This blog is the second part of the Endpoint Security series.
This part will be about enabling and configuring Microsoft/Windows Defender controlled folder access (CFA) in Intune.
I guess this feature can be useful when you haven’t implemented Applocker. I decided to create this blog after a question on the Discord WinAdmin/Intune channel about how to exclude the OneDrive process.
1.Introduction
Of course, you will need to make sure you have already enabled Microsoft Defender Antivirus real-time protection. If not? Please do…
Controlled folder access works with a list of trusted apps. Apps that are included in the list of trusted software work as expected. Apps that are not included in the list are prevented from making any changes to files inside protected folders.
Controlled folder access is especially useful when you want to protect the companies documents and information from a ransomware attack. When you are a victim of a ransomware attack, your files could end up being encrypted. When you make sure controlled folder access is enabled and configured, a notification will appear on the Windows 10 device where the untrusted app is attempting to make some changes to your documents, which are in a protected folder.
When you want some more security, please take a look at Applocker.
2. Logging
When implementing Controlled Folder access, please make sure you configure it to Audit the events instead of blocking. Also please test it out on some test devices first before turning it on.
You will need to beware of the events which can be triggered when some application is prevented write access to the protected folder.
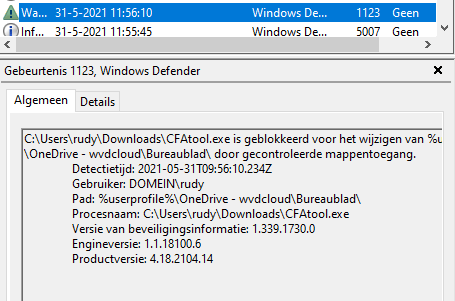
- 5007 – Event when settings are changed
- 1124 – Audit controlled folder access event
- 1123 – Blocked controlled folder access event
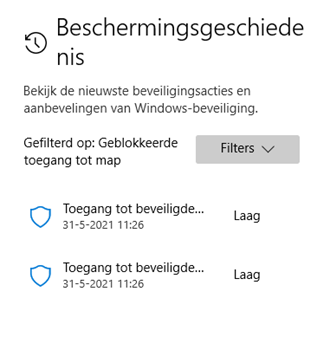
When some process is blocked, it will also end up in the Microsoft Defender protection history.
3. Enabling controlled folders
When using Intune, it’s very easy to enable this feature. You could create a new Settings catalog and just search for the term: Enable Controlled Folder Access (defender)
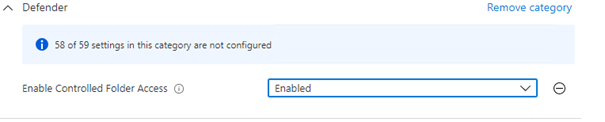
Like I told you earlier, please configure it to Audit first!
When you prefer to use the settings catalog you can also enable it by setting the enablecontrolledfolderaccess parameter
Set-MpPreference -EnableControlledFolderAccess Enabled
When the controlled folder access is active you will notice the possibility to manually turn it on or off is greyed out.
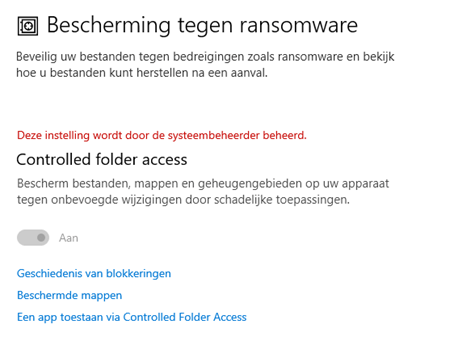
4. Allowing Applications
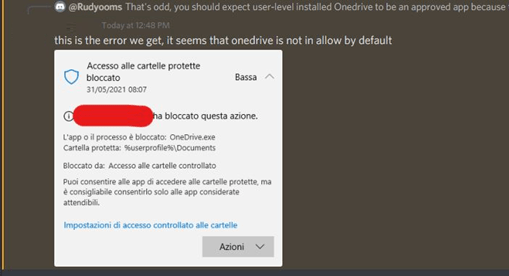
And that’s where the discord question comes into play. Onedrive.exe was installed with the user-based installation instead of a machine-wide installer. With the user-based installation, the Onedrive exe file will end up in the user’s profile, and apparently, it will be blocked. When I tested it with onedrive installed with the machine-wide installer, it didn’t have any issues accessing the protected folders.
But how are we going to allow this application? We could try to add a “*” to define a wildcard as username because it’s a tenant wide setting so on each device you have got a different username:
c:\users\*\appdata\local\microsoft\onedrive\onedrive.exe.
Please take a look at what Microsoft has to say about this:
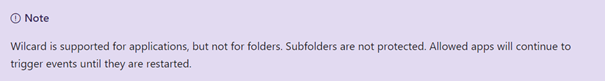
So how else could we make sure, Onedrive is allowed to access the Onedrive folders? Luckily you are allowed to use system variables like %userprofile%. The only thing you will need to do is change the c:\users\* to %userprofile%
Just like with the option to enable the controlled folder access feature, you could use the settings catalog to allow some additional trusted applications.
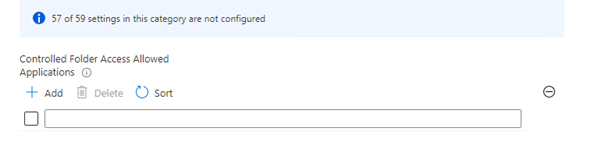
Or by using PowerShell:
Add-MpPreference -ControlledFolderAccessAllowedApplications “%userprofile%\ appdata\local\microsoft\onedrive\onedrive.exe “
5. Adding Protected Folders
You will need to beware, some folders are protected by default. You don’t have to configure anything to make sure your files are safe in these folders:

