This blog will be about a small but very useful change in how we troubleshoot Device Health Attestation issues. If you’ve encountered Device Compliance issues when using “Require BitLocker” or “Require Secure Boot” in a compliance policy, you know how frustrating it can be.
The new Tpm-PreAttestationHealthCheck task now drops a JSON file with all the info you need—TPM state, EK cert, Secure Boot, and more. Let’s take a look at the inner workings of that scheduled task is
1. Introduction
When configuring Compliance policies, it is always smart to require Bitlocker and Secure boot on the device. You can do so by configuring the corresponding Windows Health Attestation Service evaluation rules.
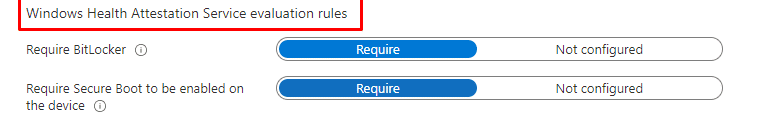
Once the compliance policies are delivered to your device and it has undergone a reboot to communicate the latest PCR values (in which Bitlocker was enabled), it should become compliant (eventually).
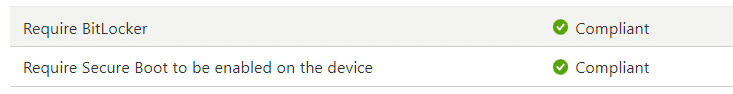
Unfortunately, there are some scenarios in which this doesn’t happen, and we end up with a non-compliant device, and with it, it could lose access to the data stored in Microsoft 365. Some time ago, I wrote a dedicated blog in which some devices didn’t come compliant because they could not retrieve the device health certificate. (DHA-Encrypted-Data)
Health Attestation Certificate | Bitlocker | Secure Boot (call4cloud.nl)
In that blog, I showed you how you could troubleshoot such kinds of issues. While working on a new (with the same error) health attestation issue with Pluton devices, I stumbled upon a new task scheduled on my insider preview VM. (Now available in 24h2)

This task’s name is Tpm-PreAttestationHealthCheck. Based on its name, it seems to perform pre-attestation health checks to ensure everything is good to go before we start looking at this new scheduled task, a quick Health Attestation CSP Refresher.
2. Health Attestation CSP.
If we want to know more about this task, Tpm-PreAttestationHealthCheck, we first need to refresh our knowledge about the Health Attestation CSP. To do so, you could take a look at this blog:
Device Health Attestation Flow | DHA | TPM | PCR | AIK (call4cloud.nl)
Or start reading the summary below.
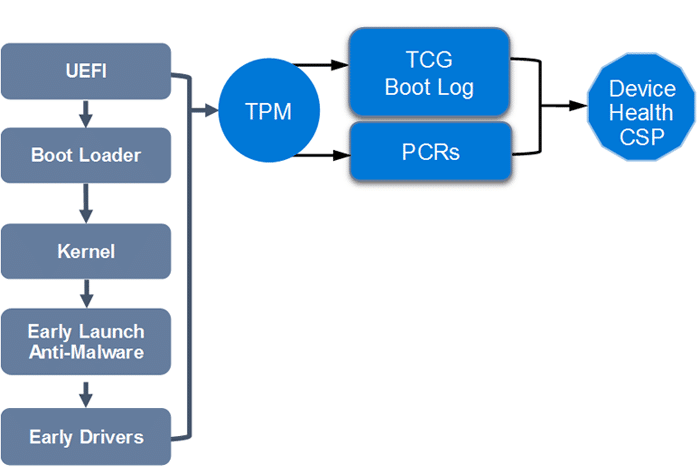
When we take a look at some of the core functions of the Windows Health Attestation CSP, we will notice that this task is responsible for
- Collecting data to verify a device’s health status.
- Sending this data to the Health Attestation Service.
- Managing the Health Attestation Certificate received from the Health Attestation Service.
