This blog will discuss some TPM Attestation issues you could encounter when running Windows Autopilot for Pre-provisioned deployments and how to troubleshoot them with a shiny new PowerShell Module.
1. Introduction
In one of my latest blogs, I showed you what happens when your device is “NOT Ready For Attestation” step by step!
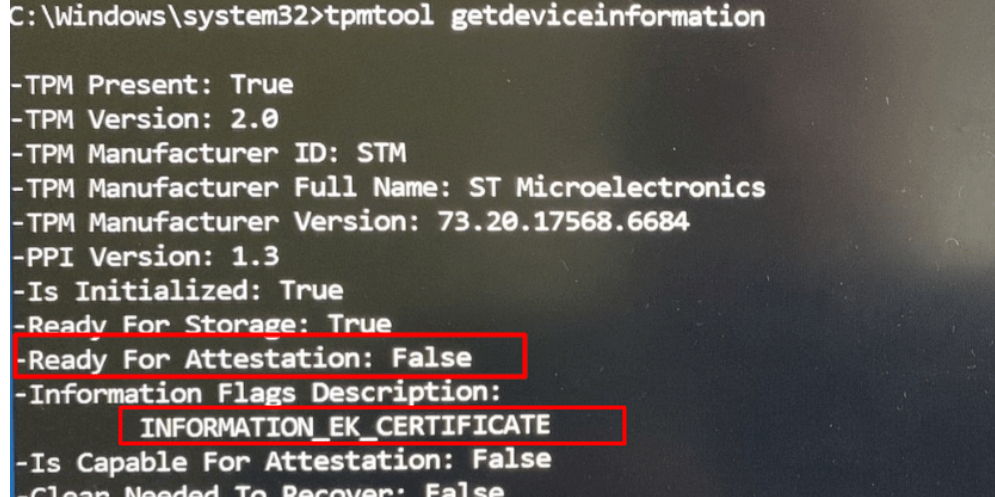
This blog also showed you how to deal with those attestation issues and how it really determines if the TPM is not ready for attestation.
That sounds great, right? But needing to troubleshoot all of these steps on your own isn’t great for most of us.

That’s why I decided to begin writing a PowerShell module that will check every single setting and try to perform some remediation while doing so.
2. The Script
I decided to upload my script to the PowerShell gallery. Uploading it to the PowerShell gallery was a job in itself, but it is working now….
When you want to start Autopilot PreProvisioning, you will need to make sure you start an additional cmd prompt. You could do so by using the Shift + F10 functionality. (If you haven’t disabled this wonderful feature)
Once you open the cmd, you will need to make sure you have opened PowerShell first before entering these commands.
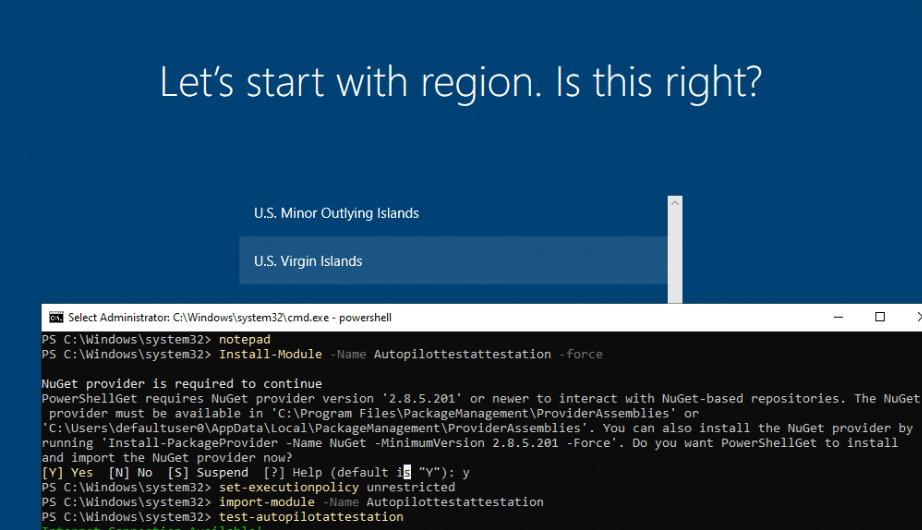
Install-Module -Name Autopilottestattestation -force
set-executionpolicy unrestricted
import-module -Name Autopilottestattestation
test-autopilotattestation
3. What does the Module do
When we are taking a closer look at what the Test-AutopilotAttestation script (AutopilotTestAttestation Module) actually does, we will notice the script will try to execute these steps!
