Obviously, mobile devices are needed to access company data, and these devices and apps need to be secured. Many articles have been written about when to use MDM and when to use MAM or combine them. This blog will be about troubleshooting App protection policies.
This week we were enrolling new surfaces and mobile devices into Microsoft 365. It can be a struggle when you don’t have a greenfield tenant and need to ensure the existing tenant gets a structured design. Migrating large organizations can take some time. you really don’t want to transform an organization to Microsoft 365 by night.
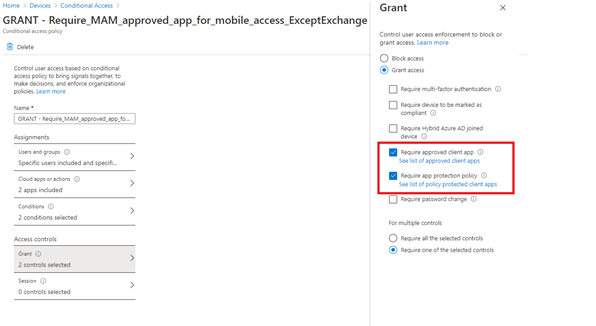
1. Conditional Access and an Approved App policy
We made sure group licensing was being applied. When a user is a member of this license group, they can enroll their devices into Microsoft 365, app protection will be applied, and conditional access will be applied to the same group. With a conditional access rule, you can require approved apps and app protection policies.
2. Enrolling the devices
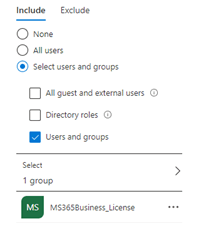
This week, we began to enroll the first batch of employees with their surfaces and mobile devices. To make sure they can still access their Teams Desktop app and their email on their iPhones before their devices are enrolled, we have created some conditional access exclusions groups. So, after their devices are successfully enrolled, we can remove the users from the exclusion groups.
So we did. The first batch of devices was enrolled and we removed them from the exclusion groups. No problems at all, all devices were compliant!… that’s what we thought.
3. The issue after the enrollment
In the evening, we received a new ticket with a screenshot (Sorry.. it’s in Dutch: Access Denied, the app needs to be protected). One of the users could not access OneDrive on their mobile devices.
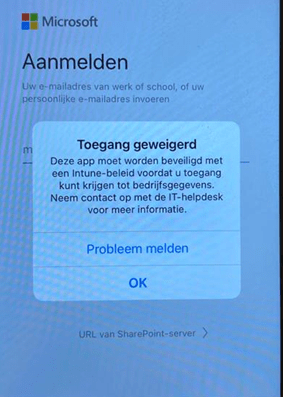
That’s odd? as they were all compliant. Let’s dig in
4. Troubleshooting App Protection Policies in Intune
So let’s start troubleshooting. These are the steps we took to troubleshoot this problem:
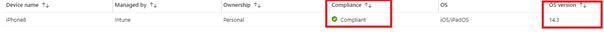
Step 1: Compliance State: Of course, the first thing we did was check if the mobile device is compliant and which IOS version is installed. As shown below, the device is compliant and up to date.
Step 2: Now that we know the device is compliant, we need to check the Azure Ad sign-in log to look for problems. Again, there were no failures.
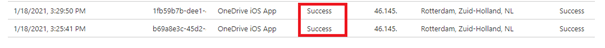
Step 3: The device is compliant and has no CA failures. The next thing we need to check is the App protection policy. We need to make sure nothing is wrong with the policy and confirm if OneDrive is targeted and assigned to the proper group.
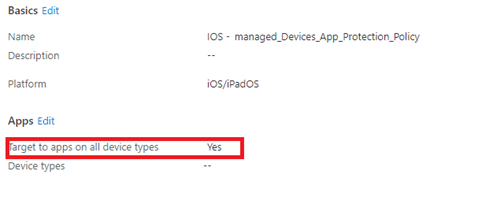
Step 4: Now it’s time to check the app protection logs as the error really looks like a problem with App Protection. We downloaded the App protection Report: IOS, Android.

After reviewing the report, the problem user was not in this report. That makes sense, as the app Onedrive is not protected with an app protection policy. What to check next?
Step 5: We selected the user status for the IOS report in the same app protection status monitor. Hopefully, it tells us a little bit more. And yes, it does

A nice error popped up: Not checked in. On the next sync, this app will receive one or more policies… That’s a little bit weird because the iPhone was enrolled in the afternoon and the company portal app was showing no errors.
Step 6: To be sure we asked if the company app was still installed and if it was showing errors. But no errors were shown. Of course, on IOS devices the company app is not required to implement App protection policies in contrast to Android.
We made certain the device was rebooted, but that did not resolve the problem. Now we know what the problem is, how are we going to solve it.?
5. Troubleshooting App Protection on the Device
Instead of using Intune you could also get your hands on a Device to start troubleshooting. When you are at the customer and you want to determine which App Protection policies were applied on the device itself, you could do so by opening edge and type: about:intunehelp. It will give you a brief summary of all the Protection Policies applied to a specific app!
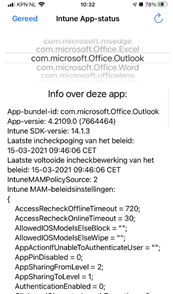
6. Solving the problem
Step 1: Let’s start with initiating a device sync from the Intune portal. Hopefully, it works.
But unfortunately, that didn’t do anything and the OneDrive app was still not working
Step 2: Even checking the status within the company app portal on the device didn’t change anything.
Step 3: let’s check what Microsoft tells us about App protection
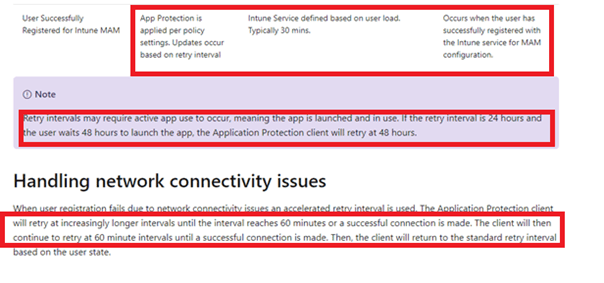
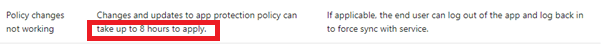
Typically 30 minutes…. I guess the word typically says it all: you must have patience…a lot of patience. But that’s not helping much when the customer is on the other side of the phone.
As mentioned at the beginning of this blog, you will need a structured design. We have created a group for each CA rule with the same name. Security is key, but we will add the user to the CA exclusion group for now so App protection is no longer required. The customer is satisfied and can resume his work.
Please beware that just excluding the user from the CA policy is not your final solution! You will need to monitor whether the App protection policy was applied the next day and remove the user from the exclusion group.

As shown above, the Microsoft OneDrive app on his device has finally received the app protection policy! Now we can be sure we can remove the user from the exclusion group.
Conclusion:
This is the way. App protection is great for protecting the data within apps on managed and unmanaged devices, but sometimes it can take a really long time before app protection policies are applied. In the meantime, you can exclude the users from the conditional access rule.
But please remember to remove the user when the issue is resolved! You really don’t want to be “bombed” by your employee when the user decides to copy all of the company data to his personal files before joining the competition!



Great summary! I have also seen this so therefore lately I’ve been applying the App Protection Policies first and then apply the CA policy much later, usually ”weeks” to be sure all phones got their app protection policies applied already…