This blog will be about some possible time-out issues you could encounter during the Account ESP phase when using Autopilot and requiring Online Microsoft Store Apps (Company Portal). I will try to explain why this could be happening and the options you have to possibly fix it.
1. Introduction
Some time ago, I wrote a blog explaining how to deliver the Company Portal to your devices and the important stuff you need to beware of!
Please read it first to get a better understanding of the differences between the Online and Offline versions of the Company Portal (Microsoft Store Apps)
A small summary of the Sharpe’s Company Portal from the blog above
| Online License | Offline License | |
|---|---|---|
| License Assigned to | Users | Devices |
| ESP: When installed? | Account Phase | Device Phase |
| Supports Device Context | Yes (but only installed in the Account Phase) | Yes |
| Requires Azure Ad Account | Yes | No |
| Automatically updated | Yes (if MS Store is available) | Yes (if MS Store is available) |
I was made aware of some possible issues you could encounter in some specific situations when using Online versions of the Microsoft Store Apps. Please note that I am NOT going to talk about the Account Phase hanging on identifying.
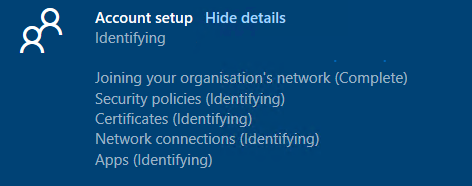
If you were expecting me to talk about that particular issue in this blog…. please read this blog below!
https://call4cloud.nl/2021/06/autopilot-skip-user-status-page-esp/
So what am I going to talk about? Let me explain! Oh, wait … even better let me show you what I am going to talk about!

As shown above, sometimes it just takes some time before Oline versions of the Microsoft Store apps can be installed during Enrollment Status Page (ESP). Besides this issue, I am also going to show you another issue you could run into. This issue could also give you a time-out when trying to install the Microsoft Store app during ESP!
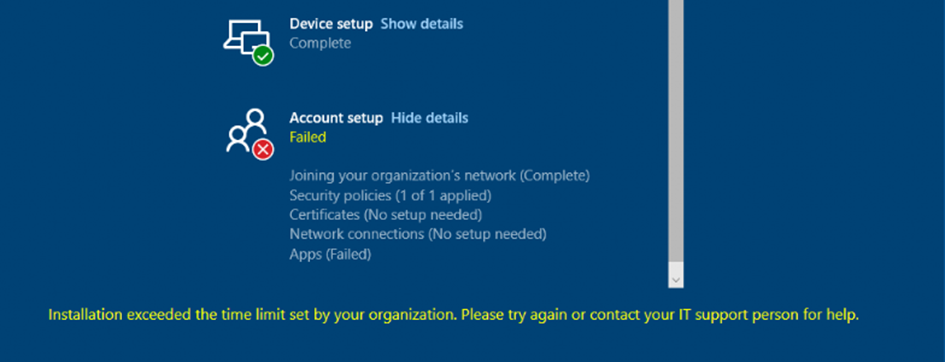
I am going to explain why Online versions of the Microsoft Store apps may take some time to install. Of course, I am also going to show you why this could get you in trouble during your Autopilot enrollment!
In this example, I am going to show you what happens when requiring the Online version of the Company Portal.
2. The Issue
When you don’t use the Offline Company portal app but the Online Company Portal app, we need to beware of a possible issue!
For the Online version of the Company Portal app (user licensed) to get installed, this user needs to silently sign in to the Microsoft Store. The MS Store app will be installed AFTER the user signs in with his Microsoft account.
Let me tell you why it is important to beware of this fact. When you are using the Online version of the Company Portal and requiring this app to be installed in the ESP during Autopilot as shown below.
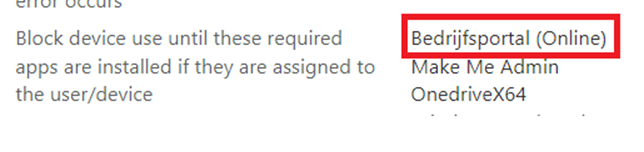
The user signing in on the device needs to have a working connection to the Microsoft Store to fetch the Company Portal App from the store. Please note: this applies to all Microsoft Store apps!!!
Let me ask you a question because I bet you configured Conditional access! When you have configured Conditional access rules to ensure your devices are compliant before they can access All Cloud Apps, how?
