This blog will be all about the Endpoint Security series blogs I have written until now and why. If you haven’t read my blogs about it please do!
1.Why?
Some time ago, I needed to configure Application Guard for a customer, but I noticed there wasn’t any useful information available… only the official Microsoft documentation. Okay, that information is pretty good, but I was missing some good insights, tips, and tricks.
So I started reading a lot of information about Application guard/Wdac/Mdac or whatever you want to call it.
After using google/bing a lot, I also realized the other features in Endpoint Security were also lacking information. So let’s talk some more about configuring Endpoint Security in Intune.
You can use the Endpoint Security node in Intune to configure device security profiles and manage security tasks for devices that are at risk.
1. You can review the status of all your managed devices when opening the “all devices” blade
2. You can deploy security baselines to make sure the best practice security configurations for devices are applied. In my opinion, it’s a great idea… but I rather know what I am doing/configuring.
3. You can manage security configuration on devices by configuring specific policies. This blog will show you the options you have when you want to configure some settings manually
4. You can set up a compliance policy to make sure your devices and users must meet specific rules to be compliant.
5. You can integrate Intune with Microsoft defender for Endpoints. Like always, make sure you have the proper license applied.
2.What’s Inside the Endpoint Security Suite
So let’s talk some more about configuring the security policies on our own instead of deploying a simple baseline!. When we open the endpoint security section in Intune we will notice it has been divided into multiple sections
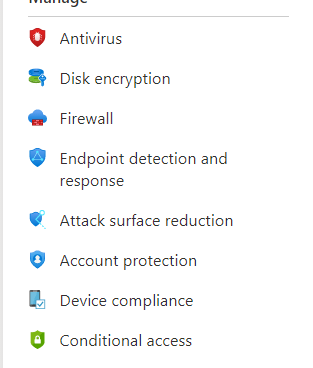
Configuring these policies is one of the many options available for configuring security settings on your devices. I prefer to have all security-related settings in one node, but if you have been reading my blogs, you will know that sometimes it’s not (yet?) possible to configure all of these settings in this Endpoint security node.
I will need to warn you because when configuring the same policy in multiple places in Intune could end up in conflicts!

Now we know we need to be careful when configuring settings manually in different places, let’s take a look at the options we have in the endpoint security itself.
2.1.Antivirus
Still need to create a blog about this topic I guess but I already created a blog about a small part of it named Controlled Folder Access
2.2.Disk Encryption
Encryption, Encryption, Encryption, and nothing more.
https://call4cloud.nl/2021/02/b-for-bitlocker
2.3.Firewall
If you need to manage your endpoint’s built-in firewall, you can configure this policy
https://call4cloud.nl/2020/07/the-windows-firewall-rises
2.4.Endpoint Detection and Response.
When you have the proper licenses, you need to make use of the Microsoft Defender for Endpoint (MDE) suite. With this configuration policy, you can integrate MDE with Intune and onboard devices with MDE
2.5.ASR
Check Part 3 about this topic, because it has some more information I need to show you
2.6.Account Protection
It’s all in the name because when configuring this policy you can configure Windows Hello and Credential Guard.
3.ASR
When we are looking at the Endpoint Security in Intune we probably notice that the most security features we could configure are located in the Attack Surface reduction section. I guess we all have Microsoft Defender enabled on our devices, so we can make use of Attack Surface Reduction.
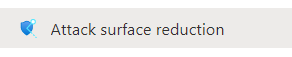
Not to be confused with the ASR Rules…
Attack Surfaces (ASR) are all the places where your organization is vulnerable to cyberthreats and attacks. Defender for Endpoint will reduce the attack surface with the use of different kinds of techniques
Attack Surface Reduction Rules are rules that are part of Windows Defender Exploit Guard that block certain activities and processes.
So first we need to take a look at what’s inside the ASR section! I will also post the link to each blog I have written about that particular topic
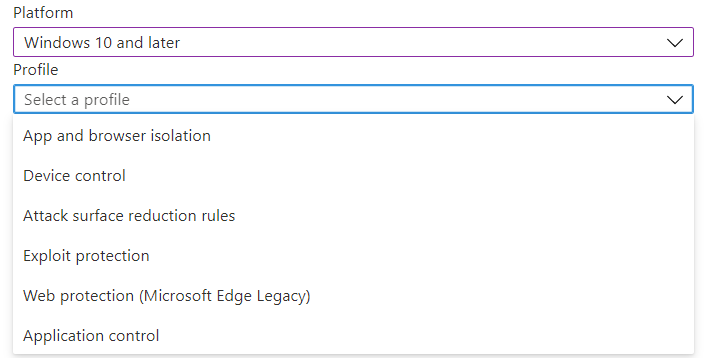
3.1.App and Browser Isolation
3.2.Device Control
https://call4cloud.nl/2021/07/o-removable-storage-where-art-thou
3.3.ASR Rules
3.4.Network/Web Protection
3.5. Windows Defender Application Control
https://call4cloud.nl/2021/06/wdac-or-the-unexpected-virtue-of-ignorance
4.What is missing in the Endpoint Security?
If you have read this blog and all the other blogs attached to it, you will probably have noticed what’s missing in my opinion!.
- WDAC: One very good example is configuring WDAC with endpoint security. You can enable it and nothing more!
Some time ago I noticed someone who experienced the same issue.
MSI Elevated privilege request – Microsoft Tech Community

2. Applocker: Unfortunately, WDAC is one of the many examples which is missing. Another good example would be Applocker. Where is Wally… ehhh Applocker?

Even while deploying a simple baseline with Applocker to block Administrative tools is already available in Intune (for education)?
https://call4cloud.nl/2020/06/blocking-administrative-apps-like-the-command-prompt-in-intune
So why is Microsoft not making sure, this important policy is also available in the Endpoint Security blade? Because I rather configure a good Applocker policy than just enabling WDAC!
3. Device Filters: And where are the Filters (preview-function)? When configuring device configuration policies, you have got filters!
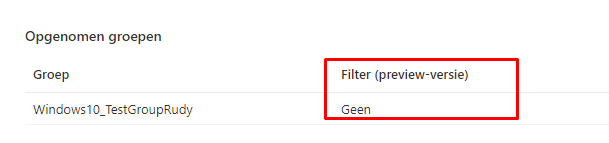
But looking at the Endpoint Security we need to use? As it is sometimes necessary to create a filter, I am totally missing this option in the Endpoint Security Section

Conclusion
Endpoint Security is great and I love to see everything in one node. It’s a shame, not every setting I want to configure is not (yet) available. But then again maybe I am just more demanding than I need to be and I just need to be happy with what options I have.