After reading this fantastic article on the Technet Community about the Attack Kill Chain, I realized I still needed to get this blog out.
This blog will be about how you could set up some simple honeypot detections by creating some canary accounts to make sure you are protected against some insider threats.
I am going to divide this blog into multiple parts:
1.Introduction
1.Introduction
Making sure you are protected against insider threats is always difficult. How can you be sure you will be notified when someone is trying to look for valuable information? Browsing through folders and opening documents is not a penalty when you have the permissions to do so.
So how could we make sure we can configure some simple notification when someone is digging into your Sharepoint data, hoping to get some valuable information?
After talking to Jan Bakker about a lot of stuff this idea somehow popped up. So here we go!
In my long history as an It admin and a Security consultant, one of the easiest notification systems we configured to detect some strange behaviour were honeypots. I had the pleasure to survive multiple penetration tests in a multi-tenant remote desktop cloud environment. The easiest way to detect “bad people”, is by creating a simple file and configure 24/7 real-time monitoring on it. The first thing every bad guy will try to do is some reconnaissance…(like shown in the TechNet Article)
A honeypot is best explained as a computer security mechanism configured to detect or counteract attempts when unauthorized use is taking place of information systems. Normally, a honeypot consists of data that appears to be legitimate data and contains information or resources of value to attackers. It is actually isolated, monitored, and capable of blocking or analyzing the attackers. So let’s go create a very simple but maybe effective honeypot in Sharepoint
2.Creating the Honeypot Document
You can create your own Canary/Honeypot Excel file but maybe we also could generate an Excel file with some additional tracking information to it. So even when a user downloads the file you will get notified!
Open Microsoft Edge and browse to: https://canarytokens.org/generate#
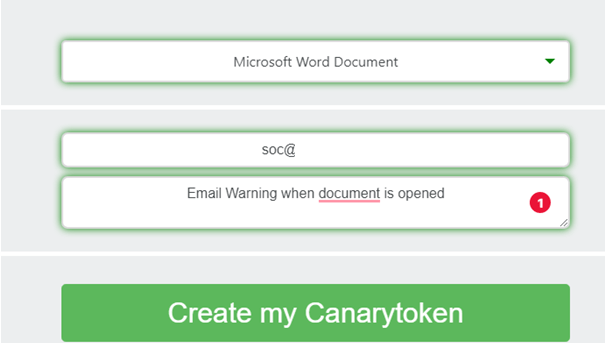
Generate, configure the email address and save the document. After you saved it, open it to add some nice fake or nice new honeypot accounts? As an example:
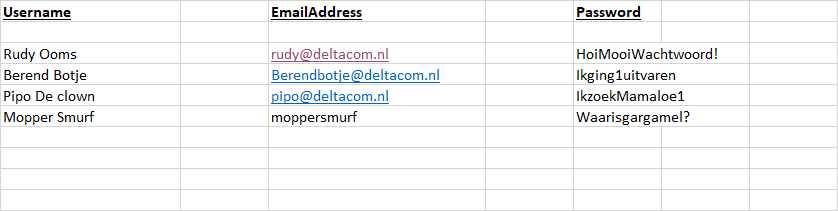
As mentioned above, I definitely would create an additional honeypot account and add it to the document. Wouldn’t it be cool you could have some more logging when someone tries to open the document and afterwards trying to log in with that same information?
I guess some fish will bite if you create a new account named: backupadmin@ with of course no permissions to anything! Please make sure you add the working information, we don’t want the user to get suspicious, do we?
3.Creating the Sharepoint site
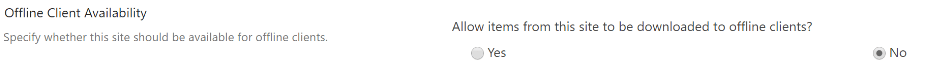
Now we have the honeypot document setup, we need to make sure we place it on a SharePoint site with some restrictions on it. Why you might ask? It’s because when you want to monitor read access to a SharePoint file it’s going to be pretty difficult when it’s synced offline to a OneDrive folder.
So please make sure you place this document on a dedicated SharePoint site with this option set to “no”
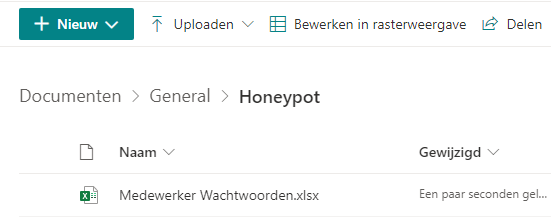
After you have created the SharePoint site and made sure it isn’t possible to sync the SharePoint site with Onedrive, place your honeypot file on it. Make sure you are giving the file a good naming. Don’t give the folder the same honeypot name as I did in the example below… (I hope that speaks for itself!)
