This blog is the eighth part of the Endpoint Security series and will be about Windows Defender Exploit Guard Network Protection WDEG-NP.
1.Information about Network protection
Microsoft Defender Exploit Guard Network Protection (MDEG-NP) extends the malware and social engineering protection with the help of Microsoft Defender SmartScreen in the Microsoft Edge browser and in the legacy browser: Microsoft Internet Explorer. Of course, MDEG-NP will also protect 3-party applications like Google Chrome or Mozilla Firefox.
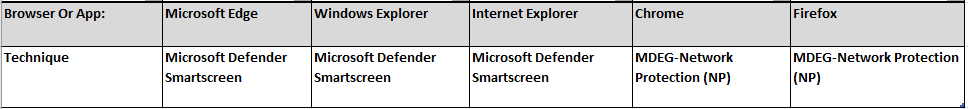
Looking at the picture above, you could say that Microsoft Defender SmartScreen will protect devices against phishing or malware websites and applications and the downloading of potentially malicious files. So, what does it do?
Microsoft Defender SmartScreen determines whether a site is potentially malicious by:
- Analyzing visited webpages looking for indications of suspicious behavior. If Microsoft Defender SmartScreen determines that a page is suspicious, it will show a warning page to advise caution.
- Checking the visited sites against a dynamic list of reported phishing sites and malicious software sites. If it finds a match, Microsoft Defender SmartScreen shows a warning to let the user know that the site might be malicious.
Microsoft Defender SmartScreen determines whether a downloaded app or app installer is potentially malicious by:
- Checking downloaded files against a list of reported malicious software sites and programs known to be unsafe. If it finds a match, Microsoft Defender SmartScreen shows a warning to let the user know that the site might be malicious.
- Checking downloaded files against a list of files that are well known and downloaded by many Windows users. If the file isn’t on that list, Microsoft Defender SmartScreen shows a warning, advising caution.
So What about the Requirements?
I guess the name says it all, you will need to have Microsoft Defender enabled otherwise it will not work at all… But make sure when configuring Microsoft Defender, you have enabled cloud-delivered protection and enabled real-time protection.
Those requirements should be no problem as we all have configured Microsoft Defender as leading av right? Looking at other features of Microsoft Defender, I guess they all want Microsoft Defender to be the active one!
https://call4cloud.nl/2021/07/o-removable-storage-where-art-thou
2.Configure Microsoft Defender network protection (Smartscreen) for Edge
Now we have all the background information we need, we need to create a new Endpoint Security Attack Surface Reduction configuration setting and select Web Protection.
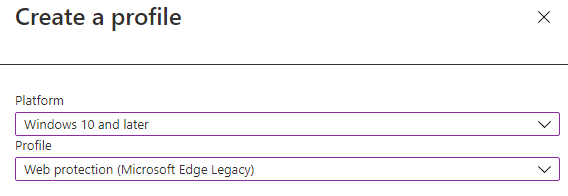
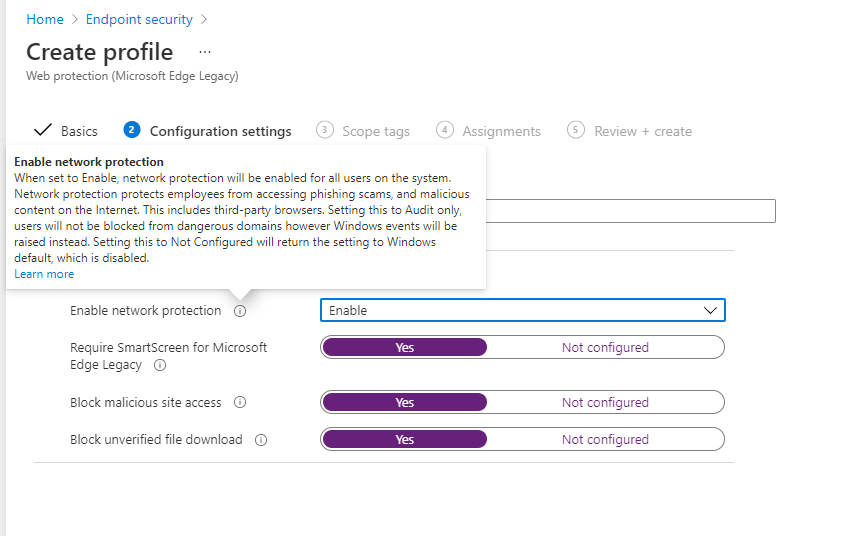
It’s very easy to enable it. Just make sure you enable network protection and configure the other 3 settings to yes.
