Last Updated on February 7, 2023 by rudyooms
This blog will be about some proactive remediations and Intune Role Assignments to make sure your service desk can help your users when they need to enter the Bitlocker recovery key and nothing more.
Even while Microsoft has some custom roles available you could still use the Awesome Proactive Remediations because you could also use Proactive remediations to determine if your devices are still having the XtsAes128 instead of the XtsAes256 Encryption
I will divide this blog into multiple parts:
- Configuring the Pro-Active Remediations
- Configuring the Intune mgt Role
- Results
- Encryption Method report
1. Configuring Pro-Active remediations:
First, download the Powershell scripts. The zip contains the Detection and Remediation scripts.
https://call4cloud.nl/wp-content/uploads/2021/05/BitlockerRecoveryKey.zip
Now we have the scripts, let’s start by creating a new proactive remediation.
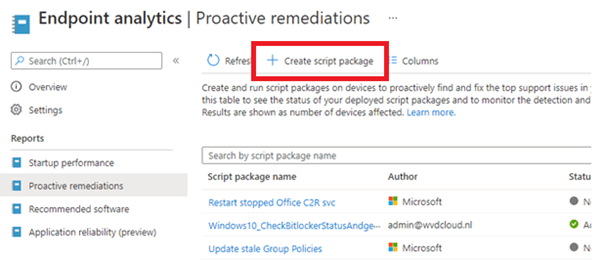
Make sure you select the detection and remediation script from the zip file you downloaded.
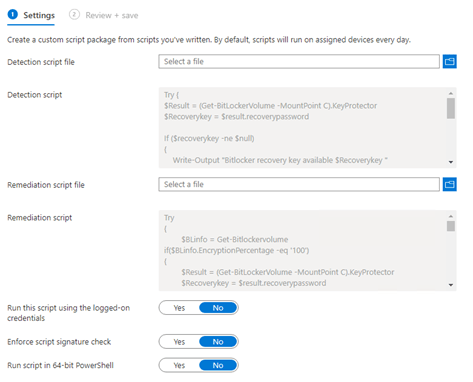
2.Configuring the Intune Mgt Role
So why do we need Role-based access control (RBAC)? RBAC helps you manage who has access to your organization’s resources and what they can do with those resources. By assigning roles to your Intune users, you can limit what they can see and change. Each role has a set of permissions that determine what users with that role can access and change within your organization.
After we know what we can do with RBAC we are going to create an additional Intune Role. But before we do, make sure you have already created a group with the service desk users in it, who need to have access to the BitLocker recovery key report.
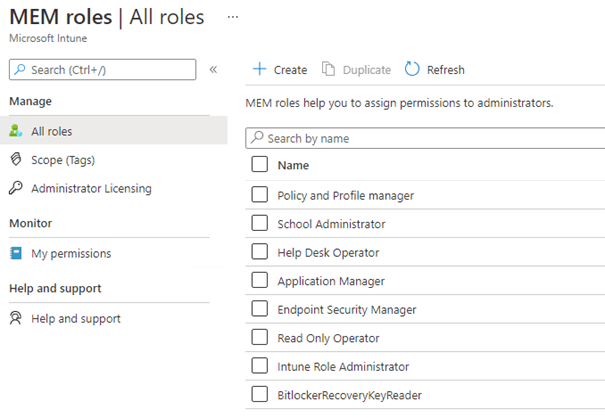
But which permissions are needed to make sure the user could access the Proactive remediations report? Let’s take a look at what Microsoft has to say.

These are the permissions needed:

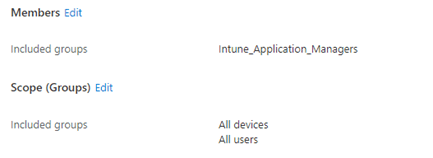
Don’t forget to assign this role to the service desk group you created earlier.
3. Testing it and the results
While testing this idea, I also solved the problem when for some reason Bitlocker failed to encrypt the device and it is tried multiple times. A good example would be if you haven’t removed your USB installation media after the installation.