- Forwarding the Health Attestation Certificate and related runtime information to MDM servers for verification.
- During health attestation sessions, transmit TCG logs and PCR values measured during boot to the Health Attestation Service via a secure channel.
- When an MDM server confirms a device’s attestation with the Health Attestation Service, it receives information about how it booted without rebooting between attestation and validation.
So, it’s safe to say that the Windows Health Attestation Service evaluates health data, generates encrypted health blobs, or produces reports for MDM servers. It verifies TPM attestation and log validity through several steps:
- Checking reports are signed by trustworthy AIKs.((Attestation Identity Key))
- Validating the signature over PCR values.
- Matching logs with PCR values.
- Examining logs for known or valid security configurations.
Now our Health Attestation CSP knowledge is a bit refreshed, let’s move on to the TpmPreAttestationHealthCheck scheduled task that arrived on our device
3. Tpm-PreAttestationHealthCheck
The latest insider preview Windows build (24h2) created a new task inside the TPM scheduled task folder.

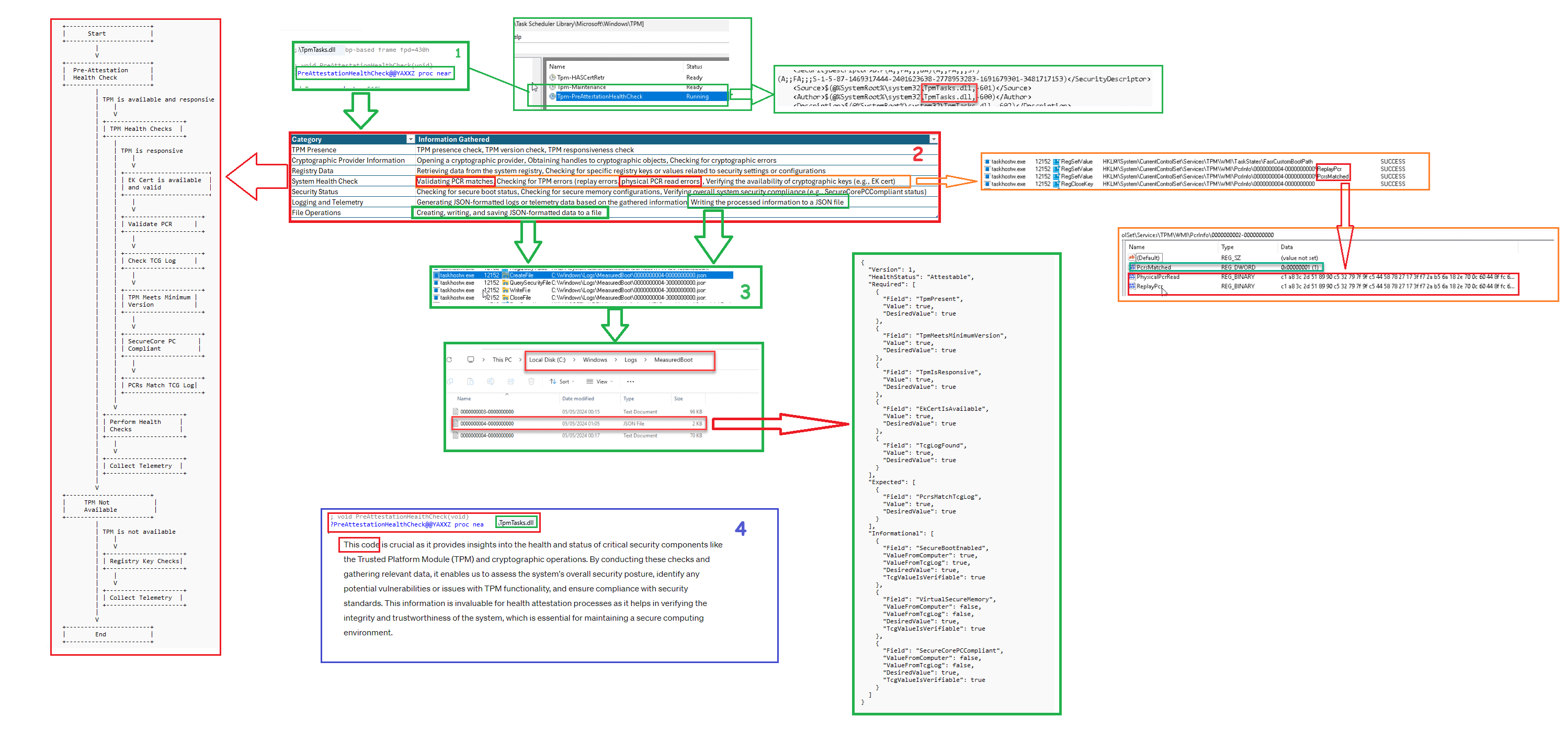
This task, Tpm-PreAttestationHealthCheck, seems responsible for performing some health checks. This task also used the tpmtask.dll to carry out its work.
