When deleting the Intune object, I noticed that Bitlocker had somehow been suspended. With Bitlocker suspended, the Protection was off. If the Bitlocker protection was turned off, the data would be accessible! Want to hear more? read the details below!
1. Bitlocker policies and deleting the object
While trying to devise a different solution for when you don’t want to perform a remote wipe, I was curious about what would happen when we deleted the Intune Object.
Please note: In this test setup, I have configured a BitLocker policy in Intune to ensure the devices are protected with BitLocker. As shown below, all settings have succeeded!
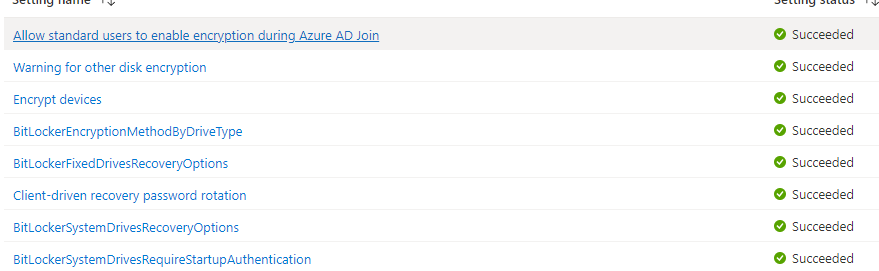
Before showing you what is going to happen, let’s first check the BitLocker protection to make sure it is configured and protection is enabled!
The easiest way to get the Bitlocker status would be to open a CMD and enter this command: Manage-bde -status
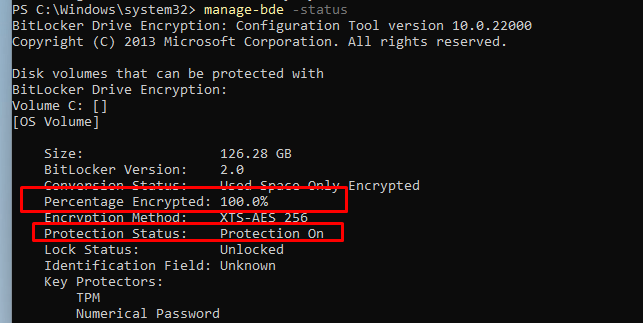
Instead of Remote wiping the device, we are going to remove the Intune object because when the device is still configured with BitLocker, we are safe, right?
2. What Happens when deleting the device from Intune?
Let’s start by deleting the Intune object, as shown below. Just select the proper device and click on “delete”
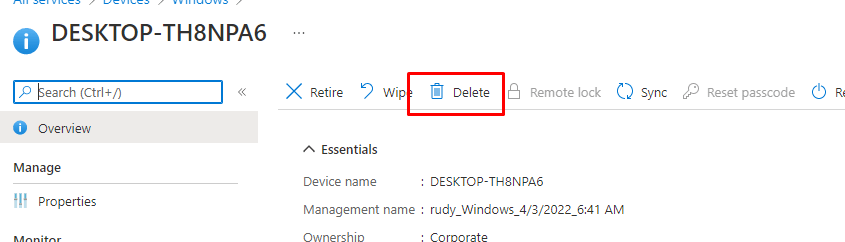
After I pressed delete, I just got myself a cup of coffee and waited to see what happened. After drinking a cup of coffee and some social talks with some colleagues I took another look at the BitLocker protection status.
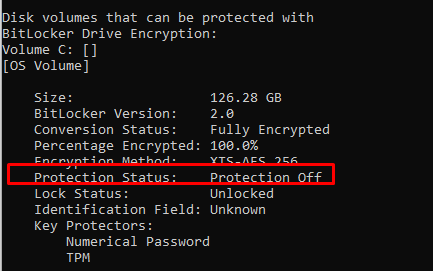
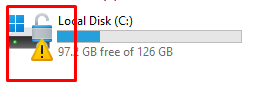
When running Manage-bde -status again, it is telling us the Protection status is Off. Yes, you read it correctly OFF not ON. Looking at the conversion status, it is luckily still fully encrypted.