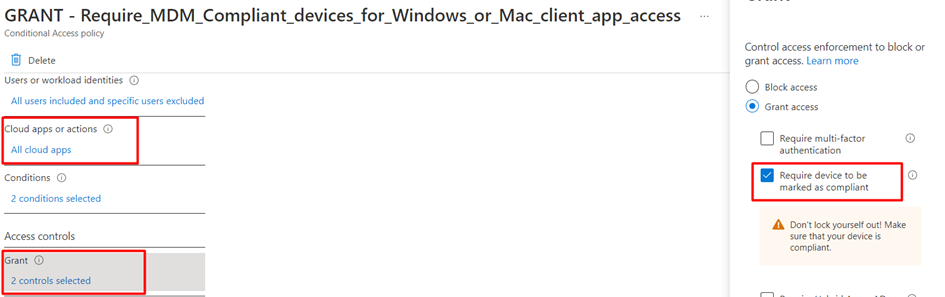
….did you target this Conditional Access policy? I guess “all users” (or a user group :P) ?
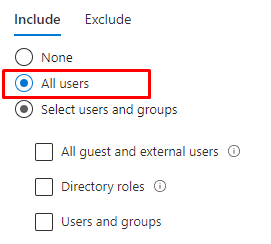
When requiring a compliant device, I bet you also have configured a compliance policy to require Bitlocker (Please read my blog about Bitlocker and DHA to understand the WHY)
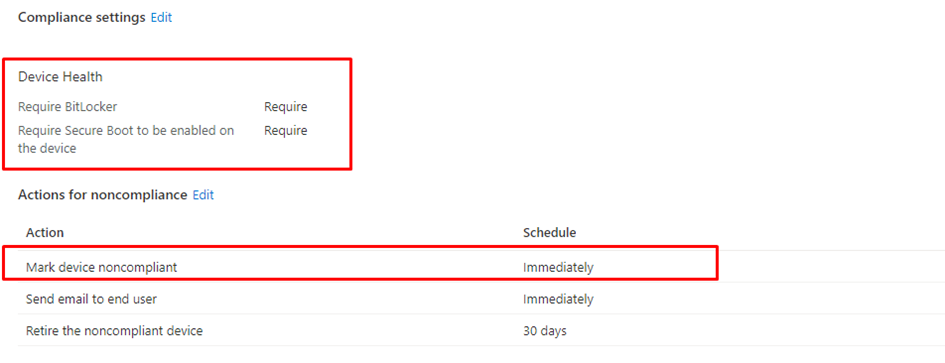
Let me explain what happens when using a Bitlocker compliance policy in combination with the Conditional Access rule mentioned earlier.
If you require the Online Company Portal during ESP and have configured Conditional Access to require a compliant device before the user can access all Cloud apps, you could be up for a challenge! The device needs to be compliant before the user can access the Microsoft Store to download the Company Portal!
When you have read my DHA blog, you will probably know that the Bitlocker status is only reported at the next reboot!!! Guess what didn’t happen when you are using an Intune device configuration profile to enable Bitlocker? A reboot! Let me explain by showing you an MS-DOC
Summary: Bitlocker will ONLY be enabled after signing in…… that’s just how the CSP works! (hopefully, this experience will be improved in the future!)
The device needs to perform a reboot AFTER Bitlocker was enabled but because Bitlocker is only enabled after logging in, the device can’t become compliant to fetch the Company Portal during the Account ESP Phase!
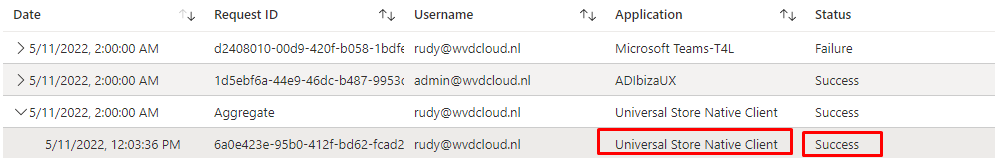
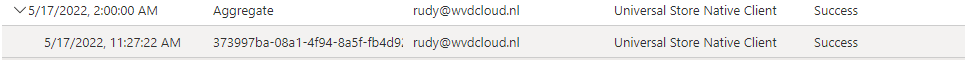
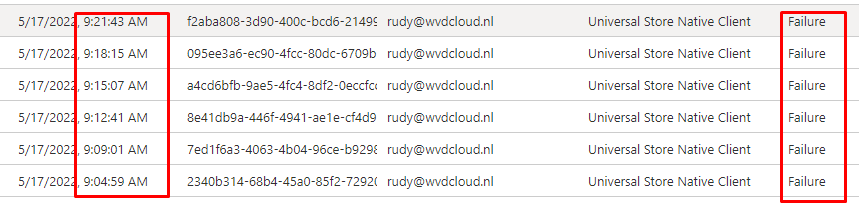
Shall we take a look at the User Sign-ins (not-interactive) after enrolling a test device with the above scenario? Maybe we could find something funny?
