This blog will focus on the 0x80190190 Bad Request (400) we could get because the SslClientCertReference is not configured and maybe a couple of other things. :). I will show you all the details you need to know to fix this issue, which is probably caused by a certificate that has the same {{DeviceID}} as your Intune MDM Device Certificate.
1. Introduction
When you have a local admin account on your device you use for break glass access, Windows LAPS could be a good solution. To activate Windows LAPS, you only need to take a few steps… its really really simple… at least if everything checks out!
What if somehow, that nicely created LAPS policy isn’t getting deployed to your devices? Last week, I was contacted by a company that ran into issues while deploying the LAPS policy.
That’s weird, right? So, what happened?
2. What we found out
The company noticed that their devices dropped out of Intune sometime ago because of the device cleanup rule they configured. As always, we need someone or something to blame, but the Intune cleanup rule wasn’t the one to blame.
When we took a closer look at the device, we noticed that it hadn’t checked in for some time, and because of this, the rule just did its job. Somehow, the Intune MDM certificate was NOT renewed on the device, and we all know what will happen when we have an expired certificate, right?

Expired certificate = No communication = No check-in = Device Rule Cleanup kicking in.
Why did that certificate expire in the first place? What happened with it? Let’s go back in time a bit to find out.
When circling back about when the issue started occurring, we noticed that it all started when the certificate was renewed last year. This looked successful in the first place, but something bad happened during the renewal. That “bad thing” started the device sync issues.
We decided to perform a remote session on one of the problem devices to gather some additional information.
- There were 2 Intune MDM device certificates on the device.
- Both did NOT have the private key attached and had now expired.
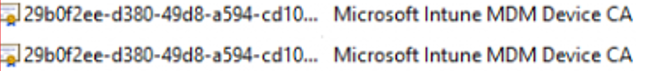
When we have two certificates on the device with the same subject name {{DeviceID}}, that is asking for problems, even Microsoft tells us the same story!
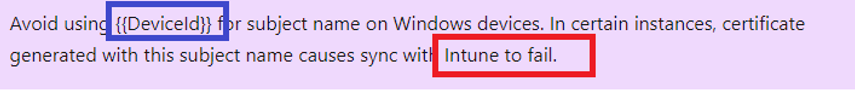
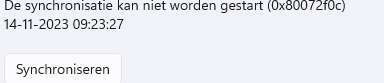
As shown above, this note tells us that certificates generated with the same subject name will cause sync issues with Intune. The moment we encounter this issue, we will notice that the sync cannot be initiated anymore (0x80190190 Bad Request (400).)
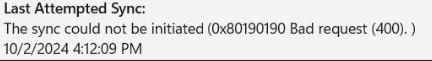
SSLClientCertReference
So somehow during the last renewal, we ended up with two certificates, not only two certificates with the same name but also some important registry settings that were missing. let’s compare a working and a not working device
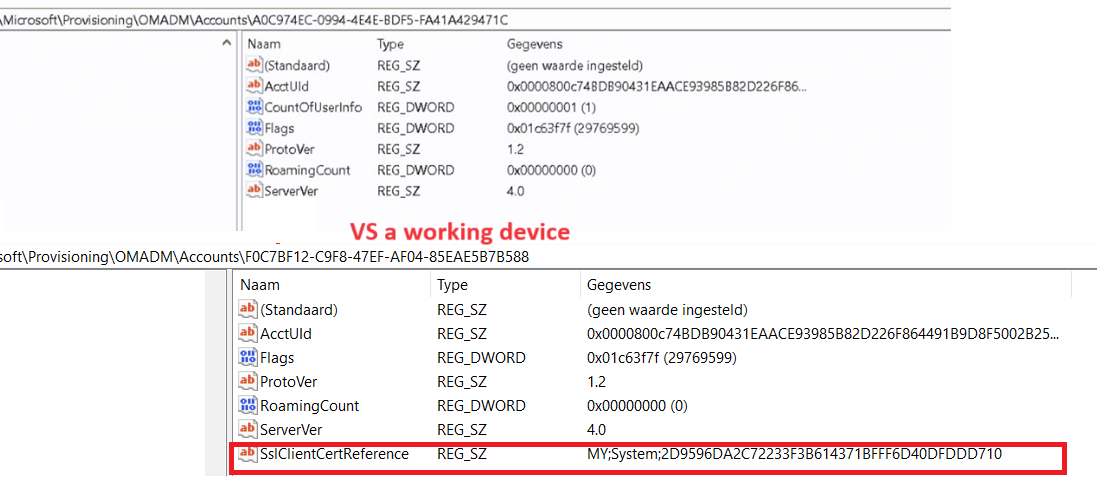
As shown above, we should have the SSLClientCertRefernce configured on a working device. This SslClientCertReference shows us the Certificate store in which it is living (MY;System) and the Intune MDM Certificate thumbprint that belongs to it. If you want to know more about where the Intune MDM Certificate should be stored, please read this blog:
https://call4cloud.nl/2022/09/intune-the-legend-of-the-certificate
With this important SslClientCertReference key missing we also could run into some weird issues when the OMADmClient needs to find the proper Certificate for renewal.