Please Note: The Bitlocker-Api event log will also mention the event ID 773. Bitlocker was suspended for volume c:
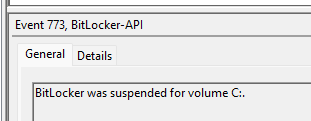
I was also curious about what happened when I pressed “delete”. Before I did, I took some screenshots of the BitLocker FVE settings in the Policies and PolicyManager\default registry keys. This screenshot below is BEFORE deleting the Intune object.
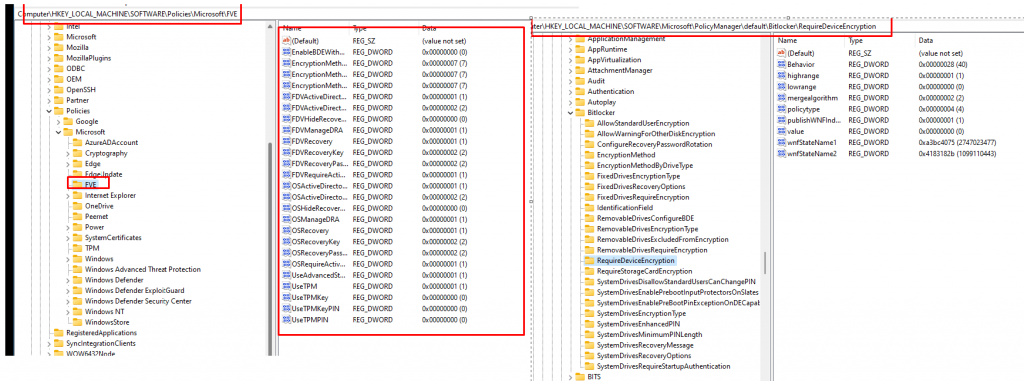
Let’s take a look at how it looks after pressing the delete button in Intune. When removing the Intune object, it’s obvious that configured Intune policies will be removed from the device. This means that the BitLocker policies will also be removed!
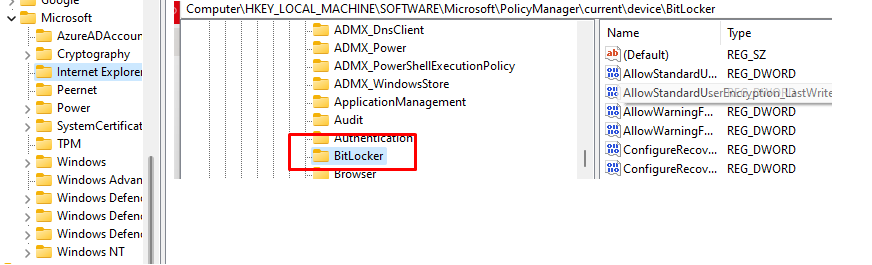
But besides removing these policies and the corresponding registry keys, BitLocker also gets suspended! I was only expecting this when the device was removed from AAD but not from Intune.
When deleting the Intune object we will notice that Just before BitLocker is suspended the process deviceenroller.exe will callup on the fveapi.Dll (Windows BitLocker Drive Encryption API)
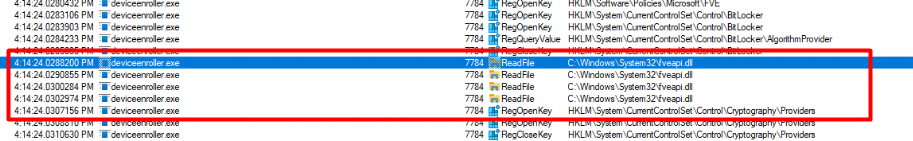
When BitLocker is suspended it allows “users to access encrypted data on a volume that uses BitLocker Drive Encryption”
So I decided to leave the device alone for a while and started to look into some other weird issues. But after waiting for a while nothing else happened so I decided to start performing some tests to check if the data is indeed accessible.
3. Could we access the data?
I decided to start with attaching the disk to another device. Dismounting the disk and mounting it on another device prompted me for the BitLocker recovery keys. So that’s all fine!
