Welcome to our Windows Enrollment Attestation series overview. This feature is also known as MDM Hardening and MDM Device Attestation. In this blog, I will explain everything you need to know about this new security feature! This series will have five to seven posts, each containing a Rudy Deep Dive!
1. Windows Enrollment Attestation
With the official release of Windows Enrollment Attestation, it’s time to explore the wonders of the Device Attestation Status reports.
This blog is the primary resource for my Windows Enrollment Attestation / MDM Hardening blogs. It will redirect to individual blogs focused on each step of the MDM/Windows Hardening process.
Let me briefly overview how Windows Enrollment Attestation functions, from the device’s initial boot to its successful enrollment into Intune.
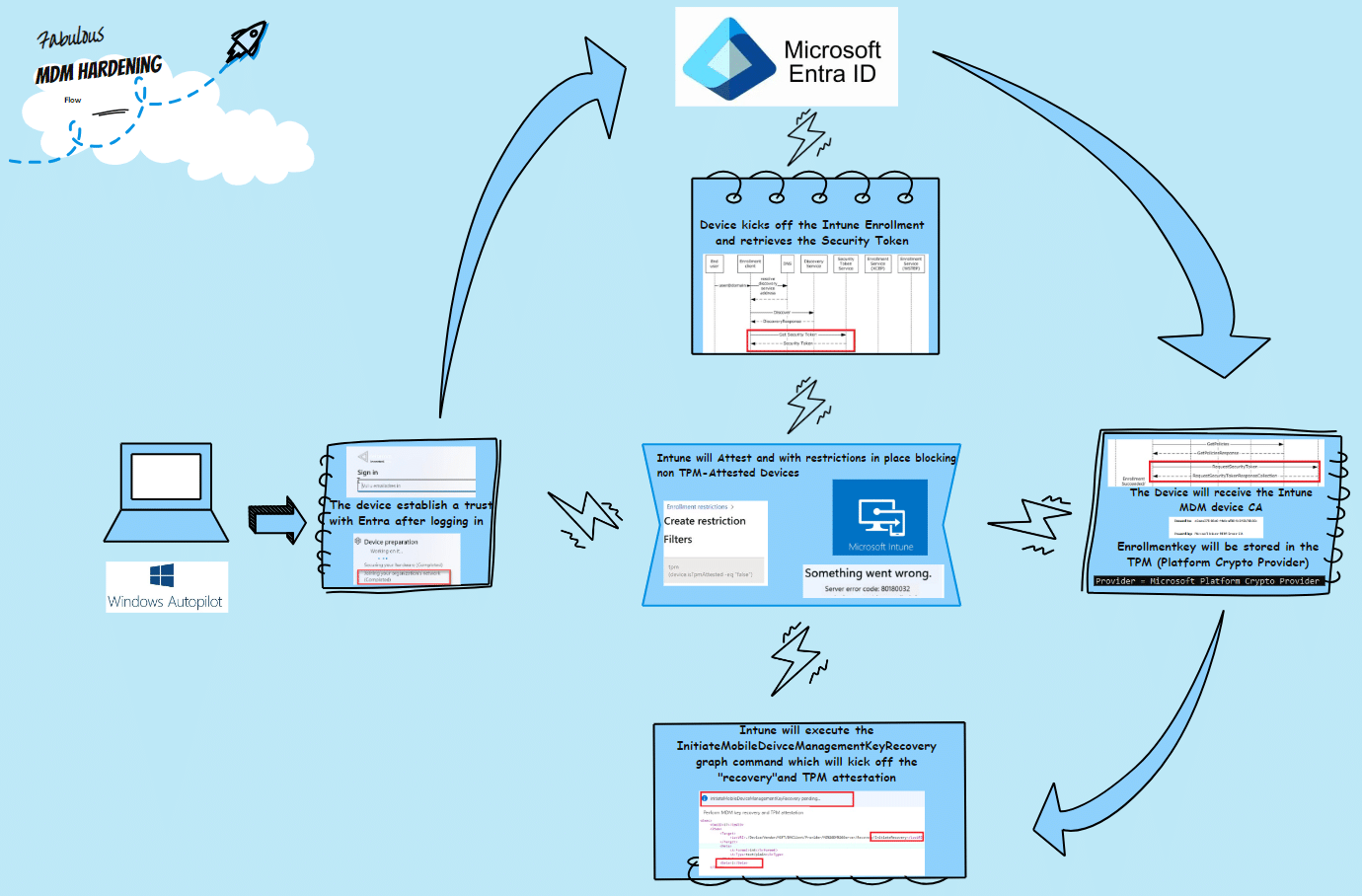
When we are enrolling our device with Windows Autopilot, the device we would be asked to enter our username and password.