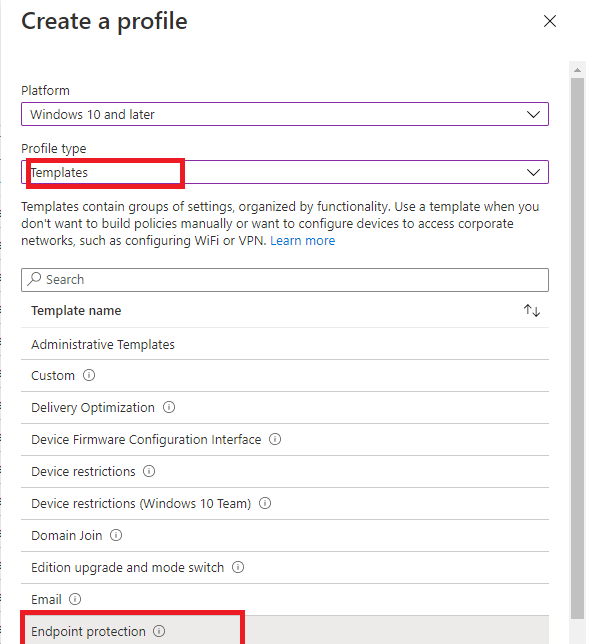
3.Configure WD SmartScreen for Explorer
Why do I need to configure an additional device configuration profile for this? that’s odd? I would prefer to configure this setting at the same Endpoint Security page where we configured the first setting.
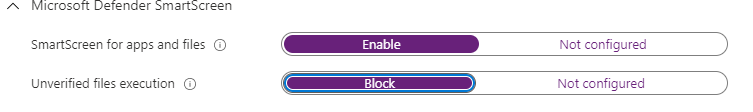
4.Configure WD SmartScreen for Internet Explorer.. NO! just block IE!
We could also configure SmartScreen for Internet Explorer but in my opinion, a way better option is to disable it! I know this blog is about how to configure it, but again….. just disable IE, please!
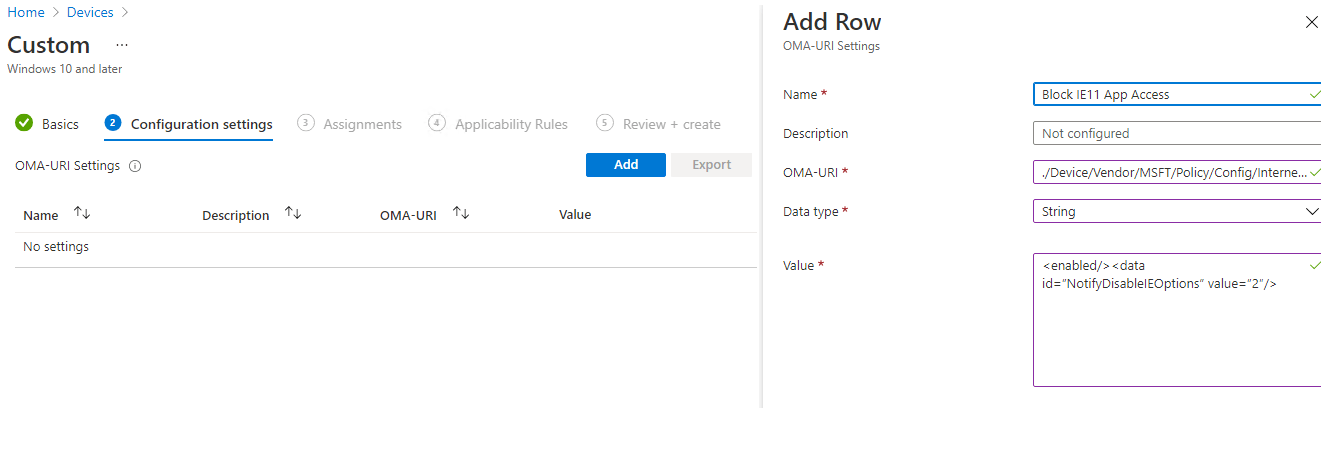
So how are we going to make sure Internet Explorer is disabled. You will need to create a new CSP with these values
OMA-URI ./Device/Vendor/MSFT/Policy/Config/InternetExplorer/DisableInternetExplorerApp
Data Type String
Value <enabled/><data id=”NotifyDisableIEOptions” value=”2″/>
 After the policy has arrived at the device, try to open Internet Explorer and wait for the warning!
