In this blog, we’ll explore why it’s absolutely critical to lock down guest user access in your Entra ID tenant. Without proper restrictions, guest users could potentially access sensitive information, leaving your tenant exposed to unnecessary risks.
Previously, I covered this topic in two related blogs focused on securing the Azure AD portal:
If you haven’t read them yet, I recommend starting there to understand why locking down your Entra ID tenant is so essential. Now, let’s dive deeper into the specifics of guest user access, the risks of default settings, and how to secure your environment effectively.
1.The Default Guest Access Entra setting and why it’s bad
By default, guest users in Entra ID may have more access than you’d expect. If you haven’t adjusted the settings in your tenant, guest users can easily query group memberships or even list all users in a group.
While the default settings may seem harmless at first, they open the door to reconnaissance activities that could lead to security breaches. For example, with just one valid UPN, a guest user can start enumerating groups and accessing sensitive user data.
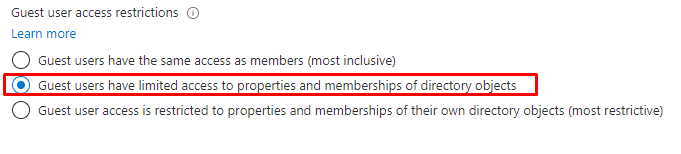
Even though the default setting prevents listing all users directly, it still allows guest users to retrieve group memberships—and this is where the real risk lies.
2. Taking a good look at the groups as a Guest user
Let’s see how guest users can exploit these default settings. Open a PowerShell session and connect to your Azure AD tenant as a guest user.
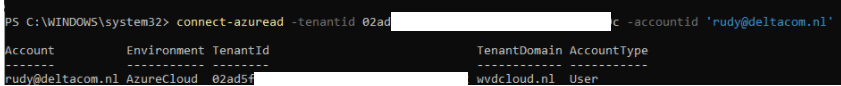
Like I told you in the first part, it isn’t possible to list all users. If you don’t believe me, just try it out yourself 🙂 !
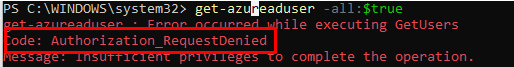
As expected, this will throw an error due to restrictions. But that’s not the end of the story. Just like the old Active Directory days when you could use commands like net group "domain users" /domain to enumerate users, Azure AD offers similar functionality for group memberships.
get-azureadusermembership -objectid(get-azureaduser -objectid ‘upn’).userprincipalname
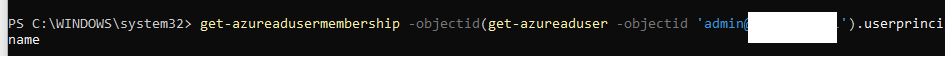
This reveals the group memberships for the specified user. If one of these groups is a licensing group, for example, you now have the Group Object ID. From there, you can list all members of the group:
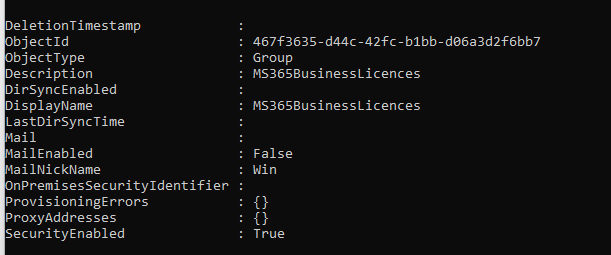
Now we have the Group object id, let’s list all the members with this command: get-azureadgroupmember -all:$true -objectid ‘groupid’
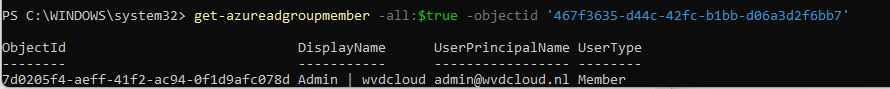
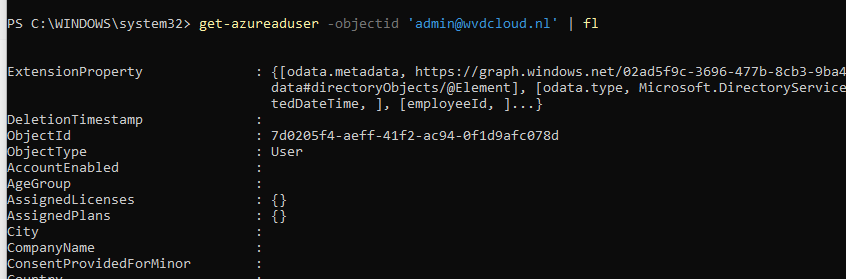
With this information, we can perform a get-azureaduser -objectid ‘upn’ | fl to get more information about the specific user. Please note… we can do this for all users!
3. Changing the Default Setting
To mitigate these risks, you’ll need to restrict group membership enumeration for guest users. This can be done via the Azure AD portal or PowerShell.
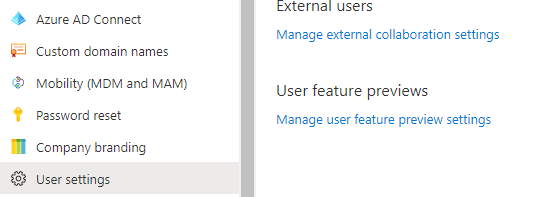
Using the Azure Portal:
Navigate to User Settings > Manage External Collaboration Settings and change the guest access permissions to block group membership visibility. You can access the settings directly here.
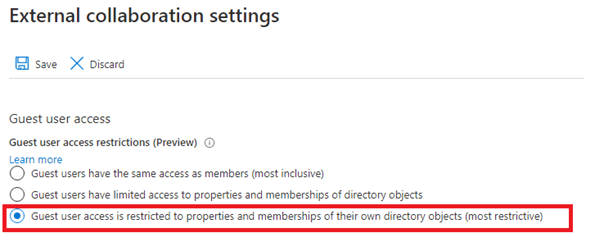
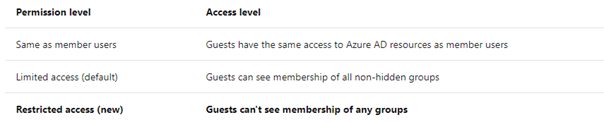
Using PowerShell:
For automation or consistency across tenants, use the following PowerShell command to adjust the guest user role:
get-AzureADMSAuthorizationPolicy | Set-AzureADMSAuthorizationPolicy -GuestUserRoleId ‘2af84b1e-32c8-42b7-82bc-daa82404023b’
Potential Impact on Teams
Restricting guest access can sometimes lead to issues with applications like Microsoft Teams, where searching for users may become restricted for guest users. Be sure to evaluate the impact on collaboration workflows and adjust your policies as needed.
Conclusion: Why Locking Down Guest Users Matters
Restricting group membership enumeration for guest users is a small but vital step in securing your Entra ID tenant. By blocking unnecessary visibility, you prevent potential reconnaissance and ensure that sensitive information stays protected.
If you’re interested in learning more about securing your tenant, check out these related blogs:
Remember, when it comes to guest access, the default isn’t enough—take control of your settings and lock it down!

