This blog will be about the Managed and Unmanaged App Protection Policies and how you can ensure that they work properly on iOS devices.
1. Introduction
When we want to protect the company data, we have multiple options.
Are you going to require compliant mobile IOS/Android devices, so each device needs to be enrolled (MDM)? Or do you have a lot of front-line workers and you only want the apps to be secured with an App Protection policy (MAM)? Or maybe a combination?
In this example, we did both. We wanted to ensure users with a Microsoft 365 Business Premium license needed to have their mobile devices managed/enrolled and all the other users could access Office365 without their devices needing to be enrolled. Of course, we will need to apply App Protection for each option.
You have to choose which of the options is the best to protect the company data. Managed devices need to get the Managed devices App Protection policy and the unmanaged devices need to get their unmanaged devices App Protection Policy.
I need to mention the fact that we do loosen the screws a bit on the Managed App Protection policies because we do have more power over that device!
2. Conditional Access Rule
So, let’s begin by locking down the environment with some Firewall Conditional Access rules. Assuming you already have blocked legacy authentication, we will create 2 additional conditional access rules.
*The first CA rule will require ms365Business licensed users to have IOS/Android compliant devices.
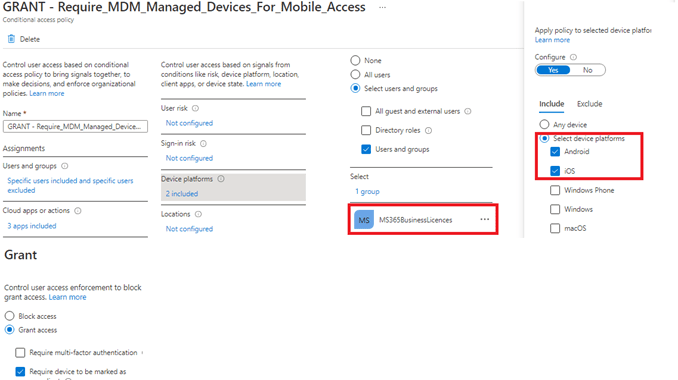
*And a second CA rule to make sure approved apps are required when you want to access the Office365 data.
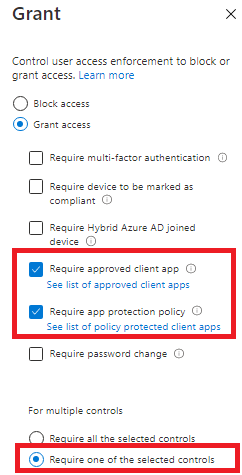
UPDATE: Please read my blog about the require app protection misunderstanding:3. App Protection Policies
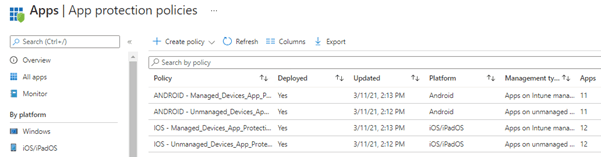
After the CA rules were created, we needed to create the App protection policies. As shown below we created multiple App protection policies. One App protection policy for Managed devices and one for unmanaged devices
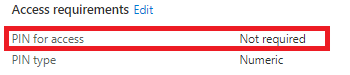
In my opinion, managed devices don’t need an additional password to open the app because you probably already made sure you have set up a compliance policy and a device configuration policy. As mentioned before, maybe you want to loosen the screws a bit on managed devices?
Another good example would be letting managed devices “send org data to other apps” but blocking these actions on an unmanaged/personal device. I have created a blog about which option you could choose and how it works in detail.
4. Android Apps
This setup is good enough when working only with Android devices. You only need to make sure your users have the Company Portal app installed. You only need to install it; there is no need for any configuration, as it functions as a broker on Android devices.
But when you have users with IOS mobile devices (I bet you do) you will need some additional configuration.
5. IOS Apps
Like an Android phone, App protection will require a Broker app. For iOS devices, the MFA Authenticator app needs to be installed. After we make sure all our iOS users have that app installed, we first need to make sure all the Applications that need the Managed App Protection policies are added to Intune. As mentioned earlier, we need to define an App Configuration Policy for each app, and how could we do this without any apps?
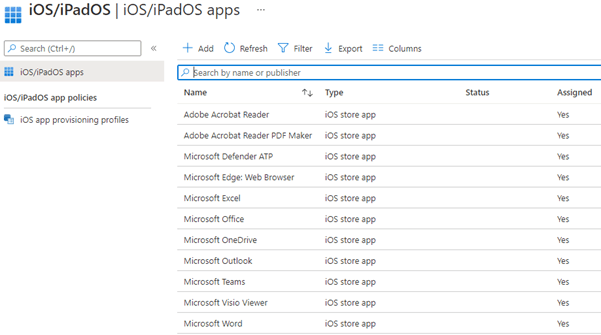
If you read my blogs often, you will probably know the whole setup can be scripted. When you need to do this manually, it will take some time so why not deploy it with PowerShell:
https://call4cloud.nl/wp-content/uploads/2021/03/IOS.zip
6. App Configuration
Now we have all the required Apps installed on the devices we still need to push an additional App Configuration, to make sure the IntuneMAMUPN is configured for each application. Please note: some apps do not support this config. Please visit this Microsoft Doc to check out all the Applications that do support it!