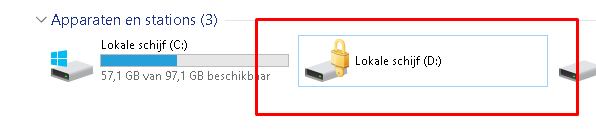
After this test, I decided to reboot the device but this time I made sure I selected “Troubleshoot” when booting from my USB Windows 11 Installation media
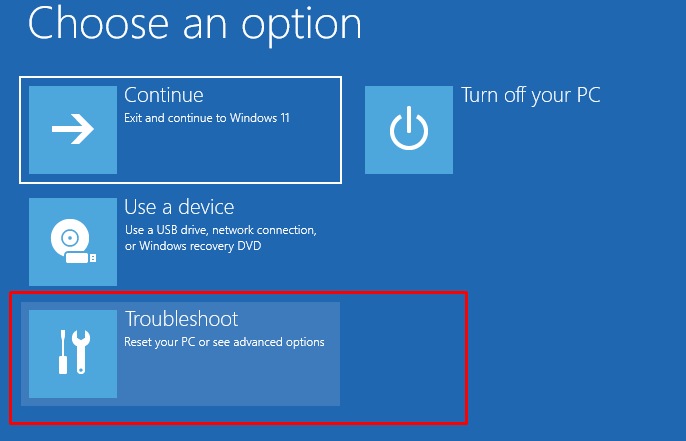
After selecting the CMD option, I was curious if I could access the data but before I could access them I needed to assign it a drive letter. As shown below, while testing the drive was still fully encrypted but the Protection is Off
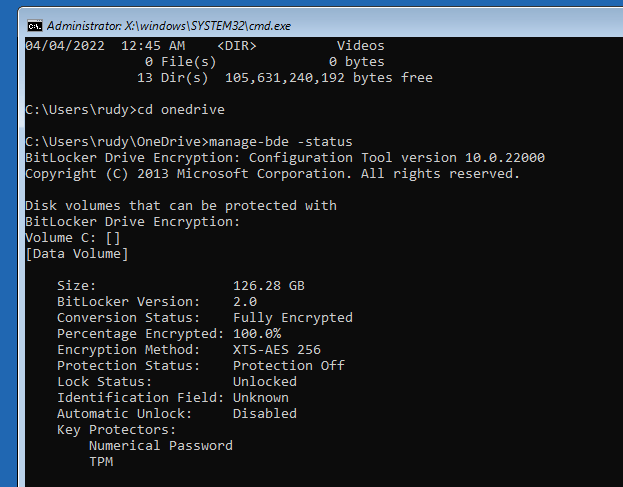
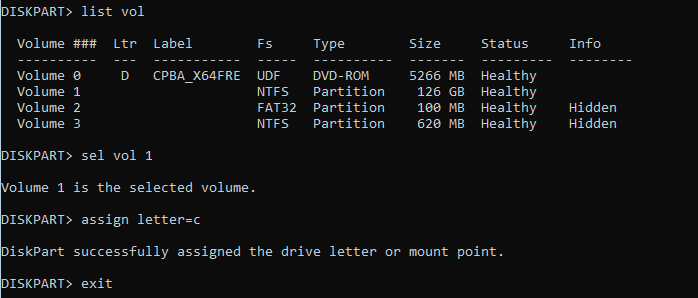
If the disk was protected with BitLocker, accessing it should be impossible, and you would be asked to unlock the drive from the Control Panel first.
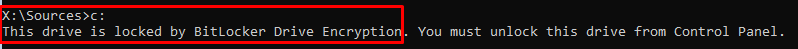
But this time, protection is off! Let’s continue. After assigning a drive letter, I was curious if we could access the disk. Let’s take a look at what we can do with it!
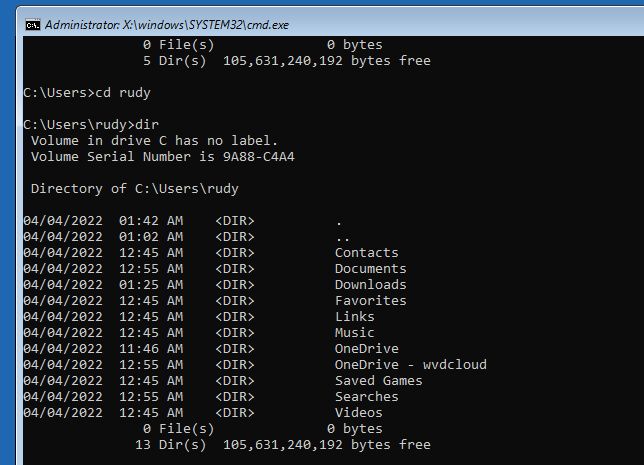
As shown above, because the Bitlocker protection is off we are not prompted to unlock the drive. We could easily access the disk and open some files!
