The May update broke Windows Subscription Activation, causing devices to drop from Enterprise to Pro. The primary culprit was a breakdown in Multi-Factor Authentication (MFA). Microsoft addressed this issue with an August update, introducing the HandleAccessDenied mechanism, which partially fixed the problem by moving MFA-related registry keys from machine-level to user-specific paths.
This change allowed many devices to renew their subscriptions and upgrade back to Enterprise, but the fix wasn’t comprehensive, particularly for environments with multiple linked work or school accounts from different tenants on the device.
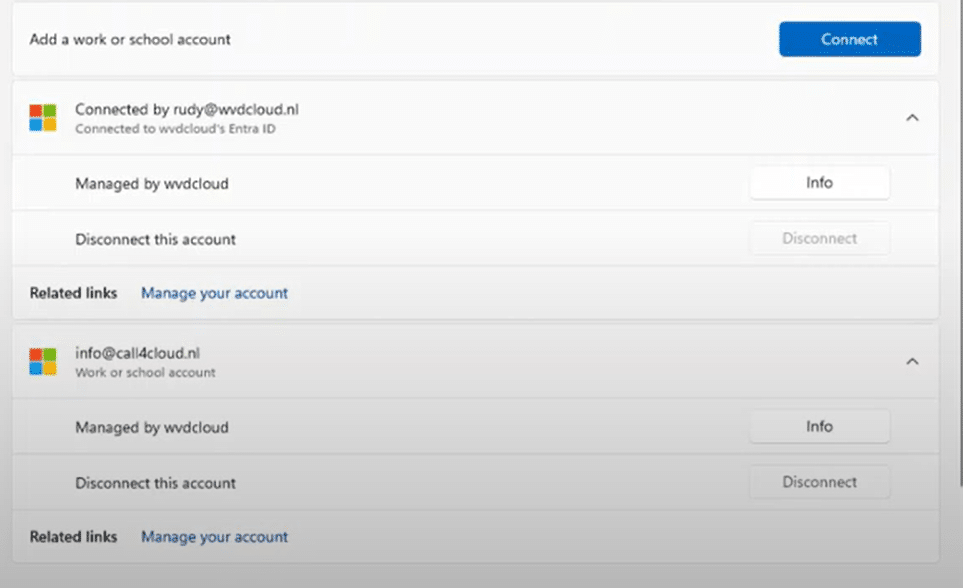
How Multiple Work or School Accounts Cause Problems
In some environments, users accidentally associate multiple AAD accounts from different tenants with a device, often when adding a second account to apps like Microsoft Teams.
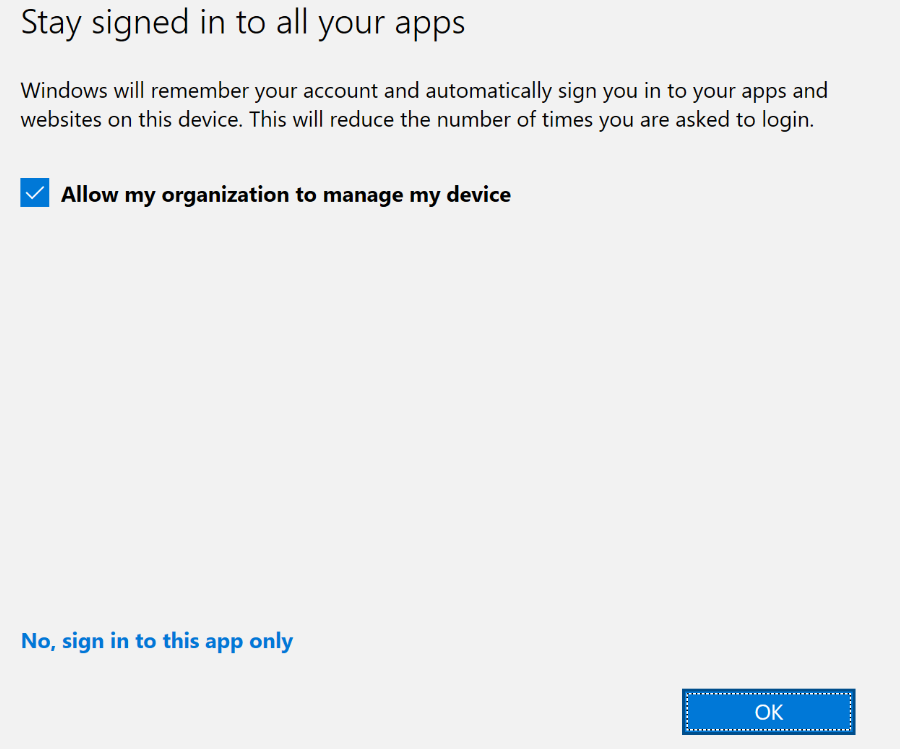
If they don’t select “Sign in to this app only,” the user will get an additional work or school account and, with it, become workplace joined. As shown below, the moment we added that account, dsregcmd /status will show within the User State that is WorkplaceJoined
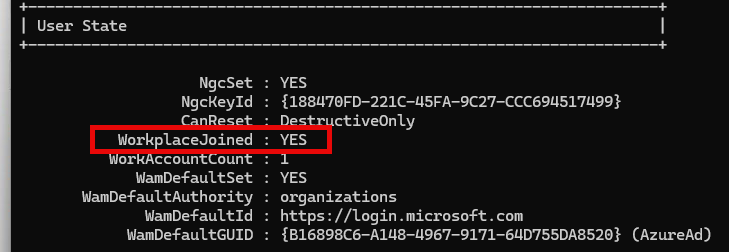
If we scroll down a bit, we will also notice the additional work account.
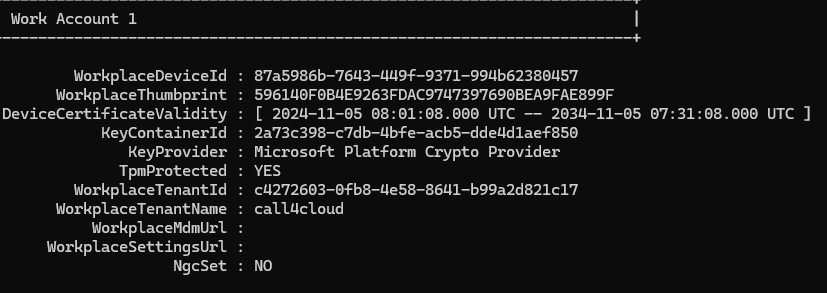
With this additional work or school account added, the LicenseAcquisitiontask may error out (0X87E10BF2)