Supported Microsoft Intune apps | Microsoft Docs
You will need to configure the IntuneMAMUPN for each app because this value is required for devices managed by Intune to identify the enrolled user account. This is very important because you really want to make sure the protected app has the correct app protection policy applied!
Let’s create a new Managed Device App Configuration Policy and select the Outlook app. Again, you will need to create an App configuration with the IntuneMAMUPN for each app. To do so, select “Managed Devices” when adding a new App Configuration Policy.
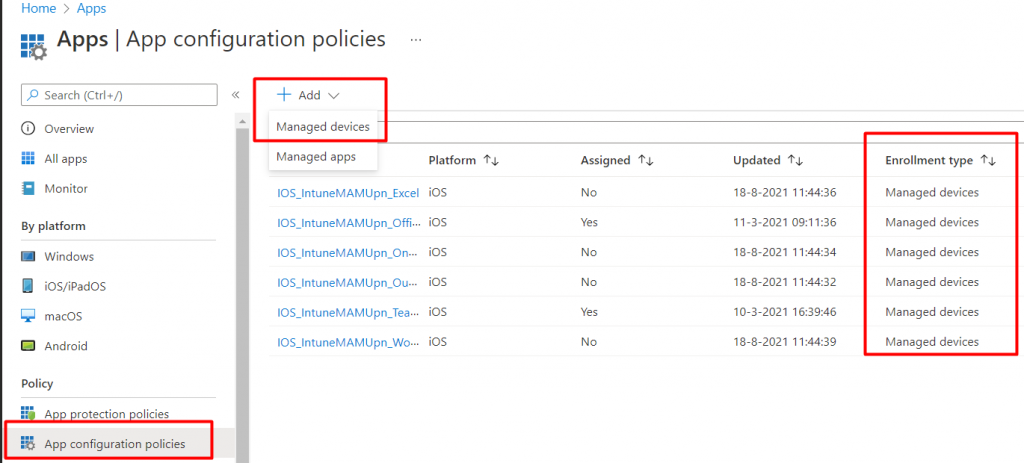
After selecting the proper App Configuration, it’s time to select IOS/IPadOS and select the “Targeted App”. In this example, I will select Microsoft Outlook.
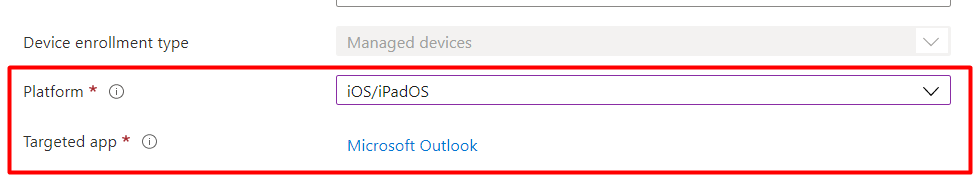
The possibility to add the required “IntuneMAMUPN” key can be found under “Additional Configuration”. Please beware the App configuration keys are case sensitive. Use the proper casing to ensure the configuration takes effect.
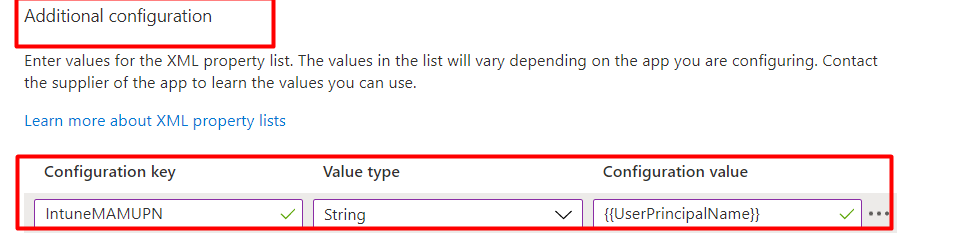
And a quick summary on how and where to configure the IntuneMAMUPN keuy
| Policy Type | Policy Selection | Policy location | Application Name | Configuration Key | Value Type | Configuration Value |
| App Configuration | Managed Devices | Microsoft Intue>Client Apps>App Configuration | Outlook | IntuneMAMUPN | String | {{UserPrincipalName}} |
7. Deploying them With PowerShell
Of course, you can do this all manually for each IOS Managed app, but why not automate the deployment of app configuration policies? As always, you can automate it with PowerShell and Graph. Take a look at my Github Page if you want to know how
Enrollment/DU at main · Call4cloud/Enrollment · GitHub
8. Results
After a while, and I mean really a while (could take up to 8 hours? Read this blog below), it will start working. I have created a blog on how to troubleshoot App Protection policies. Please read if you want to more about troubleshooting those app protection policies.
https://call4cloud.nl/2021/01/the-sum-of-all-app-protection-policies
I also showed you how to monitor/troubleshoot the app protection policies in the link above. So, let’s examine which apps understood the IntuneMAMUPN configuration.