That makes it way easier! Why? I can open that DLL file and start looking at the function in pseudocode:PreAttestationHealthCheck

Once I opened PreAttestationHealthCheck, I started reading the code. After spending some time on it, it was clear it was trying to gather all sorts of information. From there on, I first started making a summary of all the pieces of information it checks
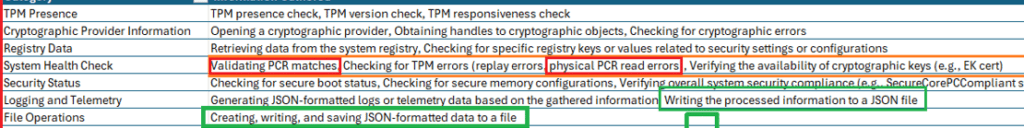
It was pretty clear that I stumbled upon 2 new things. I should start adding to my TPM attestation tool . This attestation health check verifies whether the PCRs match and logs the results to the TPM\WMI registry. When we look at the pseudocode, we indeed notice the same thing!
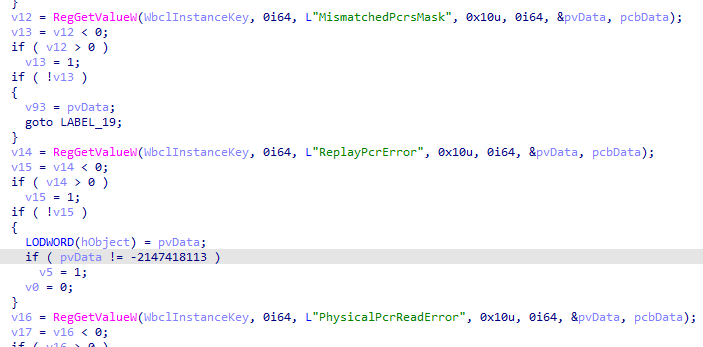
If we open the TPM\WMI registry node, we will spot the PCRInfo in it!!
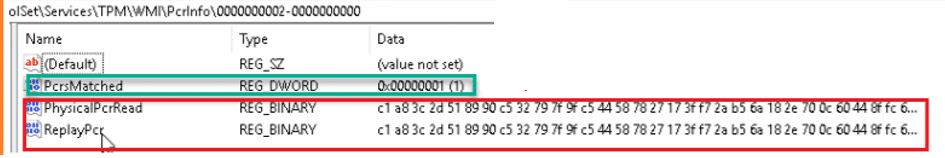
That’s a good health check!! I can use that one! From there on, I noticed something else which could also be very useful when troubleshooting attestation issues.