- The script will check if there is an Internet connection
- Will determine if the required TPM supplier websites are accessible, to fetch the EKCert
- It will determine if the zero touch deploy Microsoft service is available, as the device will reach out to this Microsoft service to fetch its Autopilot profile
- It will check if the time service is running, if not it will try to start it and configure the peer list
- When it’s done checking the time service, it will determine if the license and product type is valid to be used in an Autopilot enrollment
- The script will query the TPM settings with WMI to determine if the device is capable of attestation and if not it will try to run some additional commands
- The additional commands will check if the device has the EKCert, and TCG log, if the TPM is owned, and if the TPM doesn’t have a vulnerable firmware
- With this output, it will try to start some TPM Tasks.
- If these tasks can’t be started it will again perform some remediation to make sure the TPM maintenance task could start
- If it performed the remediations, it would try to rerun the tests again
- If the device knows for sure it got an Endorsement Key, it will try to determine if it also got its required certs attached.
- Even when the TPM-Maintenance task couldn’t be executed I decided to call up the tpmcoreprovisioning.dll myself
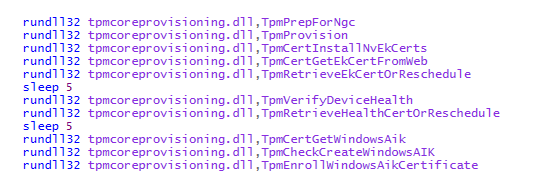
