This blog will show you a possible method for ensuring that your existing Azure Ad / Entra Joined devices that are not yet MDM / Intune enrolled are automatically enrolled in Intune.
1. Introduction
Many customers start their cloud journey using Azure Ad as their Identity Provider. Most of the time, Intune wasn’t yet part of that journey. But what if you want to ensure your devices are being already managed and enrolled in Azure/Entra but not in Intune?
Today, I enrolled existing Azure Ad joined /Entra devices into Intune. Azure Ad joined these devices but without MDM/Intune enabled or configured.
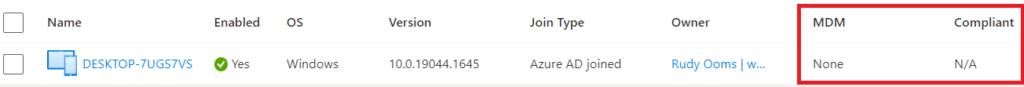
This company started with only Microsoft 365 Business standard licenses. With this particular license, we will not be able to enroll the devices into Intune.
So without the possibility to enroll devices into Intune, all of the devices were only Azure Ad Joined/ Entra joined. How will we ensure we can enroll those Entra joined-only devices into Intune?
When you want to enroll your existing Azure Ad joined device into Intune, multiple options are available to ensure the device is enrolled into MDM/Intune.
Microsoft is telling us that the official supported method uses a provisioning package.
I guess there should be an easier way to do so. Before I show you the easy way, let’s first examine the requirements.
2. The Requirements
The first one is not necessarily a requirement but could make your life much easier. When we have a third-party remote management (RMM) tool installed on those devices, we will probably have the possibility to deploy some PowerShell script to those devices in system context. (at least our RMM tool has that option)
The system permissions are necessary because enrolling an existing Azure Ad Joined device into Intune has one major requirement: You must have the right privileges (local administrator) to perform that operation! Otherwise, you will end up with some nice errors.
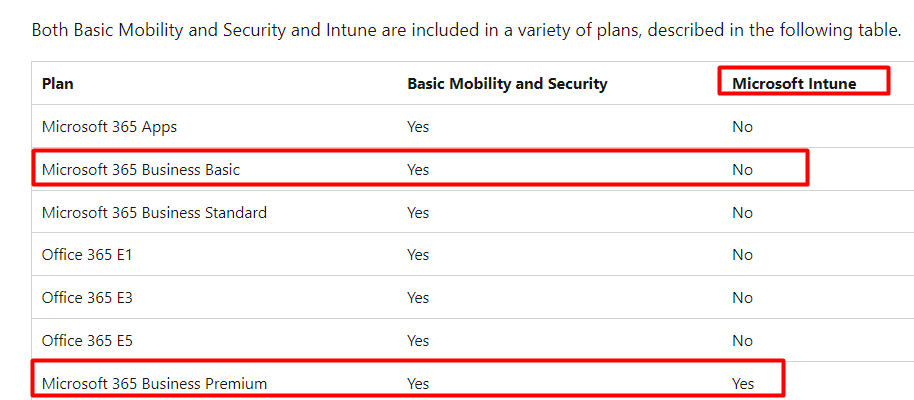
If the permissions aren’t going to be an issue, we still need to check out some other settings. We must configure the MDM scope in Intune to ensure users can enroll their devices. As shown below, we ensured only users with a proper license (Business Premium) could enroll their devices in MDM.
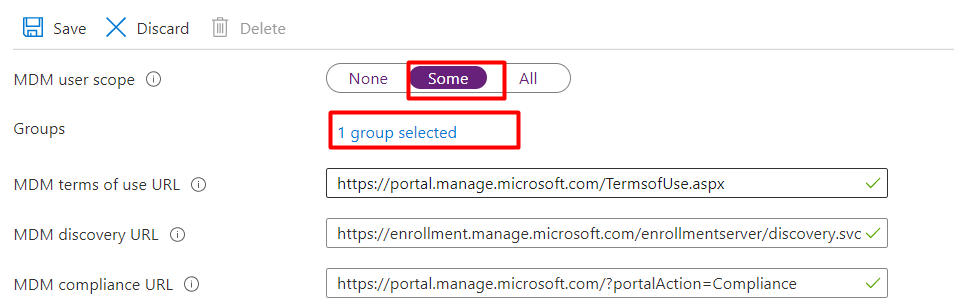
Please note: Before enrolling the device, also make sure there are no enrollment restrictions(Block Personal Devices) configured!