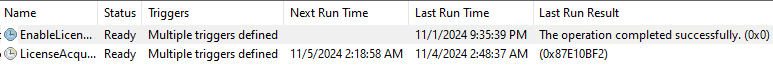
When this LicenseAcquisitiontask gives you the 0x87010bf2 error, one thing is for sure! You may have a conflict with subscription activation. Let me show you why it creates a conflict, but first, I need to explain again the role of the LicenseAcquistion task in it.
The Role of ClipRenew and LicenseAcquisition
The LicenseAcquisition task and ClipRenew play a vital role in subscription activation. Once the task is triggered, it works to:
- Create the License Request Body: This request contains critical data, including information about the users associated with the device. The request body holds all the user its identities, types, and other essential details.
- Communicate with Microsoft’s Subscription Service: After generating the license request, ClipRenew sends it to Microsoft’s licensing server to validate and issue the license.
- License Uplift: If the request succeeds, the device is uplifted to Enterprise. If not, as is the case in multi-tenant environments, the device remains stuck in Pro mode.
Now comes the funny part! Devices with multiple AAD accounts remain stuck in Pro, unable to uplift to Enterprise. This happens because the License Request Body—the JSON structure that the system sends to Microsoft’s servers, expects only one AAD tenant. It doesn’t expect multiple AAD accounts from different tenants when requesting the license!
