This blog will show you something you need to be aware of when you purchase the Intune Suite and use the Cisco DUO desktop app. When activating the Intune Suite license, you could get yourself into some trouble if you don’t know what is happening on the service side and on your devices!
1. Introduction
I noticed a question pop up in the MM CCP Channel some time ago. The OP was asking why the Autopilot Diagnostics Established Correlations registry key mentioned the wrong EntDMID. The EntDMID is your unique device ID. This Device ID in the Autopilot Diagnostics registry location should correspond to the Intune Device ID.
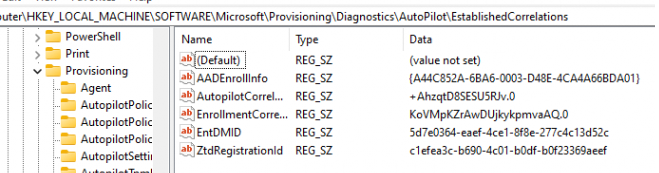
The Op mentioned that this EntDMID didn’t match the Intune Device ID, which shouldn’t be a problem in a regular situation, even when it’s a bit weird.
But if you are using Cisco DUO, you are up for a challenge. Let me tell you why! Once the DUO Desktop App is installed on your device, it will use the device its unique machine identifier to correspond with the service.
This unique machine identifier is in fact the EntDMID. Cisco DUO expects this EntdMID to be present at the \Provisioning\Diagnostics\Autopilot\EstablishedCorrelations
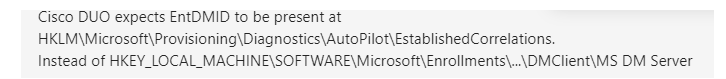
If this registry key contains the wrong EntDMID, the DUO Desktop app will report an invalid Intune Device ID. Which is still nothing to worry about, right?
2. Trusted Endpoint
First, let me show you this picture to clarify what mess we could get into when the wrong EntDMID is being used.
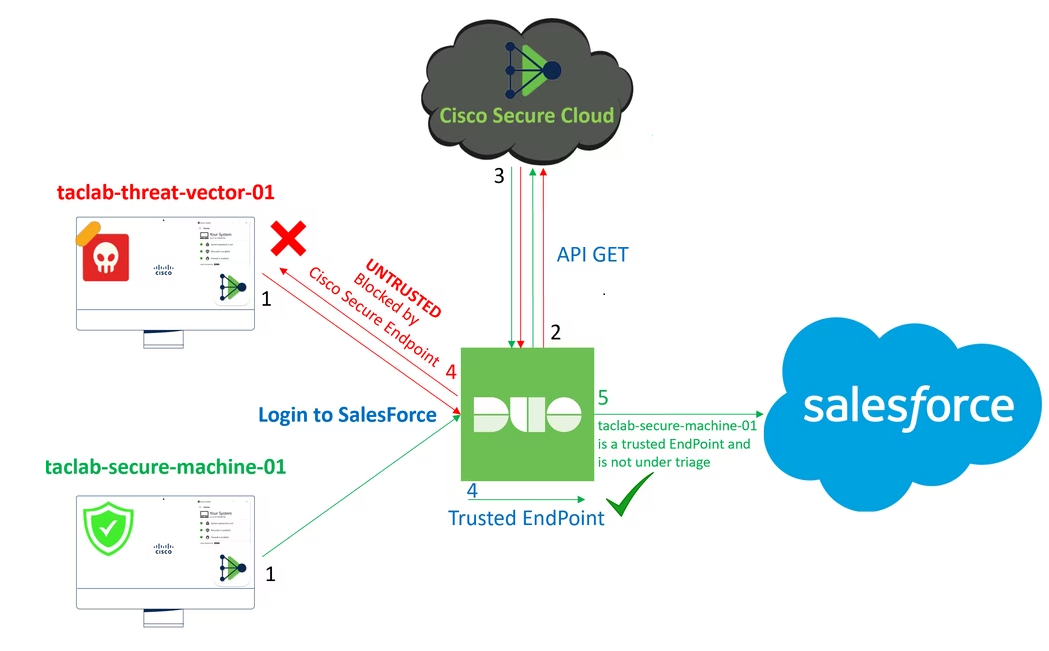
As shown above, Duo’s Trusted Endpoints feature enhances the security of your sensitive applications by allowing access to Duo-protected services only from recognized and trusted devices. Guess what happens when the device passes the wrong EntDMID

