Some time ago I wrote a blog about securing your data in which I described that this is only the first step in making sure your data is safe.
I will divide this blog into multiple parts
1.What to Protect?
For example, whilst working with Teams, did you think about the “shadow users”?
These users are not members of your Teams / Microsoft 365 groups but can still somehow access your data.
It’s very easy for an employee to share the whole Teams general folder within the Sharepoint site without you noticing. An employee just has to click on “share” to begin sharing it with an external user.
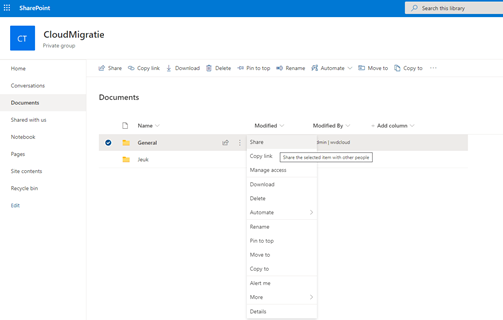
There are some barriers you can create. Some of which I already mentioned:
2. Start locking down the Office 365 tenant
But how can we protect the important Office 365 data, so we can be sure the data stays where it needs to be. To briefly sum up a few:
- The best option you got is labeling all your sensitive data. For example: You can create a sensitivity label with the same name as your Team / Microsoft group. You can set the encryption so only your own employees can open the data.
- You can create a conditional access rule to prevent downloading from non-compliant devices.
- Like I mentioned in my last blog, you can create group labels. When creating a new team you can choose to select the label to prevent users from adding guests.
- Disable the possibility to let members share the site/folders and files. When choosing this option, only the site owners can share files/documents. This might not be a good fit for your organization if you collaborate a lot with external users.
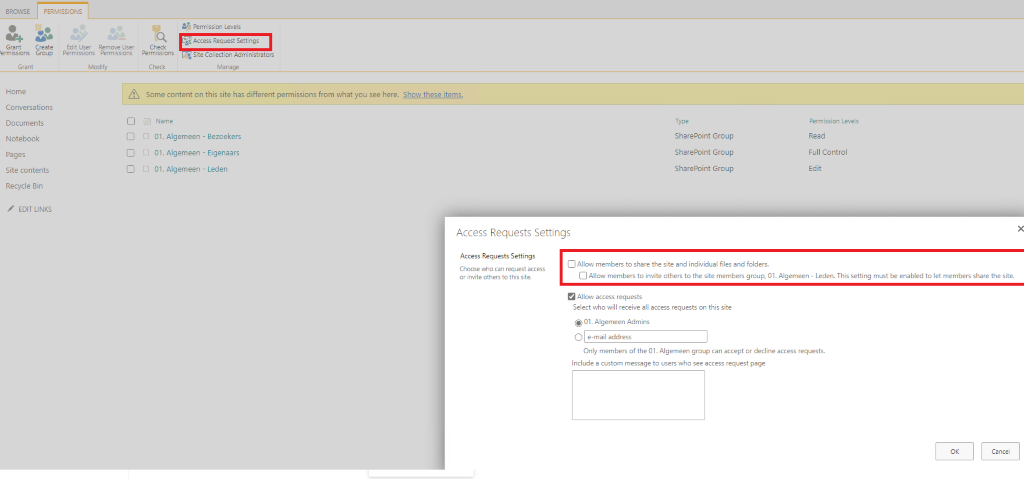
- The last and probably the worst option you have is to disable external sharing at all. Of course, this is not an option for most businesses. Users will just find other ways to share their documents and collaborate. So instead of blocking collaboration entirely, let’s tighten the screws a little, shall we?
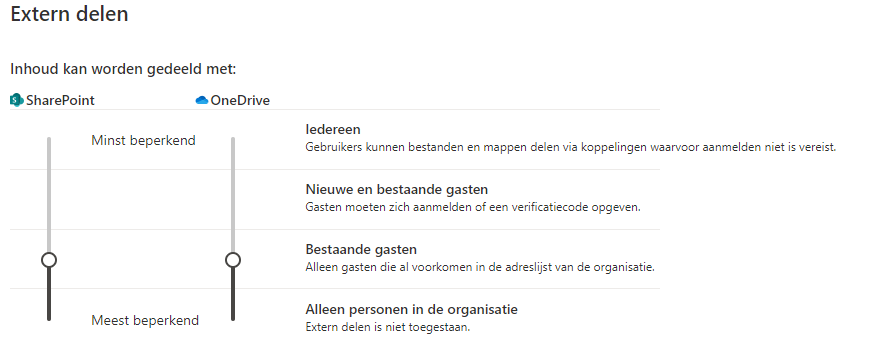
So, you got your barriers all set up! What now? Setting up your monitoring is the next step you have to take.
3. Monitoring Access to Office 365
3.1 Activity Alerts
The first option you have is setting up some protection/activity alerts for basic monitoring. Beware… it could take up to 15 minutes before an alert is generated.