- The device would start enrolling into Entra (joining organization)
- The device would start the Intune enrollment and start asking for the security token (Authentication)
- After receiving the Security token, the device *should eventually retrieve the Intune Device Certificate
- The Enrollment Keys of the Certificate will be stored in the TPM (UseTPMForEnrollment Key)
- With the Keys stored in the TPM, Intune could initiate the attestation by sending out a graph call to InitiateMobileDeviceManagementKeyRecovery
- The InitiateMobileDeviceManagementKeyRecovery graph call would kick off the MDM Key Recovery (RecoveryCSP) and TPM attestation.
- We can place a filter to ensure that the device needs to perform a successful MDM attestation. If the device cannot perform attestation, it will be *blocked and will NOT receive the Intune Device Certificate.
2. The Fallout Explanation of Windows Enrollment Attestation
In the first part of this blog, you can read the official explanation of what is happening under the hood of Windows Enrollment Attestation. I decided to do the same, but this time, in Fallout style and my unique way.
As dwellers of our digital shelter, we stand amidst the remnants of a post-nuclear era, piecing together the fragments of knowledge to safeguard our sanctuary from the chaos beyond. Imagine a group of brave survivors gathered around a flickering terminal, their eyes gleaming with determination as they unravel the secrets of Windows Enrollment Attestation, AKA MDM Hardening.
The first step beckons in the heart of our shelter: “usetpmforenrollmentkey.” This function, akin to fortifying our gates against marauders, ensures that the Intune MDM device certificate takes refuge within the secure confines of the TPM, shielding it from the hazards of the Software KSP lurking in the wasteland.
But our journey does not end there, fellow inhabitants. The discovery of the Recovery CSP is a beacon of hope amidst the digital rubble. With its power, we can mend the fractured bonds of the Intune certificate’s fate, ensuring our resilience in the face of unforeseen adversities.
As our knowledge deepens, we uncover a hidden arsenal within the Microsoft Graph: “initiatemobiledevicemanagementkeyrecovery.” This elusive Graph URL, powered by the enigmatic AllowRecovery CSP, breathes life into our defenses, enabling us to trigger the Windows Enrollment Attestation process from afar, like sending a signal beacon across the wasteland.
With these vital components in hand, our group of survivors engineers the final piece of our defensive puzzle. Behold the enrollment filter, a digital barrier that separates friend from foe. Only those devices that have undergone the rigorous Windows Enrollment Attestation ritual gain entry, while the rest are barred like intruders attempting to breach our shelter’s perimeter.
Thus, the cycle completes, and the digital frontier stands fortified against the encroaching shadows, much like a vault sealed against the dangers of a post-nuclear world.
End of story…..
3. The 4 Windows Enrollment Attestation Steps
If you read the incredible story above, it will become evident that I will tell four separate stories, all of which correspond to the MDM attestation/hardening.