3. Triggering the Enrollment
We need to develop a faster solution when you don’t want to go through all the steps to create a provisioning package and end up as a grumpy old man.

If you aren’t deploying this script below with system context (RMM tool requirement), we need to download and use PSExec. (Sysinternal tools)
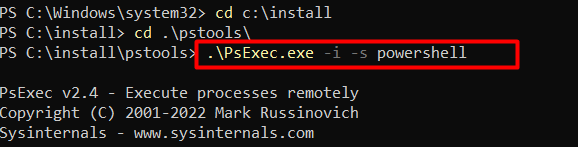
With Psexec -s we can start the enrollment that triggers the DeviceEnroller command with these arguments /c /AutoEnrollMDM in the System context (PSEXEC).
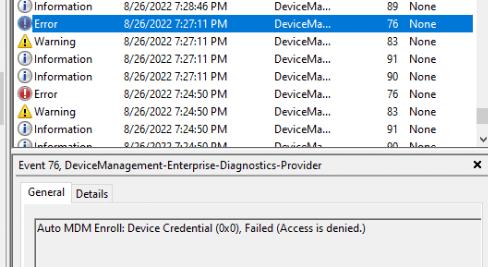
If you don’t execute this command in the system context, you will notice a nice error mentioning: “Auto MDM ENroll: Device Credential (0x0), Failed (Access is denied). So please….use PSEXEC to kick off the enrollment if you are doing this on your own and not using an RMM tool.
Let’s continue with the script! As shown below, I also ensured that the MdmEnrollmentUrls are configured before we start the enrollment!
I got 2 PowerShell scripts.. one just doing its job and one that creates a scheduled task to do exactly the same thing.
The simple one
# Set MDM Enrollment URL's
$key = 'SYSTEM\CurrentControlSet\Control\CloudDomainJoin\TenantInfo\*'
$keyinfo = Get-Item "HKLM:\$key"
$url = $keyinfo.name
$url = $url.Split("\")[-1]
$path = "HKLM:\SYSTEM\CurrentControlSet\Control\CloudDomainJoin\TenantInfo\\$url"
New-ItemProperty -LiteralPath $path -Name 'MdmEnrollmentUrl' -Value 'https://enrollment.manage.microsoft.com/enrollmentserver/discovery.svc' -PropertyType String -Force -ea SilentlyContinue;
New-ItemProperty -LiteralPath $path -Name 'MdmTermsOfUseUrl' -Value 'https://portal.manage.microsoft.com/TermsofUse.aspx' -PropertyType String -Force -ea SilentlyContinue;
New-ItemProperty -LiteralPath $path -Name 'MdmComplianceUrl' -Value 'https://portal.manage.microsoft.com/?portalAction=Compliance' -PropertyType String -Force -ea SilentlyContinue;
# Trigger AutoEnroll
C:\Windows\system32\deviceenroller.exe /c /AutoEnrollMDM
The Scheduled Task One
Another option you can use if you don’t want to leverage PSExec because of some ASR rules/AV Blocking it. Besides, it could be blocked and create a lot of noise if you have a SIEM. If we want to enroll our existing device into Intune without using Psexec, we could also just create a scheduled task that will literally do the exact same thing.
As shown below, this script will create a scheduled task under system context and will trigger the deviceenroller.exe with the /c /AutoEnrollMDM parameters.
$triggers = @()
$triggers += New-ScheduledTaskTrigger -At (get-date) -Once -RepetitionInterval (New-TimeSpan -Minutes 1)
$User = "SYSTEM"
$Action = New-ScheduledTaskAction -Execute "%windir%\system32\deviceenroller.exe" -Argument "/c /AutoEnrollMDM"
$Null = Register-ScheduledTask -TaskName "TriggerEnrollment" -Trigger $triggers -User $User -Action $Action -Force
Start-ScheduledTask -TaskName "TriggerEnrollment"4. Results:
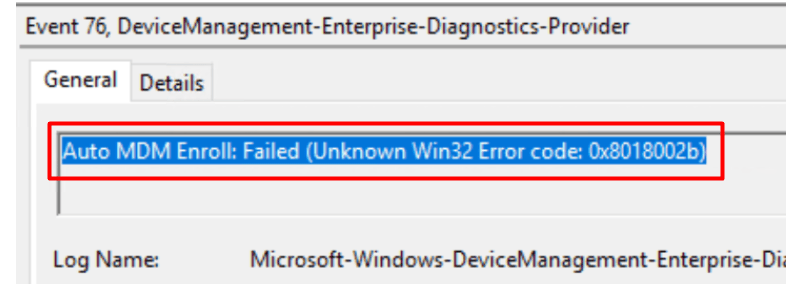
When kicking off the PowerShell script (or the scheduled task), you will need to give it some time because sometimes it could take a bit longer before the device is successfully enrolled into Intune. In the meantime, you could notice the error Auto MDM Enroll: Failed 0x8018002b (event 76) popping up in the DeviceManagement-Enterprise-Diagnostic event log.