First some background information before creating a new policy. You got 3 types of links you can create to begin monitoring shared file or folder events.
- Anonymouslinkcreated: An anonymous link (also called an “Anyone” link) is created for a resource.
- SecureLinkCreated: A user has created a “specific people link” to share a resource with a specific person. This target user may be someone who’s external to your organization
- CompanylinkCreated: User created a company-wide link to a resource. company-wide links can only be used by members in your organization. They can’t be used by guests.
So, the best option you have to create an alert when a file or folder is shared with an external user will be: “Securelinkcreated“. Now open https://protection.office.com/managealerts
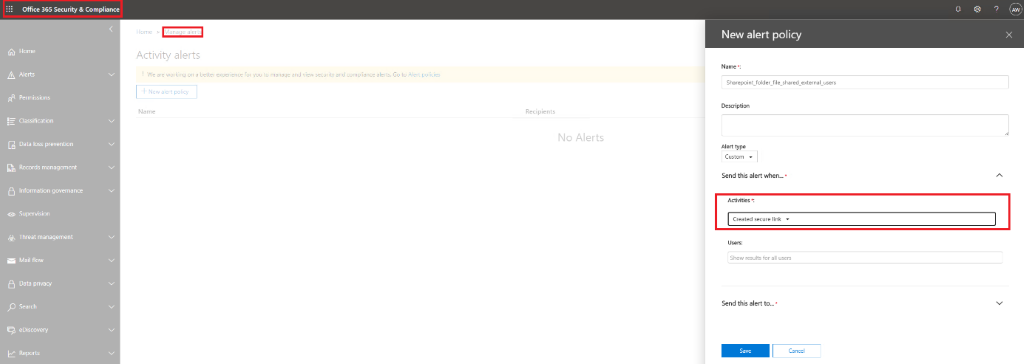
Please beware this is not the same as: https://protection.office.com/alertpolicies. Securelinkcreated is not available within these alert policies!
After creating your policy, go share a folder with an external user! You’ll see the alert will generate and look something like this:
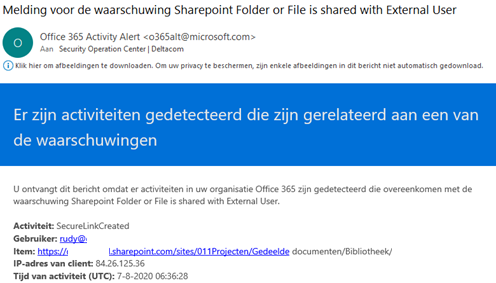
Of course, you can setup your Activity Alerts with PowerShell. Make sure you create a connection with PowerShell to the compliance center:
$fileandpagepolicyparams = @{
“Name” = “Sharepoint Folder or File is shared with External User”;
“operation” = “securelinkcreated”;
“notifyuser” = "soc@company.com";
“Description” = “Folder or File in Sharepoint Shared with External User.”;
“Severity” = “High”;
}
$result=New-ActivityAlert @fileandpagepolicyparams 3.2 MCAS / Microsoft Defender for Cloud Apps
The second option, and probably the best, is Microsoft Defender for Cloud Apps (previous MCAS). You’ll need to have proper licensing to fully use all of its functionality. With MCAS you got way more settings you can configure to get notifications. Let’s begin with a new policy with almost the same settings as the activity alert created earlier. Please beware it can take some time before you’ll receive an alert when a sharing event occurs.