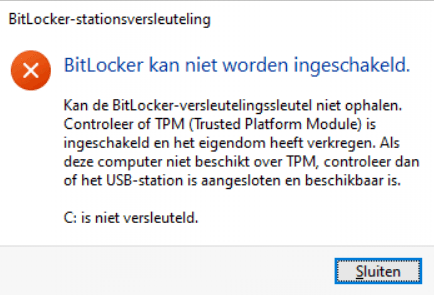
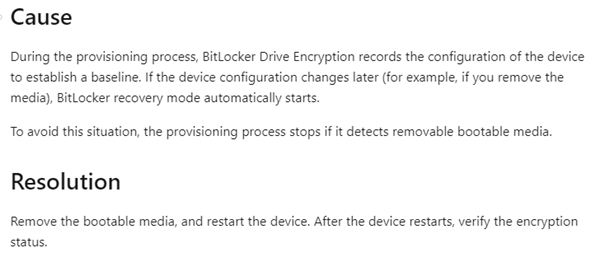
You can be sure the Proactive remediations will try to activate BitLocker each hour. So I didn’t remove the iso after the installation and rebooted a couple of times before I removed the removable media. After a while, the pro-active remediations also tried to kick in.
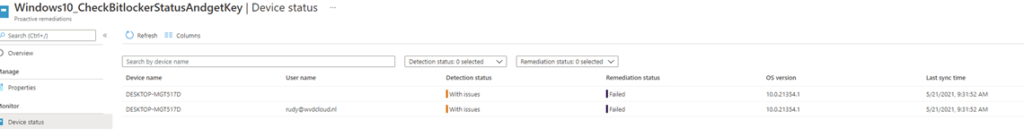
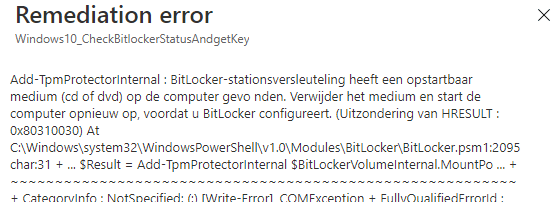
In English: It detected removable media you need to remove it and reboot the device. Now we need to wait an hour before the proactive remediations try to detect and remediate when necessary….

And after an hour, the detection script was executed. Let’s open the Microsoft Intune management log first before we continue.
Detection
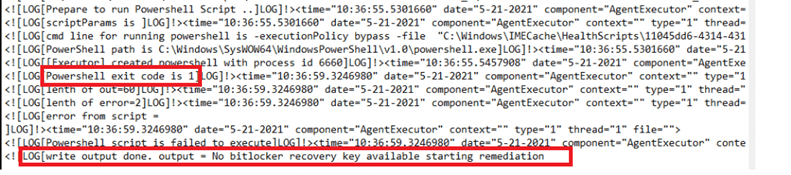
And of course, because the detection script was exited with the status code 1 it will start to remediate the problem.
Remediation:
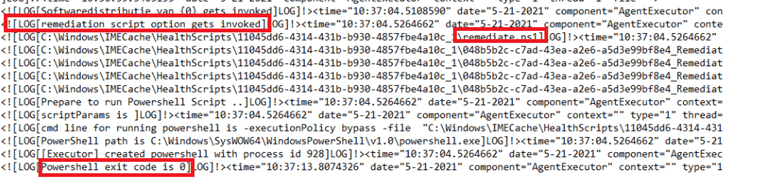
Now the problem was remediated successfully it started encrypting the device.
Results:
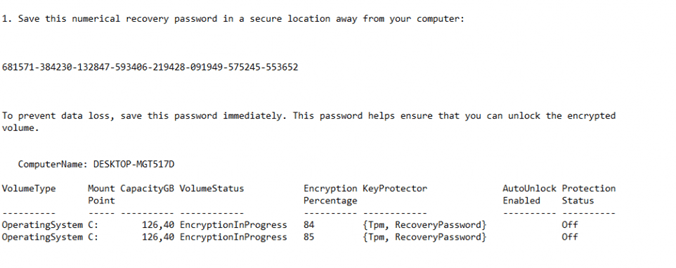
First, let’s check as a global admin if we can get some detection results. As also shown in my last blog, you will need to add some columns otherwise you will not see the results.
