In this blog post, I will explore the wonders of Windows LAPS and what happens when you remotely perform a password rotation from Intune—nothing more!
1. Introduction
As almost every MVP has already written a blog about deploying and configuring Windows LAPS, I am skipping that one. I assume we all know by now how to enable LAPS in Azure, right?
If not, and you want to know how to enable and configure the LAPS policy, please visit this blog post.
LAPS around Intune (joostgelijsteen.com)
Let’s continue because I am going to show you what actually happens when you press this button of magic to rotate the local admin password.
Is that really the “only” thing you will show us?

Short answer: YEP!!!..…
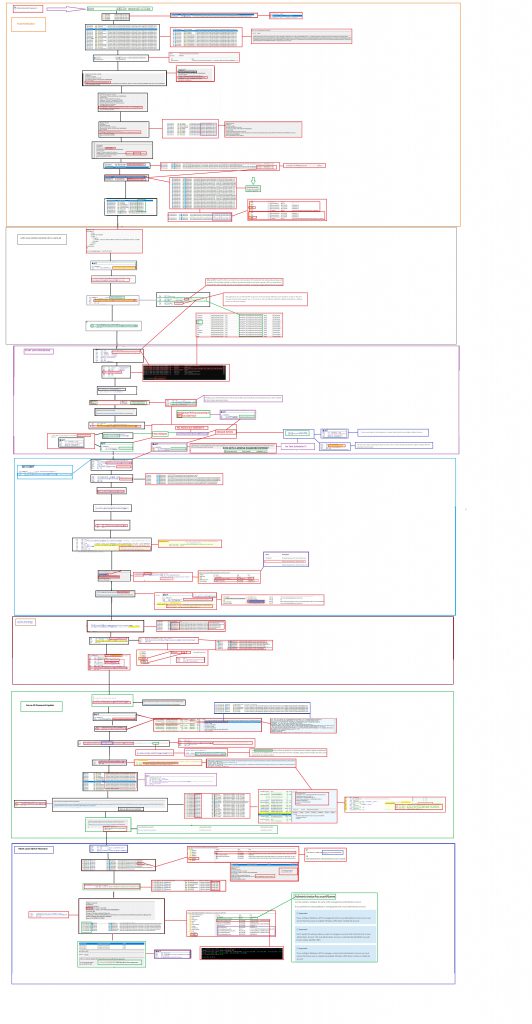
Let’s start with a simple MSPaint Flow. After the flow, I will try to talk you through the flow about what’s happening and what caught my eye
2. The Wonderful AKA Painful MSPaint flow
While writing the blog and creating the flow it became bigger and bigger but this flow will explain what is happening when you press the magic rotate password button.

