings
Of course, as I mentioned in the expedite flow, telemetry is also needed, so we need to make sure it’s configured. In the example below, telemetry is configured to “full,” so that’s not going to give us any problem. Please make sure telemetry is set at least to basic.
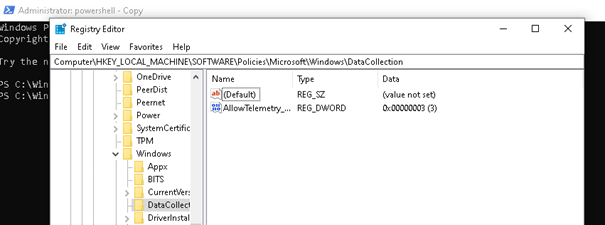
Why does it take so long to push an update? I was expecting it to be delivered within an hour.! Let’s dig further.
The Update health tools and update service
The Microsoft update health tools (Expedite client) are responsible for receiving the update, so I made sure the service which is created when you install the update health tools is started.
When checking out this service, please make sure your Windows update service isn’t disabled.

Windows Health Monitoring
Before you can monitor results and update the status for expedited updates, you must have configured Windows Health Monitoring. I can’t say it enough, it’s very important this is configured for some good reporting.
Of course, we were already using endpoint analytics, so the health monitoring policy was configured for endpoint analytics. Maybe I forgot to also select the Update part?
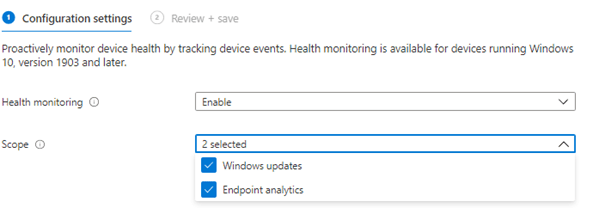
As shown above, that also wasn’t the case and the problem was not the reporting part but the installing part.
LOGS:
Maybe you noticed in one of the pictures I showed you earlier, there is a log folder inside the update health tools folder. Let’s take a look at it, open the event log, and open the log file
That’s not a lot of good information, so we have got two options here.
- Powershell
- Perfview
Option 1 Powershell
With this option, we need to open the file explorer and open the log folder. We are going to convert them using this command: Get-WindowsUpdateLog -etlpath. But to do so we need to change the names of the logs first. Select all of them and click on rename and type: WindowsUpdate
Open PowerShell and launch this command: Get-WindowsUpdateLog -etlpath “C:\Program Files\Microsoft Update Health Tools\Logs”
The Get-WindowsUpdateLog cmdlet merges and converts Windows Update .etl files into a single readable WindowsUpdate.log file. If you want to read more about this command, please visit the Microsoft webpage : Get-WindowsUpdateLog (WindowsUpdate) | Microsoft Docs
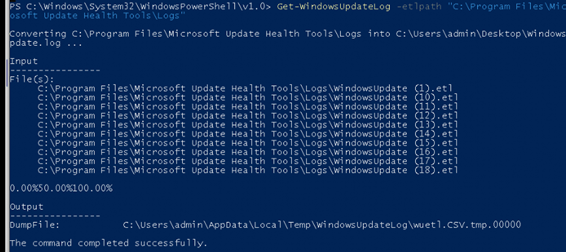
All of the logs are now converted and readable, but unfortunately for me.. there was nothing useful in it.
Option 2: PerfView
We are going to download Perfview first:
https://www.microsoft.com/en-us/download/confirmation.aspx?id=28567
After we have opened we can select the folder with all the etl files in it we noticed earlier.
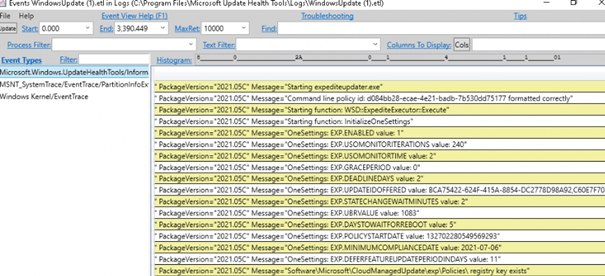
As shown above, this is giving me more information than I expected to be honest. Looking at the last line, it is giving us a registry key!

