SIEM (security information and event management) is a set of tools used to monitor, identify, analyze and record security events.
Of course, you could use Azure log analytics and Azure Sentinel as your SIEM. But for small businesses (SMB) I’d recommend starting with Solarwinds as your Microsoft 365 SIEM moving forward!
But who’s checking all these security events? That’s why you probably need a SOC (Security operation center). SMB don’t necessarily need to set up a full-blown SOC. So why not upgrade your Solarwinds Dashboard into a small SOC? For example, you can configure email notifications for all checks and forward them to your incident management software (also included in Solarwinds).
In my last blog, I showed you some checks you could add to your monitoring templates.
Go ahead and add some countermeasures on these checks! You can configure additional tasks for when a check fails.
Windows Defender

Next step is to create a nice task, which fires off a script to update Windows Defender and run a quick scan. Of course, you could add more automation to it. (like running an offline scan)
$date = Get-MpComputerStatus | select *age
$updateage = $date.antivirussignatureage
$datescanned = $date.quickscanage
If ($updateage -gt 1) {
Update-MpSignature
} Else {
'Defender is up to date'
}
start-mpscan -scantype fullscan -scanpath "c:"
A new Local admin detected
You have to remove all additional local admins from your Windows 10 devices. Go check out this blog to learn more about this subject.
But monitoring is key! You need to monitor these events.
Try {
$admin = net localgroup administrators | select -skip 6 | ? {$_ -and $_ -notmatch 'Task completed.|^administrator$|^admin$'}
If ($admin -eq $null)
{
Write-Output "No additional local admins found"
exit 0
}
Else
{
Write-Output "BEWARE!!! another local admin has been created: $admin"
Exit 1001
}
}
catch
{
#Write-Warning "Value Missing"
Exit 1001
}
Like the countermeasures I implemented with Windows Defender, you can do the same with this check. Go and add an assigned task to it.
$remove = net localgroup administrators | select -skip 6 | ? {$_ -and $_ -notmatch 'De opdracht is voltooid.|^administrator$|^admin$'}
#remove the accounts
foreach ($user in $remove) {
net localgroup administrators "`"$user`"" /delete
}
Applocker
No local admins is the first step in a secure environment, securing your Windows 10 devices with Applocker is the second step. Go read this blog to learn how to implement it.
Again…monitoring is key. You want to monitor when Applocker blocks an app execution. Here is an example you can use.
Try {
$Result = get-winevent -FilterHashTable @{LogName="Microsoft-Windows-AppLocker/EXE and DLL";StartTime=(get-date).Addseconds(-360)}|Where-Object{($_.id -eq 8004) -and ($_.message -notlike "*GPSCRIPT.EXE*") } | ft message
$ID = $Result | measure-Object
If ($ID.Count -lt 5)
{
Write-Output "No Applocker events found"
Exit 0
}
Else
{
Write-Output $result
Exit 1001
}
}
catch
{
Write-Warning "Value Missing"
Exit 1001
}
WIP
Windows information protection is one of the Microsoft tools for protecting information on your Windows 10 devices. I am not (yet) a big fan of WIP (I will tell you why in one of my next blogs). But when using it, you can also monitor these events just like I did with Applocker.
Sysmon
I am not going to tell you why I think you need it. But if you want to have more insight into what’s going on, start using it. Download Sysmon and create a new Intunewin app (don’t forget to increase the Sysmon event log).
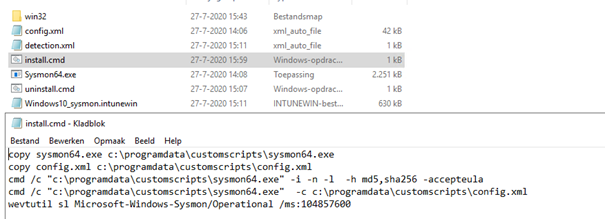
And yet again… monitoring! Create some event checks and look out for these suspicious logs.
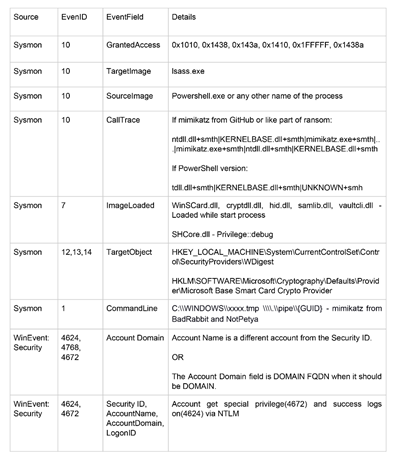
Conclusion:
Setting up a SIEM is very important for monitoring your devices. With the proper licenses, you can use Azure Sentinel and log analytics. Microsoft announced a collaboration with Solarwinds, so why not use Solarwinds, to begin with? You can create a lot of checks and countermeasures to protect your devices. Because… I need you to monitor your devices, sir.

