This blog will be about why only securing your Mobile apps and desktop clients on IOS and Android devices will leave some holes in your security!
In one of my last blogs, I showed you how to set up App protection policies on unmanaged and managed devices.
https://call4cloud.nl/2021/03/the-chronicles-of-mam
After some feedback, I realized I did not show the conditions, which client apps should be selected. When you are configuring Conditional Access there are some best practices. Two of them are definitely proper naming and making sure you split some rules.
When you decide to split some rules, you will notice troubleshooting will be easier and when you need to exclude a user you can only target the Browser app. Not to forget the most important reason why you need to split some rules: Require all OR one of the selected controls, when using teams.
Take a look at my blog about this topic:
Call4Cloud requiring Approved Apps or an App Protection Policy
It’s very important to create an additional CA rule to ensure users cannot logon to portal.office.com with Google Chrome or Safari on their unmanaged devices.
The only thing you need to make sure, you select:
*Office 365 cloud app
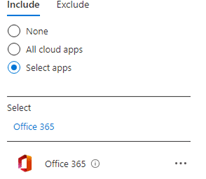
*Device Platform
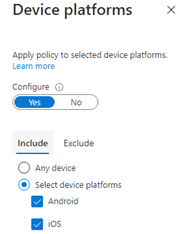
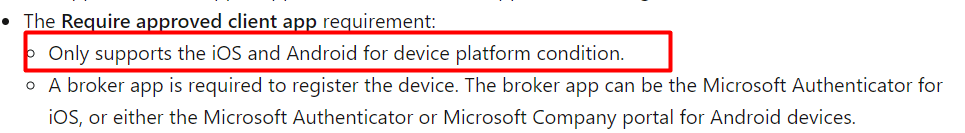
*Please make sure you only select Android and IOS as the Require Approved app is only supported on mobile devices.
*Client apps
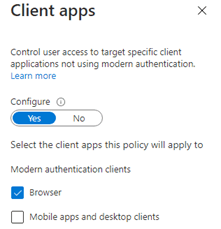
As shown above, with this rule, I only selected the Browser. Make sure you also have a CA rule where you select the Mobile apps and desktop clients.
*Grant
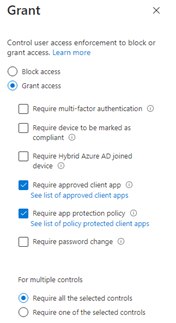
Unlike the CA policy for mobile apps and desktop clients, I selected Require All of the selected controls this time.
Let’s test it. When you make sure users can bring their own device with or without enrollment, you will have managed and unmanaged app protection policies. It’s funny to see that when you test it out on your Android personal profile instead of your work profile, you will notice you will be prompted to use Edge.
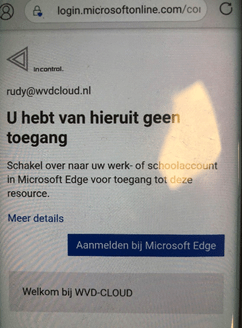
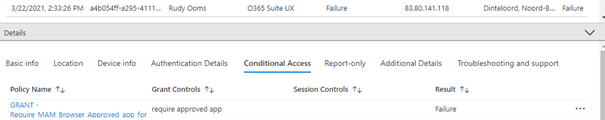
When you switch over to Microsoft Edge, Microsoft Edge will tell you to install the company portal first (as broker). After you install the company portal, the unmanaged app protection policy will kick in.
You could monitor this behaviour in the app protection monitor. In this App protection monitor possibility, you will notice there are 2 policies for the same device.
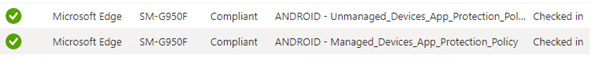
Conclusion:
You will need to pay attention when configuring Conditional Access, you are not leaving any holes inside your wall of security.


Hi,
How do you differentiate between managed and unmanaged devices (mobile devices)?
Do you use a dynamic device group and base the CA on those groups?
I would like to know you set this up so that managed mobile devices get other policies then the unmanaged ones.