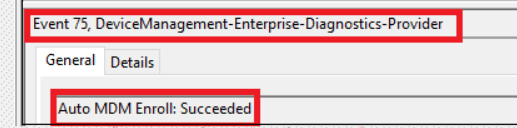
After some time of waiting you will notice event 75 with the message that Auto MDM Enroll: Succeeded
For the people who don’t believe that this process will only take a few seconds, here you go
5. Troubleshooting the Enrollment
I removed this part from this blog because it was becoming too large, and while becoming too large, it was overshadowing the main part of the blog.
Please visit this blog if you are dealing with Intune Enrollment Errors or if you are missing the scheduled task to start the enrollment
https://call4cloud.nl/2022/06/how-to-get-the-intune-enrollment-errors-outta-your-ass/
Conclusion:
When your devices are already enrolled in Azure Ad, you don’t need to reinstall them to ensure they are enrolled into Intune/MDM. Sometimes, enrolling a device into Intune sounds easier than it is. Hopefully, the troubleshooting part showed you how to deal with those kinds of situations!
Please Note: Wiping the device and enrolling it with Autopilot is the path you will need to take… but sometimes that path isn’t always available!




Hi,
thanks for your tutorial!
Do you mean Azure AD joined or registered?
https://media-exp1.licdn.com/dms/image/C5612AQE5lJbTDgF-Xw/article-inline_image-shrink_1000_1488/0?e=1609372800&v=beta&t=FfHYRZ9me0btNv9OnRT_1HJ4bCXb8a5G9ojexf9jLqg
best regards
Manuel
how long does it take for the scheduled task to show up? How long on avg before it enrolls with Azure AD? Been waiting 4hrs and nothing on ether front. Running version 20H2
Normally, when you configure this setting your already azure ad joined device will register itself in Intune. This setting will not join the device to azure.
Thank you! I couldn’t find any mention of this on the setup or troubleshooting pages, unless I’d glazed over it.
As soon as I set this GPO and triggered the scheduled task, the devices checked in to Intune as ‘Co-managed’. Also gave them a reboot to speed up the client, rather than waiting 240 minutes for the retry.
Rudy, you are the man! This post saved me so much time and so many headaches.
Many thanks!
On a computer that is currently Azure AD Joined if you put in place the registry key in this location: HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\CurrentVersion\MDM
The device will never create the scheduled task. As soon as I made the changed via Local Group Policy Editor the scheduled task gets made as soon as I run GPUpdate. Without the local GPEDIT not even the “EnterpriseMgmt” folder within scheduled task gets generated.
Any thoughts on how to get around this so the change can be made with just a regedit? It would be a lifesaver for automating this,
Replying to myself here. I may have found a PowerShell script to do this. The scheduled task has to be made. You can’t just flip the registry keys. I’ve not tested yet but here is a potential solution: https://timmyit.com/2018/12/17/mdm-join-an-already-azure-ad-joined-windows-10-pcs-to-intune-with-a-provisioning-package/
What happens when you use C:\Windows\System32\deviceenroller.exe /c /AutoEnrollMDM from a system shell(psexec)
How would you deploy the powershell script when the devices are not managed or domain joined?
Thats going to be difficult…we used the rmm tool we deployed earlier to do so
Hey Rudy
If users enrol as local admin… Will they keep local admin on the enrolled device?
If so that seems like a big no no :o)
Regards from Denmark
Depends on what”you” configured in Intune 🙂 , as you are enrolling a device into a mdm… so I assume you have your configuration profiles in place to make sure the user isn’t going to be an admin right?
Thanks for the quick response. And All your blogs.
I end up with error “Auto MDM Enroll: Device Credential (0x0), Failed (Unknown Win32 Error code: 0x80180026)”
Any idea ?