Register:
Now we have seen the registry key within PerfView let’s check it out! Open Regedit and open this key: HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\CloudManagedUpdate\uhs\settings
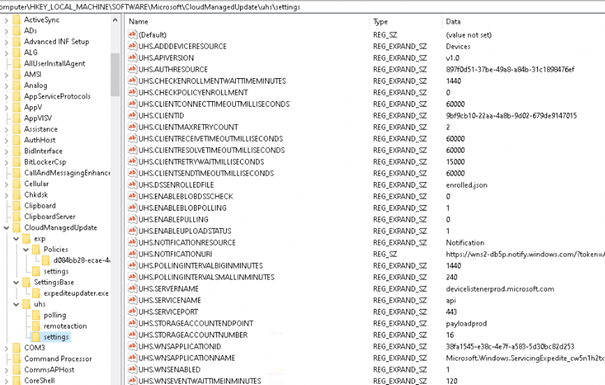
Looking at the picture above: you will notice the UHS.SERVERNAME. It’s the WUfB-DS I mentioned earlier.
So, I guess all the necessary settings are configured. But still, it wasn’t working.
When looking at the exp policies/settings registry key: Software\Microsoft\CloudMangedUpdate\Exp\Policies there is a policy created but why doesn’t it work as it should?
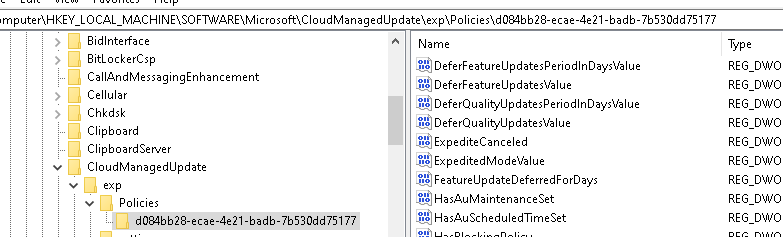
10. What to do now?
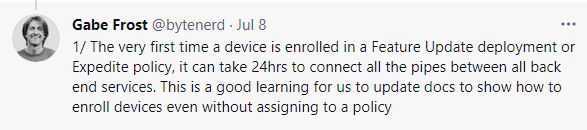
I truly love the idea of pushing these important updates with the Windows quality Updates preview feature, but I want the update to be installed within the hour! Not waiting 24 hours or more. If you haven’t used the Expedite Update feature previously and this is the very first time you have used the quality update preview to expedite an update, you may need to wait 24 hours before “all the pipes between all back end services” are connected.
So I created detection and a remediation PowerShell script to use with Proactive Remediations!. I guess I love them. If you want to read more about them:
Proactive Remediations – Call4Cloud
So, let’s create one. Download these PowerShell scripts and select them when you are configuring the proactive remediation! https://call4cloud.nl/wp-content/uploads/2021/07/updatewithproactive.zip
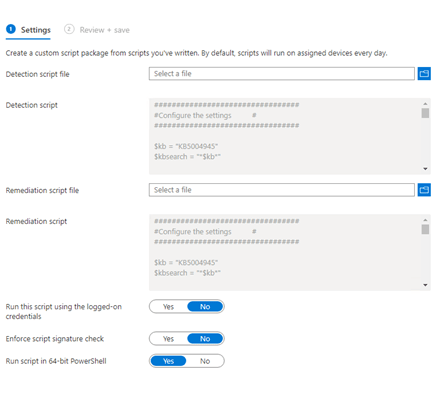
When taking a good look at the proactive remediations scripts you downloaded earlier, you will notice some things:
- I am using the pswindowsupdate to install the required update
- I am simply using the build-in get-hotfix PowerShell command to determine if the update is installed or not. You could also use this command: get-wmiobject -class win32_quickfixengineering
- If the update is not installed the remediation script will kick off and will try to install the update with the PS windows update tools.
- I am downloading serviceui.exe from my website to make sure I can show some messages from the system context to the user context. If you want to read more about this: Company App: Unchained – Call4Cloud
- I will create a scheduled task. This task will notify the user with a toast message from the System context to the User context and will install the update, after the update has been installed it will kick off another notification to the user about the status (step 6)
- After trying to install the update, it will again check if it has been installed correctly by again using the get-hotfix command. This output will be used for the proactive remediation status
- You may notice that both of the PowerShell scripts are converted to a base64 command. You can read more on this blog about how to do this https://call4cloud.nl/2021/05/the-laps-reloaded/#third-part.
- I added the toast PowerShell scripts to the remediation script itself so you can change it to your liking.
11. Proactive remediations Results:
During the installation:
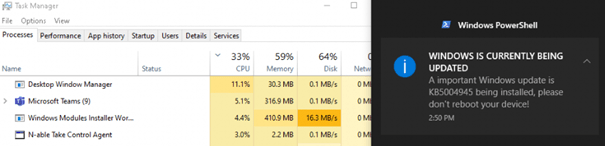
After the proactive remediations kick off, you will notice that within a few seconds, the Windows module installer worker will be launched, the update will be installed, and you will be prompted with a nice balloon notification!
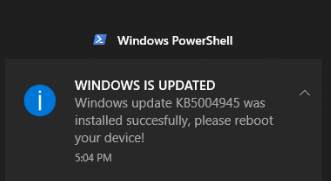
After the installation:
I created a toast notification to show the end-user when the update was successful and they need to reboot their device!
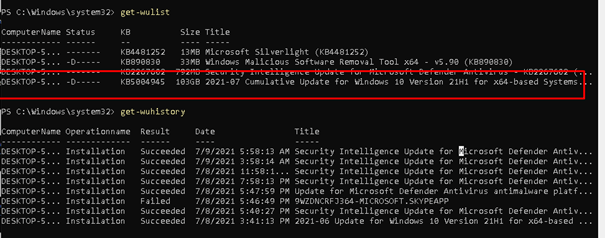
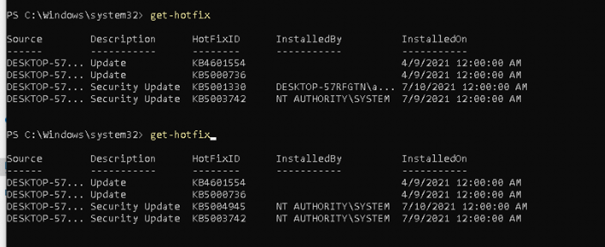
Also, get-hotfix (manually) will tell us the update is installed!
After some time the status was also reported back to Intune and was visible inside the Proactive remediations.
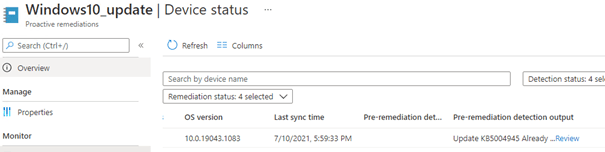
Also, exporting the Proactive remediations to CSV showed me the same output

If you look closely the Export button was gone again? I showed you in my last blog how you could do this with PowerShell if the export button was gone.
https://call4cloud.nl/2021/06/proactive-remediations-lost-in-powershell
12. Reset the whole device and try it again with Quality Updates
As Gabe Frost mentioned, It can take some time before your tenant is ready to deliver those quality updates. So I reverted back to the hyper-v snapshot I took before I started with this whole blog but this time I just waited until after I recreated the Quality Update Policy.
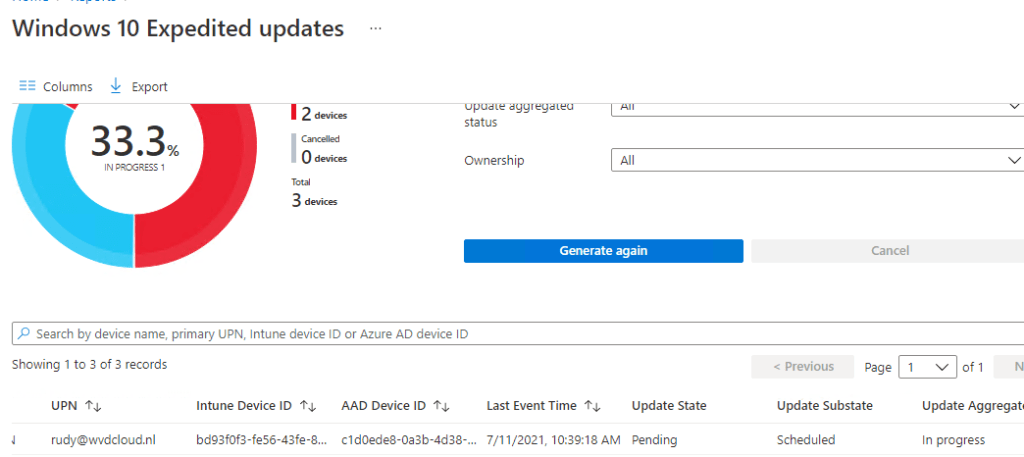
And yes!!!! the update was scheduled and in progress. While watching the report in Intune I noticed some CPU load from the Windows installer process on the device and after a while, I got notified to reboot the device!