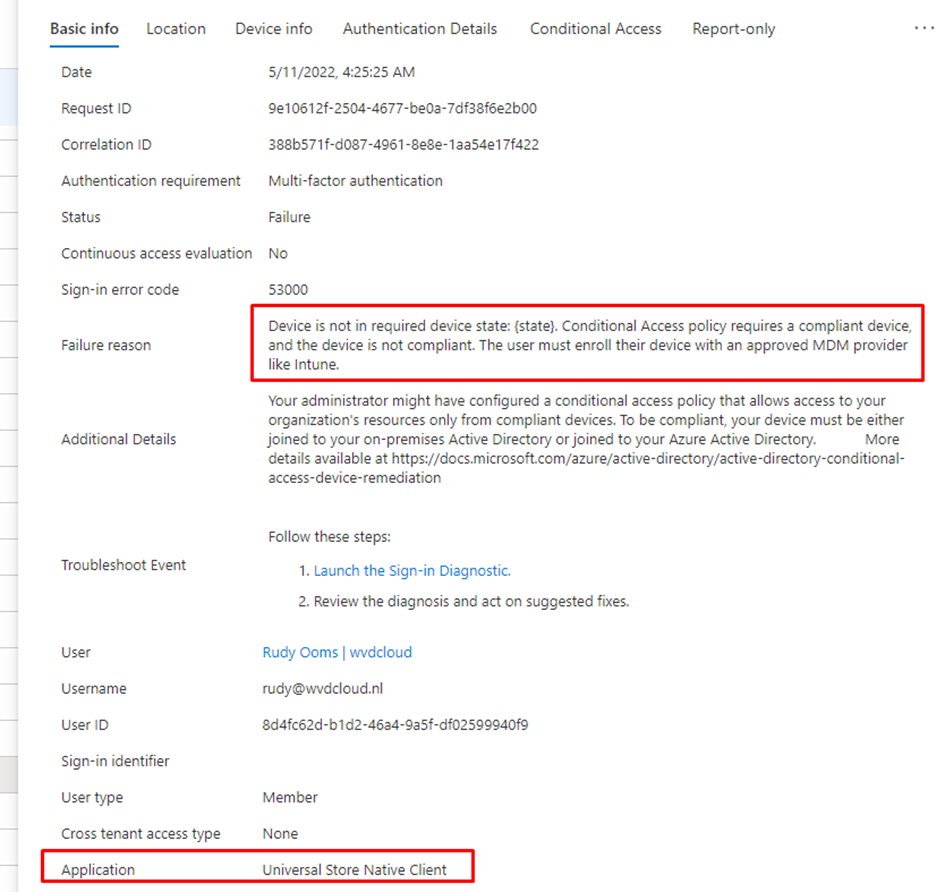
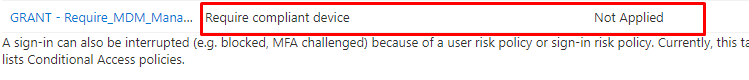
As shown above, Conditional Access is blocking access to the Application: Universal Store Native Client from my device because the device is not in a required device state (compliant) and it is giving us the Sign-In error code 53000.
