This blog will be an additional blog to the TPM attestation series I wrote some time ago. In this one, I am going to take a closer look at why Attestation is timing out on a lot of HP G9 Serie devices when you are using Windows Autopilot for Pre-Provsioned deployments (or self-deploying)
1. Introduction to TPM Attestation errors
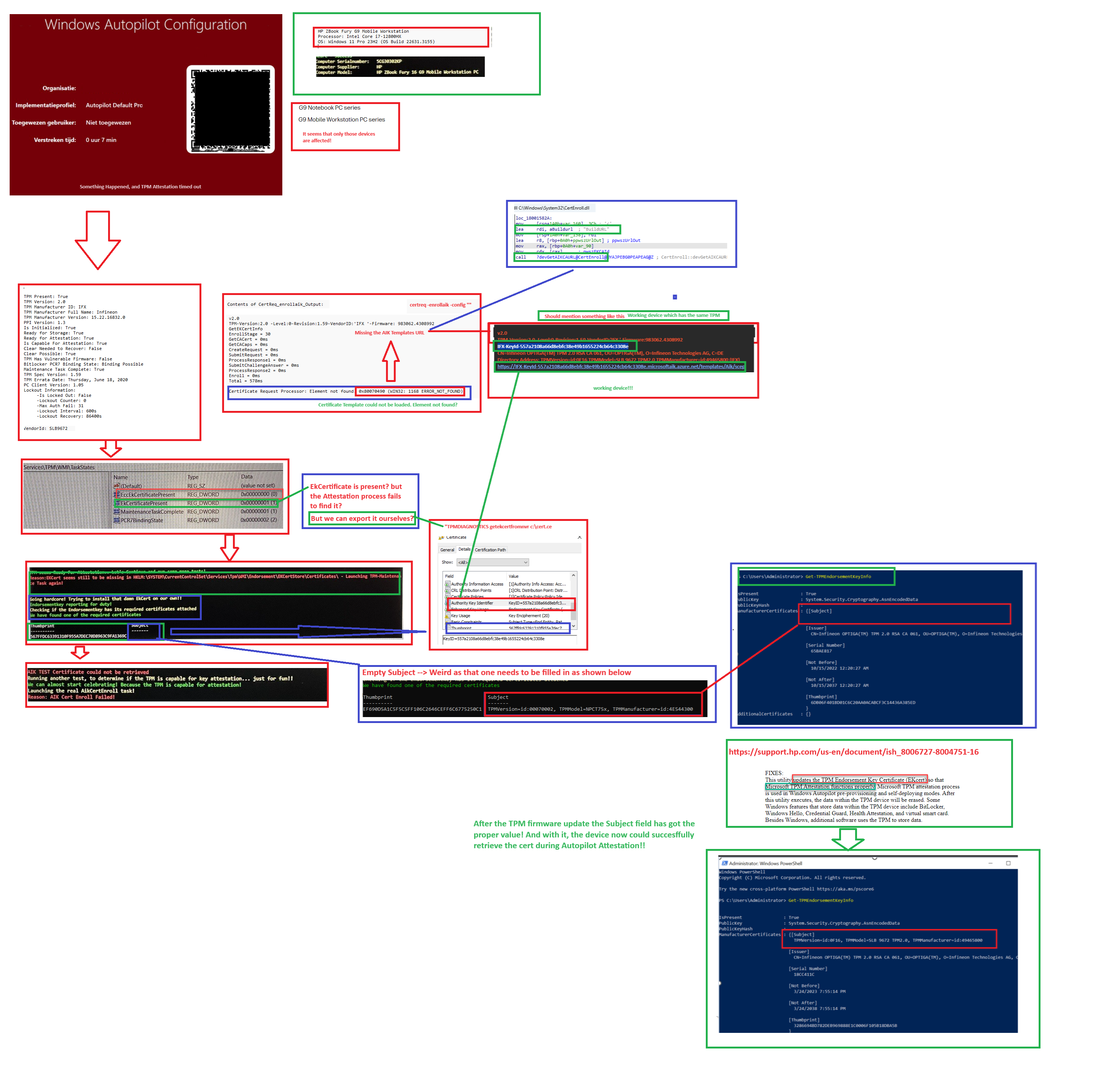
A week ago, I received an email message in which someone was asking for help. He was trying to enroll his HP ZBook Fury G9 Mobile Workstation with Autopilot for Pre-Provisioned deployment.
While trying to perform a TPM Attestation, something happened, and a TPM attestation time-out occurred.
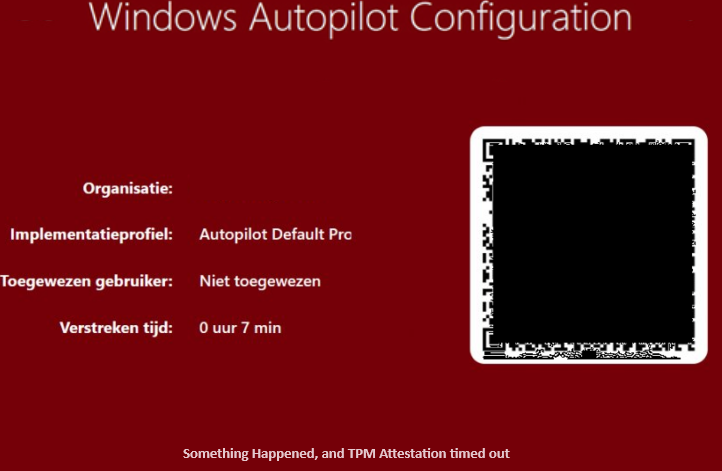
When the attestation fails, you will have a failed Autopilot enrollment. Attestation is needed to prove the system’s trustworthiness and to show that it has not been tampered with. Without it, the Entra Join will not happen!
The funny thing is, that other HP G10 devices with the same TPM and firmware seem to be enrolling without any issue.
Besides the working g10 devices, he already tried fixing the TPM attestation issues with the tool I wrote some time ago, making it even more interesting. So I guess this blog post is going to be an additional one to the TPM attestation series I wrote some time ago
Attestation and Compliance Series – Call4Cloud – Intune | MMP-C | WinDC | Autopilot
Shall we take a look at what was happening on the device?
Oh, wait. Before you do… you need to read this blog. (If you know what ready for attestation truly means… you are good to go!)
https://call4cloud.nl/2022/08/ready-for-attestation-a-true-underdog-story
2. The Main Issue
As mentioned in the introduction, he also tried to run the TPM diagnostics tool I wrote some time ago.
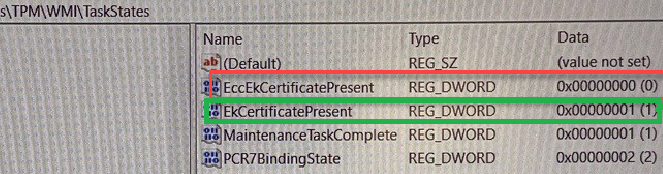
When looking at the output, it is pretty obvious that the Endorsement Key Certificate seems to be missing on the device (at least in the WMI task states registry key).
This EKCertificate is required to build the AIK attestation URL, so without it to valid AIK URL. As shown below, it seems that the first attempt to check the Certificate Failed.
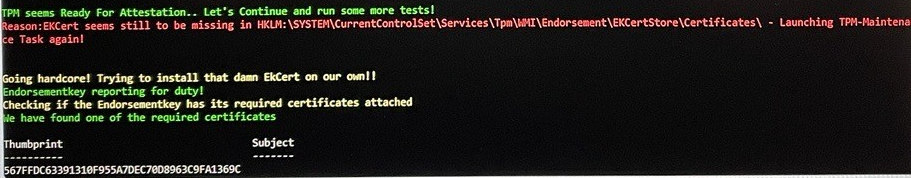
From there on the script tries to manually find and install the Ek Certificate itself, which seems to work. The only weird thing in the output above, is that the “Subject” is empty? So far, I know, this should contain some more information.