Using psexec -i -s powershell.exe
I had an issue with your powershell, for some reason the JoinInfo and TennantInfo in the registry wasn’t there. I think I didn’t wait long enough but I’m sure what actually populates that info.
Is there any way to automatically enroll a not Azure Ad joined device to MDM only with a username/password combination? E.g., to run some scripts with an embedded username/password and MDM server enrollment URL.
Rudy! You’re an awesome bro! I used your powershell script but the scheduled task never scheduled. I still successfully enrolled my AzureAD only clients in Intune within seconds using your Psexec method. Let’s go have a beer sometime on me 🙂
In many PCs don’t have enrollment task.
After Option 3. PowerShell had error: “Reg key alredy exist.”
Then gpupdate /force – Windows failed to apply the MDM Policy settings.
How can fix this?
Found an easier way enroll Azure AD Joined devices in Intune. I ran this as the logged in user who was a local admin rights, but it might not be a requirement.
Go to Accounts > Access work or school > Enroll only in device management. Sign in using your work Microsoft credentials. Follow the bouncing ball. Done!
The device gets registered in Intune as a personal device, which you can change in Properties to Corporate if you want.
On the users device, it now shows connected to two Work accounts, one says “Connected to Contoso’s Azure AD” (this was when it was originally Azure AD Joined), and another that says Connected to Contoso for Mobile Device Management Only.
Hi… Never said that, this option wasnt possible 😛 (admin is required)
https://call4cloud.nl/2022/09/intune-the-legend-of-the-certificate/
But maybe not the best option…. as the certificate (mdm) could be stored in the user store
Hello, I stumbled across this method as well. Only thing is my user profile is not there to log into, test.user@domain.com, the PC logs straight back into the Local admin account. Any ideas to get this test.user back?
Can I just say thank you so much for this tutorial. I have wasted so much time on this and Microsoft’s documentation on this very subject sucks. It sucks like most of their documentation to be honest.
This has managed to get the devices from Azure AD to Intune. Thanks again!!
I combined both scripts and was able to enroll the computers almost instantly. Hope this helps others!
# Create Registry Path for MDM AutoEnrollment
$registryPath = “HKLM:\SOFTWARE\Policies\Microsoft\Windows\CurrentVersion\MDM”
New-Item -Path $registryPath -Force
# Add Registry Keys for AutoEnrollment
$Name1 = “AutoEnrollMDM”
$Name2 = “UseAADCredentialType”
$value = “1”
New-ItemProperty -Path $registryPath -Name $Name1 -Value $value -PropertyType DWORD -Force | Out-Null
New-ItemProperty -Path $registryPath -Name $Name2 -Value $value -PropertyType DWORD -Force | Out-Null
# Force Group Policy Update
gpupdate /force
# Speed up the process by configuring MdmEnrollmentUrl and other URLs, and then forcing device enrollment
$key = ‘SYSTEM\CurrentControlSet\Control\CloudDomainJoin\TenantInfo\*’
$keyinfo = Get-Item “HKLM:\$key”
$url = $keyinfo.name
$url = $url.Split(“\”)[-1]
$path = “HKLM:\SYSTEM\CurrentControlSet\Control\CloudDomainJoin\TenantInfo\$url”
New-ItemProperty -LiteralPath $path -Name ‘MdmEnrollmentUrl’ -Value ‘https://enrollment.manage.microsoft.com/enrollmentserver/discovery.svc’ -PropertyType String -Force -ea SilentlyContinue
New-ItemProperty -LiteralPath $path -Name ‘MdmTermsOfUseUrl’ -Value ‘https://portal.manage.microsoft.com/TermsofUse.aspx’ -PropertyType String -Force -ea SilentlyContinue
New-ItemProperty -LiteralPath $path -Name ‘MdmComplianceUrl’ -Value ‘https://portal.manage.microsoft.com/?portalAction=Compliance’ -PropertyType String -Force -ea SilentlyContinue
& C:\Windows\system32\deviceenroller.exe /c /AutoEnrollMDM
Thanks… made me realize I needed to update the script in that blogpost with the one we are always using these days 🙂
Do I have to customize this script for our environement or just run this on the device that needs to join Intune?
Nope.. you could just run it on the devices that need to be enrolled into intune
That combined script is the jam – works like a charm.. Thank you.
Hey there,
Is there a way to do it with a non local admin logged in and no RMM?