- If the device is ready for attestation and has the certs it will try to fetch the test-AIK certificate, 10 times.
- Depending on that outcome it will also try to test if the device is capable of attestation or the errors it got
- When it looks like it’s really ready for attestation, it will also run the AikCertEnroll task and will watch the error code output.
- Determining the error output it will show you if the device is ready for attestation or… not… If it’s ready for attestation you will get a nice GIF! Isn’t that nice?
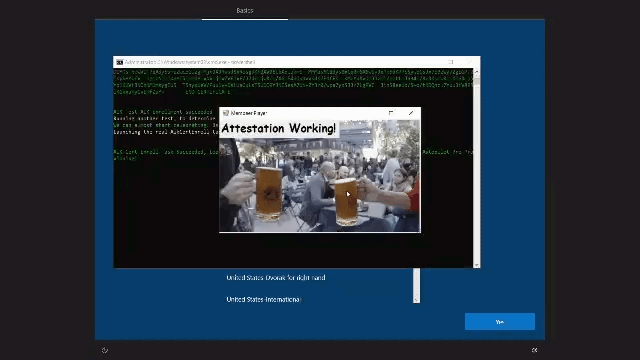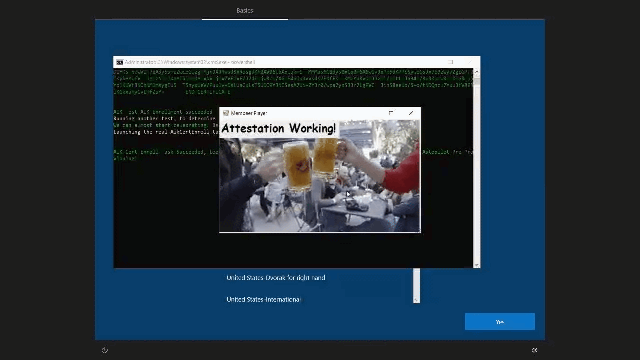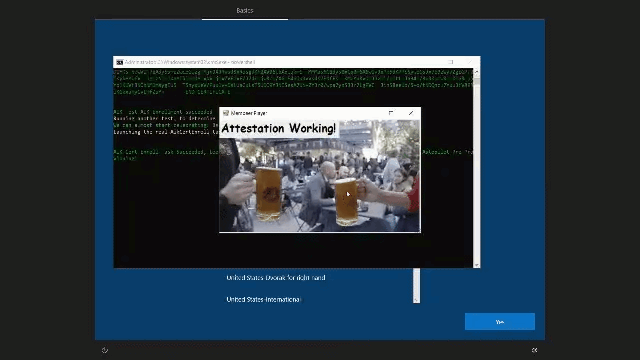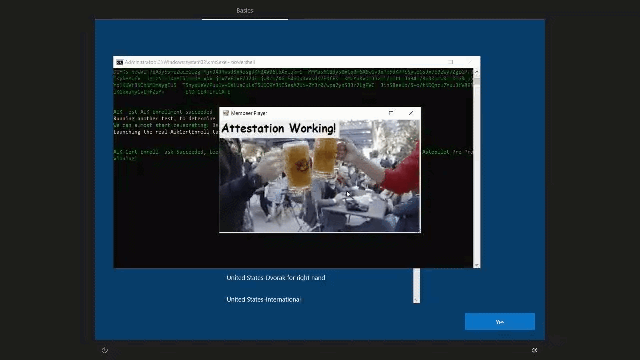
4. Results
When you are running this PowerShell module on a Virtual Machine it will fail and will tell you that the device isn’t ready for attestation. That isn’t a surprise, right?
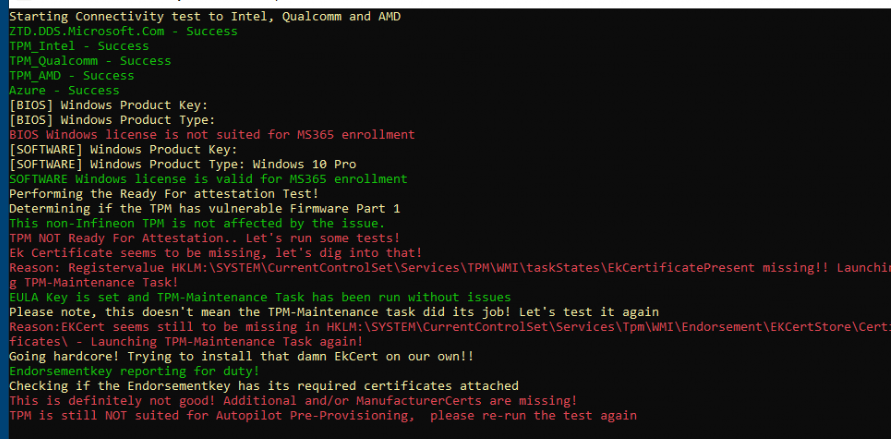
When running the same script on a physical device, the result needs to be green. Of course, as mentioned in part 3 it will also try to remediate (if possible) if something is broken
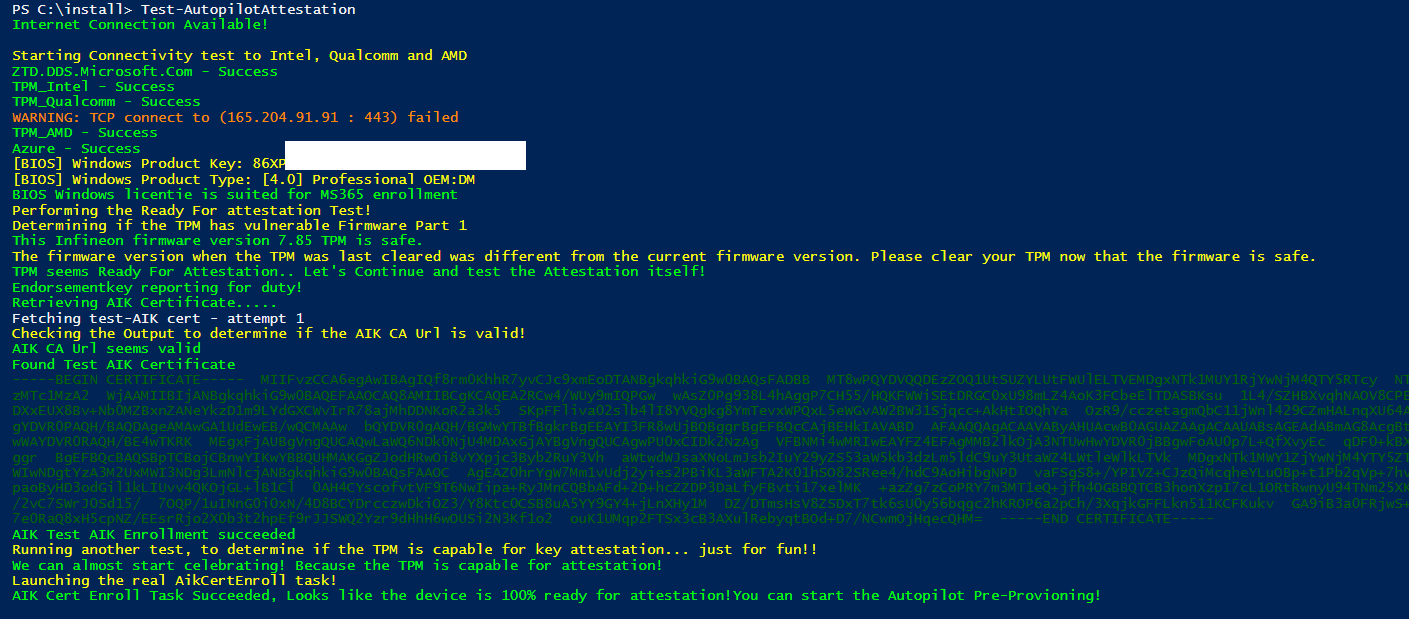
Conclusion
This is still a beta version and I am trying to ensure it doesn’t fail you. So please try it yourself and contact me if you encounter some weird issues!
With your help, we can build a PowerShell module to make sure, everyone can start troubleshooting their TPM attestation issues or we just th



