We talked about this in our MMSMOA session, but I still needed to write something about it…..so here we go! This blog will be “again” about issues with the Intune Certificate but this time I am going to show you how Defender For Endpoints (MDE) could save your ass when the device is no longer able to communicate with the Intune Service
1. Introduction
In one of my older blogs, I showed you how to deal with Expired, Duplicate, Lingering, or even a nonexistent, removed, or deleted Intune MDM Certificate.
Sync issues 0x80190190 and the Intune MDM device Certificate (call4cloud.nl)
In the blog above I provided you with a PowerShell script to fix the sync issue by removing the old lingering stuff and certificates from the device but what if you don’t have direct access to the device?
So how are we going to deliver this PowerShell script? With Intune? Nope! Delivering PowerShell scripts with Intune isn’t an option anymore because the Intune certificate is missing in action. So we need to come up with a new solution
2. Prerequisites
Before I show you the easy way to fix it, we need to examine some prerequisites to make this work. Let’s look at them one by one.
1. Defender Licensing
As shown below, when you don’t have an additional RMM tool in place, you will need to be licensed for Microsoft Defender for Endpoint (MDE)
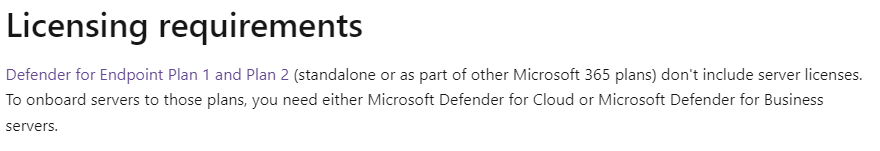
So, if you have a nice Microsoft E5 license, you are good to go!
2. Enrolled Devices
Besides the licensing requirement, your devices also need to be enrolled into Defender for Endpoint but that sounds obvious, right?
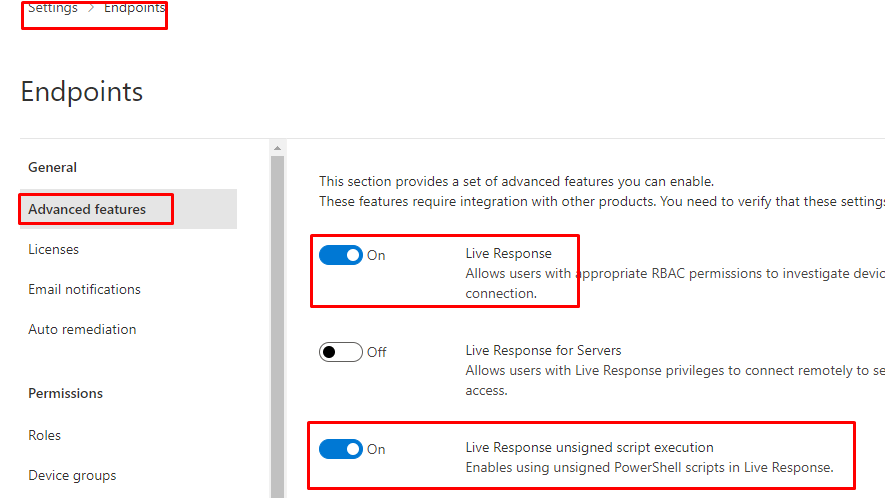
3. Live Response
If we want to deploy a PowerShell script to the device we need to make sure that we don’t forget to enable “Live Response”
3. How To Fix it
With “all” the prereqs met, let’s take a look at how we are going to fix it. To do so you need to open the Defender for Endpoint portal and click on the “Assets/ Devices” button
Press on the device in question that has the missing or broken Intune Certificate

The device tab will open and will show you a lot of options. We are going to press the nice 3 dots right on top and going to select “Initiate Live Response Session”
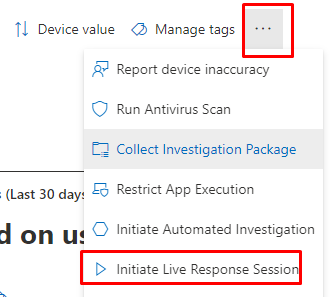
In the next screen, we will notice a nice “Command Console“. Before we can do anything we still need to upload a file (PowerShell script) to the Library

In this screen, you need to select the PowerShell script to fix it.
