Microsoft has continuously refined how Windows handles Subscription Activation, particularly in environments with strict Conditional Access policies. These changes are key to providing a smoother user experience and enhanced security. In this post, I’ll guide you through the evolution from initial workarounds to a more secure, user-specific solution in the latest Insider build. This shift marks a significant step in resolving the activation issues many of us have faced.
1. The Journey from Temporary Fixes to Robust Solutions
Initially, organizations faced issues with Subscription Activation, particularly when Conditional Access policies were applied. To avoid failures, administrators had to exclude two specific cloud apps—Universal Store Service APIs and Web Application and Windows Store for Business, as discussed in detail in this blog post. This exclusion was necessary because the Conditional Access policies would block the activation process.
To mitigate this, Microsoft introduced the MfaRequiredInClipRenew function.
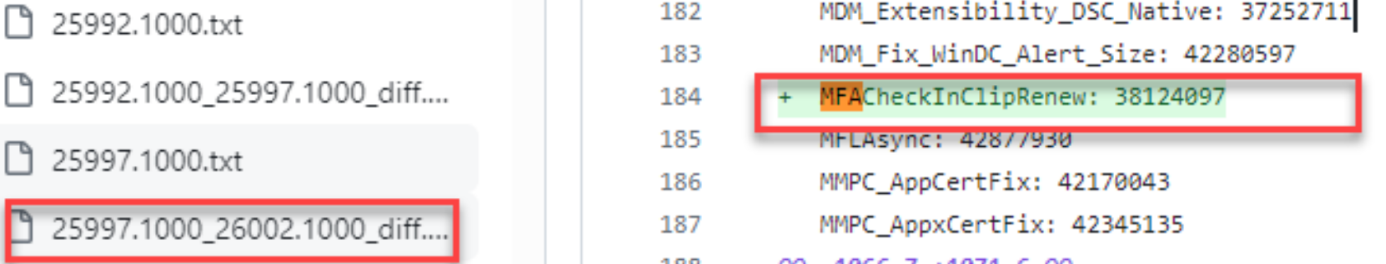
Starting with Windows 11 version 23H2 and the KB5034848 update, Microsoft has introduced this MfaRequiredInCliprenew feature. Users will receive a toast notification prompting them to authenticate when Subscription Activation needs to be reactivated.
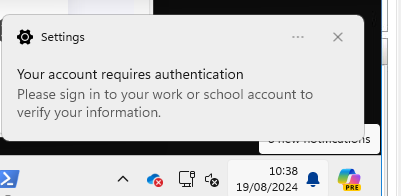
The notification displays the message: “Your account requires authentication. Please sign in to your work or school account to verify your information.” Besides the toast notification we could also spot the same message when clicking on the toast notification and opening the work or school account settings
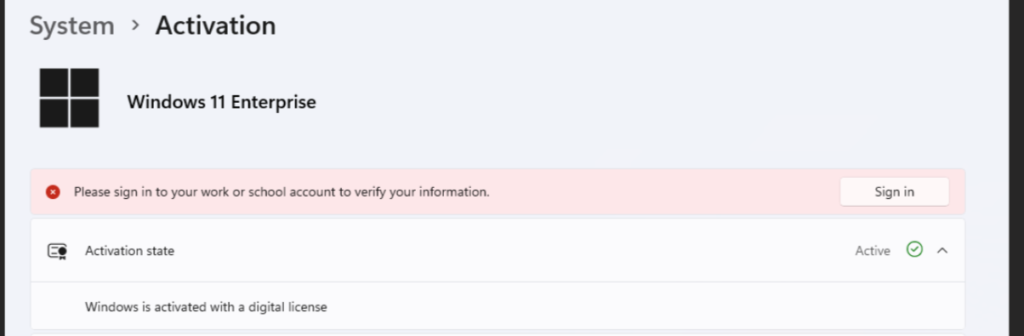
This prompt typically appears when a device has been offline for an extended period. This change removes the need for Conditional Access exclusions for Subscription Activation, simplifying the process while enhancing security.
However, this approach introduced a new challenge: the activation task ran under the interactive user account, and the logged-in user didn’t have the necessary permissions to create this key in HKLM.