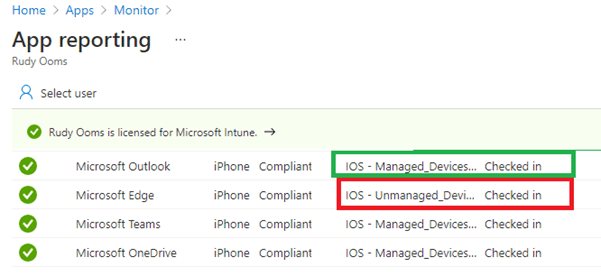
You can check if the Microsoft Edge app configuration was applied successfully by looking at it.

As shown above, it tells us it’s “Not Applicable.” I guess Edge does not respond to the configuration policy, but Teams/Onedrive and Outlook did.
Please Note: If the app assignment was configured as available instead of required. You will need to reinstall the already installed app from the Company Portal.
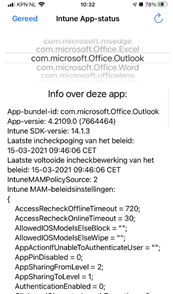
When you are at the customer and you want to determine which App Protection policies were applied, you could do so by opening edge and type: about:intunehelp. It will give you a brief summary of all the Protection Policies applied to a specific app!
Conclusion:
When securing your Office 365 data, you will need to find the golden middle; otherwise, lines will be drawn in the sand. On your left, there is data to protect, and on your right side, there are users who need to get their jobs done. You really need to let the end-users understand why it’s important.



For Step 6, I’m pretty sure the IntuneMAMUPN stuff is only needed for MDM, so “Managed Devices” instead of “Managed Apps”. In Managed Apps, you will find there’s no way to add that config key.
Totally true… After migrating my website it looks like somehow some old versions of mine blogs were migrated… Just uploaded the right version in where I am referring to the Managed Devices
Hello good sir! Great article, very informative. When you state “After a while and I mean really a while, it will start working” – do you have an estimate on how long?
Hi thanx!!.. I am explaining that part in the blog: https://call4cloud.nl/2021/01/the-sum-of-all-app-protection-policies/ I mentioned at the end
In section 5, referring to iOS apps – how does the deployment of VPP apps play info this scenario? Also, what if the user has downloaded the apps and they are not deployed from the management console?
Thank you so much for this post.
I’m having a strange issue one iOS devices when enable the app protection policy.
As soon as app protection policy is enabled, the Settings native app on iOS start to ask for the Microsoft account password. When i try to reenter the password, says that the Apple Internet Accounts enterprise application (default on on Azure, didn’t create anything) is not compliant with app protection policy.
Did you have any issue of this kind ? Microsoft support don’t have a clue about this after hours and hours of calls and troubleshooting.
Thank you so much
Hi… So you are saying that when an app protection policy was applied the settings app ask for a Microsoft account password?(which apps did you target? all or some specific ones?)
Hi, just Microsoft Edge. But for some reason as soon as you enable the app protection policy on Conditional Access, the Settings app start to ask for a password and when you try to enter the password, we got an error for Apple Internet Accounts.
Did you have any idea of why ? Or did you get any issue like this before ?
Thank you so much
Rudy I set this up as described but it didn’t work for me. My app protection policy disables app pins but I keep getting prompted for it on fully managed iPads. Are there any situations where this wouldn’t work ?
Also it seems it takes quite a long time fro app config policies to apply. how long in your experience ?
Andy Jones
Is there any option to only apply app protection policy on unmaged devices?
You could configure app protection for android and ios and only target Unmanaged or Managed devices in the Device types section… if that is what you are referring to
Thanks so much for this. I am in the process of setting up InTune for our iOS devices and was going crazy trying to get Outlook and Edge config settings pushed out.
hey I am trying to configure some app protection policy only for unmanaged device I don’t want to touch the managed devices, how can I configure that? (only for iOS)
Microsoft removed device selection dropdown while creating protection policies so now how can I distinguish between managed and unmanaged iOS devices in Intune?
any help will be appreciated
I am trying to do the same thing and the device filters will not work for me. I can see in app configuration that the intunemamupn config has been applied to my test group users but Managed App filter is still not populating managed devices.
Did you get this solved. Im in the same predicament. Filters are in place and In IntuneMAMUPN configuration profile, yet the user is enrolled with the unmanaged policy.
Thank you for this blog and this article in particular.
is this page still relevant in 2024 despite the small visual difference in intune?
how do you specify json to imprt with DU4b_AppConfigurationPolicy_ImportFromJSON.ps1 ? When I run the script, it say “no json specified”
Thank you