Fun fact: In a normal situation where you have just one certificate, this SslClientCertReference key and value should be automatically generated and set on the fly by the OMADMClient when our device is syncing with Intune.

The OMADMClient would kick off the GenerateSslClientCertreference function to start generating the required SSLClientCertReference
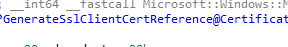
3. SslClientCertSearchCriteria
If the device is syncing, it must find the SSL Certificate, as that certificate secures the communication between the device and MMP-C Intune. Luckily, the OMADMClient has a nice function called GetSslClientCert.
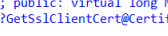
This function checks out the SslClientCertSearchCriteria, which specifies the client certificate search criteria and parses this information.
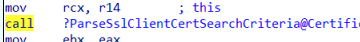
If somehow that SslClientCertSearchCriteria key is missing in action, the device would stop syncing immediately and would end up with the error 0x80072f0c
This SslClientCertSearchCriteria Registry key, as shown below, is based upon the entdmid (unique device ID for Intune…) and some additional stuff added.

Based on that outcome, the OMADMClient, knows where to find the certificate with that subject name in the given store AKA FindCertificateInStore
If you have two devices with the same EntdmID, I guess configuring and setting that value is going to be fun. Remember the picture I showed earlier to not have a certificate with the same deviceid?
I assume that when you have two certificates with the same deviceid, that value isn’t going to be set, and with it, you could end up in a world of pain and syncing issues.
Summing it up:
- The SslclientCertSearchCriteria needs to be configured.
- The Sslclientcertreference “should” be configured automatically when syncing.
Adding the missing private key and the expired cert to it, damn… Let’s switch back and take a look at what happened during the last renewal
4. PrivateKeyCreation
In this situation, it’s hard to know what happened because it all happened with the last renewal which was more than a year ago. Getting the root cause will be difficult for us, but luckily, some errors and issues will be stored in the Registry.
If we take another look at a previous blog I have written, we will notice that we could try to look up the last Renew Error Code
What happens when renewing the Intune MDM Certificate (call4cloud.nl)
We can do so by opening the registry and opening the Microsoft\Enrollment\Guidofenrollment and taking a look at the RenewErrorCode
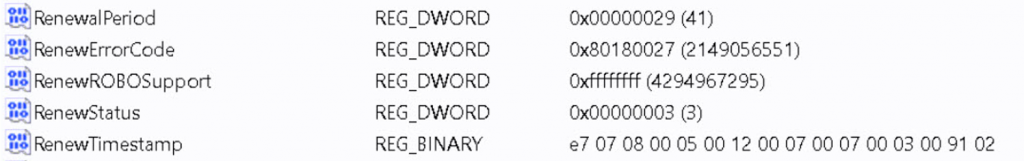
This error code will tell you what happened during the latest renewal. When looking up this error code: 0x80180027 (2149056551) we will find out that this error code is telling us that MENROLL_E_CERTPOLICY_PRIVATEKEYCREATION_FAILED AKA PrivateKey Creation Failed!
win32/desktop-src/MDMReg/mdm-registration-constants.md at docs · MicrosoftDocs/win32 · GitHub
This indeed corresponds with what we noticed: two Intune Certificates with the private key NOT attached! So, by the looks of it, when the certificate was up for renewal, the new Intune certificate came down to the device, but somehow, the Private Key creation failed (even when we can attach it manually with PowerShell?), and with it, the SSLclientcertreference was not set!
5. Detect and Remediate where possible
When you encounter all of these weird errors, you could, of course, run the IntuneSyncDebugTool. This tool will try to find each problem and fix it for you.
Intune Sync Debug PowerShell Tool to fix Intune Sync Issues (call4cloud.nl)
This tool needs to be run manually but what if we don’t want to run it manually? We could use some proactive remediations, right? Proactive remediations are cached on the device and will be executed when the Intune Management Extension detects that it needs to be executed.