After the policy has arrived at the device, try to open Internet Explorer and wait for the warning!
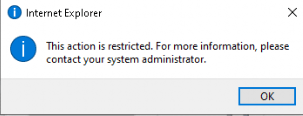
Why enable SmartScreen for Internet Explorer when you can block it ?
5.Checking the configuration and some testing
Okay, now that everything is configured, we are going to take a look at how you could make sure it’s configured and how you could enable some logging before we test it.
Checking the Configuration
Powershell
First, let’s see how you can ensure network protection is enabled. You could simple open PowerShell and run the get-mppreference command

Security Settings Page
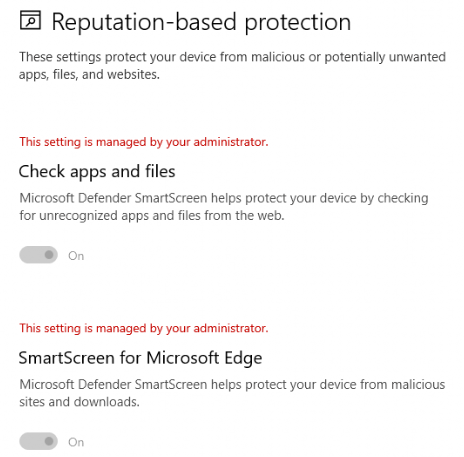
Or just open the Security Settings Page to check if the necessary settings are configured and greyed out (so you can’t change them!).
Intune:
And, of course, there is Intune! Go open your device blade and select a device with the Network configuration enabled and click on “Endpoint Security Configuration.”
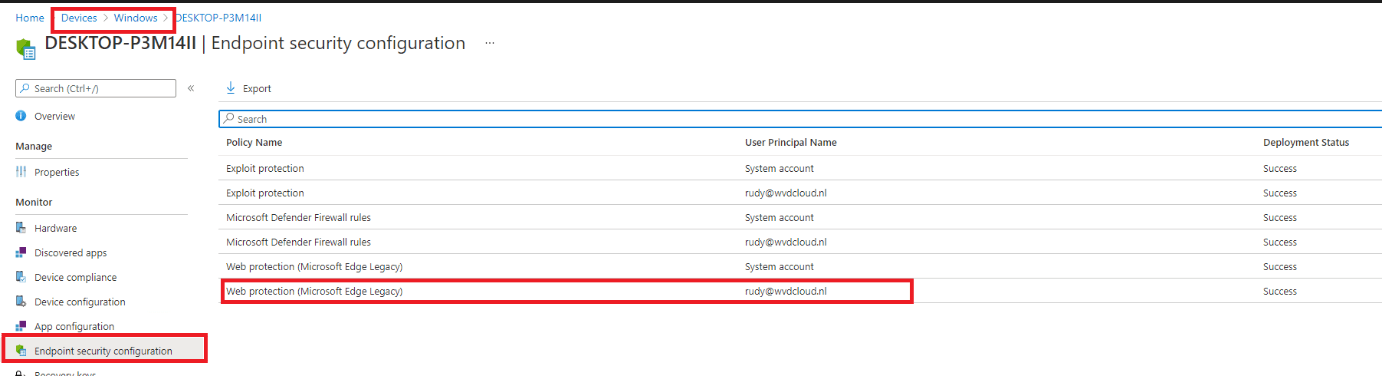
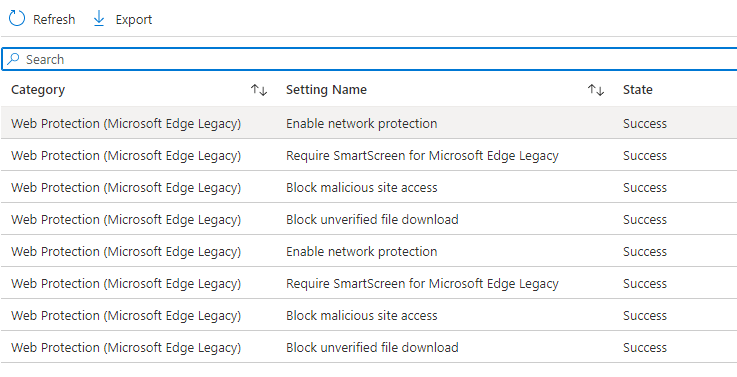
6.Testing
Now we are pretty sure network protection is enabled and configured, we still need to enable the smart screen debug event log. Otherwise, we could miss some events.
Right click on the debug event log and click “enable log”
