This blog will focus on the importance of the Enrollment Time Group (JustIntTimeConfiguration), which is currently only used with Autopilot Device Preparation.

1. Introduction
The moment Autopilot Device Preparation was shown to the world, another essential brick of that process was also announced.
This brick is the Enrollment Time Grouping (ETG), also known as Just In Time Configuration. This group is a significant requirement for a smooth Autopilot Device Preparation enrollment. Why, let me explain…
This device security group is a just-in-time group, AKA an enrollment time group. It ensures that your device automatically becomes a member of this group during enrollment instead of after. This allows Intune to deliver configurations, reduce post-enrollment latency, and improve productivity quickly.
With your device automatically becoming a member of this group the moment you enroll your device, you can assign your Win32 Apps and Policies to it. (instead of using all devices).
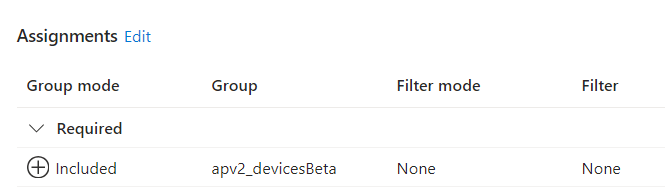
With the apps and your security policies assigned to this specific group, you can ensure that devices enrolled with Autopilot Device Preparation will get all the required apps and policies installed. If you don’t use this group, it could take some time before the apps appear.
It’s good to know that when a device is removed from this enrollment time group, Microsoft Intune reexamines the policy configurations and prompts the device to check in to receive updated configurations.
With all of this power, I guess it’s safe to say that this enrollment time group is essential for the whole Autopilot Device Preparation enrollment. Let’s take a look at how we set it up!
2. Configure the Enrollment Time Grouping
Before we could configure the Autopilot Device Preparation profile, we first need to create a new device security group.
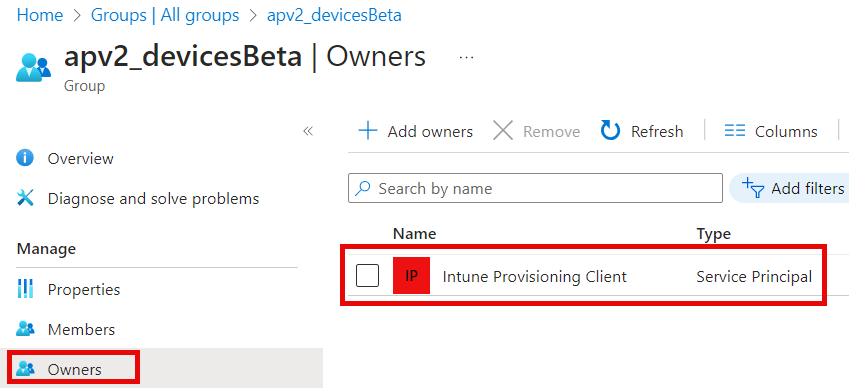
One of the most important rules when creating this security is to define the Intune Provisioning Client service principle as the owner. If you don’t configure the proper owner, saving the Autopilot Profile will error out!
If the Intune Provisioning Client service principle is missing, we must create it using PowerShell and manually connecting to Entra. Once connected to Entra, we can fire off this script.
import-module AzureAD
Connect-AzureAD
New-AzureADServicePrincipal -AppId f1346770-5b25-470b-88bd-d5744ab7952c.
This script will ensure that it will be created if the service principle is missing. Once this device security group is created, we can configure it in the corresponding Device Preparation policy.
As mentioned before, saving the profile will give you an error if this group doesn’t have the proper owner.
3. The Graph Behind it
As always, when configuring something in the portal (which could give us false errors), we can also use Microsoft Graph to check if the profile was saved with the proper Entra security group.
To retrieve information about this Just In Time Assignment Policy, we must perform a GET operation to this URL. As shown below, you need to change the policy ID to the ID of the Device Preparation Policy
If we perform a GET to this URL, it should show us the target. This target is, in fact, the ID that corresponds to the Enrollment Time Group.