Unfortunately, the IME doesn’t like to have an Intune Certificate without a Private key attached.

So, when we need to fix or prevent some of these issues, we need to have an additional tool in place or ensure you have configured a scheduled task on the device to do the same. (or rely on some other core functionality inside Microsoft’s code, which I am going to talk about in the next blog)
- The MDM Certificate Private Key is Missing
- The missing Sslclientcertreference
- The possible missing SslClientCertSearchCriteria
- The Expired Certificate
Fix 1: Private Key
Detection
# Intune Cert Name
$certName = "Microsoft Intune MDM device CA"
# Finding all certs with the certname and if private keys are missing
$certificates = Get-ChildItem -Path Cert:\LocalMachine\My | Where-Object { $_.Issuer -like "*$certName*" -and $_.HasPrivateKey -eq $false }
if ($certificates.Count -eq 0) {
Write-Host "Everything is fine!! no certificates without private key found"
exit 0
} else {
Write-Host "Certificate found with no private key. Hold my beer, I need to run some Remediation!!!"
exit 1
}
Remediation
# Intune Cert Name
$certName = "Microsoft Intune MDM device CA"
# Finding all certs with the certname and if private keys are missing
$certificates = Get-ChildItem -Path Cert:\LocalMachine\My | Where-Object { $_.Issuer -like "*$certName*" -and $_.HasPrivateKey -eq $false}
if ($certificates.Count -eq 0) {
Write-Host "Everything is fine!! no certificates without private key found"
exit 0
} else {
# Certificaten gevonden, loop door elk certificaat
foreach ($certificate in $certificates) {
# Certificaat heeft geen private sleutel
Write-Host "Fixing the Certs!!!"
# Voer certutil -repairstore my uit met de thumbprint van het certificaat
certutil -repairstore my $($certificate.Thumbprint)
}
exit 1
}Fix 2 : Sslclientcertreference
Detection
#Get guid of the intune enrollment (ignoring the MMP-C one)
$ProviderRegistryPath = "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Enrollments"
$ProviderPropertyName = "ProviderID"
$ProviderPropertyValue = "MS DM Server"
$GUID = (Get-ChildItem -Path Registry::$ProviderRegistryPath -Recurse -ErrorAction SilentlyContinue | ForEach-Object { if((Get-ItemProperty -Name $ProviderPropertyName -Path $_.PSPath -ErrorAction SilentlyContinue | Get-ItemPropertyValue -Name $ProviderPropertyName -ErrorAction SilentlyContinue) -match $ProviderPropertyValue) { $_ } }).PSChildName
$SslClientCertReference = $null
$SslClientCertReference = Get-ItemPropertyValue HKLM:\SOFTWARE\Microsoft\Provisioning\OMADM\Accounts\$GUID -name SslClientCertReference -ErrorAction SilentlyContinue
$Thumbprint = Get-ItemPropertyValue HKLM:\SOFTWARE\Microsoft\Enrollments\$GUID -Name DMPCertThumbPrint
$cert = Get-ChildItem Cert:\LocalMachine\My\ | Where-Object {$_.Issuer -Like "*Intune MDM*"}
$SslClientCertSearchCriteria = Get-ItemPropertyValue HKLM:\SOFTWARE\Microsoft\Provisioning\OMADM\Accounts\$GUID\Protected -name SslClientCertSearchCriteria -ErrorAction SilentlyContinue
if($SslClientCertReference -notlike "*$thumbprint*"){
write-host "SslClientCertReference is NOT set correctly!!!!!!!"