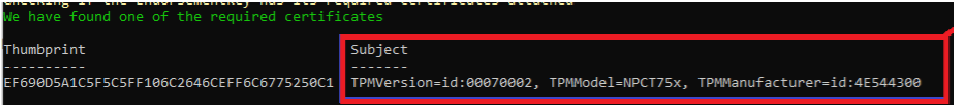
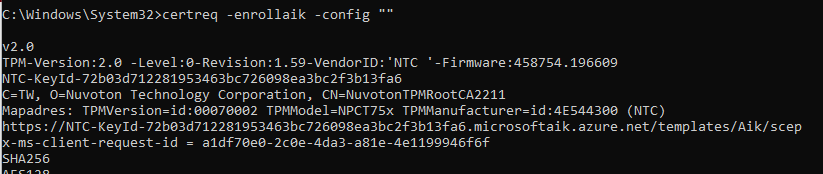
It looks that even with my TPM attestation script getting the EK Certificate, retrieving the test AIK Certificate with the certreq -enrollaik -config “” command was still failing
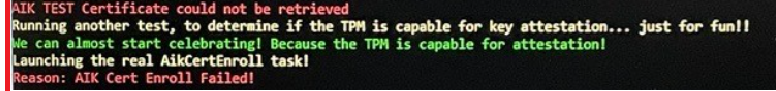
That’s weird, so I asked him if he could manually run the same command.
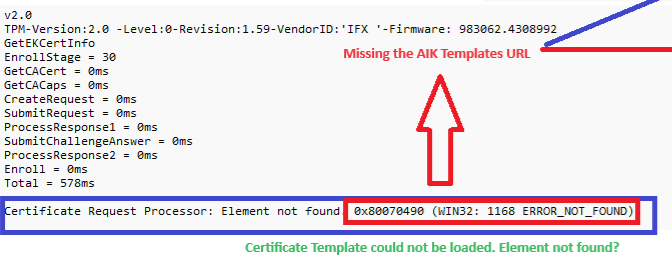
As shown above, the base request is trying to get more information about the EkCertificate but it doesn’t show any information about it. Instead, it is giving us the error message: Element not found (0x80070490) and the corresponding (Win32: 1168 ERROR_NOT_FOUND). This error message indicates a problem with getting the templates. This could be very true when looking at the certreq.exe. The first step it will take is getting the template property.
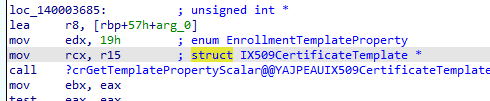
Once it gets the template, this request should start by creating the subject alternative name from the EK key first
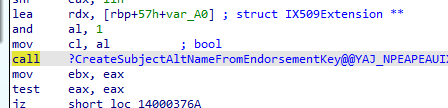
This Subject’s Alternative name correlates to the missing Subject information we noticed in the Certreq request
If it gets the Subject Alternative name, it will try to get all the information about the Manufacturer and the EkCertificate
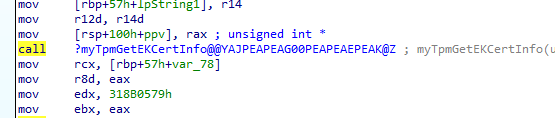
Which performs an external call to the crypttpmmeksvc.dll, which would fetch the information of the EkCert
If that doesn’t fail (as we noticed with the HP G9 Series) this is what we should get in a successful request.
I guess it’s pretty obvious that we have an issue fetching the Endorsement Key Info. We will spot the same kind of behavior when we manually execute the get-tpmendorsementkeyinfo.
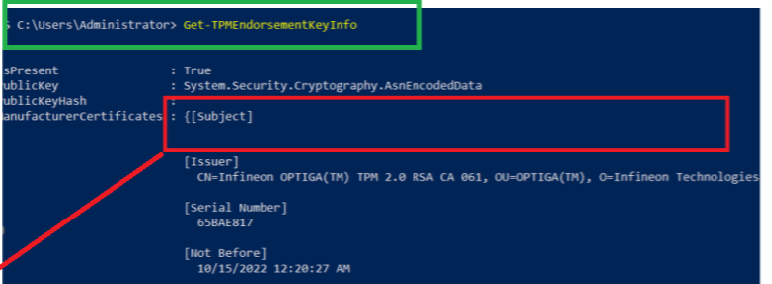
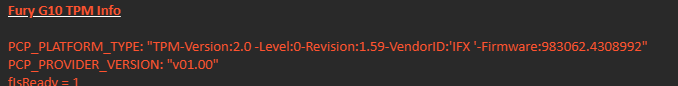
As shown above, the Manufacturer Certificate shows the empty subject we also noticed. How are we going to fix this issue? It starts to look like an HP issue and not a Microsoft Issue because the working G10 HP device has the same TPM firmware: 983062.4308992 as the G9 one
3. The Hidden Fix
Luckily, there is an easy fix to ensure your HP Elite, EliteBook, Pro, Probook, ZBook, and a lot more G9 HP series will be able to perform a successful attestation.