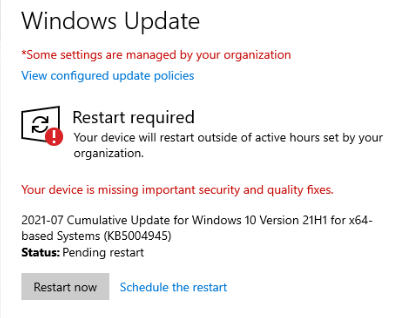
Again I opened PerfView and the Registry to take a look at what’s happening under the hood
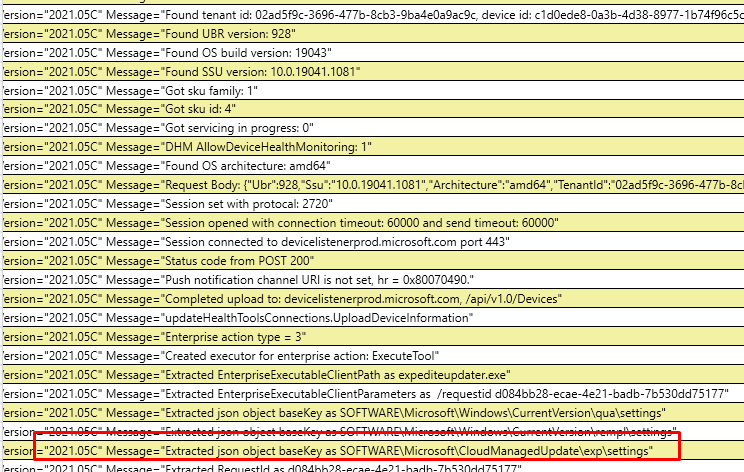
When looking at this registry key, I noticed the same two settings (EXP.graceperiod and EXP.Minimumcompliancedate) we specified in the Quality Update preview: the update we want to install and the grace period!
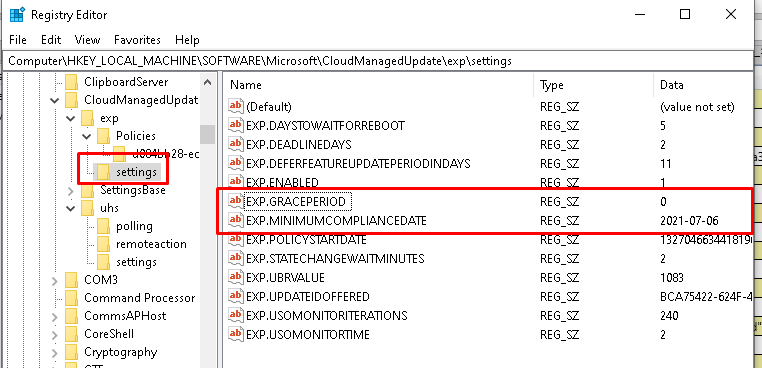
But I am not done yet… when looking at the Health Update tools, they are really necessary, so they must have a role to play? Yes, they do… After some playing around with the expediteupdater I noticed this: / requestid
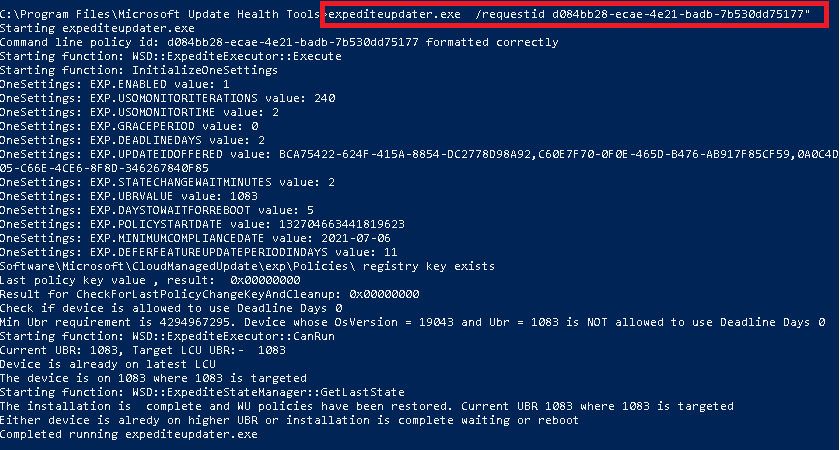
It’s very nice to see you could also “trigger” the process? You only need to open the registry and note down this key inside the policies folder and request it as I did.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\CloudManagedUpdate\exp\Policies
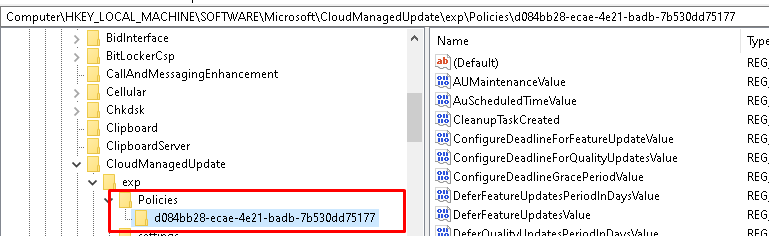
Of course, the key only exists when you configured/enabled a quality update policy.
13. Reset the Whole device and trigger the quality updates on your own!
I guess now I know how it works and what to request, I want to know if I could manually trigger it? I again reverted back to my snapshot and opened the registry. I noticed two policies this time instead of
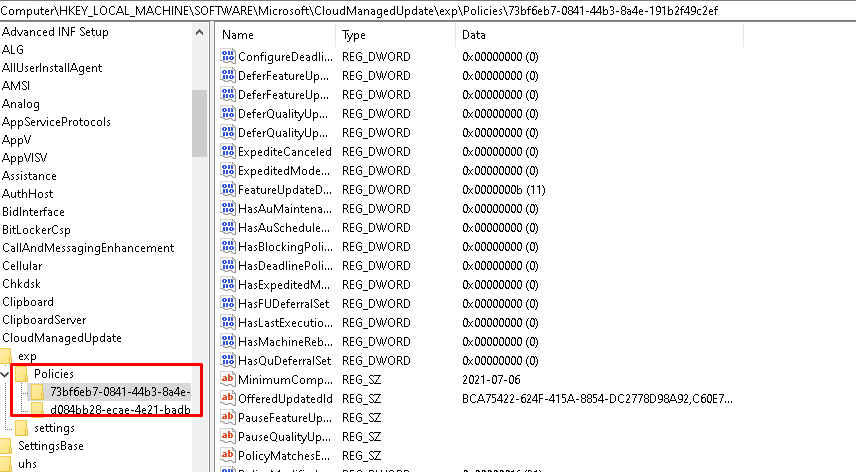
Okay? Let’s request something!

After a minute, it was starting to scan for updates and showed us the “GetUpdatesInProgress“
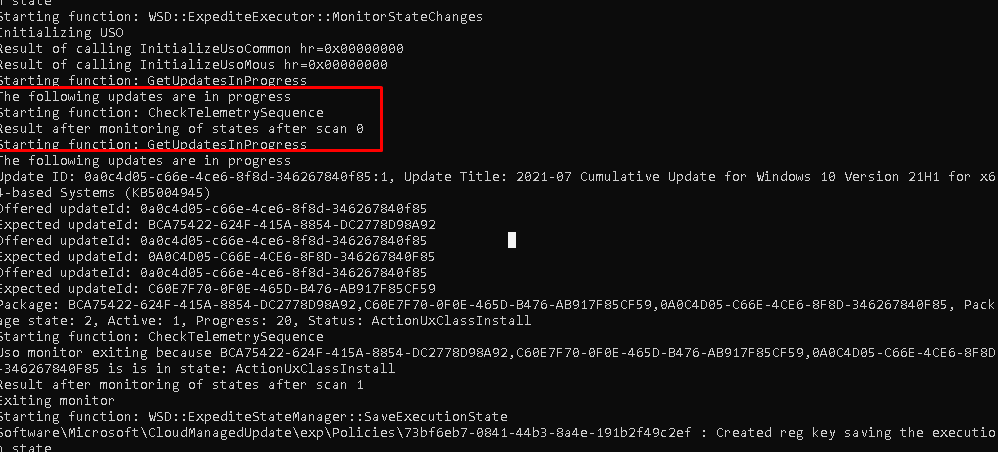
And it launched the Windows modules installer! I guess to install the required update?