Exit 1
}else {
write-host "SslClientCertReference is set correctly"
Exit 0
}
Remediation
#Retrieve GUID for Intune Enrollment registry path
$ProviderRegistryPath = "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Enrollments"
$ProviderPropertyName = "ProviderID"
$ProviderPropertyValue = "MS DM Server"
$GUID = (Get-ChildItem -Path Registry::$ProviderRegistryPath -Recurse -ErrorAction SilentlyContinue | ForEach-Object { if((Get-ItemProperty -Name $ProviderPropertyName -Path $_.PSPath -ErrorAction SilentlyContinue | Get-ItemPropertyValue -Name $ProviderPropertyName -ErrorAction SilentlyContinue) -match $ProviderPropertyValue) { $_ } }).PSChildName
$Thumbprint = Get-ItemPropertyValue -Path HKLM:\SOFTWARE\Microsoft\Enrollments\$GUID -Name DMPCertThumbPrint
#Restores missing registry key based on GUID and Thumbprint
New-ItemProperty -Path HKLM:\SOFTWARE\Microsoft\Provisioning\OMADM\Accounts\$GUID -Name SslClientCertReference -PropertyType String -Value "MY;System;$Thumbprint" -Force
Fix 3: SslClientCertSearchCriteria
etection
#Get guid of the intune enrollment
$ProviderRegistryPath = "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Enrollments"
$ProviderPropertyName = "ProviderID"
$ProviderPropertyValue = "MS DM Server"
$GUID = (Get-ChildItem -Path Registry::$ProviderRegistryPath -Recurse -ErrorAction SilentlyContinue | ForEach-Object { if((Get-ItemProperty -Name $ProviderPropertyName -Path $_.PSPath -ErrorAction SilentlyContinue | Get-ItemPropertyValue -Name $ProviderPropertyName -ErrorAction SilentlyContinue) -match $ProviderPropertyValue) { $_ } }).PSChildName
#get the entdmid
$entdmid = Get-ItemPropertyValue "HKLM:\SOFTWARE\Microsoft\enrollments\$guid\dmclient\ms dm server" -name entdmid
#determine if the searchcriteria is set
$SslClientCertSearchCriteria = Get-ItemPropertyValue HKLM:\SOFTWARE\Microsoft\Provisioning\OMADM\Accounts\$GUID\Protected -name SslClientCertSearchCriteria -ErrorAction SilentlyContinue
$SslClientCertSearchCriteriagood = "Subject=CN%3d$entdmid&Stores=MY%5CSystem"
if($SslClientCertSearchCriteria -notlike $SslClientCertSearchCriteriagood){
write-host "SslClientCertSearchCriteria is not correct or not set"
#Exit 1
}else {
write-host "SslClientCertSearchCriteria is correct"
#Exit 0
}
Remediation
$ProviderRegistryPath = "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Enrollments"
$ProviderPropertyName = "ProviderID"
$ProviderPropertyValue = "MS DM Server"
$GUID = (Get-ChildItem -Path Registry::$ProviderRegistryPath -Recurse -ErrorAction SilentlyContinue | ForEach-Object { if((Get-ItemProperty -Name $ProviderPropertyName -Path $_.PSPath -ErrorAction SilentlyContinue | Get-ItemPropertyValue -Name $ProviderPropertyName -ErrorAction SilentlyContinue) -match $ProviderPropertyValue) { $_ } }).PSChildName
$entdmid = Get-ItemPropertyValue "HKLM:\SOFTWARE\Microsoft\enrollments\$guid\dmclient\ms dm server" -name entdmid
$SslClientCertSearchCriteriagood = "Subject=CN%3d$entdmid&Stores=MY%5CSystem"
New-ItemProperty -Path "HKLM:\SOFTWARE\Microsoft\Provisioning\OMADM\Accounts\$GUID\Protected" -name SslClientCertSearchCriteria -PropertyType String -Value "$SslClientCertSearchCriteriagood" -Force
Fix 4: The Expired Certificate
Some time ago I dedicated a blog to this issue and how you could fix the expired or missing Intune cert even when you can’t sync your device.
To fix this issue, I used the MDE connection to do so (sense). Of course, you could also use an additional RMM tool, like we do, to enroll the device again.