get below error message:
Retrieving AIK Certificate…..
Fetching test-AIK cert – attempt 1
Checking the Output to determine if the AIK CA Url is valid!
AIK CA Url seems valid
AIK TEST Certificate could not be retrieved
Running another test, to determine if the TPM is capable for key attestation… just for fun!!
We can almost start celebrating! Because the TPM is capable for attestation!
Launching the real AikCertEnroll task!
Reason: AIK Cert Enroll Failed!
How to fix it, please? Thank you in advance.
Hi.. Could you take a look at this registry key $AIKError = “HKLM:\SYSTEM\CurrentControlSet\Control\Cryptography\Ngc\AIKCertEnroll\ and which errorcode that key has
more information for your reference:
SCEP Certificate enrollment for WORKGROUP\LAPTOP-VNL9760E$ via https://NTZ-KeyId-022cbeed5d77060f2833e9d5376ba8bc308cd9ba.microsoftaik.azure.net/templates/Aik/scep failed:
SubmitDone
Submit(Request): Bad Request
{“Message”:”No valid TPM EK/Platform certificate provided in the TPM identity request message.”}
HTTP/1.1 400 Bad Request
Date: Sun, 04 Sep 2022 08:48:13 GMT
Content-Length: 96
Content-Type: application/json; charset=utf-8
X-Content-Type-Options: nosniff
Strict-Transport-Security: max-age=31536000;includeSubDomains
x-ms-request-id: 89baaed4-4863-4e12-9699-cd4c088ed20c
Method: POST(11422ms)
Stage: SubmitDone
Bad request (400). 0x80190190 (-2145844848 HTTP_E_STATUS_BAD_REQUEST
Thanks.
