This blog will take you on a little journey into a discovery I made while exploring the new Administrator Protection feature in Windows 11. If you’ve been keeping up with my posts, you already know how exciting this feature is, but what I stumbled upon is even more exciting.
While digging around in the lsasrv.dll and the registry, I uncovered something that isn’t immediately obvious: the ShadowAdminPairs registry key. Let me tell you how it works and why you should care.
What is Administrator Protection?
If this is your first time hearing about it, Administrator Protection is Microsoft’s great attempt to improve security for local admin accounts. Instead of letting your admin token float around like candy in a jar, this feature locks it down, only pulling it out when necessary. Think of it as putting your local admin in “Clark Kent mode,” hiding that powerful Superman identity until it’s really needed, reducing the risk of someone hijacking those privileges.
The goal is to secure the Administrator privileges we use every day. It works great, even when you start adding ENTRA users to the local admin group. That’s where I noticed something interesting…
ShadowAdminPairs: A Key Discovery
While playing around with an Entra (AKA External SID) user as a local admin, I stumbled across the ShadowAdminPairs registry key.
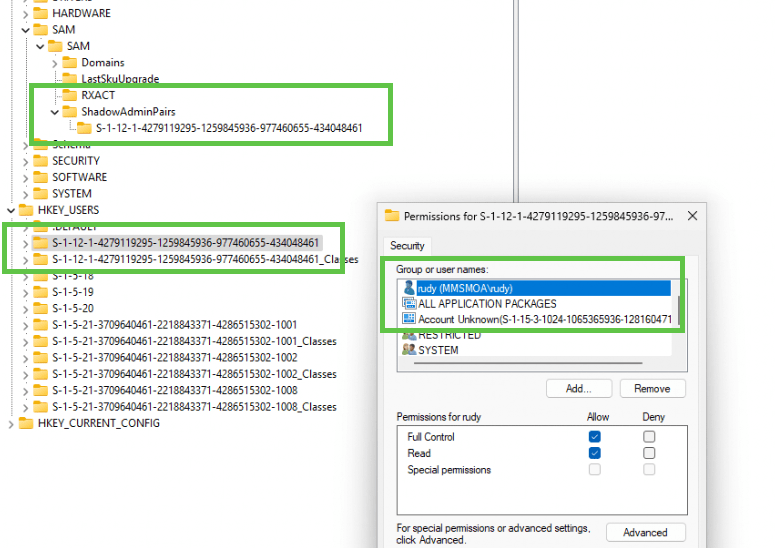
This key stores a mapping between foreign external Security Identifiers (SIDs), like the one used by Azure AD accounts, and the local account SIDs that Windows recognizes.
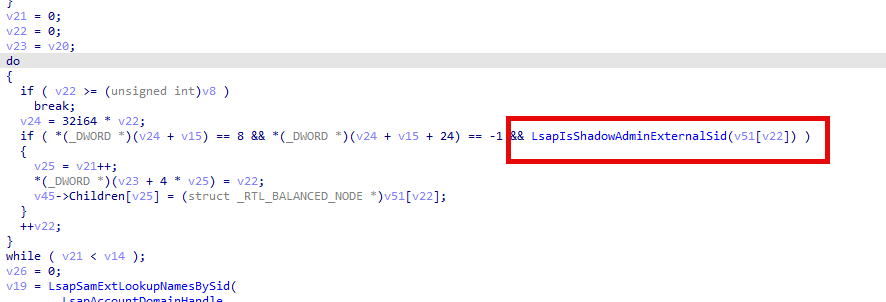
We can spot this behavior when looking at the lsasrv.dll. As shown below, it will check if the shadow admin account (Account protected by the Administrator Protection feature) is a local domain SID or belongs to an external SID.