The JSON License Request Body
To understand the problem better, let’s look at a simplified version of the License Request Body generated by ClipRenew:
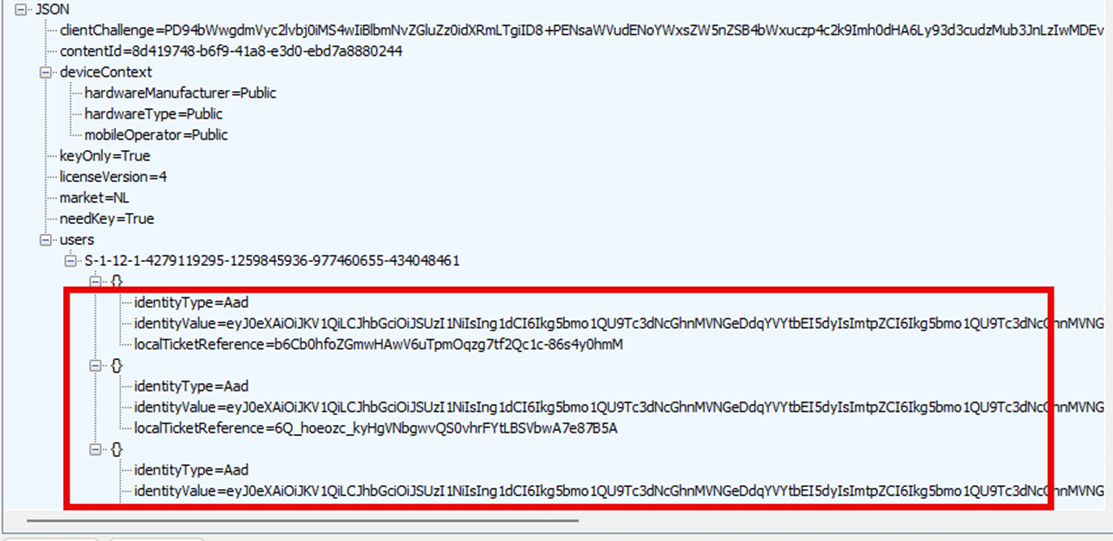
The “users” section lists all the AAD accounts linked to the device in this request. When multiple AAD accounts are present, the ClipRenew process seems to attempt to request a license for all AAD accounts. If more work or school accounts are connected to the device, the service will tell us that it got a bad request and will give us this error in the response.
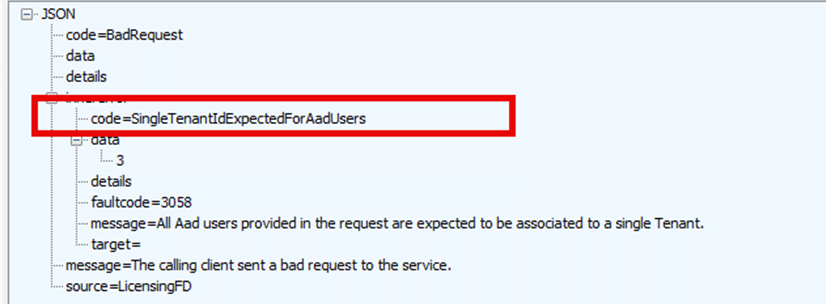
As shown above, the response is giving us a bad request. If we zoom into the details, we will spot a nice error code: SingleTenantIDExpectedforAadusers.
The Impact of Multiple Work or School Accounts
When multiple AAD accounts are linked to a device, the ClipRenew process fails to handle the conflicting accounts. The License Request Body includes the users part, which lists all AAD users associated with the device. However, ClipRenew expects only one AAD tenant, and when multiple are detected, the task fails with the error:
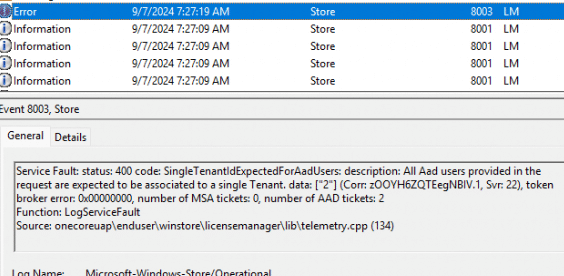
- Service Fault: status 400 code: SingleTenantIdExpectedForAadUsers:
- description: All AAD users provided in the request are expected to be associated with a single Tenant.
- Number of AAD Tickets: 2
This failure prevents the device from being uplifted back to Enterprise, leaving it stuck in Pro mode despite having valid licenses.