https://call4cloud.nl/2023/05/fixmissingintunecertificate-withmde/#part3
6. The Flow
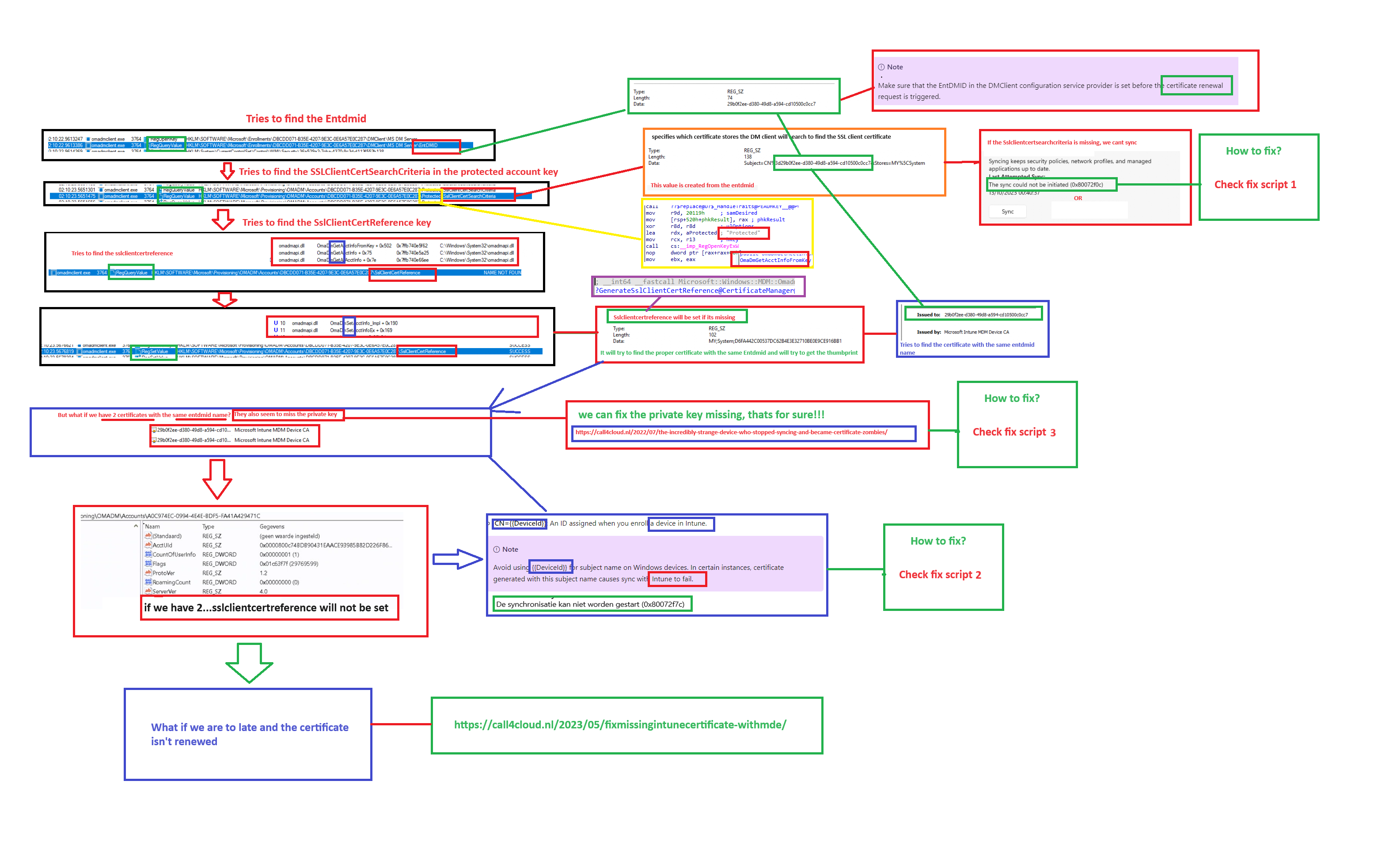
As always, the corresponding flow AKA my personal white screen MSpaint drawing board makes it more sense (at least for me)
7. What now?
I have provided you with the background information about what could have happened on the device, but still, a lot of pieces of the puzzle are missing. One thing is for sure: Something happened to a lot of devices more than a year ago that caused them to end up in the state I showed you above.
Wouldn’t it be nice if we also had another column we could add to our device blade in Intune? So that besides the Expiration date of the Management Certificate, we would also detect if there were issues with it?
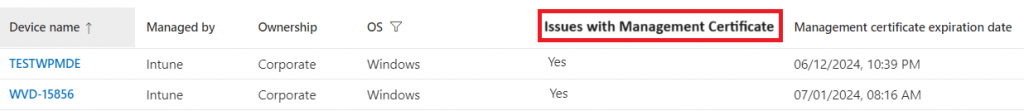
So my question to everyone who is reading this and has experienced the same issue is, please leave me a message because we still need to find the root cause. Luckily, we can fix it or prevent it, but we still want to know what happened! I will keep you posted when we find out what happened.
Conclusion
Even now, as we near the end of 2023, we could still be dealing with management certificate issues. Hopefully, this blog has shown you again how to detect them and how to prevent Intune management certificate issues from happening.



In fix 2 should I update those values?
$ProviderPropertyName = “ProviderID”
$ProviderPropertyValue = “MS DM Server”
If yes where i can find them this part is not clear that script need to be adjusted to environment.
ok i found that there is registry object ProviderID with Value MS DM Server ;]