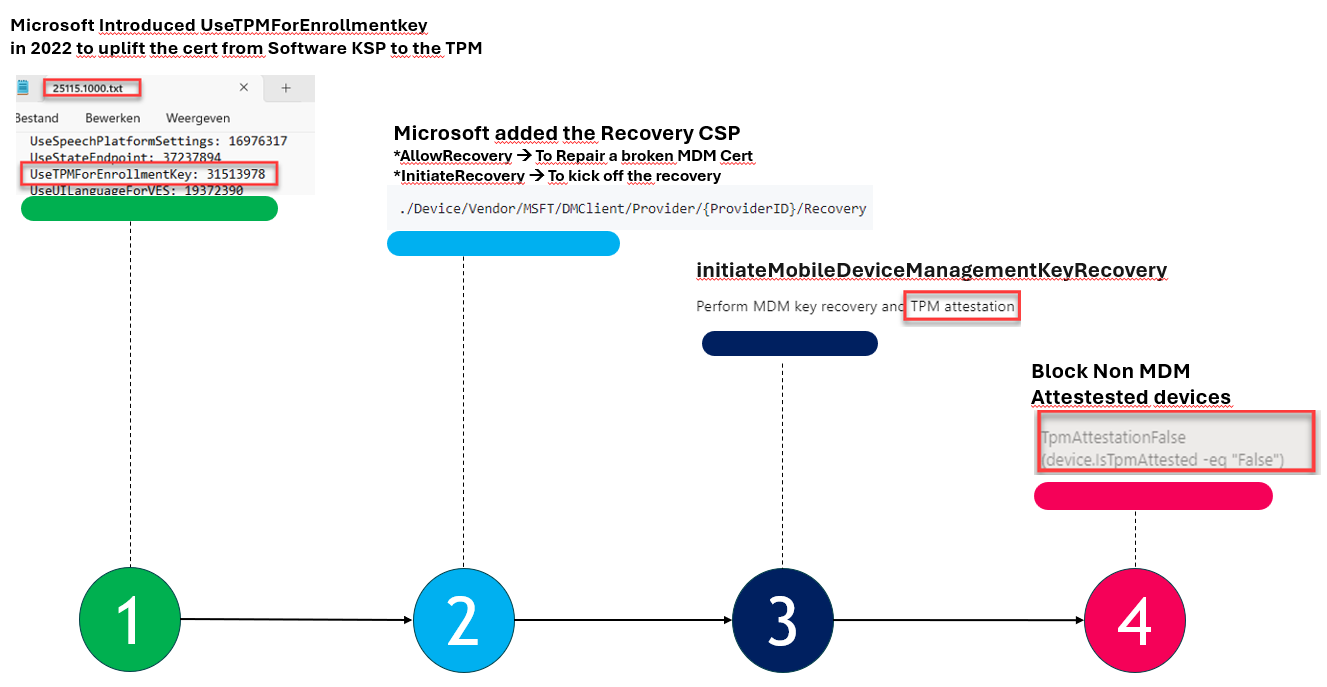
- UseTPMForEnrollmentkey (introduced in 2022) to uplift the Intune MDM Cert to the TPM
- Tada!!! At the same time, the Recovery CSP came to life. This CSP could repair (uplift) the Intune Certificate when needed and has a CSP to trigger the recovery.
- To initiate this CSP from Intune, we need Microsoft Graph. Microsoft introduced the Initiatemobiledevicekeyrecovery graph. This graph, will perform the MDM recovery (initiaterecovery) and MDM TPM attestation.
- With all this power, Microsoft now could give us a filter to block all devices that didn’t perform MDM / TPM attestation (device.istpmattestated – eq “false”)
4. The Links
Here are the links to each blog corresponding to each step in the Windows Enrollment Attestation process. Each of these blogs will be a deep dive … so prepare yourself!



Hi, is there a way to attestate the devices trough graph? I found this link https://learn.microsoft.com/en-us/graph/api/intune-devices-manageddevice-initiatedeviceattestation?view=graph-rest-beta but it seems it doesnt work since I dont receive any output.
Used this command:
Invoke-MgGraphRequest -Uri “https://graph.microsoft.com/beta/deviceManagement/managedDevices(XXXXXXXXXXXXXXXXXXXXXX’)/initiateDeviceAttestation” -Method POST
Thank you!