Provisioning non-Entra enrolled Windows Pro devices with AppLocker can be quite challenging since AppLocker isn’t officially supported on Windows 10 Pro without using Intune… or so I thought! With a little research and some unconventional scripting, I managed to make AppLocker work on these devices.
To do so I wasn’t relying on Intune or upgrading to Enterprise editions but using the WMIBridge
Why AppLocker is Tricky on Windows Pro
When trying to configure AppLocker on a Windows Pro device, you’ll notice a peculiar message appear in the event logs: Component not available on this SKU.
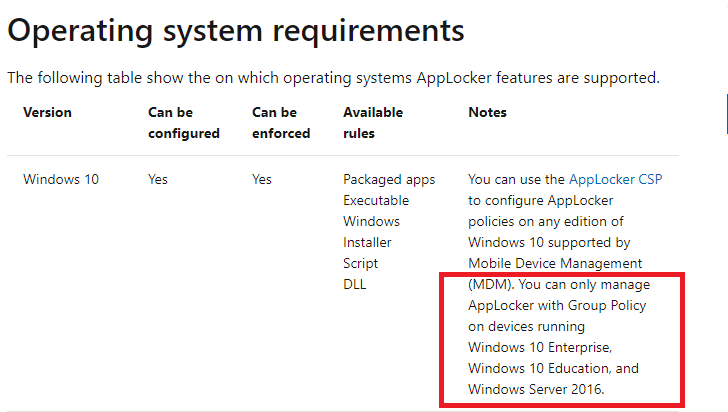
This is because AppLocker is designed to work on Windows Enterprise and Education editions. The documentation clearly states that AppLocker policies won’t function on the Pro edition, leaving administrators without a clear path to implement app restrictions.
But I wasn’t ready to give up. My goal was to find a workaround that could push AppLocker policies to Windows Pro devices, even if it meant using some less conventional methods.
Rewind: Using the WMI Bridge
Some time ago, I wrote a blog on how to automatically wipe and reset your on-premises domain-joined devices to prepare them for Autopilot enrollment. In that PowerShell script, I leveraged the WMI bridge to reset the device. It sparked an idea—could I use the same technique to push AppLocker policies to Windows 10 Pro?
I began my exploration by opening WBEMTest, a handy tool for interacting with the WMI repository. With it, I connected to the following namespace: root\cimv2\mdm\dmmap
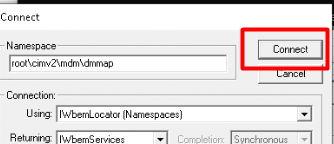
This namespace provides access to the Device Management (DM) WMI bridge, allowing administrators to interact with the Mobile Device Management (MDM) policy settings directly on a Windows device.
Finding the Right Class for AppLocker
Once connected to the namespace, it was time to find the correct class for AppLocker. I used the “Enumerate Classes” button and, after some searching, found exactly what I was looking for: MDM_AppLocker_ApplicationLaunchRestrictions01_EXE03
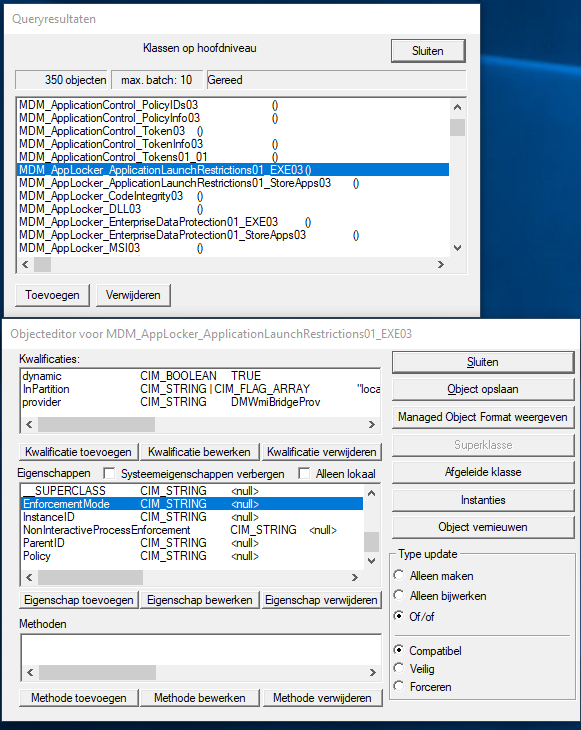
This class is responsible for configuring AppLocker’s application launch restrictions for executable files. Next, I opened this class to identify the key properties I’d need to successfully create and deploy an AppLocker policy.