It’s a good thing you could also enable this event log with PowerShell so you can deploy this to your devices with a PowerShell script:
$log = Get-WinEvent -ListLog ‘Microsoft-Windows-SmartScreen/Debug’
$log.IsEnabled = $True
$log.MaximumSizeInBytes = 21053440
$log.SaveChanges()
Another possibility is this one lined PowerShell Command
wevtutil sl Microsoft-Windows-SmartScreen/Debug /e:true
Now we have enabled the necessary logging I am going to run 2 tests with 2 browsers. In the first test, I am going to browse to an unsafe website with Chrome and Edge. In the second test, I will try to download multiple files with Chrome and Edge to see what Happens
Test 1.1 Edge Unsafe Website
Let’s open your Edge browser and open https://smartscreentestratings2.net. You will be presented with a nice red error screen.
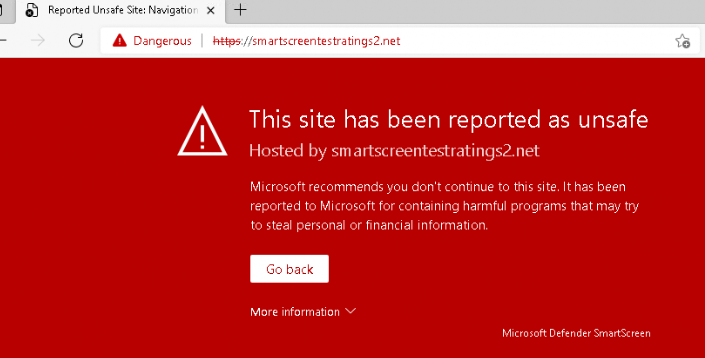
But no events were logged in the SmartScreen or Windows defender event log? At first, I thought I was missing something but perhaps, reading the Microsoft Docs a little bit better would help…

Test 1.2 Chrome Unsafe Website
After we have seen Edge will not report it to the event log, I downloaded google (even when I really don’t know why I need chrome anymore) and browsed to the same URL. Of course, I was presented with an almost identical red error screen.