There seems to be a very hidden document on the website of HP, that mentions all of the g9 devices that had issues during Autopilot and performing attestation
support.hp.com/us-en/document/ish_8006727-8004751-16
In this HP document, you will find a link to an Endorsement Key Certificate Update Utility.
https://ftp.hp.com/pub/softpaq/sp148001-148500/sp148219.exe
This utility updates the TPM Endorsement Key Certificate (EKcert) so that Microsoft TPM Attestation functions properly.
That indeed sounds like what we need! After running the get-tpmendorsementkeyinfo command on a different HP G9 device, we immediately spot the difference.
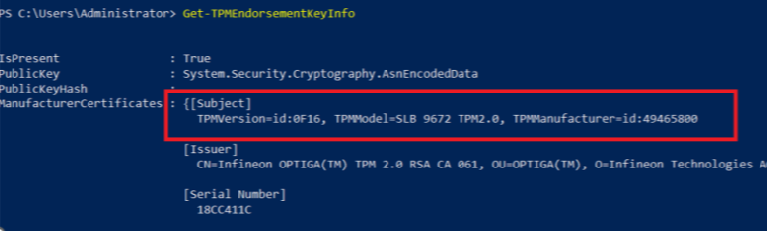
As shown above, we now have a filled-in subject. After the tool did its job we restarted the Autopilot enrollment and within a few seconds, TPM attestation was successful!
You might be wondering why I called it a hidden document… Well, this is why. When searching for that file or any keywords you will get zero useful results!
4. The flow everyone loves, right?
Conclusion
Hopefully, this blog post will increase the number of search results, and people who are experiencing TPM attestation issues with their HP G9 Devices will have an easy fix!



Great article and detailed explanation.
I am having the same exact issue but on a virtual machine on HyperV. Do you think there is a fix for this from MS like the one from HP?
Did you also checked https://call4cloud.nl/autopilot-0x80280009-tpm-attestation-virtual-machine/ … as tpm attestation is not possible on hyper-v
Weird. I’m getting this issue on a Dell Precision 3470. It was working ok previously.
Could you Perform these steps:
Initialize-TPM -AllowClear
Clear-TPM
Reupload the hardware hash
And try again? (it seems that after the tpm firmware upgrade somethings were messed when it compared the ekcert with the ekpub)
We executed these steps on a 23h2 widnwos build .. and afterwards we reinstalleed the device with 24h2 and tried again (which now worked)
I’m getting the ‘Element not found. 0x80070490 (WIN32: 1168 ERROR_NOT_FOUND) when I run ‘certreq -EnrollAIK’ config “”‘ on some Dell Latitude 5420.
However the Get-TPMEndoresementKeyInfo returns a valid looking [Subject]:
TPMVersion=id:00010101, TPMModel=ST33HTPHAHD4, TPMManufacturer=id:53544D20
Autopilot pre-provisioning is failing for me on 3 of these Dell devices. Is there a similar fix from Dell?
Do you have the full output of that command? (get-tpmendorsement and the cerreq command?)