Now we have everything in place, it’s time to add some logging to it. You have multiple options to choose from. I will show you how you can do this with some simple Alert Policies and with MCAS
4.Logging with an Alert policy
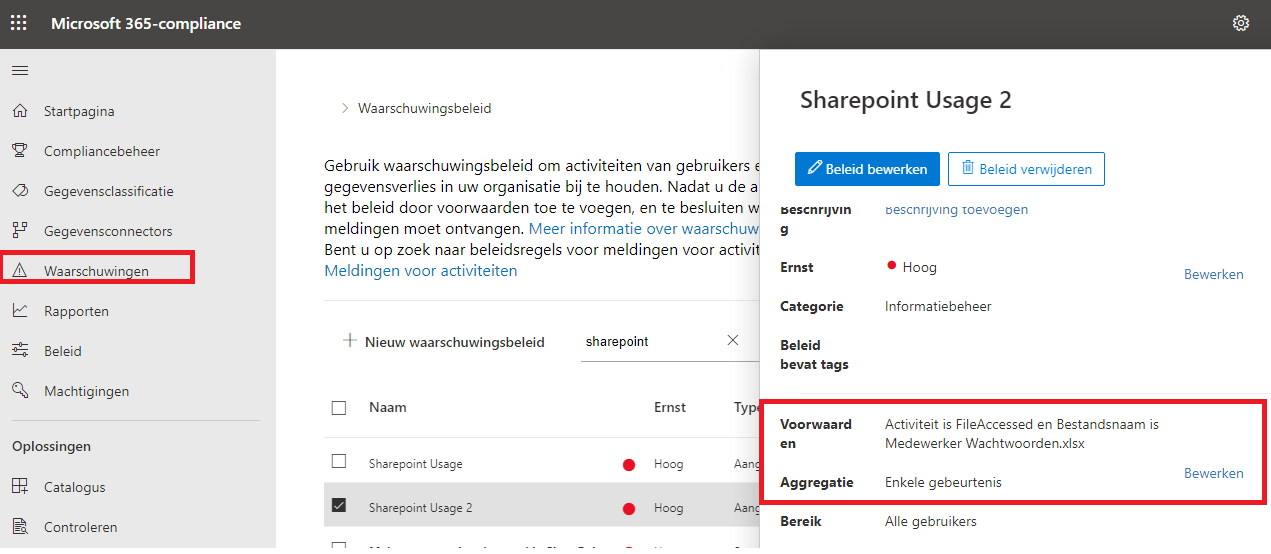
Let’s start with some basic logging when you don’t have MCAS at your disposal. Open the Compliance Centre and start created a new alert policy.
Waarschuwingsbeleid – Microsoft 365-compliance
File Policy
To create a new file policy, you will need to make sure you selected the proper activity and the honeypot file and nothing more.
5. Logging with MCAC Threat Detection Policy
Again, just like we did with the alert policies we need to create a new MCAS policy. One big difference between MCAS and the Alert option, you can do a lot more with MCAS. So this time we are going to create 2 policies. One to monitor the file and one to monitor the honeypot user login. So open your Microsoft Cloud App Security Dashboard and create a new policy.
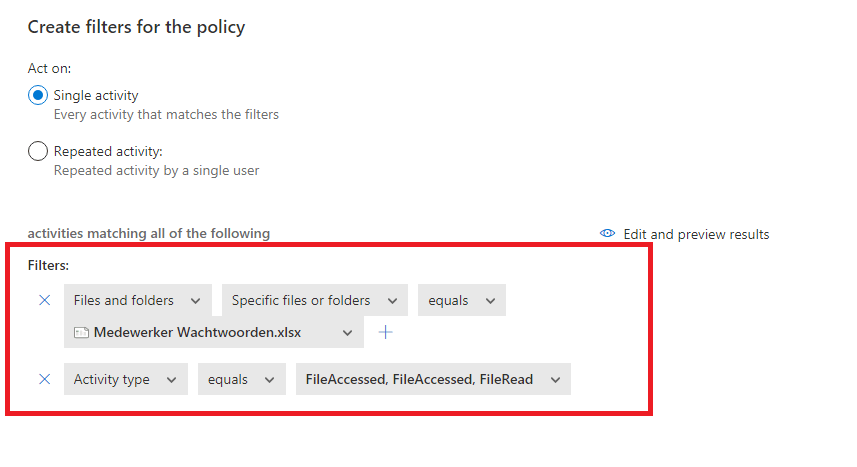
1.File Activity policy
The only two things we need to specify is the file we created earlier and the activity type. I selected: FileAccessed, FileRead, Filedownloaded and make sure you configured the email notifications!
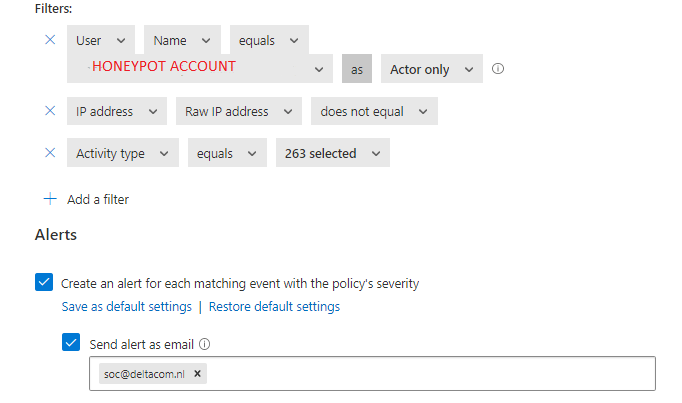
2.Honeypot Account Activity Policy
Just like with the threat detection policy we could create another policy targeting the honeypot username and again the activity Type. This time I made sure I selected everything…. I really want to be notified the moment “someone” is “touching” that specific account. It’s the same policy you would create when monitoring your break glass accounts!