After running this and enrollment is done in Intune what does happen with for example a Bitlocker policy? Does it actively apply this policy?
When the device is enrolled, it will start syncing with intune and with it fetching the policies.. so the bitlocker policy will be downloaded and applied
Not getting any errors, not seeing devices in Intune either. They are either Entra Joined or Registered. I was getting errors previously that the regkey did not exist under TenantInfo.. that went away but still no change.
I assume you run that command in system context. Also its good to know that when there are lingering keys (enrollments), it will not work
Thanks Rudy! You’ve helped me out so many times with your posts, you’re the best!
Quick question. Anyone else that knows the answer feel free to jump in!
I have a bunch of Azure Joined laptops in the field. I have successfully used PSexec in my tests to run PS on remote devices, but these devices are Azure AD Joined, and nothing i do PSexec wise is allowing me to get to them im guessing because they arent hybrid or domain joined. Is there any way of executing this script on them remotely?
Hi..thanks
If you dont have management over them (defender or an rmm tool) than it would become difficult as you will need to have some remote control on them
I tried the code but that threw this error
Auto MDM Enroll: Device Credential (0x0), Failed (Unknown Win32 Error code: 0xcaa10001)
my device was a virtual machine running on the windows 10. And the device is azure AD joined as mentioned
I assume you used psexec to elevate yourself to system context?
I got the same error message.
Did you find the cause for it?
Thanks, this guide was so helpful! We found some of our computers had recently started vanishing from InTune but were still in Entra and AutoPilot.
We used the scheduled task method to get them to reenrol into Intune.
We noticed though that we were not seeing Event 76 in the event viewer so we had an extra step we had to before they would retry enrolling.
In case anyone else is in this situation, the extra step was to remove a reg key from:
Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Enrollments
When you look in there, you’ll see lots of keys (not for just InTune) but the one you are looking for has a lot of information on it compared to the others and contains the enrollment.manage.microsoft.com under DiscoveryServiceFullURL.
Once you have located this key, you can delete it. You should then see Event 75 to show it has succeeded (or Event 76 if something else is stopping it…MFA in our case!)
Hope that helps, and thanks again for the guide!
I get the following after running the script:
# Create Registry Path for MDM AutoEnrollment
$registryPath = “HKLM:\SOFTWARE\Policies\Microsoft\Windows\CurrentVersion\MDM”
New-Item -Path $registryPath -Force
# Add Registry Keys for AutoEnrollment
$Name1 = “AutoEnrollMDM”
$Name2 = “UseAADCredentialType”
$value = “1”
New-ItemProperty -Path $registryPath -Name $Name1 -Value $value -PropertyType DWORD -Force | Out-Null
New-ItemProperty -Path $registryPath -Name $Name2 -Value $value -PropertyType DWORD -Force | Out-Null
# Force Group Policy Update
gpupdate /force
# Speed up the process by configuring MdmEnrollmentUrl and other URLs, and then forcing device enrollment
$key = ‘SYSTEM\CurrentControlSet\Control\CloudDomainJoin\TenantInfo\*’
$keyinfo = Get-Item “HKLM:\$key”
$url = $keyinfo.name
$url = $url.Split(“\”)[-1]
$path = “HKLM:\SYSTEM\CurrentControlSet\Control\CloudDomainJoin\TenantInfo\$url”
New-ItemProperty -LiteralPath $path -Name ‘MdmEnrollmentUrl’ -Value ‘https://enrollment.manage.microsoft.com/enrollmentserver/discovery.svc’ -PropertyType String -Force -ea SilentlyContinue
New-ItemProperty -LiteralPath $path -Name ‘MdmTermsOfUseUrl’ -Value ‘https://portal.manage.microsoft.com/TermsofUse.aspx’ -PropertyType String -Force -ea SilentlyContinue
New-ItemProperty -LiteralPath $path -Name ‘MdmComplianceUrl’ -Value ‘https://portal.manage.microsoft.com/?portalAction=Compliance’ -PropertyType String -Force -ea SilentlyContinue
& C:\Windows\system32\deviceenroller.exe /c /AutoEnrollMDM
This is the error;
SYSTEM\CurrentControlSet\Control\CloudDomainJoin\TenantInfo\* : The module ‘SYSTEM’ could not be loaded. For more information, run ‘Import-Module SYSTEM’.
