Making sure your devices are up to date with the latest Microsoft updates is one of the key pillars of hardening your endpoints.
Updating your devices through Intune is a piece of cake. Setting up your Windows 10 update rings can be done within a few seconds.
Setting up the Windows update rings can be done manually, or you can automate the whole process. I personally like to automate the whole tenant deployment process. But that’s not the main reason of this blog.
You need to ask yourself; how can I monitor my endpoints to make sure the updates are successfully installed without the need of an azure log analytics instance? Personally, I would like to know when updates are failing on the customer endpoints!
So, how are we going to get notifications? you could set up an azure log analytics instance in combination with your OMS. But as you probably know, Microsoft and Solarwinds are collaborating, giving us more options.
Solarwinds also has his own patch management system. When using Solarwinds you can configure alerts when updates are failing. But personally, I don’t really like Solarwinds Patch MGT, I prefer Intune. So why not combining SolarWinds and Microsoft? I’ll show you how you can use Solarwinds to set up your Windows update monitoring.
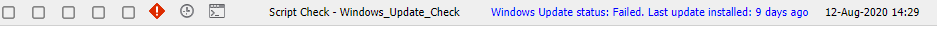
As the picture above shows, the script will trigger an alert when your endpoint has updates failing or when updates are not installed within the last 40 days. Of course, you can increase the amount of days to your liking.
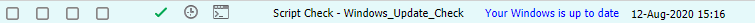
When your device has no failed updates and has installed updates within the last 40 days, everything is fine and you will receive no alert!
Function Convert-WuaResultCodeToName
{
param( [Parameter(Mandatory=$true)]
[int] $ResultCode
)
$Result = $ResultCode
switch($ResultCode)
{
1
{
$Result = "Inprogress"
}
2
{
$Result = "Succeeded"
}
3
{
$Result = "Succeeded With Errors"
}
4
{
$Result = "Failed"
}
}
return $Result
}
function Get-WuaHistory
{
# Get a WUA Session
$session = (New-Object -ComObject 'Microsoft.Update.Session')
# Query the latest 1000 History starting with the first recordp
$history = $session.QueryHistory("",0,1000) | ForEach-Object {
$Result = Convert-WuaResultCodeToName -ResultCode $_.ResultCode
# Make the properties hidden in com properties visible.
$_ | Add-Member -MemberType NoteProperty -Value $Result -Name Result
$Product = $_.Categories | Where-Object {$_.Type -eq 'Product'} | Select-Object -First 1 -ExpandProperty Name
$_ | Add-Member -MemberType NoteProperty -Value $_.UpdateIdentity.UpdateId -Name UpdateId
$_ | Add-Member -MemberType NoteProperty -Value $_.UpdateIdentity.RevisionNumber -Name RevisionNumber
$_ | Add-Member -MemberType NoteProperty -Value $Product -Name Product -PassThru
Write-Output $_
}
#Remove null records and only return the fields we want
$history |
Where-Object {![String]::IsNullOrWhiteSpace($_.title)} |
Select-Object Result, Date, Title, SupportUrl, Product, UpdateId, RevisionNumber
}
Try
{
$status = Get-WuaHistory | where-object {($_.title -like '*Cumulati*') -or ($_.title -like '*Security Update*') -or ($_.title -like '*Onderdelenupdate*')} | select -first 10
$check = $status[0].result
$date = $status[0].date
$updatefailed = $status[0].title
$datenow = get-date
$difference = New-TimeSpan -Start $date -End $datenow
$differencedays = $difference.days
#solarwinds check
If ($check -eq "Succeeded" -or $check -eq "InProgress" -and $differencedays -lt 40)
{
Write-output "Your Windows is up to date"
exit 0
}
else
{
write-output "Windows Update status: $check. $updatefailed. Last update installed: $differencedays days ago"
exit 1001
}
}
catch
{
Write-Warning "Value Missing"
exit 1001
}
Some information about the script:
- I am excluding the defender/skype updates when searching which updates are installed
- I am excluding the Inprogress status. I don’t really need to know that kind of information
Conclusion:
Of course, you will need to make sure your endpoints are up to date but please don’t forget to set up monitoring. Not monitoring Windows updates? Is it bad? As opposed to good? Yes, it’s really bad. It can be a security risk!.

