The past year I blogged a lot about securing and monitoring your devices. Of course, Microsoft 365 E5 is the way to go when you want to maximize your security, but for the SMB the license can be too expensive. For these customers, Microsoft 365 business premium is the best choice. But when you choose Microsoft 365 Business premium you can’t make use of the advanced security features.
Of course, by now you have implemented adminless and AppLocker on your devices but what about monitoring AppLocker? When we can’t use the full E5 license, do we need an additional monitoring tool like Solarwinds/N-Able to make sure AppLocker notifications are monitored?
The answer is: NO.
I have come up with this solution. (I tried it with Proactive remediations, but did not like the 1-hour delay) It still needs a little bit of work and polishing but I like it so far… I am going to create a new Win32 app that creates a scheduled task to monitor the AppLocker event log and will send a message to a specific team’s channel with all the information you need when an 8004 event occurs. In my opinion, you need to know if a user tries to open PowerShell for example (why do end-users need access to PowerShell?)
As an IT reseller, you will have multiple customers you may want to monitor. There are some steps to be taken.
- Create teams/channels and the connectors and make sure the channel notifications are enabled
- Create the PowerShell script to send notifications with the AppLocker event
- Create the PowerShell script to create a scheduled task to monitor the AppLocker event log
- Create the Intunewinapp and push it to the devices and start testing!
Step 1:
The first step you will need to take is to create a new team. In my example, I created a new team: customers inside this team I created a channel for each customer we want to receive notifications for.
When you have created the channels, you can add a webhook connector to it.

Step 2 and 3 combined:
Now we are going to create the PowerShell script. It contains 2 parts, the send to teams’ part and creating the scheduled task with an event log trigger. (You will need to replace the webhook web URL in the script below)
##################
# Create the ps1 #
##################
$content = @'
#########################
#send to teams function#
#########################
function Send-toTeams {
param (
[Parameter(Mandatory=$true)]
$webhook,
[Parameter(Mandatory=$true)]
$text
)
$payload = @{
"text" = $text
}
$json = ConvertTo-Json $payload
Invoke-RestMethod -Method post -ContentType 'Application/Json' -Body $json -Uri $webhook
}
#########################################
# Device/tenantname/teams kanaal #
#########################################
$channel = “URL FROM THE WEBHOOK CONNECTOR!!!!!!!!”
$compname = $env:computername
$tenant = Get-ItemProperty -Path HKLM:\SOFTWARE\Microsoft\Provisioning\OMADM\Accounts\*\Protected -name "Name"
$tenantname = $tenant.name
$message = $result.message
$username = (Get-WmiObject -Class Win32_Process -Filter 'Name="explorer.exe"').
GetOwner().
User
#########################
#Applocker events zoeken#
#########################
Try {
$Result = get-winevent -FilterHashTable @{LogName="Microsoft-Windows-AppLocker/EXE and DLL";StartTime=(get-date).Addseconds(-300)}|Where-Object{($_.id -eq 8004) -and ($_.message -notlike "*CMD.EXE*") -and ($_.message -notlike "*GPSCRIPT.EXE*") }
$message = $result.message
$text = $message+" | "+"Klantnaam:"+$tenantname+" | "+"Computernaam:"+$compname+" | "+"Gebruikersnaam:"+$username | convertto-json
$ID = $Result | measure-Object
If ($ID.Count -gt 0)
{
send-toteams -webhook $channel -text $text
Exit 1
}
Else
{
Write-Output "No applocker events found"
Exit 0
}
}
catch{
$errMsg = $_.Exception.Message
Write-Error $errMsg
exit 1
}
'@
###########################################
# create custom folder and write PS script#
#############################################
$path = $(Join-Path $env:ProgramData CustomScripts)
if (!(Test-Path $path))
{
New-Item -Path $path -ItemType Directory -Force -Confirm:$false
}
Out-File -FilePath $(Join-Path $env:ProgramData CustomScripts\applockernotifcations.ps1) -Encoding unicode -Force -InputObject $content -Confirm:$false
#######################################
#Second part!!! register script as scheduled task#
######################################
$class = cimclass MSFT_TaskEventTrigger root/Microsoft/Windows/TaskScheduler
$trigger = $class | New-CimInstance -ClientOnly
$trigger
$trigger.Enabled = $true
$trigger.Subscription = '<QueryList><Query Id="0" Path="Microsoft-Windows-AppLocker/EXE and DLL"><Select Path="Microsoft-Windows-AppLocker/EXE and DLL">*[System[EventID=8004]]</Select></Query></QueryList>'
$ActionParameters = @{
Execute = 'C:\Windows\system32\WindowsPowerShell\v1.0\powershell.exe'
Argument = '-NoProfile -File c:\ProgramData\CustomScripts\applockernotifcations.ps1'
}
$Action = New-ScheduledTaskAction @ActionParameters
$Principal = New-ScheduledTaskPrincipal -UserId 'NT AUTHORITY\SYSTEM' -LogonType ServiceAccount
$Settings = New-ScheduledTaskSettingsSet
$RegSchTaskParameters = @{
TaskName = 'Applockernotification'
Description = 'Runs at Applocker event 8004'
TaskPath = '\Event Viewer Tasks\'
Action = $Action
Principal = $Principal
Settings = $Settings
Trigger = $Trigger
}
Register-ScheduledTask @RegSchTaskParameters
When looking at the complete script, you will notice I am searching for some more information to get the device, tenant, and username from which the Applocker event occurred. This information is necessary to act on.
Step 4.
Now we have the PowerShell script we can create a new Intunewin app and push it to your devices.


Now the app is ready and deployed to our clients, we can start testing. Try to open something you blocked with AppLocker (Look at my other AppLocker blogs to get a good list of files you will need to block)

Looking closer at the message itself, you will notice:
Company name, Device name and username
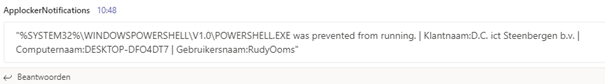
Isn’t it cool you can receive notifications when someone tries to open applications which they don’t have access to?
Conclusion:
Some time ago, I had an email conversation with Alexander Fields about the possibility to get rid of all additional tools and still be able to take care of your customers.
I guess this solution to monitor your devices is a decent step in the right direction. Eyes bright, chins up, smiles on. We can monitor Applocker without third-party tools. And Applocker is just one of the many examples you can monitor with this idea.


Great idea and implementation. But how can we avoid a loop, because of the “psscriptpolicytest”-Files? If we create a powershell-script with a trigger in the eventlog for errors of blocked scripts, every time this script tries to run another error shows up for blocked files of this script and so on…
To allow the Hash of the pssscriptpolicytest-file seems not to be the best option.