From there on, it will try to build the Shadow Account Key Path. (Samsrv.dll)
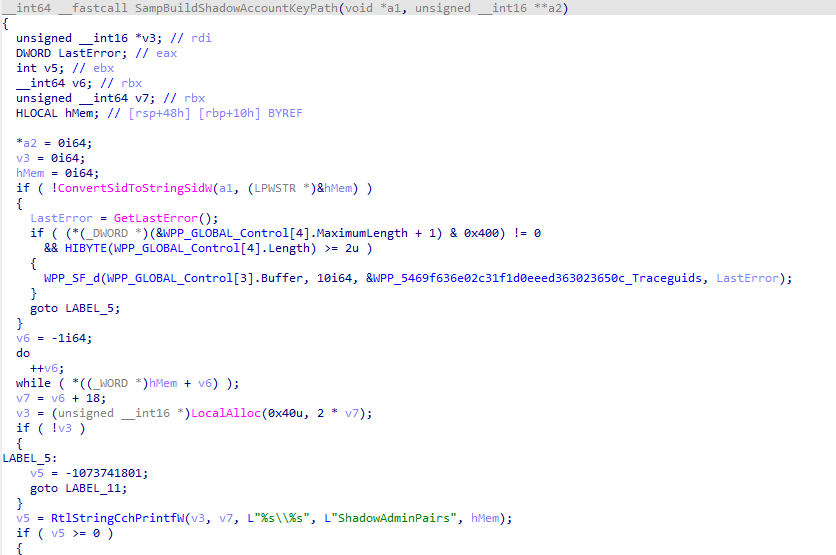
So, why does this key matter? When you add an Entra user to the local admin group, Windows needs a way to map that cloud identity back to the local context to handle permissions correctly. That’s exactly what the ShadowAdminPairs key does! The ShadowAdminPair is the bridge between the foreign (entra) SID and the local SID, allowing Windows to treat your ENTRA user as if they were a local admin.
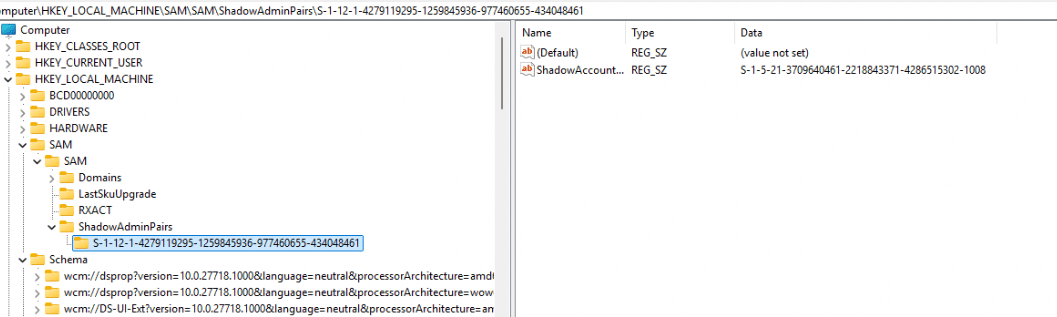
As shown above and below, the ShadowAdminPair is created the moment the Entra user becomes a local admin.
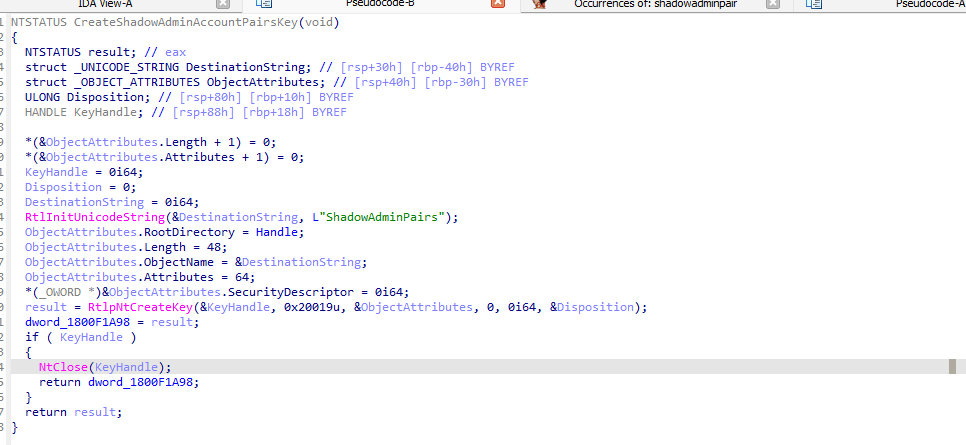
The Experiment: Deleting the ShadowAdminPairs Key
Out of sheer curiosity, I decided to delete the ShadowAdminPairs key to see what would happen. And, as expected, it didn’t go well! After removing it, I noticed errors cropping up when I tried to log in or perform any admin-level operations using my ENTRA account.