Please Note: you can click on it, this will give you the possibility to download the linked BMP. Otherwise, it isn’t going to be human-readable! Also to add, I am not a Microsoft Employee
3. The Improved Password Rotation flow
If you don’t want to get all the details, this flow is simpler but easier to follow. I divided it into three parts.
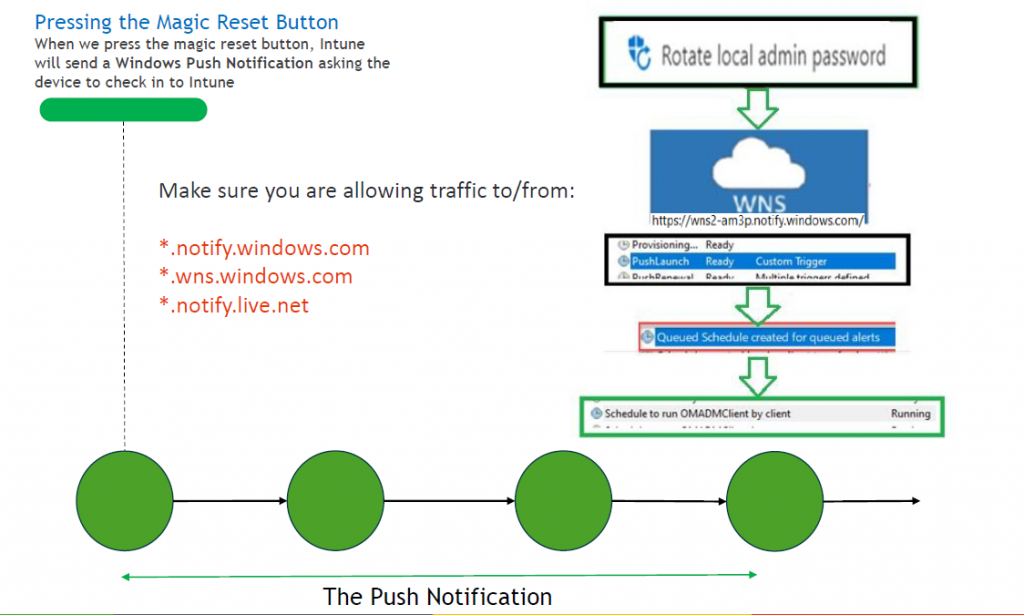
Part 1: The Push Notification
Part 2: LAPS Policy Processing
Part 3: Update/Rotate The LAPS Password
4. Explaining the LAPS flow
My advice? Open the flow on your second monitor and this summary on your first monitor. I will try to give a small summary of what’s happening in the flow
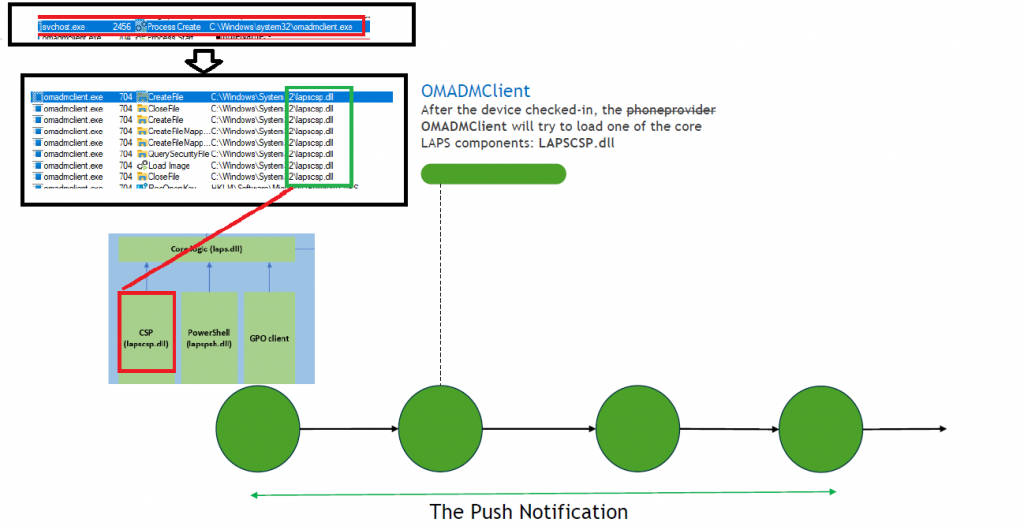
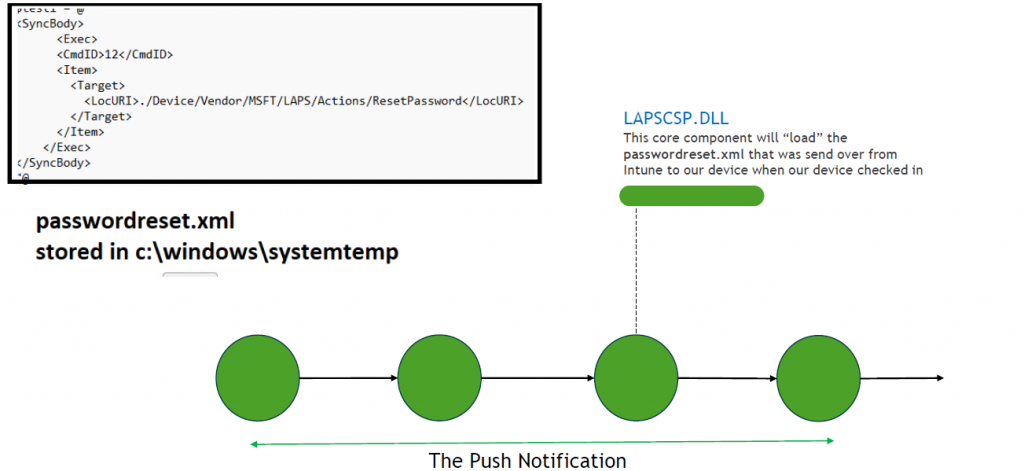
-When clicking the “Rotate Local Admin” button in Intune, the device would send out a push (dmwappushservice) notification to the device. This will execute the OMADMClient.exe process and will start the password rotation by using the ResetPassword XML that was sent over to the device.
-At that moment in time the lapscsp.dll is loaded and the ResetPassword XML is invoked. But how does the Lapscsp.dll communicate with the laps.dll?
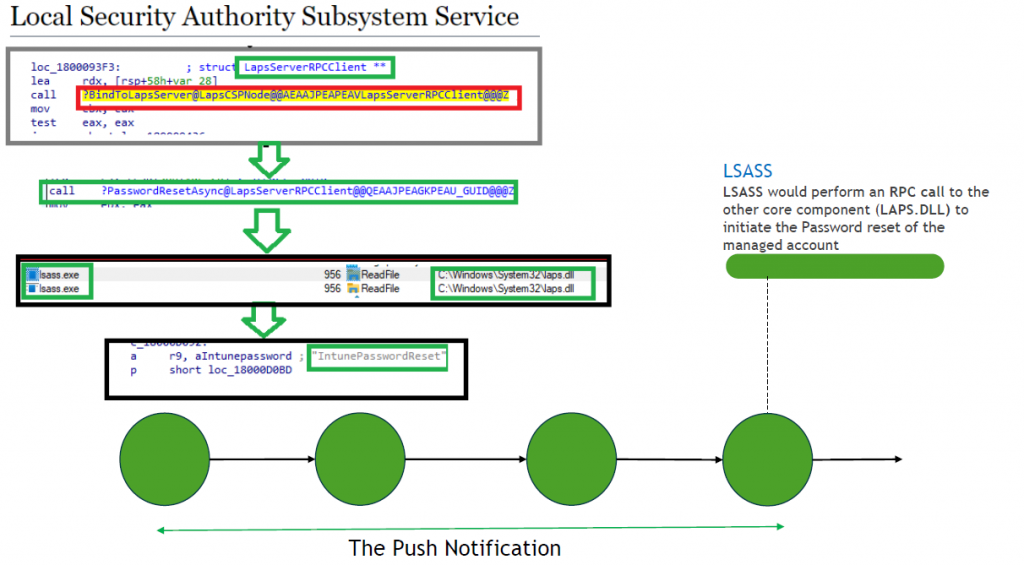
-This is magic part number 1. When looking at the lapscsp.dll it seems like it makes an internal LRPC call to the LAPS LRPC Endpoint (that lives in the LSASS world?) to initiate the password reset.

It does so by using the NCALRPC protocol.
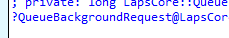
-Let’s move on to magic number 2: When going through all the code (laps.dll,lapscsp.dll and LSASS) another magical world opened up! After spending a lot of time on it, the only real conclusion I can make is that all actions (Password Reset and PostAuthActions/PAA)are ALL QUEUED. Everything let me back to the “QueueBackGroundRequest” function in the LAPS.Dll
-Some of the actions are delayed (1 hourly background policy check for example) and some of them (non-delayed) are executed instantly.
-The delayed actions are using a thing called set threadpooltimer. I guess the name says it all because that one would set the “Timer”. So NO task scheduler for us! So for example, if we tried to execute a process with that LAPS admin account (even when authentication is successful or not.. Microsoft is aware) It will queue a background task to perform a PostAuthResetoperation that will rotate the password. Please note: When your device is turned off (is taking a nap) before the PAA could take place you could run into an issue in which the timer would be signaled immediately when the system wakes.

But at that point in time the Network Adapter isn’t awake yet. Guess what happens? Nothing! As there is no network connection, no password rotation will take place (Microsoft is aware)
-The Non-delayed action will trigger a background Threadpool callback to start the password reset. From there on it will become a little bit easier to follow as LAPS.dll will start the password reset itself
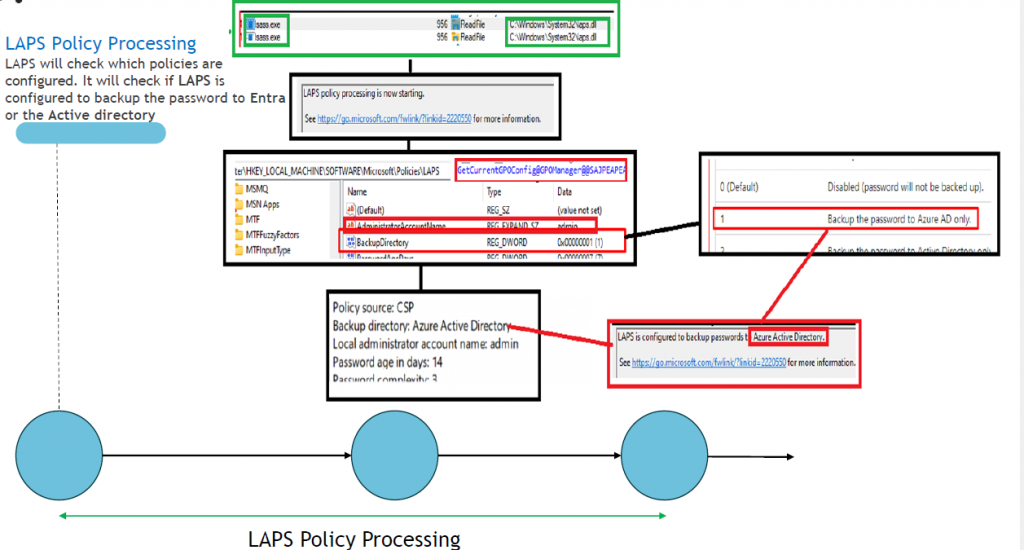
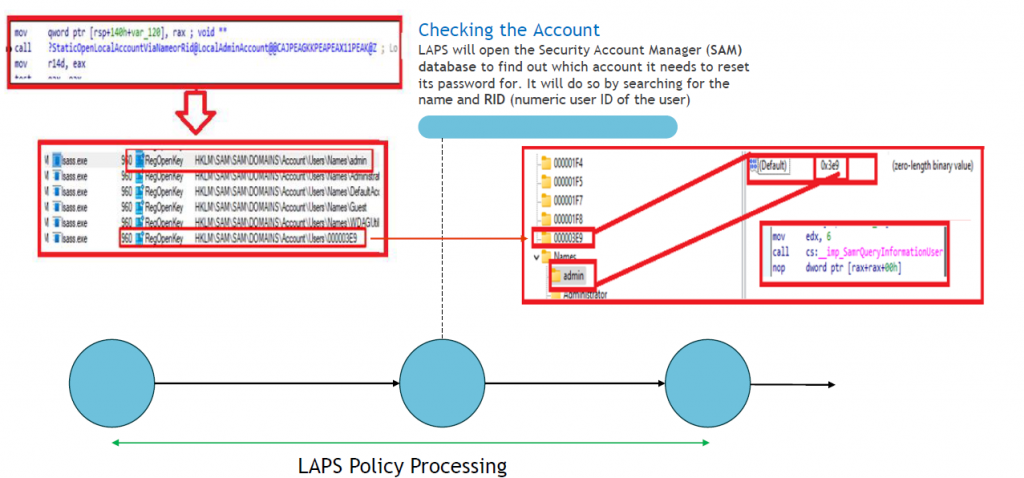
-Before resetting the password, the LapsCoreProcessing function will start checking things like the AADJoinInfo, the current defined settings/policies, and which local admin account needs his password reset.
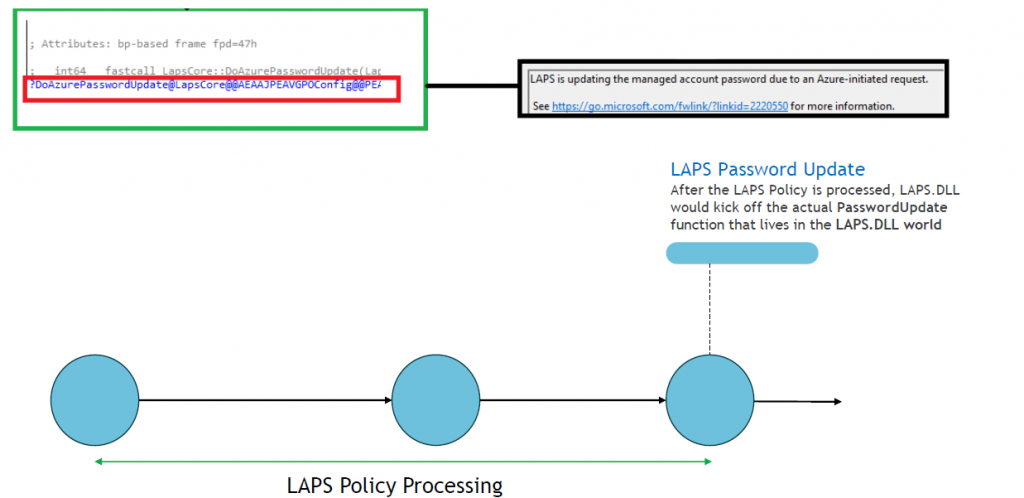
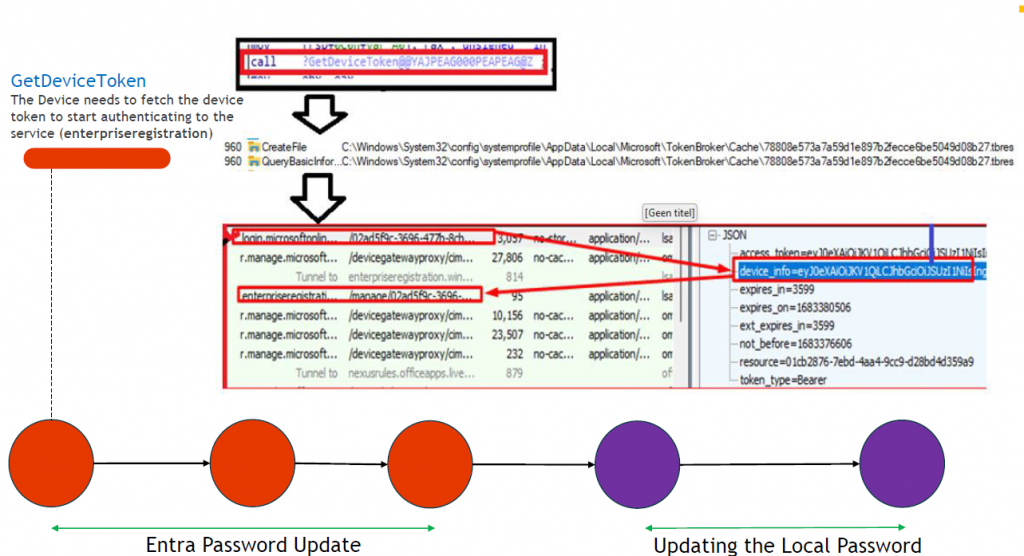
-The lapscoreprocessing function would call upon the DoAzurePasswordUpdate function. This function needs to get the devicetoken token to authenticate to Microsoft.
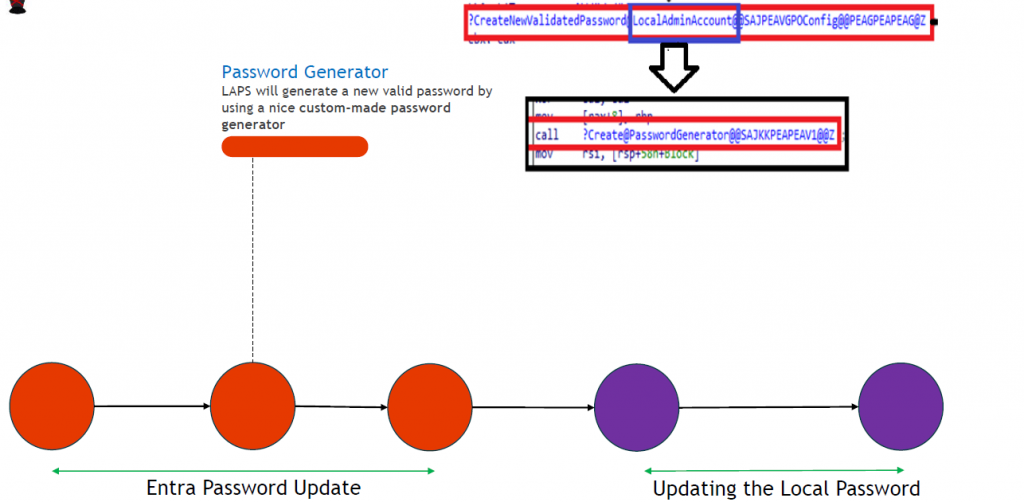
-If laps.dll was able to fetch the devicetoken and if the devicetoken is valid, LAPS.dll would start creating a new password and would validate the password against the existing password policy on the device.