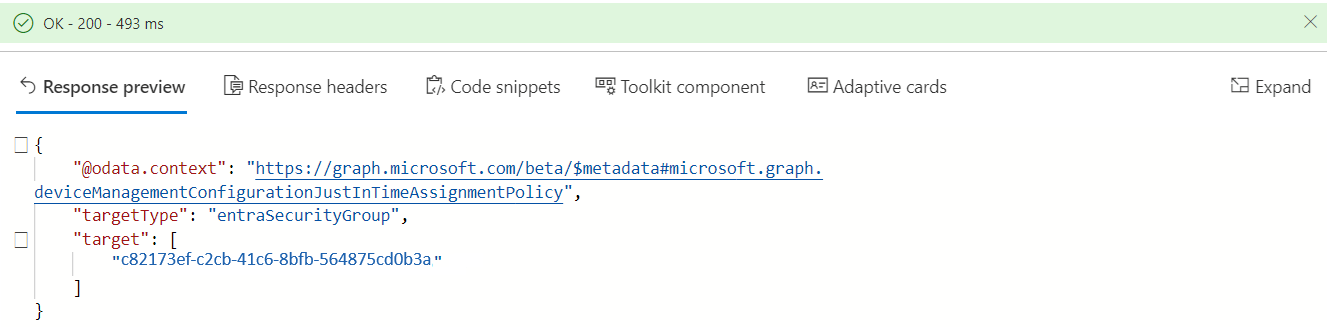
As shown above, everything looks good, right? Shall we check out how our device is being added to this Enrollment Time Group during the Autopilot Device Preparation Enrollment?
4. The Flow
As mentioned in the introduction, when enrolling the device with Autopilot Device Preparation, the device automatically becomes a member of this