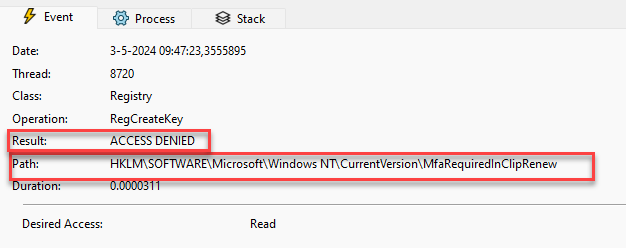
If this registry key wasn’t created successfully, the LicenceAcquistion scheduled task would error out and would throw the access is denied error (0x80070005)
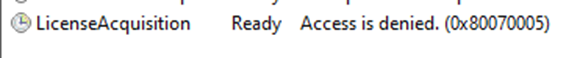
This issue caused new devices to fail to upgrade to Windows Enterprise and caused existing devices to revert back to Windows Professional.
To address this, I developed a PowerShell script that adjusted permissions to allow the task to be completed successfully. Feel free to read the full story that led me to the fix.
However, this solution was only a temporary fix. Recognizing all the subscription activation issues, Microsoft introduced the Handle_Access_Denied mechanism, allowing the system to retry operations upon encountering permission issues.
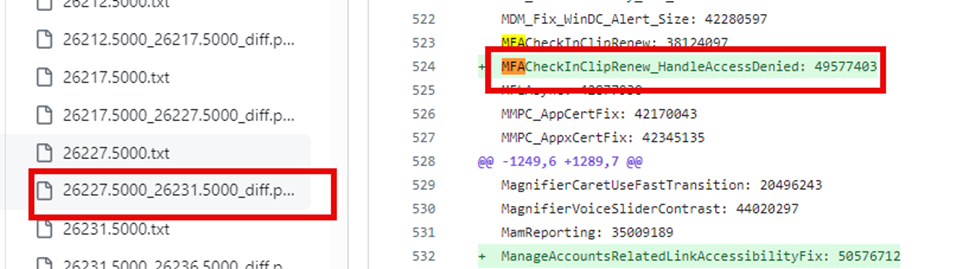
While this provided some relief, it added complexity and didn’t fully resolve the underlying problem. Read the full handle_access_denied story here on the Patch My PC Website:

2. The Shift to User-Specific Registry Paths
With the release of Insider build 27686.1000, Microsoft has taken a significant step forward by introducing the ChangePathRegistryKeyForMFAFeature.
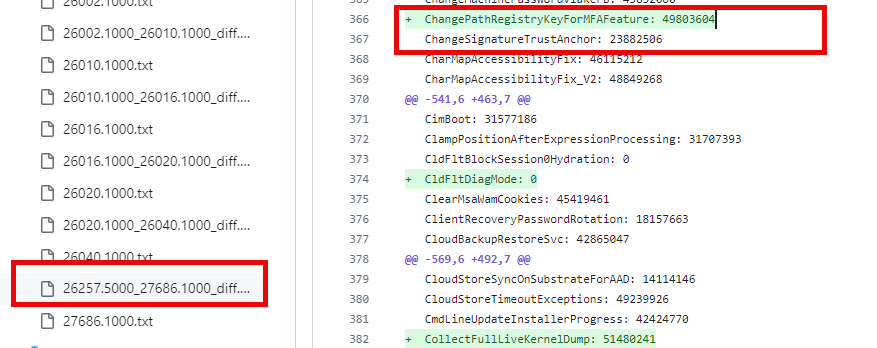
This ChangePathRegistryKeyForMFAFeature relocates the MfaRequiredInClipRenew registry key from the machine-level HKLM to a user-specific registry path.