Hi, Just as the message is telling you: No valid TPM EK/Platform certificate provided in the TPM identity request message
Could you check if the device has the ekcert installed? Could you list the output of this command: Get-TPMEndorsementkeyinfo I am curious if it has a valid certificate (additional or manufacture)
PS C:\WINDOWS\system32> get-tpmendorsementkeyinfo
IsPresent : True
PublicKey : System.Security.Cryptography.AsnEncodedData
PublicKeyHash :
ManufacturerCertificates : {[Subject]
TPMVersion=id:0755, TPMModel=Z32H330TC, TPMManufacturer=id:4E545A00
[Issuer]
CN=Nationz TPM Manufacturing CA 001, OU=Nationz TPM Device, O=Nationz Technologies Inc,
C=CN
[Serial Number]
24D5408891E7802343F30571D7ADB00FE0A91243
[Not Before]
11/5/2020 8:00:00 AM
[Not After]
11/5/2035 8:00:00 AM
[Thumbprint]
31239F7219E1CC63A9C58AFCE33A9774011AEC7B
}
AdditionalCertificates : {}
What kind of device is it? as the error you mentioned is normally be resolved by updating the firmware
AIK Cert Enroll Failed!
TPM has Vulnerable Firmware: True
TPM Firmware Vulnerability: 0x00000001
ADV170012 – IFX ROCA/Riemann
Hi, It looks like the TPM needs a firmware update. ON what kind of device are you testing this script?
Surface Laptop 4 with NTZ TPM.
Hi!
thanks for this script. Are IFX TPMs the only one with vulnerabilities? If not, will the script be updated to include checks for all vulnerable TPMs?
I also added another check to determine some other values that could indicate some other vulnerabilities..
And what about firmware? A lot of things would be better if the script automatically applied firmware patches and like stupid manufacturers told us why it didn’t succeed when it failed!
TPM firmware is always important… but I am not going to add that stuff 🙂 would be cool indeed if it was part of it but to determine which tpm you have and firmware and download the proper one is going to be a lot of work… 🙂
Thank you so much rudyooms!! This solved our TPM attestation problem (0x81039001) on ~20/1000 devices. Not sure why it was needed on these but since it’s solved, I don’t care anymore 🙂 You’re the best!
I have tried the script on my ryzen 5800x3d with all chipset and bios drivers updated to the last version.
I’m still not able to enable support for attestation through your script, obtaining an error at the end of the test saying: “Additional and/or ManufacturerCerts are missing!”.
How could i overcome this problem?
Hi.. this old blog is still unfortunately valid for AMD 🙁 https://call4cloud.nl/2021/11/the-pursuit-of-happy-uhhh-tpm-amd-happyness-part-3/
The only thing the script doesn’t do is fetch firmware and apply the update. Because my manufacturer can’t seem to make an update that actually works!
My HP TPM Configuration Utility reports the error occurred when attempting to prepare your computer for the firmware update and aborts.
No clue as to why. I’ve turned off TPM and virtualisation and still the firmware refuses to install.
Maybe I just have to live with a vulnerable Infineon 4.40 version 1.2 TPM?
This is the first time I can’t update a device firmware on my PC.
Does this check the registry for the EULA Accepted key and resolve it?
AS per :https://call4cloud.nl/2022/08/ready-for-attestation-a-true-underdog-story/#part6
This is our most common TPM issue with older HPs.
Using OSD?
Had this problem today 1/2/2023.
I followed your fix which resolved the problem. Many thanks
Hello,
It took me 3 days to be able to address my TPM chip correctly. Unfortunately the powershell script didn’t work for me.
After I decided to reinstall windows I ran into the actual bug which is also preventing the TPM chip from being used.
The following value was set in my registry: Computer\HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control -> PortableOperatingSystem = 1
After I set this to 0 and restarted the system, everything worked!