group. It almost sounds like magic, right? This happens once you log in with your credentials and look at the “ Please Wait” screen.
Please download the file to make it a bit more readable
https://call4cloud.nl/wp-content/uploads/2024/06/apv2-device-group.gif
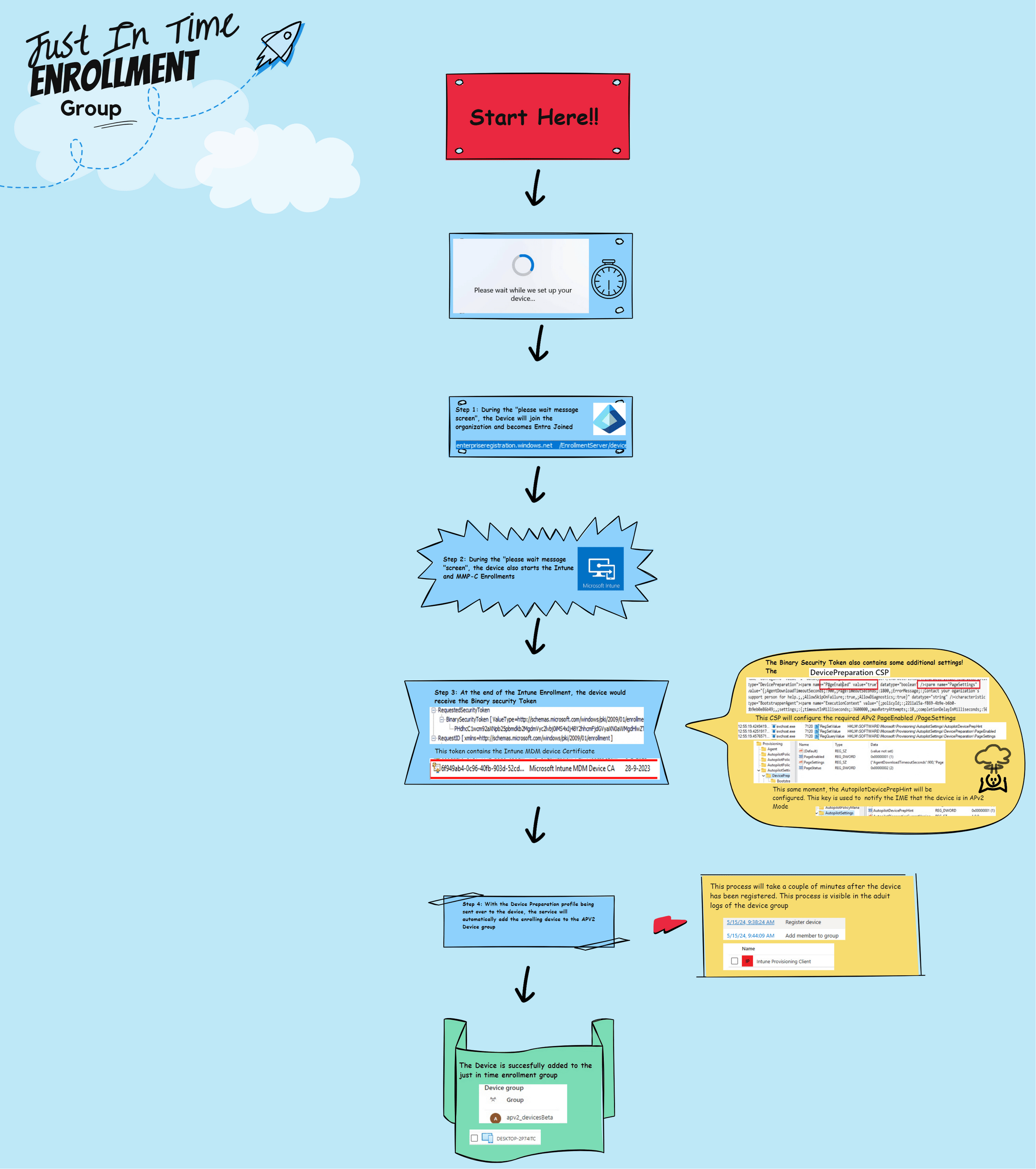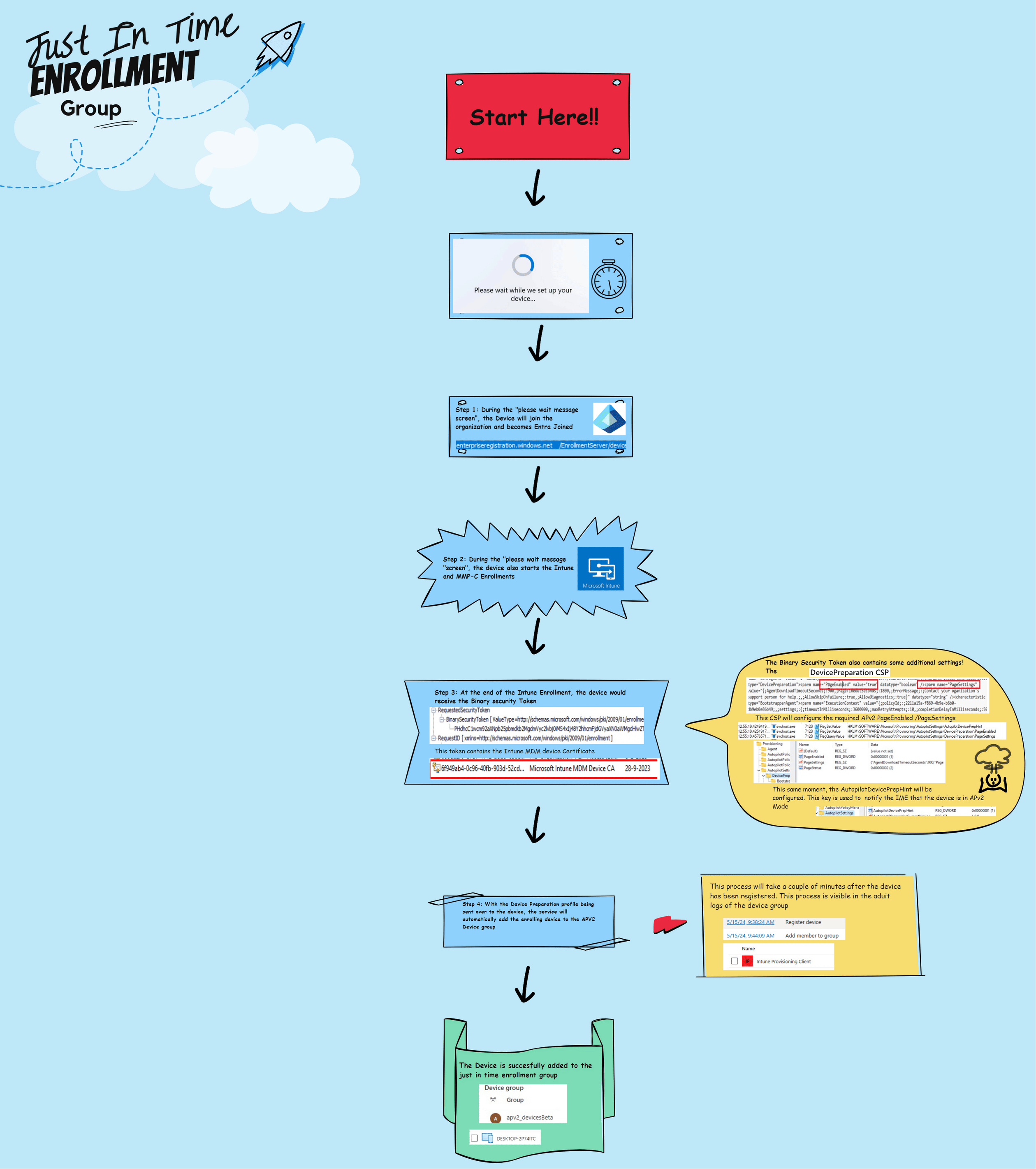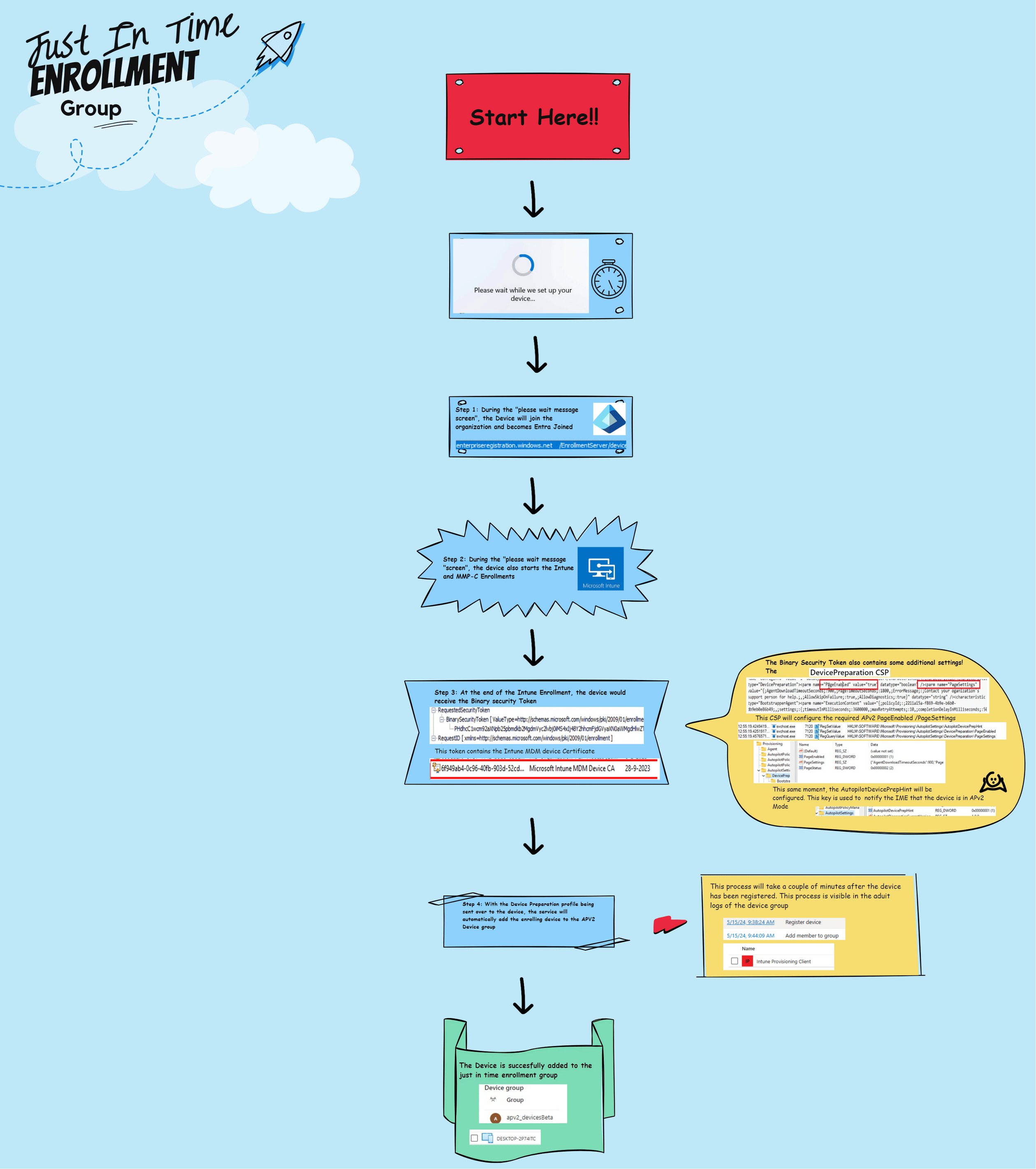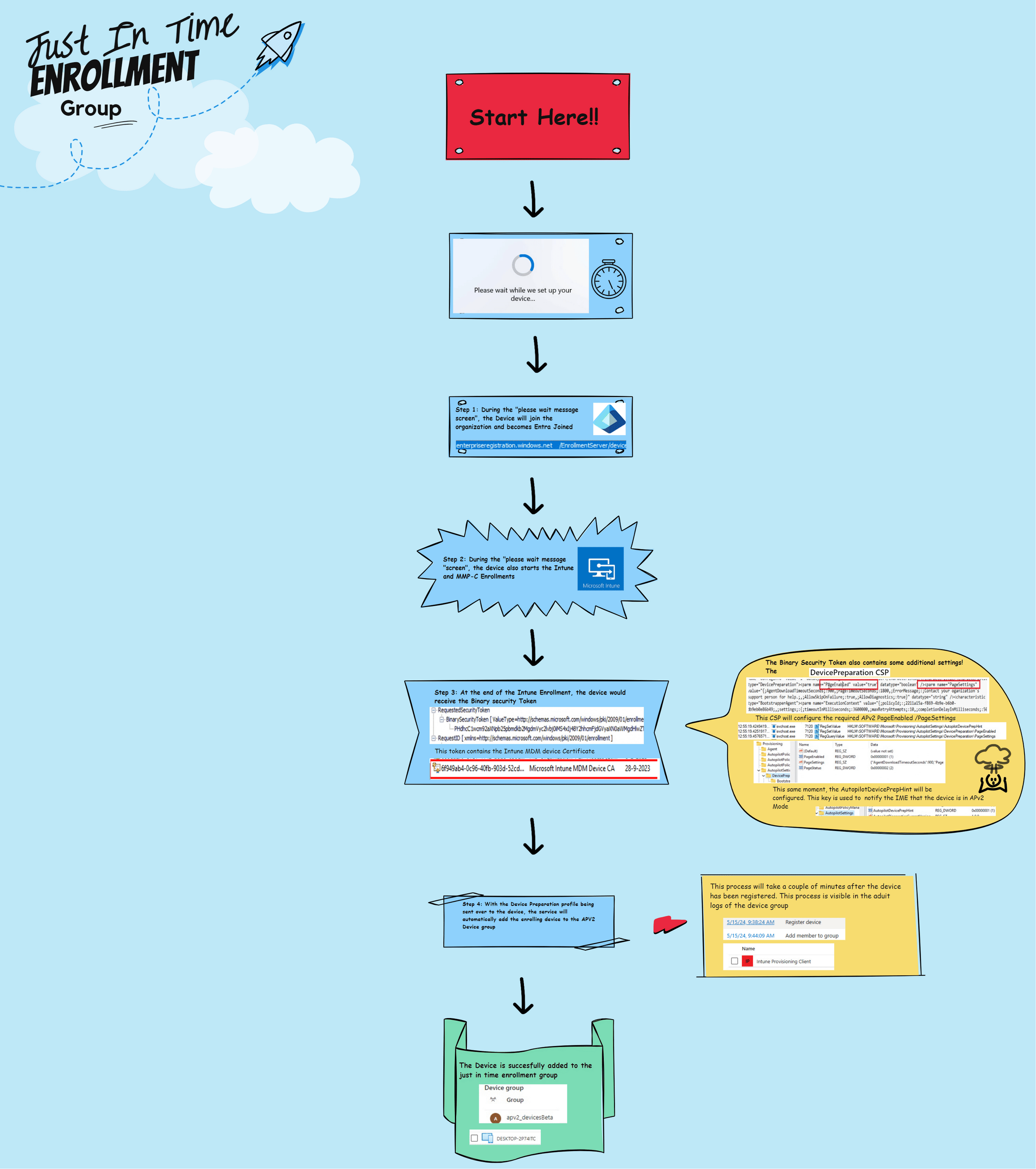