Key Properties for Configuring AppLocker on Windows Pro
The class required me to specify the following parameters:
- Namespace:
root\cimv2\mdm\dmmap - ParentID:
./Vendor/MSFT/AppLocker/ApplicationLaunchRestrictions - Class:
MDM_AppLocker_ApplicationLaunchRestrictions01_EXE03 - Group: Just like in MDM policies, you need to specify a unique
GroupNamefor the AppLocker policy. This will group all rules under the same umbrella.
Building the PowerShell Script
With all the necessary information in hand, I put together a PowerShell script to create a new instance of the MDM_AppLocker_ApplicationLaunchRestrictions01_EXE03 class and inject a policy directly into the device’s MDM bridge.
$namespace = "root\cimv2\mdm\dmmap"
$group = "applockerexe"
$class = "MDM_AppLocker_ApplicationLaunchRestrictions01_EXE03"
$parent = "./Vendor/MSFT/AppLocker/ApplicationLaunchRestrictions/$Group"
Add-Type -AssemblyName System.Web
$policy = [System.Net.WebUtility]::HtmlEncode(@"
COPY PASTE YOUR EXE INTUNE APPLOCKER POLICY
"@)
New-CimInstance -Namespace $namespace -ClassName $class -Property @{ParentID=$parent;InstanceID="EXE";Policy=$policy} Testing the Policy on Windows 10 Pro
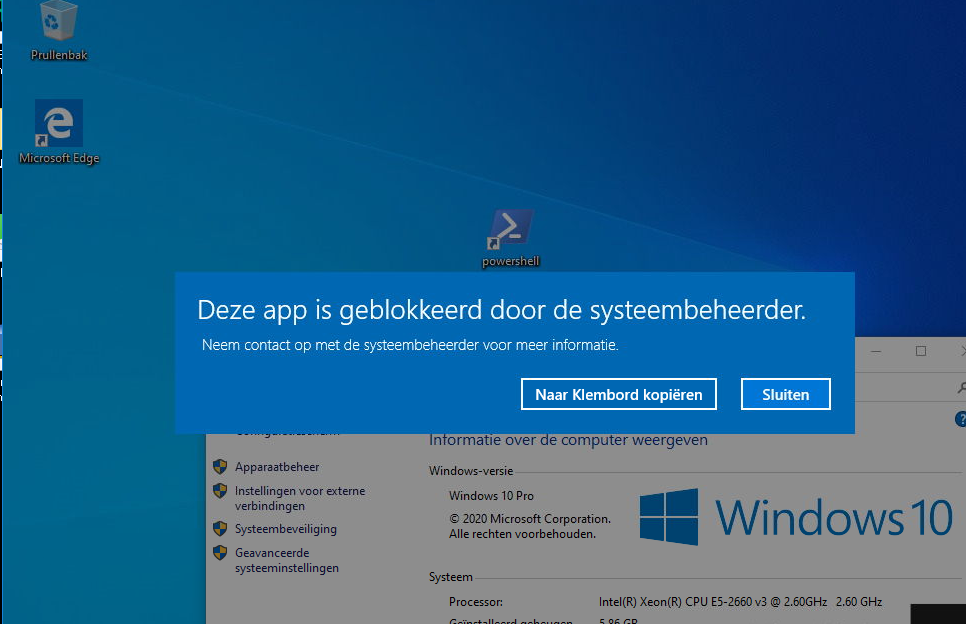
To ensure the script was functioning correctly, I created a new standard (non-admin) user account on a Windows 10 Pro device. I then attempted to launch PowerShell and a few other executable files that weren’t permitted by the policy. The result? AppLocker successfully blocked the disallowed applications!
I verified the policy’s enforcement by checking the AppLocker logs under Application and Services Logs -> Microsoft -> Windows -> AppLocker. Sure enough, the policy was being enforced, even on Windows Pro.
Final Thoughts and Considerations
It’s fascinating to see how a seemingly unsupported feature like AppLocker can be made to work on Windows 10 Pro by leveraging the WMI bridge. While this approach bypasses some licensing restrictions, it’s essential to recognize that these policies may not be as robust or centrally manageable as those configured through Intune or Group Policy on an Enterprise edition.
That said, this method could be a viable solution if you have a fleet of Windows Pro devices and you want to enforce basic AppLocker rules without upgrading or using Intune. By incorporating this PowerShell script into your device management routine, you can ensure that all Windows 10 Pro devices inside your domain receive the same level of application control.
Conclusion
In the end, my journey with AppLocker on Windows 10 Pro revealed a hidden potential that Microsoft doesn’t readily advertise. While official documentation may say otherwise, with some creative scripting and an understanding of the WMI bridge, you can enforce AppLocker policies on Windows 10 Pro—no Intune required! So if you’re managing a mixed environment and want more control over your app launch restrictions, give this method a try and see if it suits your needs.