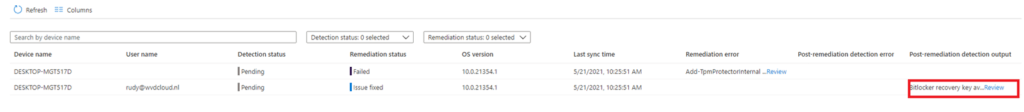
And yes… we can retrieve the BitLocker recovery key as admin!
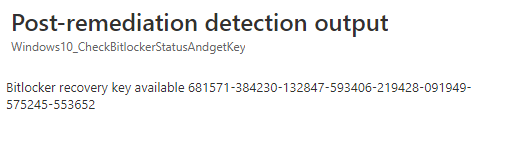
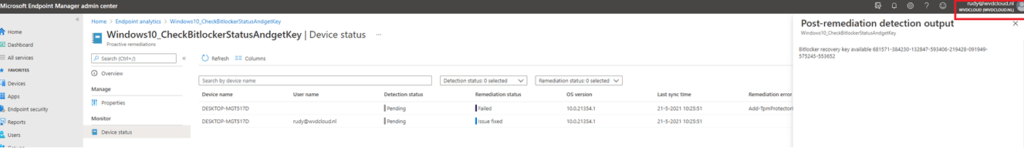
Now we are going to do the same test but this time as a normal user with the assigned Intune role we created earlier. As shown below… you can make sure the BitLocker recovery key can be extracted from Intune with RBAC configured.
4. Encryption Method report
As mentioned at the beginning of this blog, using proactive remediations to get the Bitlocker recovery key back is a cool idea (until Microsoft created their own solution) but still, you can still use it for other purposes.
One of the many examples would be to determine if your device was still encrypted with XtsAes128 instead of the XtsAes256 encryption method
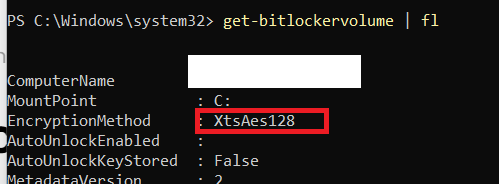
With just a simple proactive remediation (detection script only) you could find out if your devices need an update
$blinfo = Get-Bitlockervolume
if($BLinfo.VolumeStatus -eq 'FullyEncrypted' -and $BLinfo.EncryptionMethod -eq 'XtsAes128'){
Write-host "Encryption Method is 128bit. Not Good!!!!..."
exit 1
}
if($BLinfo.EncryptionPercentage -ne '100' -and $BLinfo.EncryptionPercentage -ne '0'){
Write-host "Encryption or decryption in progress."
exit 0
}
if($BLinfo.EncryptionPercentage -eq '0'){
Write-host "Encryption policy update needed."
exit 1
}
if($BLinfo.VolumeStatus -eq 'FullyEncrypted' -and $BLinfo.EncryptionMethod -eq 'XtsAes256'){
Write-host "Device ecryption is 256bit. All fine!!!"
exit 0
}With this info, you could also write a remediation script to simply Disable-BitLocker -MountPoint “C:” and re-enable it with the XtsAes256. Of course, you will also need to make sure you hav changed the Bitlocker Device configuration policy before
Conclusion:
As shown above… You can create a dedicated Intune role for your service desk to get back those BitLocker recovery keys when your users need them. Let’s get a drink and start using proactive remediations for everything



Hello,
Thanks for the article, I’m plaining to implement this solution to grant L1 support team access on the BitLocker keys, Just want to ask if any new solution you found for this request or should I follow this approach.
Many Thanks for your help.
Hi… I updated the blog as 31-03-2020 the long arrived rbac custom roles were released!
https://techcommunity.microsoft.com/t5/azure-active-directory-identity/azure-ad-rbac-custom-roles-amp-administrative-units-for-devices/ba-p/3185209?id=5004252
Sorry, I am really bad at understanding scripting. The last bit of your tips is exactly the info I need to use as all of our devices are 128-bit encrypted and need to be 256-bit encrypted. Please could you detail what I have to write as a detection script and what to write as a remediation script to detect that devices are 128-bit encrypted and switch off Bitlocker if they are?
Our 256-bit policy appears to encrypt the drive as 256-bit if it detects it as disabled – we tested it by manually decrypting a 128-bit drive and then a few hours later checked the status using manage-bde -status and it was 256-bit encrypted.