The system couldn’t correctly map the Azure AD SID to a local admin context anymore, and this led to errors like “The system cannot find the file specified”.
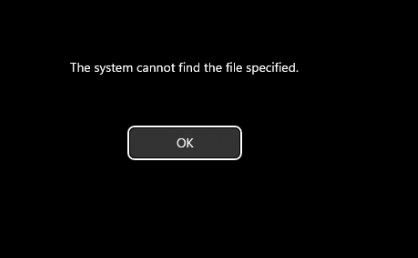
Essentially, Windows lost the mapping, and my Entra ID account wasn’t recognized as a local admin anymore.
Restoration and Behavior Change
Here’s where it gets interesting. After re-adding the missing ShadowAdminPairs key, everything started working again. The registry key restored the correct mapping between the ENTRA user (in my case, MMSMOA\rudy) and the corresponding local SID.
Here’s a breakdown of what happened when I restored the key:
- Registry Key Restored: The ShadowAdminPairs key in the registry now contains the foreign SID (something like S-1-12-1-4279119295-1259845936-977460655-434048461) and maps it to a local SID.
- Correct SID Mapping: This SID links back to my ENTRA user MMSMOA\rudy, as confirmed in the Permissions dialog. Now that the mapping is back in place, Windows can correctly map my foreign ENTRA SID to the local user context.
- HKEY_USERS Consistency: The same foreign SID also appears in the HKEY_USERS hive, confirming that Windows is handling this user identity correctly in both the registry and the SAM database.
Once the ShadowAdminPairs key was restored, the system could once again log me in as a local admin and handle elevation requests properly, without throwing any errors.
What is the ShadowAdminPairs Key?
Let’s dig a little deeper. The ShadowAdminPairs key is created when an ENTRA (or another cloud-based) user is added to the local admin group. Its purpose? Mapping the foreign SID from Azure AD to a local SID in Windows so that your ENTRA user can function as a local admin. This mapping allows the system to recognize and authorize external user identities in the same manner as it would local users.
Without it, Windows has no idea who you are in the local context, and everything breaks down
Here’s the structure of the ShadowAdminPairs key:
HKEY_LOCAL_MACHINE
└── SAM
└── SAM
└── RXACT
└── ShadowAdminPairs
└── S-1-12-1-<Foreign-SID> (Azure AD SID)
└── Local-SID-Value = S-1-5-21-<Local-SID> (Local Admin SID)
The foreign SID is mapped to the local SID. When you log in, Windows references this key to treat the ENTRA account as a local admin. Simple, right?
What Happens If It’s Missing?
If the ShadowAdminPairs key or an individual entry is deleted:
- The system loses the mapping between the external SID and the corresponding local account.
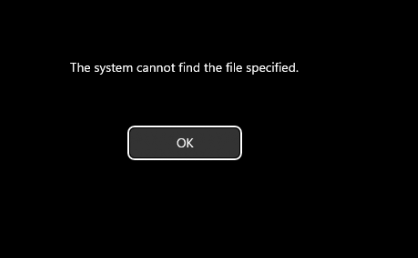
- As a result, operations that rely on this mapping (e.g., logins, elevation requests, or group membership checks) may fail with errors like “The system cannot find the file specified.”
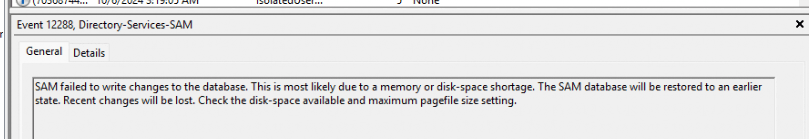
- This is because Windows attempts to locate a valid local SID for the foreign user and, without the ShadowAdminPairs mapping, it defaults to querying the SAM database, which either fails or returns an invalid SID. (event 12288)
Final Thoughts: Don’t Lose the ShadowAdminPairs Key
The ShadowAdminPairs registry key plays a crucial role in Windows 11’s Administrator Protection by mapping ENTRA user SIDs to local admin accounts. Without it, Windows loses the ability to correctly recognize and authorize cloud-based admin users, leading to login and elevation failures.
If you’re experimenting with Administrator Protection or managing local admin permissions, be mindful of this key. Deleting or modifying it without proper backups can break admin functionality, making troubleshooting a nightmare.


