Granting your users local admin permissions when deploying Windows 10 is really really best practice…I’m joking, no it’s not! I must be saying this a lot lately. You need to […]
The never-ending Command Prompt
This blog will be about some new ADMX-backed policies for MDM to block access to the Command Prompt (DisableCMD). After trying them out, I encountered some weird behavior. 1. Introduction […]
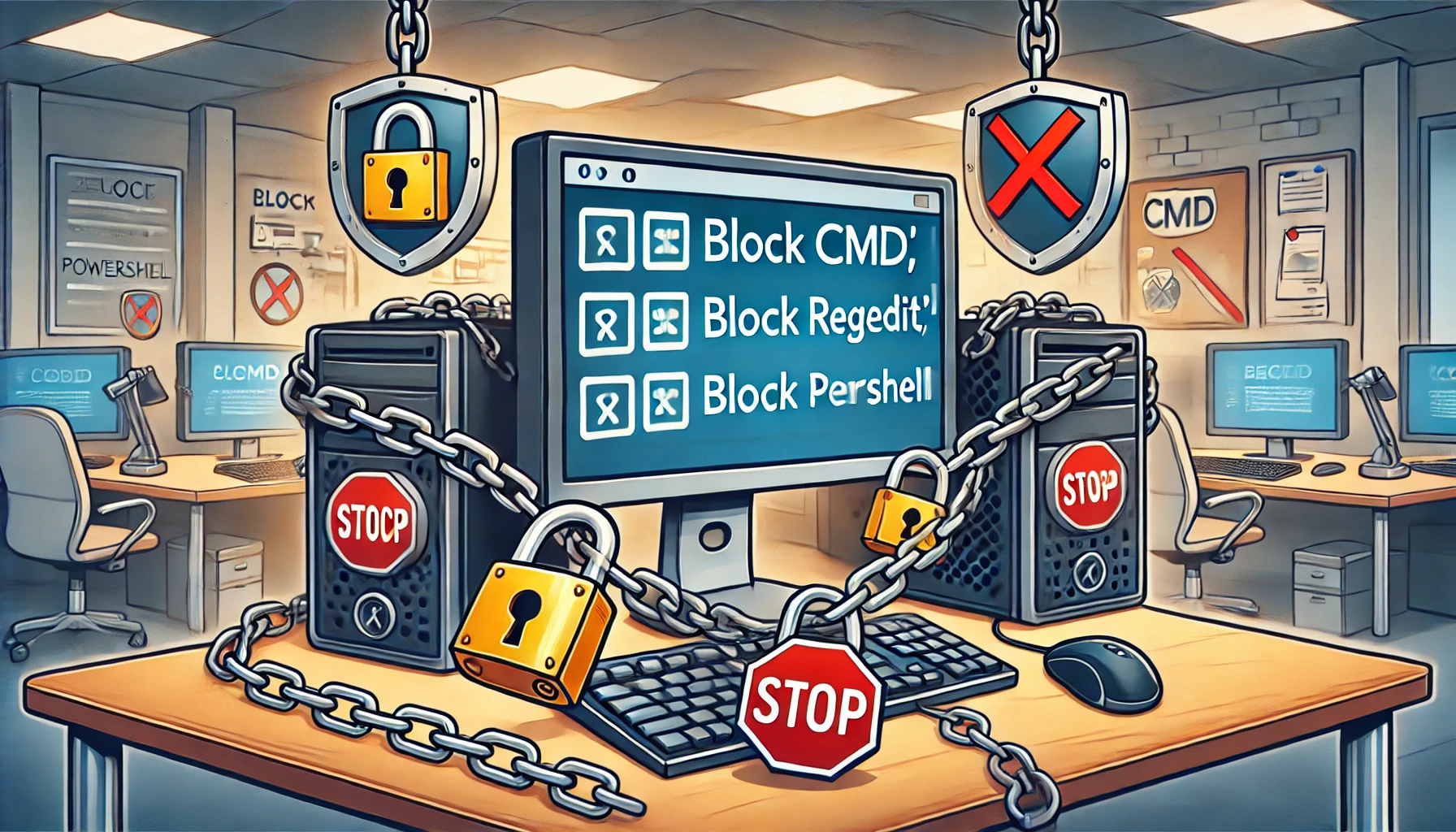
Things to block in Denver When You’re an IT Admin
In this updated guide, we’ll explore effective strategies for blocking access to administrative tools such as Regedit (Block Regedit), the Command Prompt (Block CMD), and PowerShell (Block PowerShell). We’ll break […]
Interview with the ASR rules
Protecting your devices with Microsoft Defender ASR rules is best practice, but ensure you know the caveats. The sun was probably shining when you configured your ASR rules! After deciding […]
The Fellowship Of Group Labelling
Labelling your data with sensitivity labels is the way to go. Confidential data within your organization needs to be labelled with a proper sensitivity label. You can do this manually […]
No Country For Not Monitoring
SIEM (security information and event management) is a set of tools used to monitor, identify, analyze and record security events. Of course, you could use Azure log analytics and Azure […]
Microsoft and Solarwinds, the holy grail
Solarwinds announced a collaboration with Microsoft to enhance monitoring and management. And since we use Solarwinds as our RMM solution, I think that’s really nice. In this blog, I will […]
Lock, Stock and Office 365 ATP Automation
Securing your email with Office 365 Advanced Threat Protection (ATP) / Microsoft Defender for Office 365 is like putting a cage around your email. You might ask yourself: Why do we […]
The Forgotten Fruits of Securing your Windows Endpoints
Securing your endpoints is essential to protect your systems from various security threats. This blog will walk you through the steps you need to take to ensure your endpoints are […]
My first blogpost :)
I have been thinking a lot about creating a website and to start blogging. The time is now. This a video (in dutch…) how I configured one of my test […]