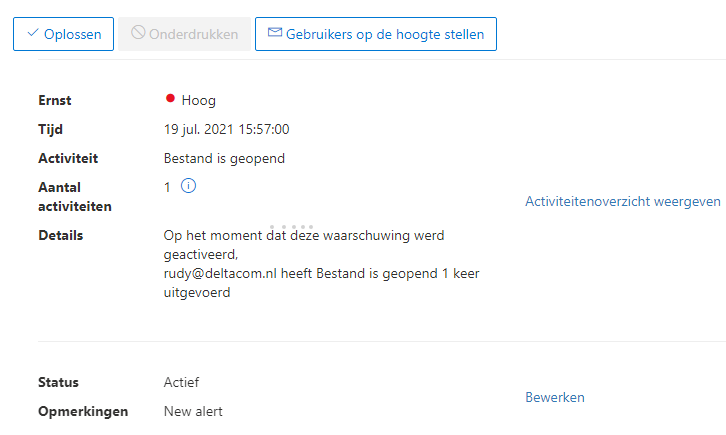
6.Alert Policy, MCAS and CanaryToken Results
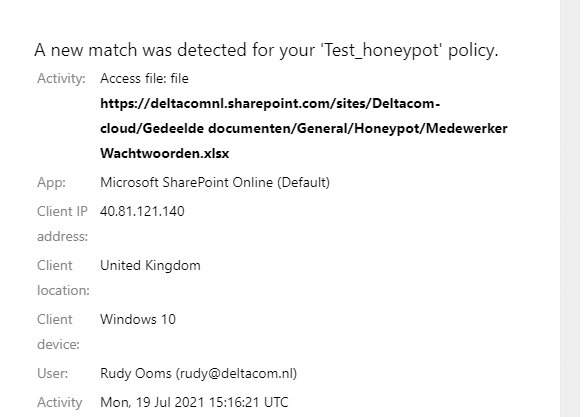
After we have created the policies, please have some patience before testing it. The first time I tested it, it had some time difference between I touched the file and the alert itself. But The next day all my tests ended up with a nice notification in like 5 minutes. I can live with that…
Notification Alert Policy Results
Notification MCAS Policy Alert
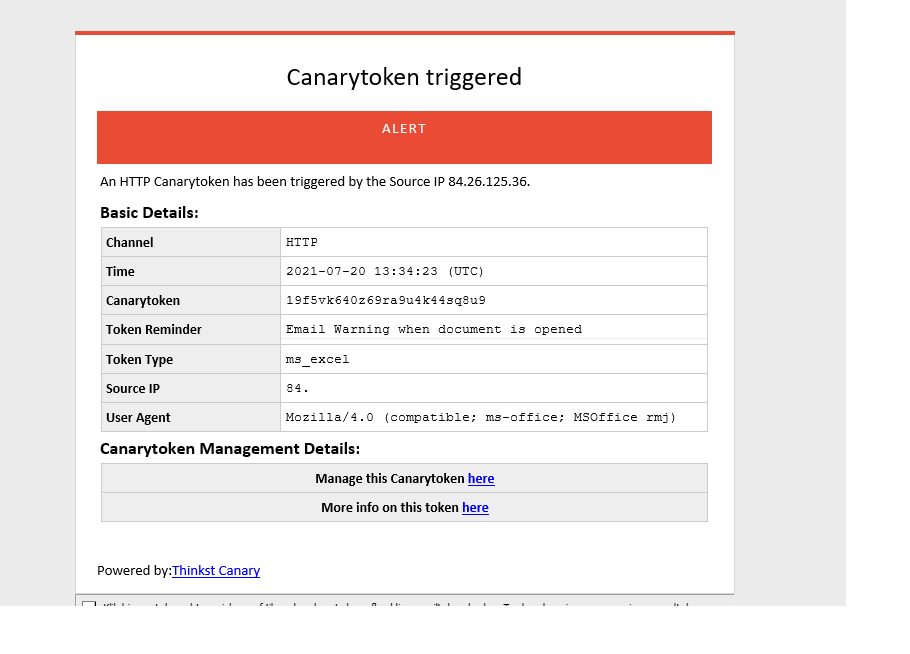
Canary Token
When someone downloads the file, you will be notified by the other alert policies but when it will take you not much time to generate a canarytoken excel document first. Getting spammed is not that bad when it comes to this kind of events.
Conclusion:
Some weeks ago we had an internal Security Audit… one of the things we needed to show were the detection controls we had in place…. but we didn’t need to show him these controls, because he was already trying to find documents with sensitive information in it, to burn us alive! But while he was trying to burn us alive because we were storing sensitive information in plain text excel files we showed him all the logging!

When you have made sure you configured some honeypot files and accounts I guess you can catch someone red-handed?