5.The details behind the flow
Summary of How the Device is Added to the Security Group (SG), also known as the Just-In-Time Enrollment Group:
1. When a device is enrolled with Autopilot Device Preparation, the first screen we will get is the “Please Wait” screen. During this screen, a lot is happening in the background.
2. In the background, the device will start joining Entra ID. After the device has been successfully enrolled into Entra and members from the local administrator group have been removed, the Intune Enrollment will be kicked off.
3. To start the enrollment, the device would send out its username/device ID information, etc, to the service (Binary security Token).
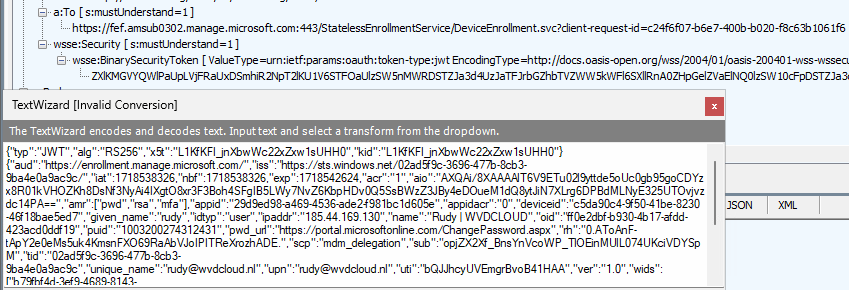
With the username sent over, the service knows that the user has an Autopilot Device Preparation policy assigned. If the user has an ADP Policy assigned, the service knows it needs to send the policy to the device to enable the Device Preparation Mode.
The service would send the MDM certificate and the required Autopilot device preparation profile, as shown below.

