Everything is about Zero trust security; you will need to implement it. Many articles have been written about zero-trust security in the last few months. Some examples:
Zero Trust Security (microsoft.com)
Take the Zero Trust Assessment (microsoft.com)
How do you best explain zero trust?
It’s like Ronald Reagan’s quote, but with one additional word: Never trust, but verify.
Zero trust ensures that identities are verified and devices are safe before you can access your corporate apps and data.
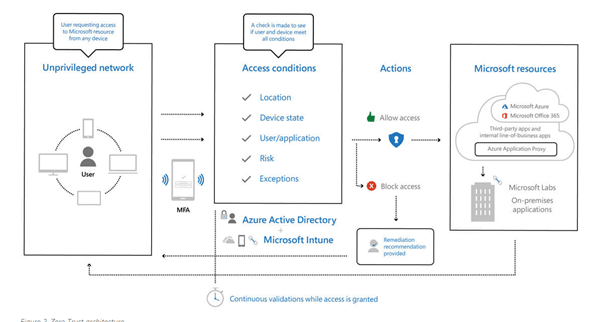
*Source Microsoft
There is a lot of information available showing you the big picture and which steps you need to take. But in my opinion, some details could be just a little bit better. Of course, the Microsoft assessment tool will show you some steps to take.
This short blog (but with a big pdf in Github) will show you how to transform from nothing to a zero-trust modern organization. This flow also lists which of the ISO 27001 controls you can cross when you have implemented that section.
I hope these steps will help you with your work and making sure you are not forgetting anything.
rudyooms84/Migration-path-to-a-zero-modern-trust-workplace (github.com)
Please contact me if I missed something. I will try to update the flow as much as possible.