But looking at Microsoft their documentation, I could not find anything about the OneDrive folders. Are they protected by default or not?
It’s very easy to check it out for yourself, just activate it on a test device and you will notice “some” Onedrive folders are protected by default
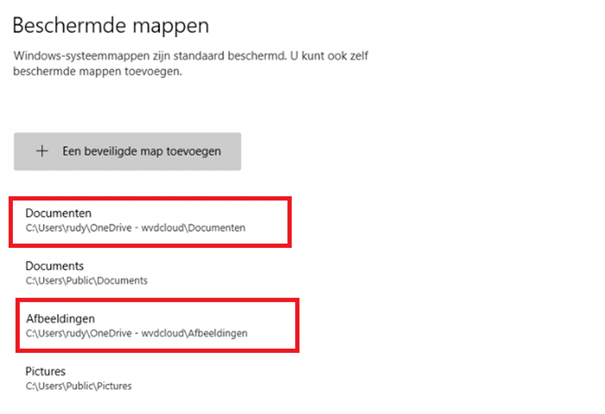
Again… when you are in need to protect some additional folders, you can add them with the settings catalog.

Or…. Again with PowerShell
Add-MpPreference -ControlledFolderAccessProtectedFolders “Full path of folder“
6. Testing it
Just believing in the fact you are all safe and totally protected is not the best practice. You will need to do some tests before you can tell for sure you are in a safe harbor and protected against ransomware attacks.
Go open the Microsoft defender test ground webpage
Home – Microsoft Defender Testground
And download the CFA test tool!
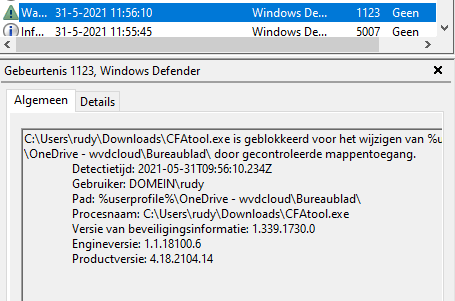
The first test I took was writing a file to the desktop
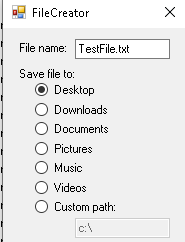
And it succeeded? I thought it was strange at first, but after a few seconds, I realized the desktop folder is not a protected folder. Just take a look at the picture I showed you earlier.
Writing a file to the desktop is allowed because it’s missing in the protected folders!
So we need to add the desktop but like I was telling earlier, you can’t specify wildcards, luckily you could still use some system variables like %userprofile%.
Add-MpPreference -ControlledFolderAccessProtectedFolders “%userprofile%\OneDrive – wvdcloud\Bureaublad\”
But writing a file to the Documents folder is protected! Please take a look at the event logs which I mentioned earlier
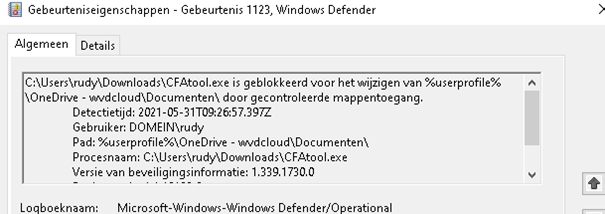
7. Results and registry locations