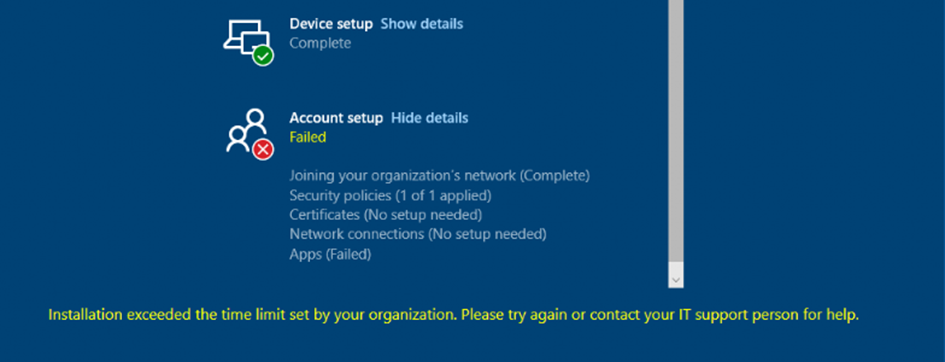
As shown above, when conditional access is blocking the deployment of the Company Online Portal app, our Autopilot enrollment will exceed the time limit because it has been blocked by your firewall, which is called conditional access!
3. Workarounds, Fixes, or how you want to call them?
We have now witnessed it with our own eyes. Conditional access could break your deployment of the Online version of Microsoft Store apps during Autopilot; let a look at what we can do to get it working!
So what options do we have to succeed out of this conditional access failure, as shown below?
3.1. SkipUserStatusPage
We could use the SkipUserstatuspage CSP setting to make sure we are skipping the Account part of the Enrollment status Page, but this could give you other issues. For example, when the device is not yet compliant, the OneDrive KFM will not kick in. OneDrive KFM will not kick in simply because It can’t access the Microsoft 365 data because it is being blocked by conditional access.
3.2. ESP and Requiring Apps
A very good option would be to NOT configure the Online version of the Company Portal as a required app during the ESP. Please note: When not requiring this app, the user must wait some time before the Company Portal arrives on the device after signing in.
3.3. Conditional Access and Targeting All Cloud Apps
We could change the Conditional Access rule to only target the Office 365 Apps
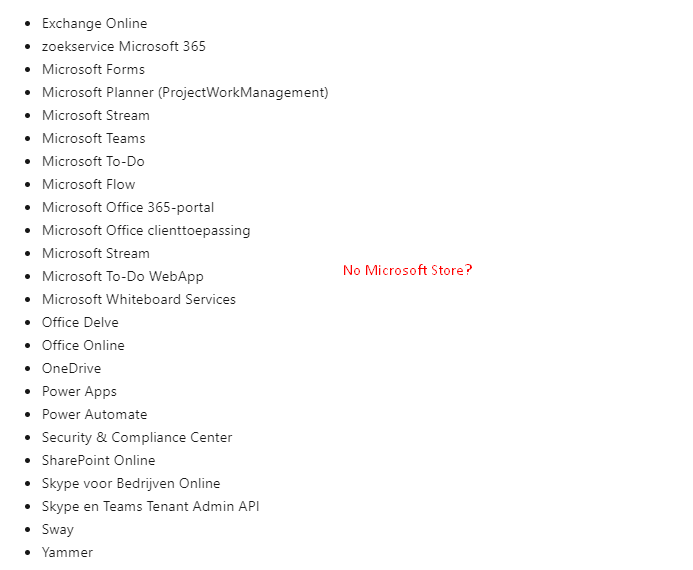
As shown below, the Office 365 Apps, don’t include the Microsoft Store
3.4 Conditional Access and Excluding the Universal Store Client?
Instead of targeting only the Office 365 apps, we could also still use the “All Cloud Apps” and exclude the “Univeral Store Native Client (268761a2-03f3-40df-8a8b-c3db24145b6b)” app from the GUI.
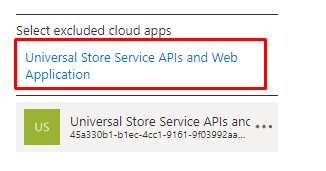
As shown above and below, even when it has a different App ID, we will notice that the “require a compliant device Conditional Access rule” will not be applied! When Conditional Access isn’t blocking the connection to the Microsoft Store, the Company Portal app can be installed successfully!
3.5 Switching between Offline and Online
We could switch to the supported Offline version of the Company App. Because this app uses a Device license instead of a User license and isn’t blocked by Conditional Access.
3.6 Changing the Device Health Compliance policy
We could change the Compliance Policy to only mark the device NOT compliant after 2 days (or a couple of hours) instead of marking it NOT compliant immediately. Because as told in my DHA blog, the device NEEDS to reboot before it could pass the Bitlocker compliance state to the DHA service.
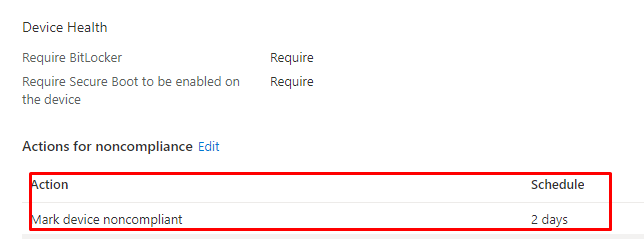
When configuring the compliance policy to mark the device non-compliant after 2 days, it will be in the grace period. This will give you the time to make sure the device becomes compliant. In the meantime, a connection to the Microsoft Store can be made, and the Company App will be installed successfully during Autopilot!

But do we really want to have a device without Bitlocker being Compliant/In grace being able to access the company data for 2 days?
3.7 Configuring Bitlocker with PowerShell
We could switch from an Endpoint Security profile (CSP) to enable Bitlocker to a PowerShell script to enable Bitlocker (Or a PowerShell script converted to a Win32app as that would also work). When using a PowerShell script to enable Bitlocker, it will be activated during the Device Phase
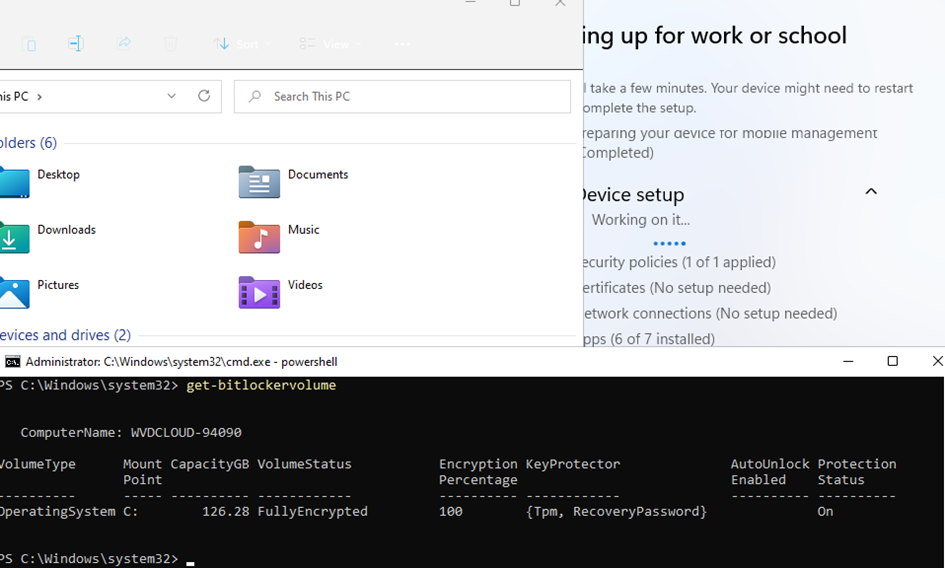
After the device ESP phase is done, the device will reboot (because of the WUfB Rings)and continue to the Account Phase. That reboot will ensure that if Bitlocker finishes the encryption of the hard drive in time, it can report back its Bitlocker status to the DHA service!
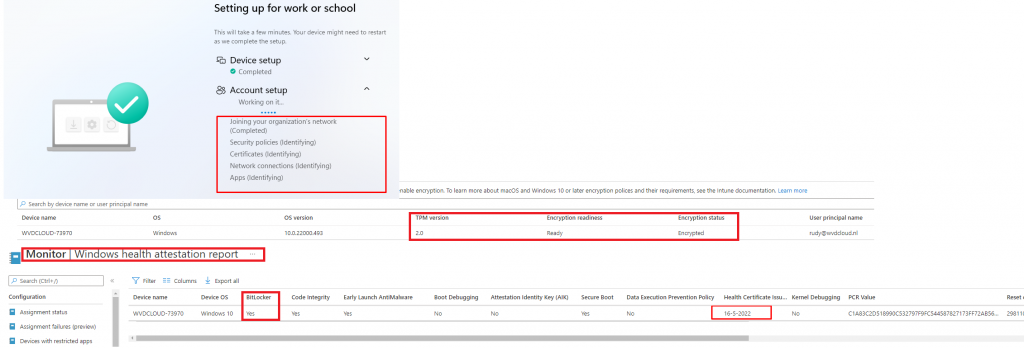
When the account phase starts, it will try to fetch the Company portal from the MS Store but to succeed it needs to be compliant first to pass your Conditional Access rule. When the device is NOT compliant yet, you will notice in the store event log that the store doesn’t succeed to GET the Company Portal app
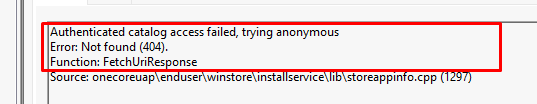
It will take some time before the compliant status has been checked, it even retries to establish a connection with the Microsoft Store every 3 minutes when it doesn’t succeed!