All the information this pre-attestation health checks gather is logged and exported to a JSON File. This JSON can be found in the c:\windows\logs\measuredboot folder
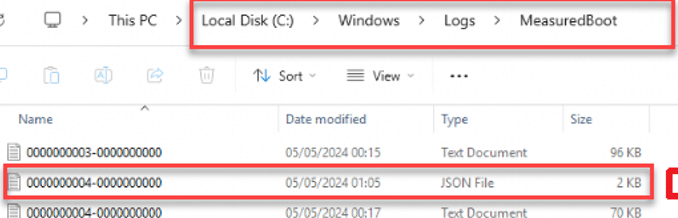
If we open that nice JSON, we spot all the checks this new Tpm-PreAttestationHealthCheck scheduled task performs! The JSON is divided into three categories. Checks that are Required, Expected and Informational
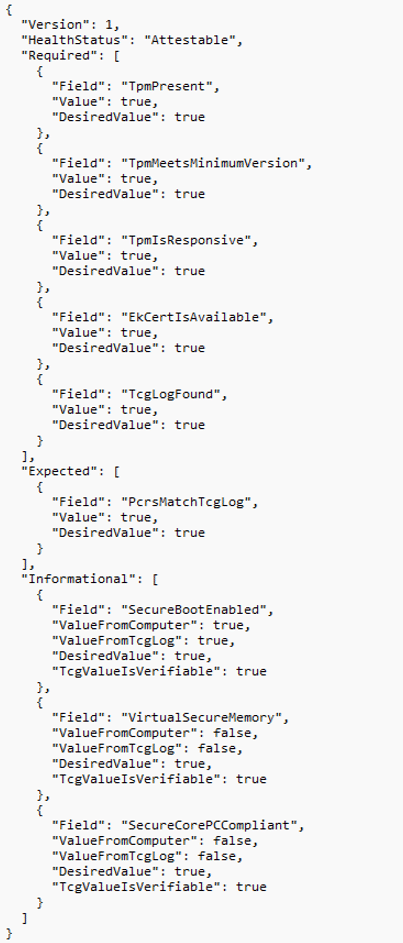
- TpmPresent
- TpmMeetsminimumversion
- TpmisResponsive
- EkCertIsAvailable
- TcgLogFound
- PcrtsMatchTcgLog
- Securebootenabled
I guess querying this JSON when you have issues with Health Attestation is an excellent thing to do!.
4. The Flow
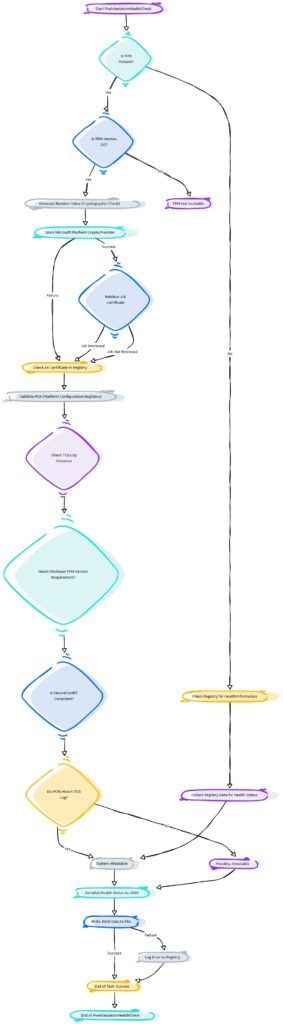
As always, there is a weird and maybe funny mspaint flow with all strings attached.
But I am also improving my flows… I start with Paint and end up with a Mermaid flow. Which one do you prefer?
Conclusion
This new scheduled task, called Tpm-PreAttestationHealthCheck, will undoubtedly provide more insights into what goes wrong when health attestation fails. So, if you have attestation issues, check out this JSON first! (afterward, you can contact me… and pass me that JSON)



it should become compliant (eventually).
Unfortunately, the eventually is why we have not enabled bit locker compliance, except for the ZTNA VPN. “Eventually” for a new employee means being locked out of the main work platform