Controlled Folder Access must be a part of your defense-in-depth security strategy but Controlled Folder Access can’t protect you against ransomware in all situations. You will need to make sure you implement adminless and Applocker because when a hacker succeeds in getting elevated privileges on a system, the hacker could easily disable Controlled Folder Access. But on systems that are properly secured, Controlled Folder Access provides an additional layer to your defense strategy protection against ransomware.
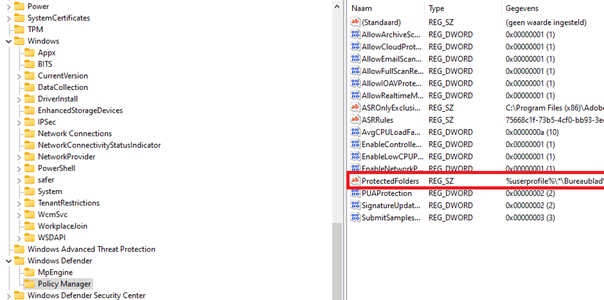
To finish this blog please take a look at the registry locations where the policies are stored
HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows Defender\Policy Manager
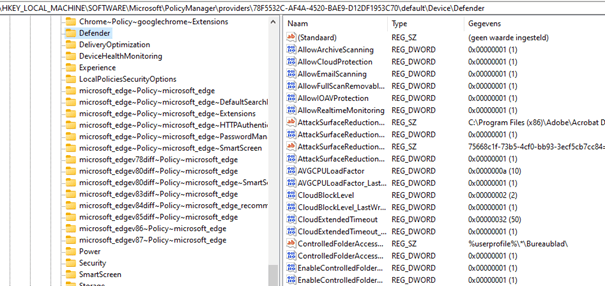
And the Policymanager Intune registry value:
8.But What About Checkdisk?
I received some feedback on Linkedin about the fact running Controlled Folder access could interfere with running Checkdisk.
As controlled folder access would make sure some files can’t be changed by malicious processes, it could break check disk?. I needed to test if that was true.
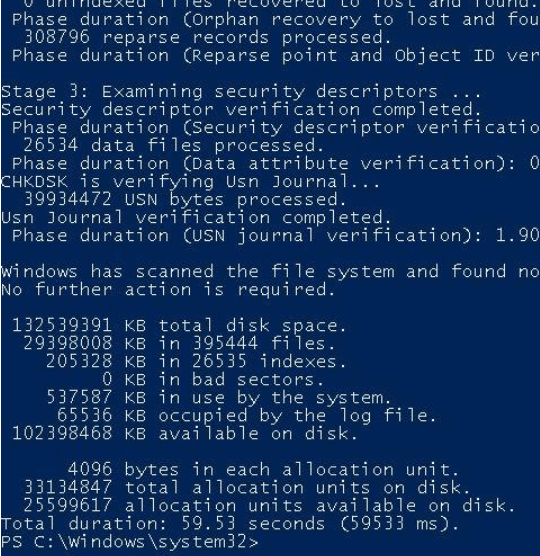
I made sure I launched a full check disk

As shown above, I needed to reboot my device (tested it multiple times on a virtual and physical machine)

Both of them succeeded in scanning the whole drive because it scanned the hard drive before the OS is booted.
Also running a quick check disk is not an issue inside Windows itself. Of course, when there are files/parts of your hard drive damaged inside the protected folders you could run into some issues… but if that occurs maybe just changing your hard drive would be a better solution?
Conclusion:
As told in the results part, CFA is a part of your defense strategy. Only relying on CFA is totally not the best practice. Please take a look at my other blogs about hardening and securing your Office/Endpoints/Edge browser.
Thumbs up if you have all those security barriers in place. “how proud can a father be?

If you want to read more parts of the Endpoint Security Series:
*The first part about Application Guard (click here)
*The third part about Attack Surface Reduction Rules (click here)