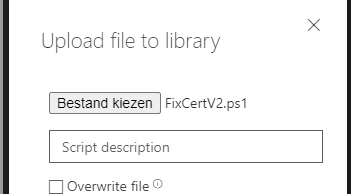
As shown above, I selected the “FixCertV2.ps1” PowerShell script. Here is the content of this file
$RegistryKeys = "HKLM:\SOFTWARE\Microsoft\Enrollments", "HKLM:\SOFTWARE\Microsoft\Enrollments\Status","HKLM:\SOFTWARE\Microsoft\EnterpriseResourceManager\Tracked", "HKLM:\SOFTWARE\Microsoft\PolicyManager\AdmxInstalled", "HKLM:\SOFTWARE\Microsoft\PolicyManager\Providers","HKLM:\SOFTWARE\Microsoft\Provisioning\OMADM\Accounts", "HKLM:\SOFTWARE\Microsoft\Provisioning\OMADM\Logger", "HKLM:\SOFTWARE\Microsoft\Provisioning\OMADM\Sessions"
$EnrollmentID = Get-ScheduledTask -taskname 'PushLaunch' -ErrorAction SilentlyContinue | Where-Object {$_.TaskPath -like "*Microsoft*Windows*EnterpriseMgmt*"} | Select-Object -ExpandProperty TaskPath -Unique | Where-Object {$_ -like "*-*-*"} | Split-Path -Leaf
foreach ($Key in $RegistryKeys) {
if (Test-Path -Path $Key) {
get-ChildItem -Path $Key | Where-Object {$_.Name -match $EnrollmentID} | Remove-Item -Recurse -Force -Confirm:$false -ErrorAction SilentlyContinue
}
}
$IntuneCert = Get-ChildItem -Path Cert:\LocalMachine\My | Where-Object {
$_.Issuer -match "Intune MDM"
} | Remove-Item
if ($EnrollmentID -ne $null) {
foreach ($enrollment in $enrollmentid){
Get-ScheduledTask | Where-Object {$_.Taskpath -match $Enrollment} | Unregister-ScheduledTask -Confirm:$false
$scheduleObject = New-Object -ComObject schedule.service
$scheduleObject.connect()
$rootFolder = $scheduleObject.GetFolder("\Microsoft\Windows\EnterpriseMgmt")
$rootFolder.DeleteFolder($Enrollment,$null)
}
}
$EnrollmentIDMDM = Get-ScheduledTask | Where-Object {$_.TaskPath -like "*Microsoft*Windows*EnterpriseMgmt*"} | Select-Object -ExpandProperty TaskPath -Unique | Where-Object {$_ -like "*-*-*"} | Split-Path -Leaf
foreach ($Key in $RegistryKeys) {
if (Test-Path -Path $Key) {
get-ChildItem -Path $Key | Where-Object {$_.Name -match $EnrollmentIDMDM} | Remove-Item -Recurse -Force -Confirm:$false -ErrorAction SilentlyContinue
}
}
if ($EnrollmentIDMDM -ne $null) {
foreach ($enrollment in $enrollmentidMDM){
Get-ScheduledTask | Where-Object {$_.Taskpath -match $Enrollment} | Unregister-ScheduledTask -Confirm:$false
$scheduleObject = New-Object -ComObject schedule.service
$scheduleObject.connect()
$rootFolder = $scheduleObject.GetFolder("\Microsoft\Windows\EnterpriseMgmt")
$rootFolder.DeleteFolder($Enrollment,$null)
}
$IntuneCert = Get-ChildItem -Path Cert:\LocalMachine\My | Where-Object {
$_.Issuer -match "Microsoft Device Management Device CA"
} | Remove-Item
}
Start-Sleep -Seconds 5
$EnrollmentProcess = Start-Process -FilePath "C:\Windows\System32\DeviceEnroller.exe" -ArgumentList "/C /AutoenrollMDM" -NoNewWindow -Wait -PassThru
Please Note: I also added the Microsoft Device Management Device CA Certificate to it… If you don’t use EPM you can remove it.
With the PowerShell script uploaded, you can now execute it. You can do so by using: “run FixCertV2.ps1”
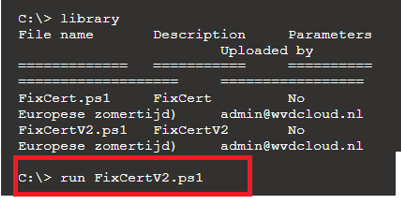
4. The Results
In the video below, I have a device with sync issues and a missing Intune MDM device certificate. In the background, I will kick off the PowerShell script with Defender for Endpoint and Live Response.
Fix missing Intune Certificate with MDE – YouTube
Todo: If you have multiple devices that are giving you the same issue, you can also create an app registration to execute the same script using Live Response on multiple devices
Conclusion
Having sync issues is pretty bad, if it’s not DNS it is probably your Intune Certificate that is giving you the sync issues. With MDE you can remotely fix those sync issues! isn’t that nice?