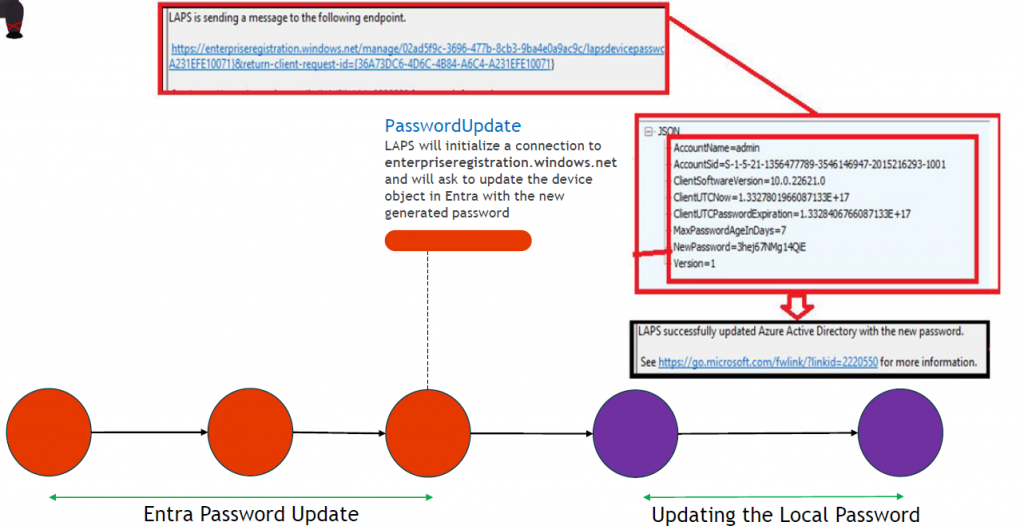
-The new freshly generated password would first be sent over to enterpriseregistration.windows.net. With the password being sent over to, the device its local admin password in Azure Ad would be updated.
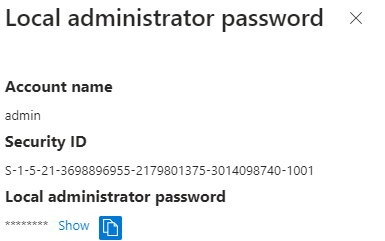
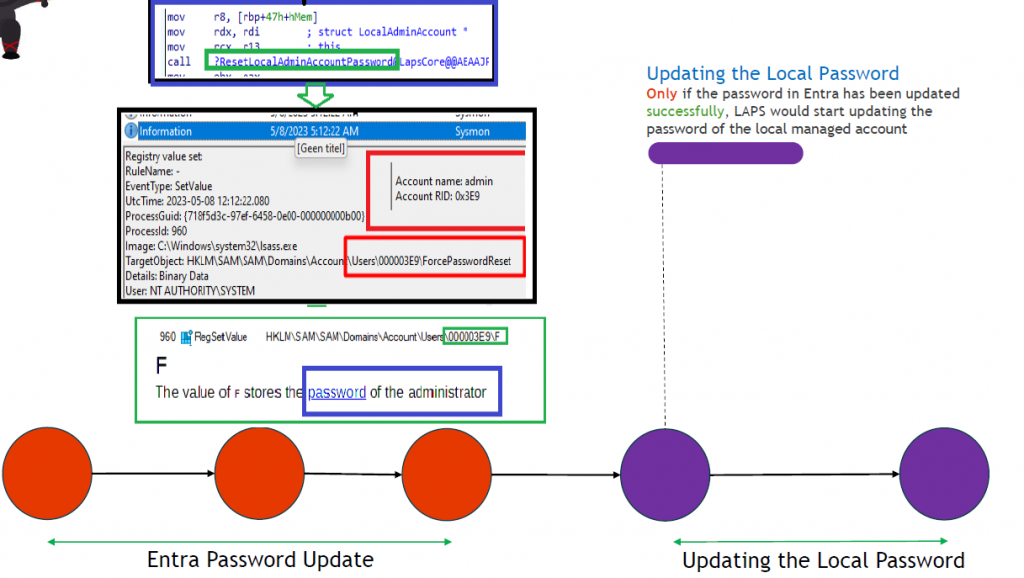
-After the password is sent over to Azure it would initiate the ResetLocalAdminAccountPassword function to make sure that the actual local admin password is also updated (with of course the same password 🙂 ) . We will notice this because lsass.exe performs a write operation to the SAM database.