At line:1 char:8
+ $key = SYSTEM\CurrentControlSet\Control\CloudDomainJoin\TenantInfo\*
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : ObjectNotFound: (SYSTEM\CurrentC…in\TenantInfo\*:String) [], CommandNotFoundException
+ FullyQualifiedErrorId : CouldNotAutoLoadModule
Hi
I’m tasked with troubleshooting a bunch of machines in my organisation that have failed to move over to hybrid intune managed. I’m pretty much a novice at this to be honest.
They appear as Microsoft Entra hybrid joined but no owner assigned and MDM = N/A
Are these scripts designed to work in the case of hybrid joined machines that have failed to appear in Intune?
Thanks
Can I apply this procedure on Entra hybrid joined devices?
The official method would be to use a gpo to kick off the intune enrollment.. did you already go down that road or ?
I may be off the mark but if we have a batch of Intune laptops that are currently “Entra Registered”, could this script possibly help to convert them over to “Entra Joined”? currently we have to dsregcmd /leave , sign out, sign in as a local admin and go to Access Work or School and manually join there to handle it so hoping to find a Powershell method to take care of it
Hello,
I got some computer on RMM so I thought I would just push the above as a Powershell script to a machine as a test
“# Set MDM Enrollment URL’s
$key = ‘SYSTEM\CurrentControlSet\Control\CloudDomainJoin\TenantInfo\*’
$keyinfo = Get-Item “HKLM:\$key”
$url = $keyinfo.name
$url = $url.Split(“\”)[-1]
$path = “HKLM:\SYSTEM\CurrentControlSet\Control\CloudDomainJoin\TenantInfo\$url”
New-ItemProperty -LiteralPath $path -Name ‘MdmEnrollmentUrl’ -Value ‘https://enrollment.manage.microsoft.com/enrollmentserver/discovery.svc’ -PropertyType String -Force -ea SilentlyContinue;
New-ItemProperty -LiteralPath $path -Name ‘MdmTermsOfUseUrl’ -Value ‘https://portal.manage.microsoft.com/TermsofUse.aspx’ -PropertyType String -Force -ea SilentlyContinue;
New-ItemProperty -LiteralPath $path -Name ‘MdmComplianceUrl’ -Value ‘https://portal.manage.microsoft.com/?portalAction=Compliance’ -PropertyType String -Force -ea SilentlyContinue;
# Trigger AutoEnroll
C:\Windows\system32\deviceenroller.exe /c /AutoEnrollMDM”
I pushed it a few days ago but not getting any activity on Intune.
You did mention 2 scripts but only have 1 listed above, just a little confused.
Hi.. it also depends on some othre things as well.. did you examined the DeviceManagement-Enterprise-Diagnostic event log? it should mention something usefull
Thank you for this! Is there a way to do this on bulk devices that were Entra joined already and need to be enrolled to Intune? Considering Entra joined devices will have no presence in on-prem AD to push any GPOs and no presence in Intune yet as well? Any insights would be great.
Depends if you have an additional rmm tool in place
Is the scheduled task meant to repeat every minute indefinitely? I didn’t see any mention of it, it sounded like perhaps a one time process to complete this considering you can run a one time powershell? I used your script exactly and it created a repeat every minute indefinitely task. Thank you for your work your site is great!
‘Simple script’ has a ‘bug’:
$path = “HKLM:\SYSTEM\CurrentControlSet\Control\CloudDomainJoin\TenantInfo$url”
correct way is
$path = “HKLM:\SYSTEM\CurrentControlSet\Control\CloudDomainJoin\TenantInfo\$url”
mmm yeah… i noticed the same… which is weird as when I click edit .. i can see the backslash… i added another one.. and now it shows.. well thats weird 🙂
Whey you are creating registry key in the script but do not creating any registry keys in schedule task?
‘Please note: Before enrolling the device, also make sure there are no enrollment restrictions(Block Personal Devices) configured!’
Sorry for asking but why is this? Is it the way Intune sees this method as ‘personal’?
PS C:\Users\xxxx> test-intunesyncerrors
Directory: C:\
Mode LastWriteTime Length Name
—- ————- —— —-
d—– 4/8/2025 2:07 PM temp
Get-ScheduledTask : No MSFT_ScheduledTask objects found with property ‘TaskName’ equal to ‘PushLaunch’. Verify the
value of the property and retry.