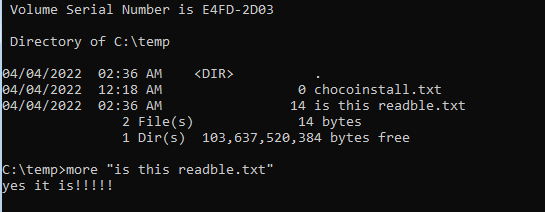
Should I tell you something funny? Just use Xcopy to copy all of that sensitive data to your USB stick!
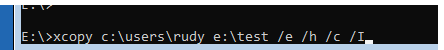
After plugging the USB stick into another device, you will notice that the data is also readable!
4. Microsoft Docs
As always, we need to read the MS-Docs if we want to know what happens!
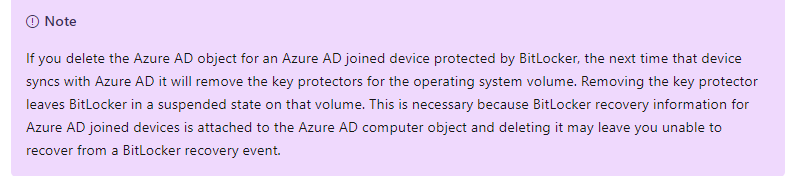
The MS-docs is mentioning the fact that when removing the AAD object, the key protectors are removed when the device is synced. When removing the key protectors it will leave BitLocker in a suspended state
But I am not removing the AAD Object! I am ONLY removing the Intune object. I guess MS needs to add a couple of lines to this MS-Docs.
When BitLocker is suspended it could be possible to recover data when using the Windows Recovery Environment, so please make sure when you remove the Intune Object there is no sensitive data left on the device.
5. A Possible Solution
I guess we could just use a PowerShell script to enable and configure BitLocker instead of a device configuration profile as I showed you in one of my earlier blogs.
https://call4cloud.nl/2021/02/b-for-bitlocker
When not using the PowerShell option to deploy BitLocker we could also adjust this PowerShell script to make sure it will only try to resume Bitlocker each 1 minute if it got suspended
##########################
# create bitlocker.ps###
############################
$content = @'
$BLinfo = Get-Bitlockervolume
if($BLinfo.VolumeStatus -eq 'FullyEncrypted' -and $BLinfo.ProtectionStatus -eq 'Off'){
Resume-BitLocker -MountPoint "C:"
}
'@
##########################
# output content to file #
##########################
$path = $(Join-Path $env:ProgramData CustomScripts)
if (!(Test-Path $path))
{
New-Item -Path $path -ItemType Directory -Force -Confirm:$false
}
Out-File -FilePath $(Join-Path $env:ProgramData CustomScripts\resumebitlocker.ps1) -Encoding unicode -Force -InputObject $content -Confirm:$false
###########################################################
# register script as scheduled task to run at each logon #
###########################################################
$triggers = @()
$triggers += New-ScheduledTaskTrigger -AtLogOn
$triggers +=New-ScheduledTaskTrigger -Once -At (Get-Date) -RepetitionInterval (New-TimeSpan -Minutes 5)
$User = "SYSTEM"
$Action = New-ScheduledTaskAction -Execute "powershell.exe" -Argument "-ex bypass -file `"C:\ProgramData\CustomScripts\resumebitlocker.ps1`""
Register-ScheduledTask -TaskName "ResumeBitlocker" -Trigger $Triggers -User $User -Action $Action -Force
################################
###Start bitlocker encryption###
################################
Start-ScheduledTask -TaskName "ResumeBitlocker"
Conclusion
When you have configured a BitLocker device configuration profile, and you have deleted the Intune object, the BitLocker protection will be suspended! When it’s suspended, you can easily access the data from WINRE! Of course, when it’s a personal BYOD, I get it, but it’s not a personal device! It’s a company-owned device!
I guess when you have configured BitLocker with an Endpoint security profile, it’s not safe to delete the object when sensitive data is still on the device! You will need to make sure the data is removed yourself!
I could say, initializing a remote wipe is safer…. but then again…please describe the word “safe”