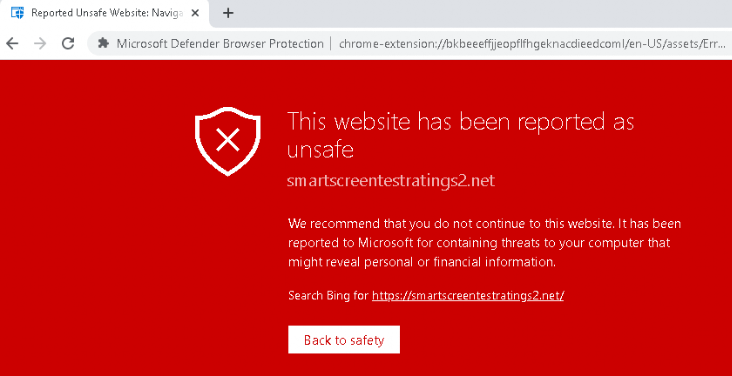
But this time, the Windows Defender Event log started logging… As shown below a lot of event 1126 are showing up!
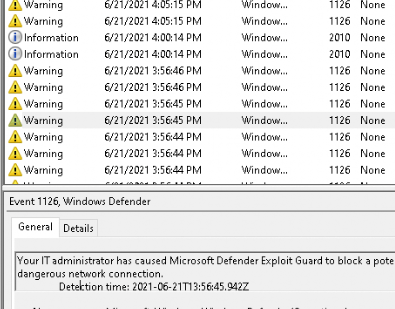
Let’s see if there is a difference when I am going to download some files.
The link to the files: AppRep – Microsoft Defender Testground
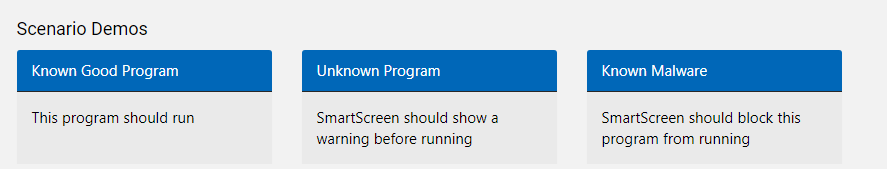
Test 2.1 SmartScreen Edge
First, I tried to download the 3 files with Edge.
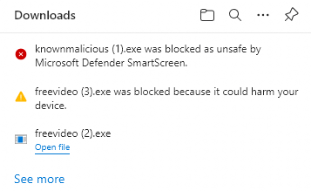
Just like Microsoft is telling us, the first one is allowed, the second will warn us, and the third will be blocked. But again, what about the event log? I guess we will need to wait forever.

Test 2.2 SmartScreen Chrome Dowload
But what about Chrome? I opened Chrome again and did the same test. When I tried to open the file, the red smart screen blocked it, and an event was logged in the SmartScreen event log
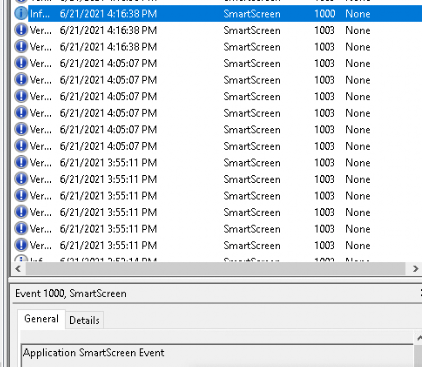
Conclusion
It’s always a good idea to implement some additional security to your devices, and it’s very easy to do so. Don’t forget to enable the File Explorer Smart Screen. Is it weird that the Edge browser doesn’t log anything at all?

As mentioned before this was the eighth part of the endpoint security series, if you want to read the other parts:


I don’t understand some things
– I have to configure smartscreen for explorer via configuration profile
– I need to activate the feature from the defender dashboard
– I need to have network protection enabled
— I can do it through policy antivirus or policy web protection (legacy) from endpoint security blade
Is it correct?
What is the difference between configuring network protection via legacy web protection or via antivirus policy?
I do not understand this, there is confusion.