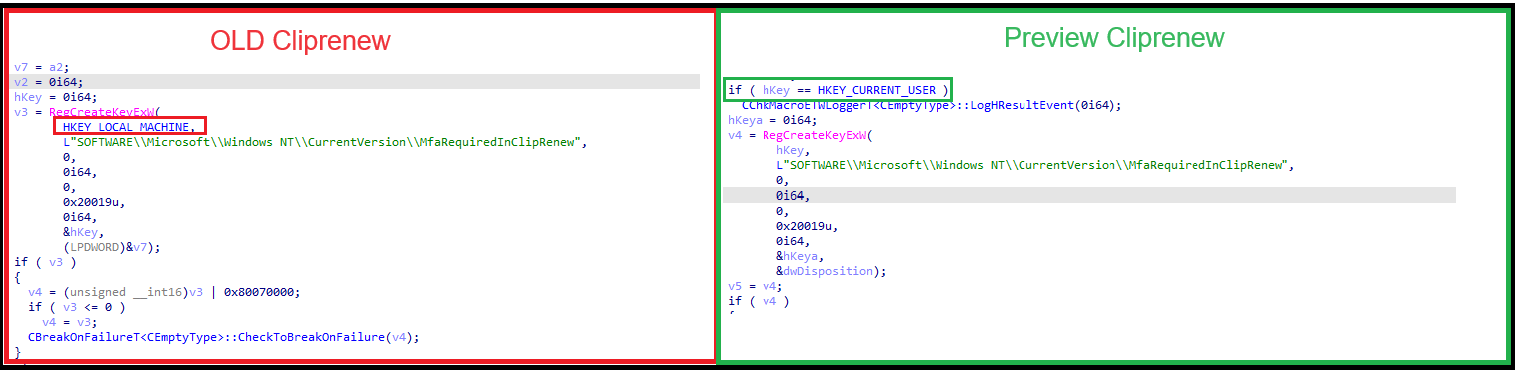
We can spot this new behavior when looking at the HKEY_CURRENT_USER key. As shown below, I now have the MFARequiredInClipRenew registry key in my user account registry hive.
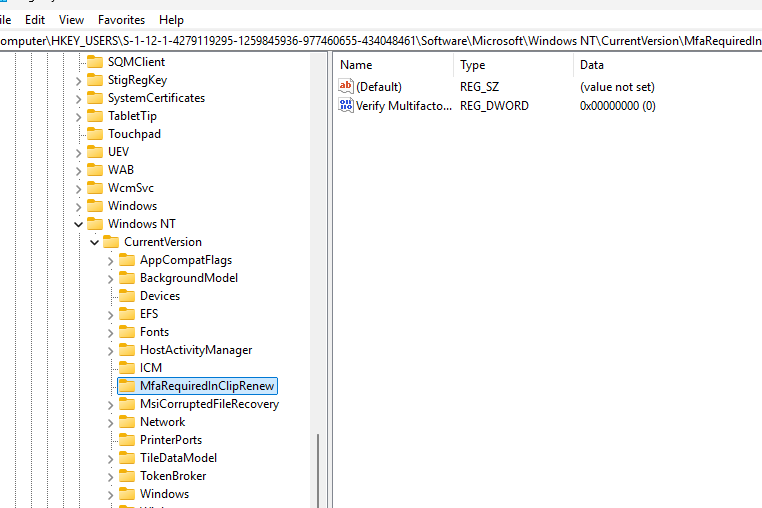
Besides this new location, we can, of course, spot the same flow when running Procmon. As shown below, it will try to find the logged-in user and will create the MFARequiredInClipRenew registry key if it doesn’t exist.
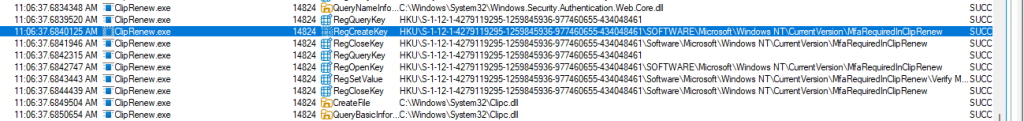
This shift is transformative for several reasons:
- User-Centric Security: Moving the key to a user-specific location ensures that MFA requirements are enforced on a per-user basis, reducing the risk of unauthorized access. Each user’s settings are now isolated, making security policies more effective and easier to manage.
- Streamlined Conditional Access Management: With the key now stored in the user’s registry path, the need to exclude specific cloud apps from Conditional Access policies is eliminated, greatly simplifying policy management.