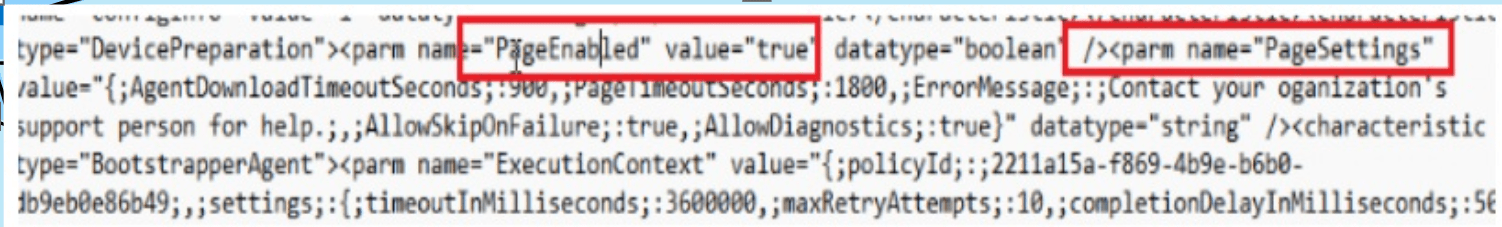
4. With this device preparation policy sent to the device, the service also knows it must start adding the device to the just-in-time enrollment group. The Intune Provisioning Client will take care of this process.
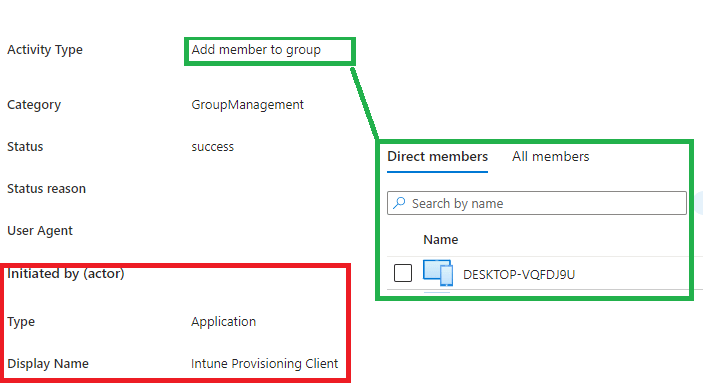
This whole process seems to be happening in the background on the service side. I assume it is happening on the service side, so we can’t mess with it, AKA Security Reasons.
5. Once the device is enrolled with Intune, the Intune Management Extension (IME) installation will be executed to start the provisioning process. Based on prior checks, the device is assumed to have already been added to the enrollment time group. From there on, the device would start syncing with Intune and send the DevicePrepSync alert to the service regarding the provisioning status.
When looking at the documentation about this DevicePrepSync alert, these are the 4 phases the device preparation sync could show.
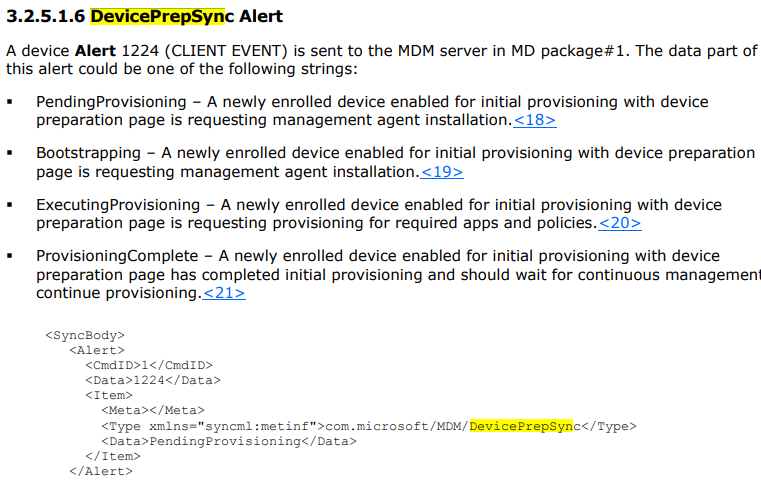
The provisioning will go through those 4 steps, and at the end, it will send out the ProvisioningComplete alert to mark the enrollment as completed.
Conclusion
The Enrollment Time Group is essential to the Autopilot device Preparation process. This group ensures you can target the apps and policies for your Autopilot Device Preparation devices. Without this group, we could have devices without any apps or policies deployed.
I am glad that Microsoft has also published the corresponding documents about this magical group! Go check them out! Set up enrollment time grouping – Microsoft Intune | Microsoft Learn