The Solution: Managing Multiple Work or School Accounts
The most effective way to resolve this issue is to manually disconnect any extra work or school accounts from Settings > Accounts > Work or School Accounts. This step removes the additional AAD accounts, allowing the LicenseAcquisition task to proceed with only one account, which successfully generates the license request and uplifts the device to Enterprise.
Step-by-Step Guide to Disconnect Extra Accounts:
- Open Settings: Navigate to Settings on your Windows device.
- Access Accounts: Click on Accounts.
- Work or School Accounts: Select Work or School Accounts from the sidebar.
- Identify Extra Accounts: Look for any additional accounts that shouldn’t be linked to the device.
- Disconnect: Click on the unwanted account and select Disconnect.
- Confirm: Follow the prompts to remove the account from the device.
By ensuring that only one AAD account remains linked, the LicenseAcquisition task can successfully process the license request, enabling the device to uplift back to Enterprise.
For the people not believing me
When you don’t want to do all that manual labor to fix the subscription activation issues when there are multiple work or school accounts connected to your user, please take a look at this additional blog:
Conclusion: A Partial Fix and What’s Next
While the August update addressed the core MFA issues from the May cliprenew issue, devices with multiple work or school accounts configured from different AAD Tenants, continue to struggle with subscription activation, and the ClipRenew process remains unable to handle these complexities. The result of these complexities is that the device will be stuck on Windows Pro.
Until Microsoft releases a more comprehensive fix, IT administrators will need to manually disconnect the AAD accounts. This ensures that devices can be uplifted properly from Pro to Enterprise, even in complex environments.



Hi Rudy,
Thanks for your help. Great job as always.
The problem we have in our company is that we need to add multiple work accounts to log into GlobalProtect for other clients with different Microsoft accounts, so we can’t have just one… Should we wait for Microsoft to solve this, or are the Entreprise subscriptions limited to devices with only one logged-in Microsoft account?
multiple account should give an issue… because the license is upgraded during the enrollment… if you add multiple accounts later on.. that shouldnt be an issue.. except if the deivce dropped down back to pro. than those accounts will cause issues
Hi Rudy,
On our side we have the same problem of Windows Enterprise which becomes Windows Professional again.
But we do not have the same causes. We are still on Windows 10 so the problem related to the bad patch from Microsoft is not the reason.
We have had a ticket open for almost a year with Microsoft support but it does not work. We tell them that we have the problem on Windows 10 but they have been trying to get us to install the Windows 11 patches for a month…
And when I see the store logs I see the opposite problem on our side. Windows does not seem to recognize any accounts for the license. while the accounts are properly connected and these accounts have the Windows Enterprise license.
We are with PCs managed by Autopilot in Hybrid mode.
Maybe you have an idea please? I can’t stand this problem anymore… 😉
Here is our store log:
Satisfaction error from service: 1: Users do not possess any satisfying entitlements for the content id in question. (Corr: +ualvkQ/OU2f5prY.45, Svr: ent-648465b664-67cjx), token broker error: 0x00000000, number of MSA tickets: 0, number of AAD tickets: 0
Function: LogSatisfactionError
Source: onecoreuap\enduser\winstore\licensemanager\lib\telemetry.cpp (177)
That licenseacquitision task… does that one get an error or?
Yes we have an error in settings\update and security\activation
It says that Windows Enterprise license is not valid.
And when we go en Setting/System/Shared experience we can click on repear. After that a pop up appear that says just a moment. It close and open again 3 times but it’s doing nothing and no error.
Rudy,
How about admin accounts that do not have any licenses attached to them in AAD? In our environment, we have admin accounts that IT users to exclusively login to VMs for all admin functions. We never have users with licenses attached login to these devices. Will this cause problems?
Thanks for all your hard work! Your blogs are some of the best on the internet!
Hi Rudy,
Thank you for this detailed article.
We have the same problem with several hundred devices. It’s difficult to manually delete multiple accounts other than those of our organization.
Is there a tracking number at Microsoft to have a resolution status ? I can’t find it on my side at the moment.
Thanks !
working on the 2 blogs that contains the autoamation.. as it steel needs to be tested a bit more 🙂
But this is one of the 2 possible solutions: if you could try them on q of those devices to find out if this one fixes this multiple aad tenant issue asw well.. that would be nice