C:\Windows\System32>certreq -EnrollAIK -config “”
v2.0
TPM-Version:2.0 -Level:0-Revision:1.59-VendorID:’STM ‘-Firmware:66305.0
GetEKCertInfo
EnrollStage = 30
GetCACert = 0ms
GetCACaps = 0ms
CreateRequest = 0ms
SubmitRequest = 0ms
ProcessResponse1 = 0ms
SubmitChallengeAnswer = 0ms
ProcessResponse2 = 0ms
Enroll = 0ms
Total = 515ms
Certificate Request Processor: Element not found. 0x80070490 (WIN32: 1168 ERROR_NOT_FOUND)
PS C:\Windows\System32> Get-TpmEndorsementKeyInfo
IsPresent : True
PublicKey : System.Security.Cryptography.AsnEncodedData
PublicKeyHash :
ManufacturerCertificates : {[Subject]
TPMVersion=id:00010101, TPMModel=ST33HTPHAHD4, TPMManufacturer=id:53544D20
[Issuer]
CN=STM TPM EK Intermediate CA 06, O=STMicroelectronics NV, C=CH
[Serial Number]
7F439FA014470A10C73632ED1D1A0A557DD8E4AB
[Not Before]
2/28/2021 4:00:00 PM
[Not After]
12/31/2031 4:00:00 PM
[Thumbprint]
DEE56AA7CCE0057648BB41A50EDF6FEDBC294F22
}
AdditionalCertificates : {}
Did you also tried this download from dell? https://dl.dell.com/FOLDER11323524M/1/DELLTPM_STHE4_1.769_64_v3.exe (noticed the 2024 release date)
I’m seeing exactly the same on a Latitude 7320 – it had been happily pre-provisioning, but out of apparent masochism I cleared the TPM, and now it’s failing attestation in exactly the manner above. I’ve updated the TPM firmware to 1.769 and that hasn’t changed much. It is just in warranty – is it worth contacting Dell to see if they offer any insight?
its worth a try.. but i am going to pretty much assume, there are not going to do anything about it :(..
Could you Perform these steps:
Initialize-TPM -AllowClear
Clear-TPM
Reupload the hardware hash
And try again? (it seems that after the tpm firmware upgrade somethings were messed when it compared the ekcert with the ekpub)
We executed these steps on a 23h2 widnwos build .. and afterwards we reinstalleed the device with 24h2 and tried again (which now worked)
Yes! I did find that TPM update from Dell and applied it, convinced it would fix the issue, but disappointingly, no change!
Could you Perform these steps:
Initialize-TPM -AllowClear
Clear-TPM
Reupload the hardware hash
And try again? (it seems that after the tpm firmware upgrade somethings were messed when it compared the ekcert with the ekpub)
It worked on 23h2 .. and afterwards we reinstalleed the device with 24h2 and tried again
To be sure… did you also downloaded this bios?
https://dl.dell.com/FOLDER12339819M/1/Latitude_7X20_1.39.0.exe
I got this issue since years ago:
v2.0
TPM-Version:2.0 -Level:0-Revision:1.38-VendorID:’AMD ‘-Firmware:196665.5
AMD-KeyId-52fb59e29aa83a962fb9eef0fe5b4811de6b751e
CN=PRG-RN, O=Advanced Micro Devices, S=CA, L=Santa Clara, C=US, OU=Engineering
https://AMD-KeyId-52fb59e29aa83a962fb9eef0fe5b4811de6b751e.microsoftaik.azure.net/templates/Aik/scep
GetCACaps
GetCACaps: Not Found
{“Message”:”The authority \”amd-keyid-52fb59e29aa83a962fb9eef0fe5b4811de6b751e.microsoftaik.azure.net\” does not exist.”}
HTTP/1.1 404 Not Found
Date: Tue, 03 Dec 2024 16:28:18 GMT
Content-Length: 121
Content-Type: application/json; charset=utf-8
X-Content-Type-Options: nosniff
Strict-Transport-Security: max-age=31536000;includeSubDomains
x-ms-request-id: 265ab885-8ac8-497c-a06e-54ddb2f5b295
EnrollStage = 140
GetCACert = 0ms
GetCACaps = 640ms
CreateRequest = 0ms
SubmitRequest = 0ms
ProcessResponse1 = 0ms
SubmitChallengeAnswer = 0ms
ProcessResponse2 = 0ms
Enroll = 0ms
Total = 2515ms
Certificate Request Processor: Not found (404). 0x80190194 (-2145844844 HTTP_E_STATUS_NOT_FOUND)
Not sure how to fix it. Laptop it’s a GA508 Zephyrus from Asus
sounds like the aik attestation service (url) was not put in place.. did you checked the tpm cab file if it mentions that url and if it was removed?
Yes, it mentions that was removed, I just don’t know how to replace or generate a new one