Again, after a minute or two, expediteupdater.exe was finished, and now we need to wait until the update is done installing.
And there it is!!!! Isn’t that a wonderful message to spot?
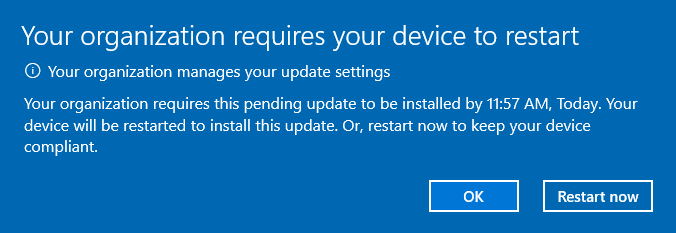
14. Summary to get Quality Update working:
- Enable Health Monitoring in your Tenant
- Make sure the Update Health Tools are installed
- Make sure telemetry is configured
- Configure the Update notification settings and make sure they are not disabled.
- Check the WuFB settings and make sure the service channel is configured to semi-annual channel
- Make sure you are licensed to use it: Windows 10 Enterprise E3 or E5/Windows 10 Education A3 or A5/Windows 10 Virtual Desktop Access
- Make sure there are no legacy old GPOs interfering (Make sure Windows Update is not pointing to WSUS like an example)
- Just wait.… if this is the first time you configured it in that tenant
- Make sure there is some activity on the device 🙂
- Maybe trigger it on your own… ?
Conclusion
I love the idea of updating Windows 10 immediately using the Quality Updates Preview, but it took too long when you enabled it for the first time.

Maybe it was because many people were using it to fix the Printer Nightmare bug with the 2021-07 update 🙂 or I still needed to wait 24 hours before everything was “connected”.
I switched to my backup plan to deploy those kinds of updates to their devices that needed it! And those toast messages are just great. But I am 100% confident all of the first delay issues are going to be resolved!


Outstanding work! I’ve been trying to figure this out for days now. I truly appreciate you sharing all this.
Hi, Thanx for your kinds words!
Thanks for this Ill try it out and see if it works.
Hola! thanks for a great article.
Any clues on how to troubleshoot “in progress” QU?
– Created new QU, targeted 2 devices, 5 days later they still show up as “In Progress”, no error.
– Deleted QU, created new one, 24h later same report “In Progress”.
– MUHS Logs confirm Tenant registered in WufB (seen this in other tenant, no Wufb Tenant registration), but I didn’t find QU profile getting ingested to registry. Didn’t find any policy in HKLM/Software….
Thanks in advance for any feedback and/or comments.
Hi,
Thanx!
Answering your question can be difficult as I don’t have my fingers on that device 🙂
So to be sure, there are no settings configured inside this key: HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\CloudManagedUpdate\uhs\settings or the exp\policies setting?
If not we can begin to look there… as the device still doesn’t received the policies
Still trying to fix the issue.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\CloudManagedUpdate\uhs\settings
Had a few keys (don’t remember them), keys had blank values.
– Waited.
– Waited.
– Got Feb Updates, still nada.
– Stopped service, deleted “uhs” key, restarted service, Keys appeared again.
– Decided to Uninstall Microsoft Update Health Tools via add/remove programs
– Tried to make the service reappear via “Check for Updates”, nada!
– PSWindowsUpdate, Install-Windowsupdate…. It didn0t work.
So, this is a lab, solution, “next”. But nope, I’m still going just for the fun of self-inflicting pain.
Thanks!
any idea about max items in the reports of Windows Update Feature update?
When i check my Win11 deployment, it shows the exact details etc. It only has 16 machines linked to it.
The 21h2 deployment, for all other machines is not showing any data during Generate Report action.