Maybe you can include this check in your script as well?
Yeah… Thats indeed a reg key that could mess with the tpm… Never noticed it before… Still odd that your device suddenly was marked as a windows to go device. Hoe did you reinstall the device?
The hint with portable OS was the hit !!!
This may have occured during hd change…
Can this also happen when using a user-driven Windows Autopilot configuration with an Azure AD hybrid join? I’m experiencing some trouble and, since on the same hardware a Windows Autopilot configuration with an Azure AD join works properly (e.g. no timeouts), I’m wondering if TPM attestation problem can be applied in the mentioned scenario 🙂
Thank you
Hi… Attestation issues should only occur at autopilot-preprovisioning or selfdeploying and maybe during health attestaion
hi
in my registry there is no ek certificate present can you help me with that as i need that for attestation and windows 11
thanks
Hi… what tpm are you using? (tpmtool getdeviceinformation)
-TPM Present: True
-TPM Version: 2.0
-TPM Manufacturer ID: INTC
-TPM Manufacturer Full Name: Intel
-TPM Manufacturer Version: 302.12.0.0
-PPI Version: 1.3
-Is Initialized: True
-Ready For Storage: True
-Ready For Attestation: False
-Information Flags Description:
INFORMATION_EK_CERTIFICATE
-Is Capable For Attestation: False
-Clear Needed To Recover: False
-Clear Possible: True
-TPM Has Vulnerable Firmware: False
-PCR7 Binding State: 0
-Maintenance Task Complete: True
-TPM Spec Version: 1.16
-TPM Errata Date: Wednesday, September 21, 2016
-PC Client Version: 1.00
-Lockout Information:
-Is Locked Out: False
-Lockout Counter: 0
-Max Auth Fail: 31
-Lockout Interval: 600s
-Lockout Recovery: 86400s
Which windows version/build are you using? I also assume you have installed the latest bios/firmwares. What happens when trying to run the tpm maintenance task?
my bios is fully updated and i have also run your powershell script which told me that “This is definitely not good! Additional and/or ManufacturerCerts are missing!
TPM is still NOT suited for Autopilot Pre-Provisioning, please re-run the test again
and i have ran your script multiple times and result is the same
this is my windows specifications
Edition Windows 11 Pro
Version 21H2
Installed on 03-Jul-21
OS build 22000.1516
Experience Windows Feature Experience Pack 1000.22000.1516.0
and also the maintenance task runs fine its just that my certificates in registry are missing or something
Mmm…could you contact me on twitter/linkedin? maybe we could figure something out so I could determine what is going on… as the intel tpm should get its ekcert
Could you install the tpmdiagnostics tool as I mentioned here: https://call4cloud.nl/2022/08/ready-for-attestation-a-true-underdog-story/
As you could try to fetch the ekcert from the web or nvr(but I assume you need to fetch it from the web)
I also assume, there is no proxy in play that blocks traffic to the intel cert services?
hi rudy
i think there is a bug or something for this webpage as earlier today i replied some messages but i am unable to see them now..
btw, i mailed you please reply asap
Hi.. Yep.. I just replied with some additional questions… (and hide the other comments to make sure the comment page was not flooded)
May god bless you. This is the one thing that will save my life…..
Invoke-webrequest -> causes to error when ie is not run yet ! use:
$WebResponse=Invoke-webrequest -Uri $imageuri -UseBasicParsing -Erroraction:Stop
$img=$WebResponse.Content
$gifbox.Image=$img
dont store stuf on your pc if its not needed ! this should work it did for me
the webresponse var you can use to check if the image is loaded but hey who cares
Hi, have you experienced getting this working on a vmware vm, running in vsphere? We have TPM provided by vsphere to the vm. From your script the issue seems to be with the AIK Cert:
AIK CA Url is not valid
AIK Test Certificate could not be retrieved
running another test …… just for fun!!
We can almost start celebrating …..
Launching the real AikCertEnroll task!
Reason: AIK Cert Enroll Failed!
I’m using the VMs for testing Intune and builds, and this is the last part I need to work on 🙁
Thanks in advance.
vTPM and attestation is not allowed. Those vTPMS are on a blocklist 🙂 … so no tpm attestation with virtual machines
This is gold. Have so far fixed issues on multiple devices devices. Thanks Rudy!
Hi Rudy,
Thank you so much for this script that I use quite often to solve Autopilot issues.
By any chance, would you know if this script could be used in a production context – AADJ devices already in production. We are trying to solve some issues we can have for reseting pin codes (WHFB)?
We are having error 0x800705b4 with an HP 14s-fq1000na. I have followed your (excellent) troubleshooting steps, and the problem seems to be with enrolling for the AIK certificate, which fails with a 404 error as the URL cannot be found. Further investigation shows that the AMD-KEYID is listed on the “Removed AIK” certificates list. I already have the most up-to-date TPM firmware for this system.
I assume the key is still listed on the block list because of the previous vulnerable versions as you mentioned in one of your blogs.
If this is the case, is there anything I can do?
Thanks!!! For now… the only thing you can do is contacting the hardware vendor :(… maybe its something they can address
hey there, can you add a force the membeer player window to stay upfront, its getting hidden behind my windows
Hi Rudy,
I have laptop Lenovo Thinkbook model 21MS, Device is getting failed during Autopilot provision with error ( 0x800705B4) TPM attestation Failed.
I have ran the script and got the error as below
AIK CA url is not valid
AIK test certificate could not be retrieved.
Reason:- AIK Cert enroll Failed.
This script has helped me revive a Dell laptop with Intel 6000 series CPU and TPM 1.2 module. I ran it, it worked, and I could install Windows 11.
The past few days I tried on 3 more identical laptops, and for some reason it only worked on 1 of them. I’ve tried on the Windows 10 that was provided, tried a reinstall, tried about anything I can think of yet nothing works. Any ideas?
Hello Rudy,
After Running your script i got this error:
Determining if the TPM has vulnerable Firmware
This non-Infineon TPM is not affected by the issue.
TPM is NOT Ready For Attestation.. Let’s run some tests!
Ek Certificate seems to be missing, let’s try to fix it!
EULA Key is set and TPM-Maintenance Task has been run without issues
Please note, this doesn’t mean the TPM-Maintenance task did its job! Let’s test it again
Reason:EKCert seems still to be missing in HKLM:\SYSTEM\CurrentControlSet\Services\Tpm\WMI\Endorsement\EKCertStore\Certificates\ – Launching TPM-Maintenance Task again!
Going hardcore! Trying to install that damn EkCert on our own!!
Endorsementkey reporting for duty!
Checking if the Endorsementkey has its required certificates attached
This is definitely not good! Additional and/or ManufacturerCerts are missing!
TPM is still NOT suited for Autopilot Pre-Provisioning, please re-run the test again
what kind of device do you have… do you have the output of the certreq -enrollaik -config “” (from elevated cmd… notpowershell)
Hi Rudy,
On a Carbon Gen 13:
In the CertReq_enrollaik_Output.txt I am getting:
Submit(Request): Bad Request
{“Message”:”Client challenge cannot be created due to failure in EncryptSecret”}
HTTP/1.1 400 Bad Request
Certificate Request Processor: Bad request (400). 0x80190190 (-2145844848 HTTP_E_STATUS_BAD_REQUEST)
Using the Test-AutopilotAttestation I’m getting this:
AIK TEST Certificate could not be retrieved
Reason: AIK Cert Enroll Failure
Have tried already Win 11 Ent 23H2 and Win 11 Ent 24H2 including Win 10 Ent 22H2 with all Windows Updates and no luck.
EKCert appears to be there. We are seeing this on multiple Carbon Gen 13’s.
seems like a bigger issue is going on…. this error has been shown to me alot the last few weeks