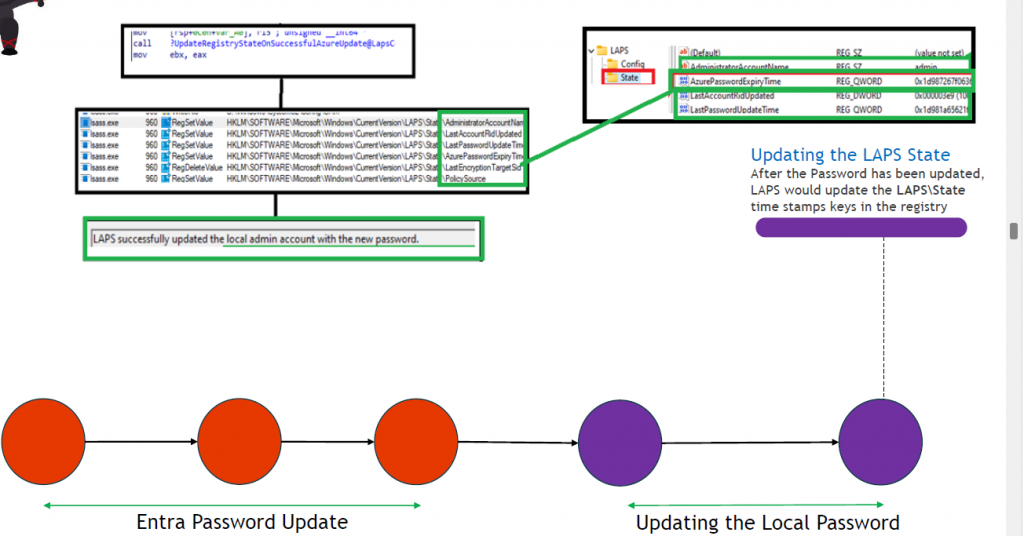
-Before the password rotation is done, lsass.exe will also update/set the LastPasswordUpdateTime and will show us the message that LAPS successfully updated the local admin account with the new password
5. My Key LAPS Takeaways
When I was looking at the rotate password functionality I was amazed by the stuff I didn’t know or have not noticed before.
Let’s start with the LRPC as I never have spent a lot of time looking at it. With the use of RPCMon and the get-rpcendpoint PowerShell function (again the NtObjectManager Module), it showed me the actual RPC Endpoint. Combining that information with the Procmon Trace and looking at the code with IDA taught me a lot about the process.
Besides the LRPC, not knowing about Threadpools and how those actions seem to be all queued (delayed and non-delayed) instead of using a scheduled task is just fantastic (okay I am no developer so…. Don’t blame me for not knowing about it)
I can only encourage you to start reading the learn docs to learn more about the Threadpool API as I found it pretty interesting!
https://learn.microsoft.com/en-us/windows/win32/api/threadpoolapiset/
6. Windows LAPS ETL Trace
I hoped I could also compare the Procmon/Fiddler/IDA flow with an ETL trace but that was harder than it looked. Let me explain!
First of I needed a trace provider to start the ETL trace. This was the easy part as we could get by opening the getlapsdiagnostics PowerShell Module
Provider: 177720b0-e8fe-47ed-bf71-d6dbc8bd2337
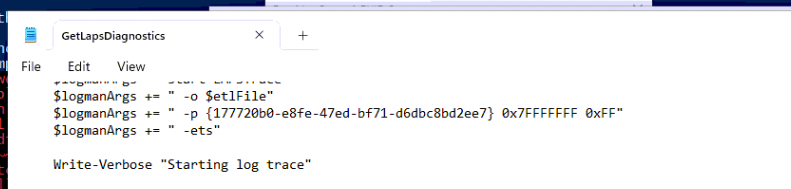
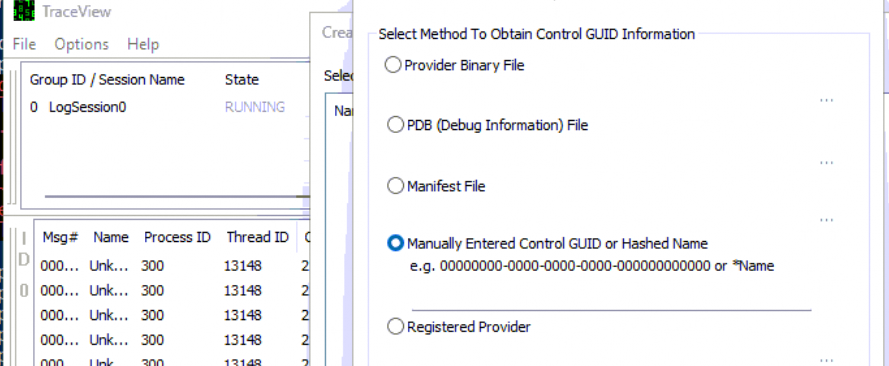
This time I used the traceview application instead of manually creating a WPR file to start a WPR trace. I only needed to enter the GUID we got from the PowerShell script
With the TraceView application ready for logging, I fired off the PowerShell script to rotate the password with the use of the CSP
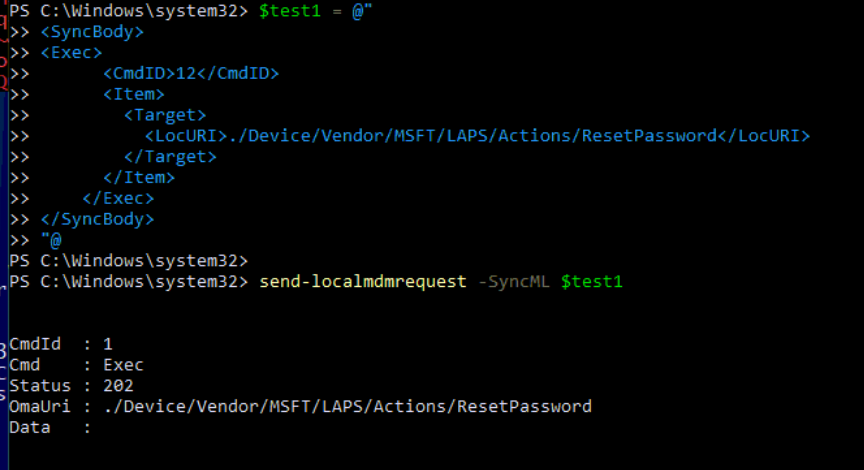
I was expecting some information but I ended up with the famous notification: No Format Information Found. The device doesn’t have the knowledge to transform the information into something human-readable.
