Hi, Refresh tokens, Hi lag when Terminating users or setting a new password.
Welcome continuous access evaluation (CAE), bye lag (1-hour refresh token)
Continuous Access Evaluation is implemented by enabling services, like Exchange Online, SharePoint Online, and Teams, to subscribe to critical events in Azure AD, like:
*Enabling MFA
*Disabling or deleting a User
*Changing a user his/her password
This process enables the scenario where users lose access to organizational SharePoint Online files, email, calendar, or tasks, and Teams from Microsoft 365 client apps within mins after one of these critical events
Claim challenge is a mechanism to indicate the token was rejected and a new token needs to be issued. So what are the benefits:
- User termination or password change/reset: User session revocation will be enforced in near real time.
- Network location change: Conditional Access location policies will be enforced in near real time.
- Token export to a machine outside of a trusted network can be prevented with Conditional Access location policies.
The latest version of the following applications below support claim challenge:
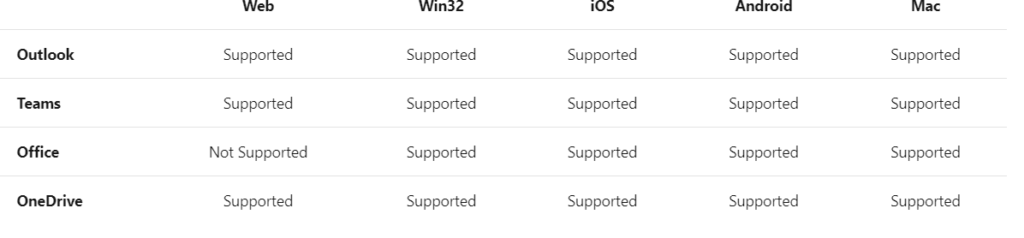
*Source: https://docs.microsoft.com/en-us/azure/active-directory/conditional-access/concept-continuous-access-evaluation
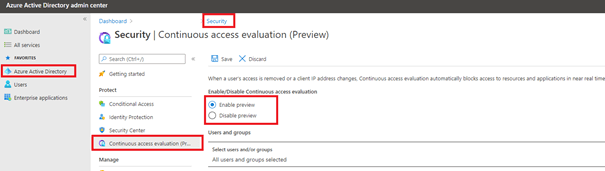
Let’s activate this new feature: (EDIT: On by default now!)
https://aad.portal.azure.com/#blade/Microsoft_AAD_IAM/SecurityMenuBlade/ContinuousAccessEvaluation
After “terminating” my test user.. all sessions were revoked instantly. Sometimes it can take about 15 minutes before everything is blocked. And beware when directly enabling the terminated user, it can also take some time before the user can access office365 again.
Of course, there are some caveats like coauthoring with multiple users on the same document. The user loses access after closing the document, closing the office apps, or after 10 hours. This can be changed by configuring a network location policy.
And like shown earlier, you need CAE capable clients like Word/Excel/Outlook/Teams for Windows/IOS/Android. But I guess when you have your modern workplace enrolled, you are working with CAE capable clients.
#####################################################################
#Enable Continuous access evaluation
#####################################################################
login-azurermaccount
$context = Get-AzureRmContext
$tenantId = $context.Tenant.Id
$refreshToken = @($context.TokenCache.ReadItems() | where {$_.tenantId -eq $tenantId -and $_.ExpiresOn -gt (Get-Date)})[0].RefreshToken
$body = "grant_type=refresh_token&refresh_token=$($refreshToken)&resource=74658136-14ec-4630-ad9b-26e160ff0fc6"
$apiToken = Invoke-RestMethod "https://login.windows.net/$tenantId/oauth2/token" -Method POST -Body $body -ContentType 'application/x-www-form-urlencoded'
$header = @{
'Authorization' = 'Bearer ' + $apiToken.access_token
'Content-Type' = 'application/json'
'X-Requested-With'= 'XMLHttpRequest'
'x-ms-client-request-id'= [guid]::NewGuid()
'x-ms-correlation-id' = [guid]::NewGuid()
}
$url = "https://main.iam.ad.ext.azure.com/api/SmartSession/Config"
$content = '{"state":1,"groupsToInclude":[],"usersToInclude":[],"isStrictLocationEnforcementEnabled":false}'
Invoke-RestMethod –Uri $url –Headers $header –Method Put -Body $content -ErrorAction Stop
Conclusion:
CAE is really great. I can’t say anything more about it… I guess it’s hasta la vista lag