At C:\Program Files\WindowsPowerShell\Modules\intunesyncdebugtool\1.0.0.19\intunesyncdebugtool.psm1:435 char:17
+ $EnrollmentID = Get-ScheduledTask -taskname ‘PushLaunch’ | Where-Obje …
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : ObjectNotFound: (PushLaunch:String) [Get-ScheduledTask], CimJobException
+ FullyQualifiedErrorId : CmdletizationQuery_NotFound_TaskName,Get-ScheduledTask
Hold on a moment… Initializing a sync and checking the MDM logs for sync errors!
Report location folder C:\Users\xxx\AppData\Local\Temp\diag
Not detecting any sync errors in the MDM log
Determining if the device is enrolled and fetching the SSLClientCertReference registry key
Thats weird, your device doesnt seem to be enrolled into Intune, lets find out why!.. hold my beer!
Checking the Certificate Prefix.. to find out if it is configured as SYSTEM or USER
Failed to get the Certificate Details, device doesnt seem enrolled? Who cares?Let’s fix it
Fixing the Intune Enrollment
Are you 100% sure you want to proceed? Because I will break everything…or not!!!!!
[Y] Yes [N] No [?] Help (default is “N”): y
Trying to enroll your device into Intune or something else…
Determing if the required MDM enrollment urls are configured in the registry
MDM Enrollment URLS are configured the way I like it!Nice!!
Please give the OMA DM client some time (about 30 seconds)to sync and get your device enrolled into Intune
Checking the Intune Certificate Again!.
Intune device Certificate still seems to be missing… sorry!
Determing if the dmwappushservice is running because we don’t want to end up with no endpoints left to the endpointmapper
The DMWAPPUSHSERVICE isn’t running, let’s kickstart that damn service to speed up the enrollment!
Determing if the certificate mentioned in the SSLClientCertreference is also configured in the Enrollments part of the registry
Great!!! The Intune Device Certificate with the Thumbprint is configured in the registry Enrollments
Almost finished, checking if the EnterpriseMGT tasks are running to start the sync!
Enrollment task doesn’t exist
Press any key to continue…:
Whats happening here? Is the script outdated?
seems that i have to update the ssl cert reference part.. with the linked/mmpc enrollment another enrollment was added to all devices.. and now finds 2 enrollments 🙂 so it can’t check if its the proper one… i have the fix so i need to update te script.. .. thanks for noticing it
#Get guid of the intune enrollment (ignoring the MMP-C one)
$ProviderRegistryPath = “HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Enrollments”
$ProviderPropertyName = “ProviderID”
$ProviderPropertyValue = “MS DM Server”
$GUID = (Get-ChildItem -Path Registry::$ProviderRegistryPath -Recurse -ErrorAction SilentlyContinue | ForEach-Object { if((Get-ItemProperty -Name $ProviderPropertyName -Path $_.PSPath -ErrorAction SilentlyContinue | Get-ItemPropertyValue -Name $ProviderPropertyName -ErrorAction SilentlyContinue) -match $ProviderPropertyValue) { $_ } }).PSChildName
$SslClientCertReference = $null
$SslClientCertReference = Get-ItemPropertyValue HKLM:\SOFTWARE\Microsoft\Provisioning\OMADM\Accounts\$GUID -name SslClientCertReference -ErrorAction SilentlyContinue
$Thumbprint = Get-ItemPropertyValue HKLM:\SOFTWARE\Microsoft\Enrollments\$GUID -Name DMPCertThumbPrint
$cert = Get-ChildItem Cert:\LocalMachine\My\ | Where-Object {$_.Issuer -Like “*Intune MDM*”}
$SslClientCertSearchCriteria = Get-ItemPropertyValue HKLM:\SOFTWARE\Microsoft\Provisioning\OMADM\Accounts\$GUID\Protected -name SslClientCertSearchCriteria -ErrorAction SilentlyContinue
if($SslClientCertReference -notlike “*$thumbprint*”){
write-host “SslClientCertReference is NOT set correctly!!!!!!!”
#Exit 1
}else {
write-host “SslClientCertReference is set correctly”
#Exit 0
}
Howdy Folks, I’m getting the following error on the enrollment script. The rest of the script is running fine:
You cannot call a method on a null-valued expression.
At C:\ALTA\intune_enroll.ps1:20 char:1
+ $url = $url.Split(“\”)[-1]
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : InvalidOperation: (:) [], RuntimeException
+ FullyQualifiedErrorId : InvokeMethodOnNull
I appreciate any help or guidance!
What is the output of the $url variable?