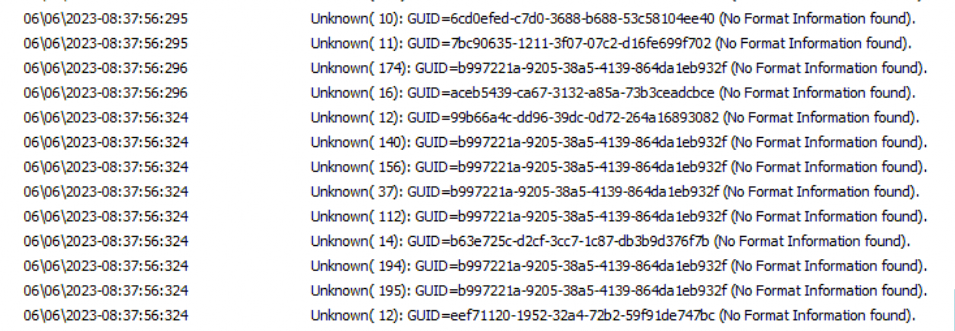
But……. 🙂 ….. If you spend a lot of time on it you can map the GUIDs to names manually. For example: EEF71120 is mentioned somewhere at the beginning and at the end of the trace.
When looking up that GUID, we will know that this GUID corresponds to the DoWork Function in the LAPS.Dll
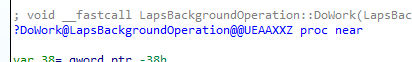
This function will call upon the function: DoCoreProcessing, which we also noticed in the flow
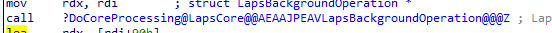
Besides the LAPS.DLL there are also some other files we need to inspect to fetch the proper WPP (Windows software trace preprocessor ) GUID.
When looking at one of the first WPP GUIDs being mentioned, dac792e, we also need to take a look at LAPSCSP.DLL
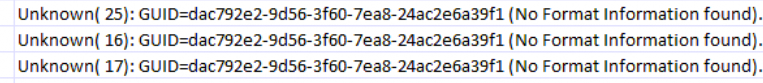
Inside this LAPSCSP.DLL we would find out the functions that are all tied together and are all making use of the same WPP GUID.
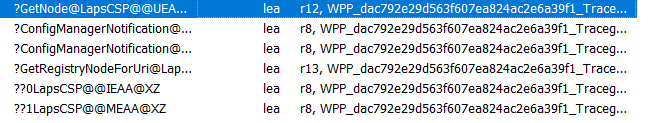
So, if you know the flow, this ETL file could fill in the gaps you have, and with all the gaps filled, you know what happened!
7. LAPS PAA and the Password reset
Besides the Intune Password rotation, the Post Authentication Actions (PAA) could trigger exactly the same …. and more. So if you want to know more about how PAA works, please read this blog below
Post Authentication Actions | Windows LAPS | SAMSRV (call4cloud.nl)
Conclusion
Maybe it’s just me but I want to know what happens when I press a button. Even when it sounds simple, mostly it isn’t! I hope that his blog taught you some about the Windows Laps Password rotation feature!
Besides this, I want to give a huge shout-out to the Microsoft Employee of the Month Jay Simmons! He is the guy who knows everything about Windows LAPS! Do you know why? He is the”one” that designed and built it!!!!!
The last few weeks I was in close contact with him and he literally explained all of the questions I had. And do you know what the most fun part is? He really liked me asking those nerdy questions about what’s happening at the code level!!
Much respect!