Luckily if the device had BitLocker enabled during the Device phase it will turn out pretty compliant after a couple of minutes!
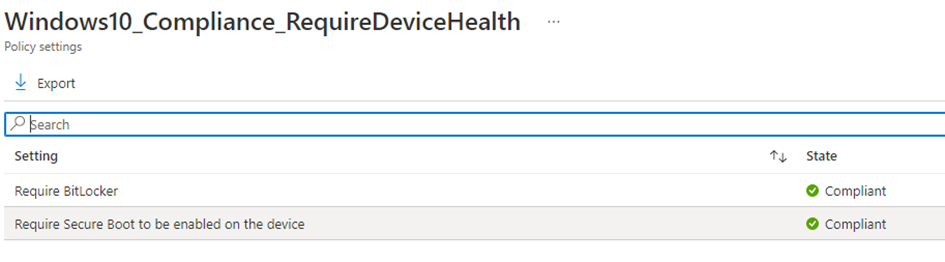
At the same moment, when the DHA service receives the Windows Health Attestation report with the Bitlocker status in it, the device will become compliant and you will no longer be blocked by Conditional Access!
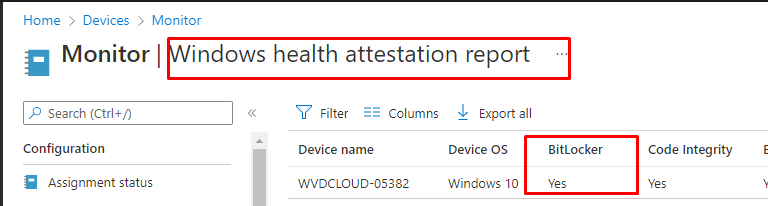
When you are no longer blocked by conditional access the MS store will start downloading the Company Portal App
After the Company Portal is successfully installed during the Account ESP phase, Autopilot will finish without any issues!
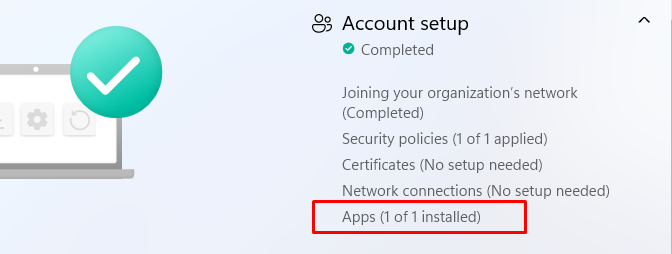
Please Note: If we perform the same enrollment but this time with an Endpoint security profile we will end up with a device with Bitlocker configured during the device phase but NOT enabled!
Conclusion
When Autopilot requires Online versions of Microsoft Store apps, it will contact the Microsoft Store to fetch the app. However, when you require a compliant device to access all cloud apps, it could take a while before the compliant status is measured and reported back to Intune. So please have a little bit of patience!

It takes some time to make the device compliant, so it could take a while before the app is installed.
Please Note: It could normally take up to about 5/10 minutes before it gets compliant during the Account ESP Phase, but it also depends on many other factors. I could assume when having 20.000 devices in your company, and they all start syncing at the same moment… you are up for another challenge
We are using a combination of the solutions I mentioned earlier to access the Online version of the Company Portal app.
- We are using a PowerShell script to enable Bitlocker until Microsoft will improve the experience when using a CSP to enable Bitlocker. When using PowerShell are pretty sure that during the device phase Bitlocker will be enabled. The device will reboot after finishing the device phase and it will report its Bitlocker status to the DHA service. After the reboot, it will start the account phase and after waiting some minutes to get compliant to pass the Conditional Access rule (All Cloud apps) it will start downloading the Company portal app.
A warning to finish the blog: There are situations when it could not be compliant in time, so keep that in mind!