- Eliminating HandleAccessDenied: The user-specific approach makes the Handle_Access_Denied fix obsolete. Microsoft has removed this workaround entirely, as the root cause—permission issues at the machine level—has been effectively resolved by moving the registry key to a more appropriate location.

3. What This Means for Users and Admins
For end-users, the transition to user-specific registry paths means a more seamless activation experience. When the system needs to reactivate—especially after a device has been offline—users will receive a clear toast notification prompting them to authenticate. This direct interaction streamlines the activation process and minimizes disruption.
I simulated this by revoking the user session and clearing out the tokens in the user tokenbroker cache folder
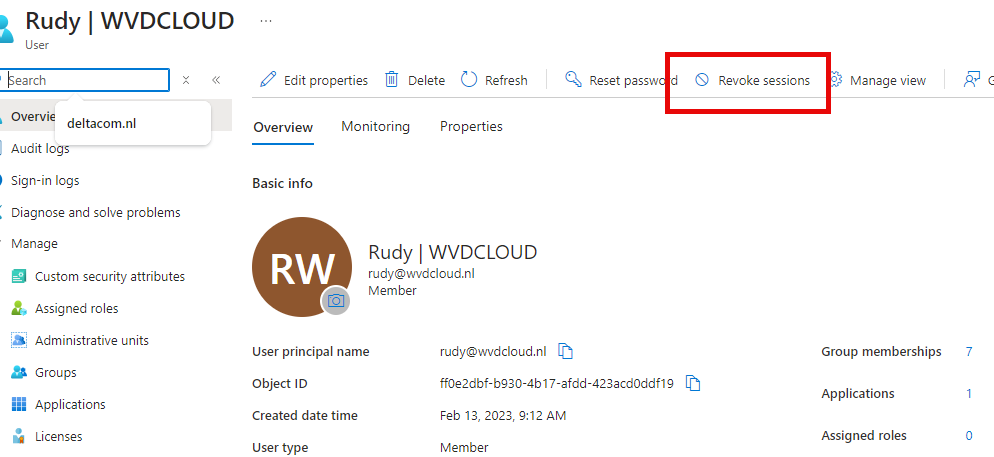
Once the session is revoked, we will get this behavior when we need to authenticate!
I need to add a small note: I got a UAC prompt at the end of the video, but I could just click on the cross to ditch it.
For administrators, removing the need for Conditional Access exclusions and deprecating the HandleAccessDenied mechanism simplifies the overall management of Subscription Activation. By aligning the activation process more closely with user profiles, Microsoft has reduced the complexity of managing Conditional Access policies and enhanced overall security.
4. Looking Forward
As Microsoft continues to refine Subscription Activation, the changes we’ve discussed are set to become standard, but they’re currently being tested in the Windows 11 Insider Preview Build 27868 in the Canary Channel. These updates focus on moving towards a more user-centric approach, which will significantly improve the security, reliability, and manageability of Subscription Activation. While we will need to wait a bit longer for these features to arrive in the regular build, these developments mark a crucial step forward in enhancing the overall user and administrative experience. Stay tuned as these updates progress towards broader release.



Hi Rudy,
I’ve found your blog invaluable in the past year, particularly around subscription activation where we deployed your workaround powershell script for many of our customers. One question here is, this is obviously now fixed my Microsoft in the latest patch. However, the script we deployed with a proactive remediation is now no longer being applied. However, the script has naturally tattooed the changes. I’ve read a few of the blog posts on this and I’m not quite sure what changes we need to put in a script to revert the registry back to normal.
Is it the case of just deleting the MfqRequiredInClipRenew path?
Maybe I am missing something….. I’ve followed these Activation issue articles since the beginning.
I am still not seeing the change to HKCU instead of HKLM in our Windows 11 23H2 latest patched systems.
Is this only in 24H2 or really isn’t in the production builds at all yet?
Any thoughts?
I am having the same results, HKLM yes, HKCU no on Windows 24H2.
I upgraded to 24H2 and same, still in HKLM and not in HKCU.
Not sure what I am missing here.
Anyone have any thoughts?
Thanks