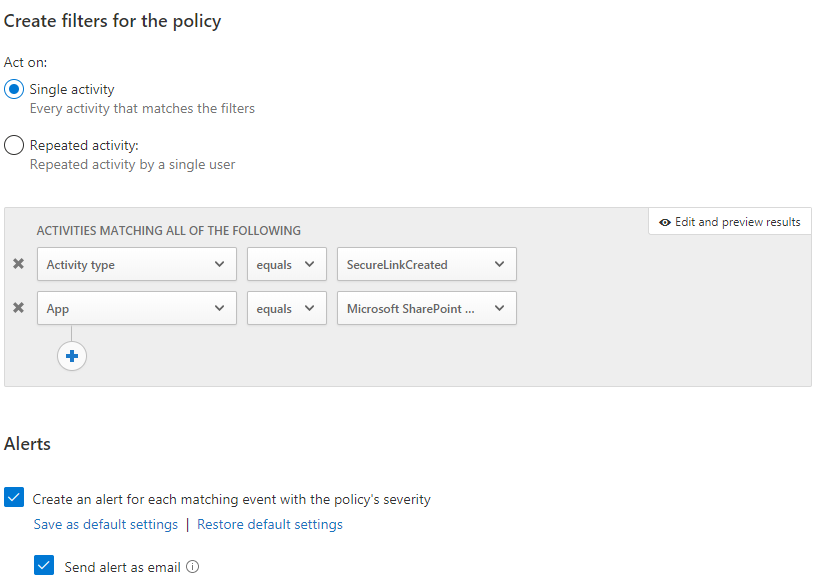
gain, go and share a folder with an external user! You will receive an email like this
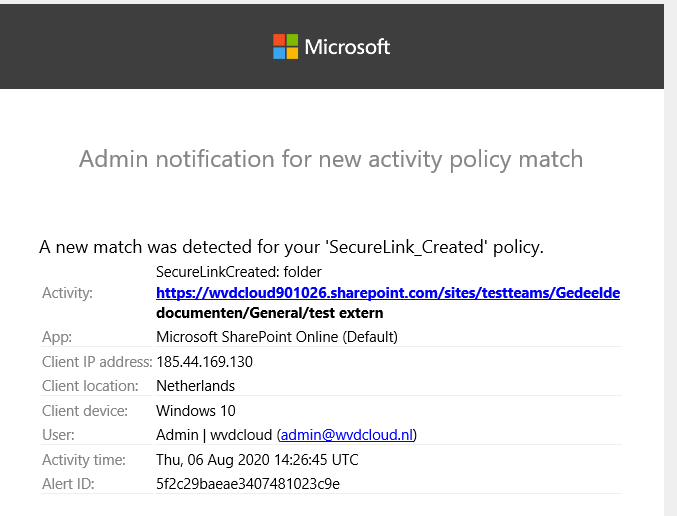
Like I mentioned before you can configure way more policies in Microsoft Defender for Cloud Apps. Go create a new file policy to get an alert when the access level equals external and the file type equals folder. You can do this manually or add this policy to your PowerShell MCAS baseline.
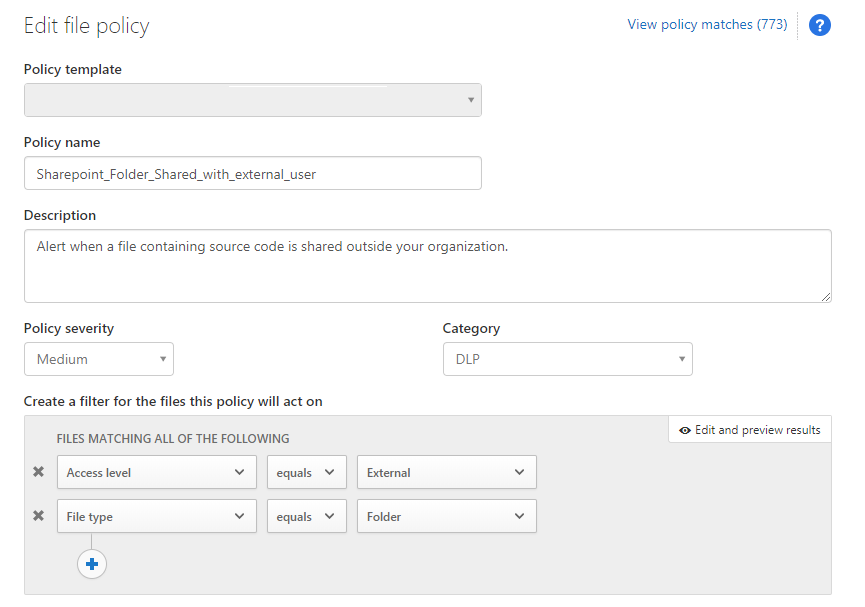
Looking at this policy, you can also set the parent folder to limit the matches.
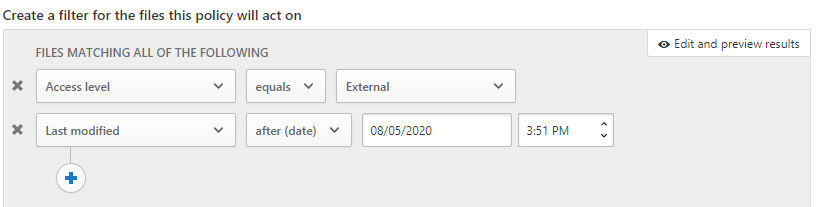
Also look at the policy template to setup monitoring and governance actions for stale files shared externally. You can define governance actions to remove the external users.
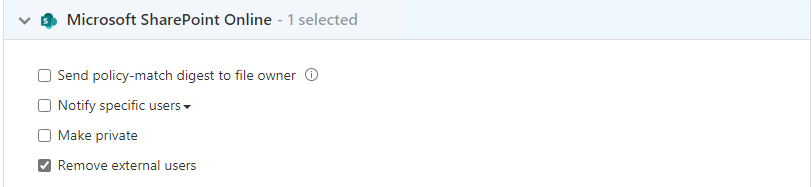
Conclusion:
Only relying on your security barriers is not the best practice. Starting tomorrow, you’ll each get to go outside and set up your monitoring in a way that you’ll be notified whenever something happens. Be sure to set up both notification options because MCAS alerting sometimes breaks: