This time, a simple blog without technical details. It will be just me showing you why I am so enthusiastic about a specific service called MMP-C and why I assume this divine infrastructure service is going to change the whole idea of how we could manage our devices
1. The overview
Let’s start with a simple overview of what I am talking about to get a better understanding
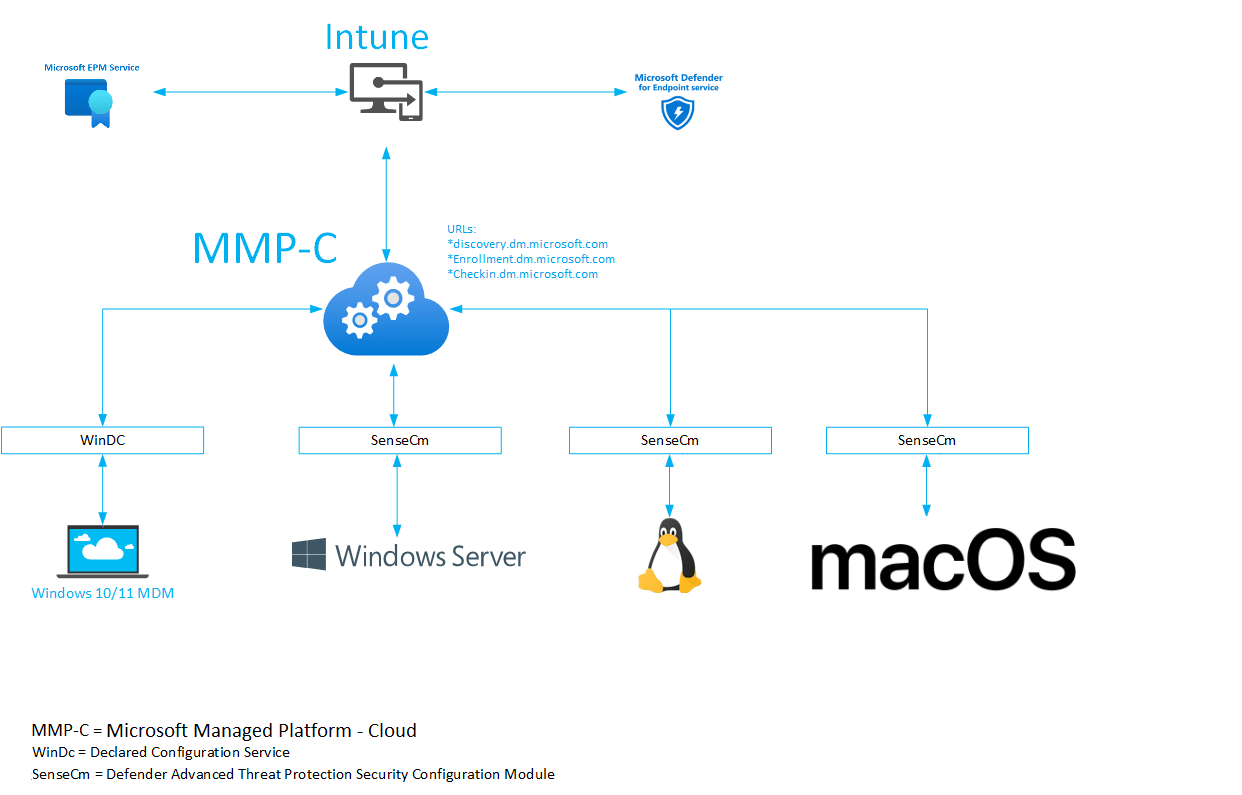
2. Explaining the overview
When we take a good look at the overview, we will notice that in the center of the universe, we can find MMP-C AKA Microsoft Managed Platform – Cloud (*.dm.microsoft.com)
This divine infrastructure seems to be (it is….)the one that ties everything together and gives all sorts of devices the possibility to retrieve policies.
For example, when using the wonderful Endpoint Privilege Management, we will notice that these EPM policies won’t arrive on the device with the use of the SideCar agent. When EPM is deployed, the device would use the WinDC service to communicate with MMP-C to retrieve the EPM policies you configured in Intune. Good to know is that the use of Declared Configurations is also way faster and way more secure
When taking a look at the new MDE Attach V2 (SIAM v2) we will notice that a NOT Entra managed server is using the Defender ATP SenseCm client to communicate with MMP-C. MMP-C would reach out to WinATP (defender) service to fetch the security management policies you configured. For now, we are still stuck to only some Antivirus, ASR, EDR, and Firewall policies but this is just the beginning of something great, right?
The same goes for Linux and MacOS devices. When we take a closer look at how those devices communicate with the service, we will again spot the MMP-C URLs (dm.microsoft.com) being mentioned
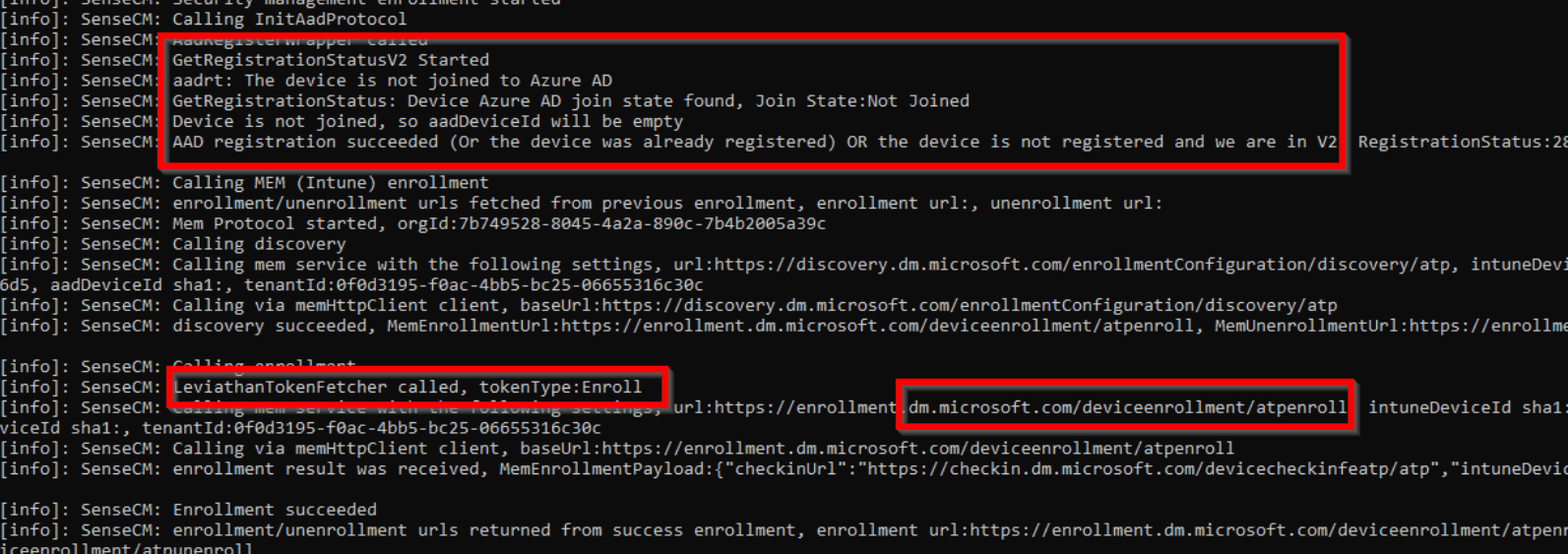
We will notice that all of those devices that are using MDE attach V2, don’t rely on an Intune enrollment but an enrollment into MMP-C. Those MDE-managed devices don’t even require the device to be Azure Ad Joined, which is great! Instead of the Azure AD token, the MMP-C enrollment and check-in rely on the Leviathan token!
With this newfound power, I guess the possibilities are endless! Microsoft is revolutionizing device management and bringing it to a higher level! Just thinking about it, you don’t any longer need to hybrid join your servers to push Intune policies to those devices. Doesn’t that sound wonderful?
When thinking about it, I only noticed how important MMP-C is; I can’t even start to imagine what Microsoft needed to change at the other services (Intune) to get this all working. I guess that part would always be hidden in the fog…
If you want to know more about how this service works and how the devices communicate with MMP-C, you should definitely read my blogs about MMP-C and WinDC. Those blogs will show you the tip of the iceberg!
MMP-C – Call4Cloud | MMP-C | WinDC | Autopilot | Intune
Conclusion
The first time I talked about MMP-C publically was at MMSMOA 2023, so everyone who was at that session and didn’t know what I was rambling about…. this was it! The last thing I want to add is that I am f.. amazed by how this service is put together and how it communicates with the other existing services.



Blows my mind more folks haven’t commented here but this is truly amazing.
Also big thanks to you for providing this information to us, can’t wait to see it evolve.