This blog will be about a new User action in conditional Access and how to deploy this setting. I will also show you how to deploy this rule among all other rules in conditional access with the use of PowerShell.
When you join/register a device you will need to require MFA in my opinion. It’s also a part of our Baseline tenant enrollment. I guess you don’t want someone outside your company joining a device with stolen credentials? Otherwise requiring a compliant device to access your data will not be an issue anymore for the attack when they have a nice compliant device.
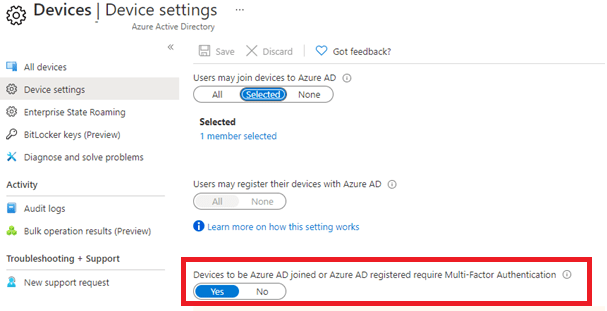
Maybe there are some issues when you configure this setting above, but this setting needs to be enabled in my opinion.
Therefore I was very happy to see, requiring MFA to register or join a device (preview) is finally available to configure with Conditional Access rules
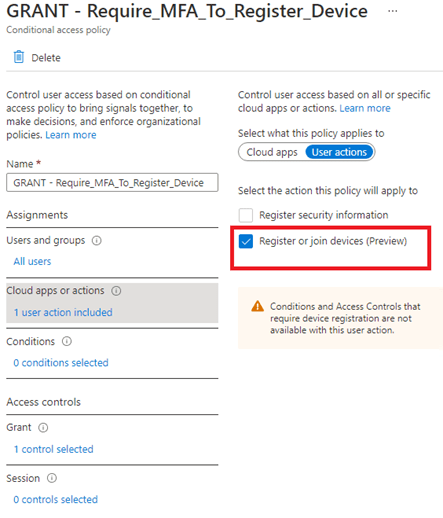
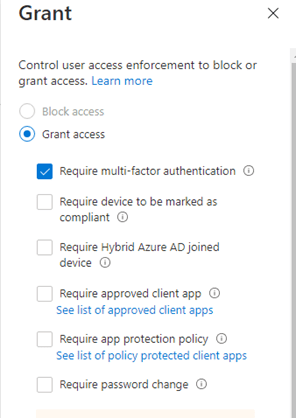
You might ask why I am happy to see this addon?
-Instead of requiring MFA for all users when joining a device, you could exclude some users.
-Finally, this MFA setting is also in the same panel as all other MFA settings. I love granularity!
Please don’t forget to change the setting in the Azure portal back to disabled after you have deployed the conditional access rule!.
When this user action was released I immediately added it to the conditional access baseline policy. You need to make sure your baseline conditional access policies are 99,99% the same in each tenant you manage.
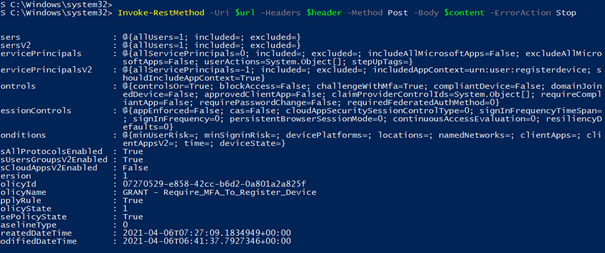
Download your baseline here (the rules are off by default):
https://call4cloud.nl/wp-content/uploads/2021/04/DeployAll.zip
Conclusion:
You will need to require MFA before any user can join their device, finally, conditional access is the way to go to configure this.