The device will end up NOT being trusted anymore, or you could get a lot of unexpected MFA prompts! If this happens on all of your devices, that could be a big shitstorm, right? Allow me to elaborate on how the EntdMID in the Diagnostics key is typically configured during the enrollment process with Autopilot.
3. EntDMID
If you are using Windows Autopilot to enroll your devices, as shown below, a lot will happen in the background without you probably noticing it
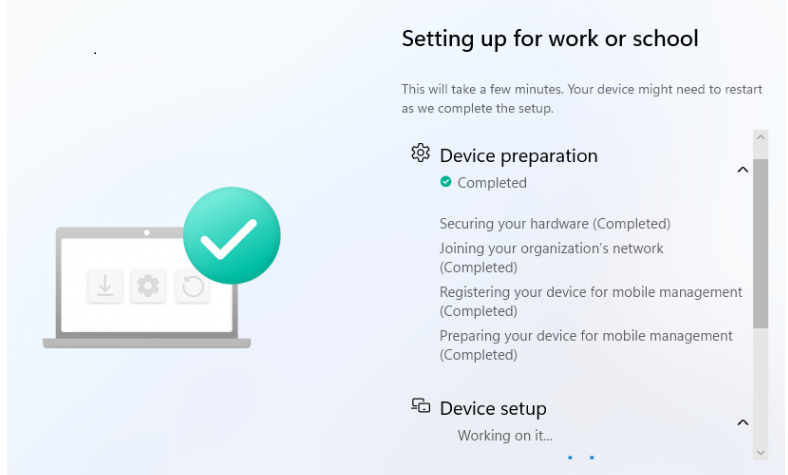
Once the device is enrolled, many registry keys will be configured, one of which is Autopilot Diagnostics. This key contains the Autopilot Correlation Data.
This correlation vector references events and the generated logs for diagnostic purposes.
This diagnostic data will be logged and stored by a particular function in the windows.management.service.dll
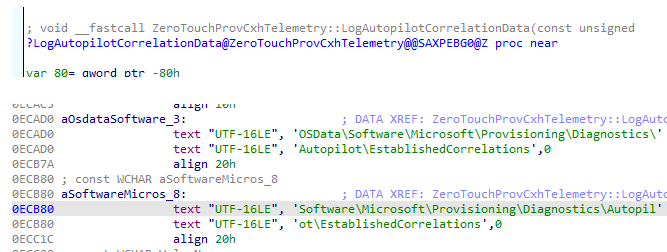
If the device is getting enrolled, it will also log the EntdMID that is used during the Autopilot enrollment itself in the same registry location.
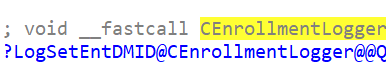
We will spot the same behavior when we use Procmon to track it. As shown below, during Autopilot enrollment, the EntdMID will be logged in using the corresponding diagnostics registry key.
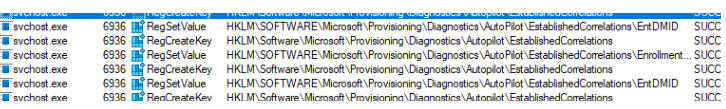
If we take a look at the registry key, we will indeed spot the EntDMID
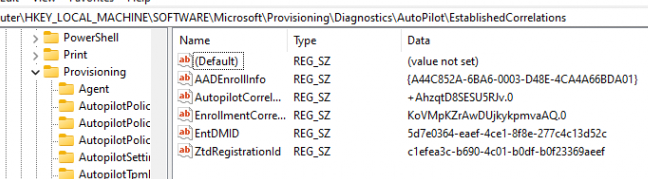
If we take a look at the Intune Enrollment registry key, we will notice that the EntDMID indeed matches the one in the Autopilot Diagnostics key

That’s weird, right? It matches the Intune device ID, so what happened on the devices from the OP?
4. Activating the Intune Suite
After an offline conversation with the OP, it became very clear when it started happening. The OP mentioned that he activated the Intune Suite license yesterday but didn’t configure any policy whatsoever.
Again… when we activate that license, some magic happens in the Microsoft background. When we activate the Intune Suite license, we also get licensed for EPM. When we are getting licensed to use EPM, the tenant will be onboarded to the Microsoft Managed Platform
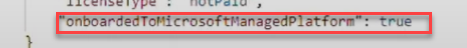
When our tenant is onboarded to MMP-C, a push command to initiate the “linked enrollment” will be automatically sent to all of your devices.
The whole flow and story can be read in this blog
MMP-C | Microsoft Management Platform Cloud (call4cloud.nl)
The bottom line is that our device will get a linked/dual enrollment automatically.
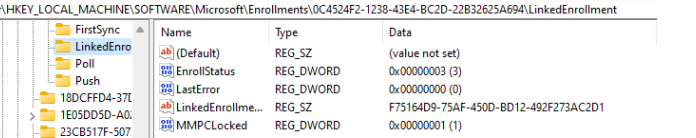
This new enrollment will talk with Microsoft’s MMP-C service to retrieve the EPM Policies. Just like the Intune enrollment, the MMP-C enrollment will also use the EntDMID to verify the device.
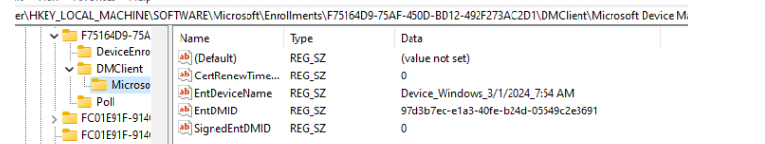
It’s all good, right? Except for one little thing: the same function logs the EntDMID key when the new enrollment kicks in.

If we refresh the Autopilot Establishedcorrelations registry key, we will notice some weird behavior.

As shown above, Autopilot Diagnostics no longer mentions the Intune Device ID, but the MMP-C Device ID. The moment the MMP-C enrollment kicked in; our device became untrusted by DUO! When our device became untrusted by DUO, all services that required a trusted endpoint broke down.
5. Fix
Now that we know what will change when you “only” activate the Intune Suite license, we also need to consider how to fix this.
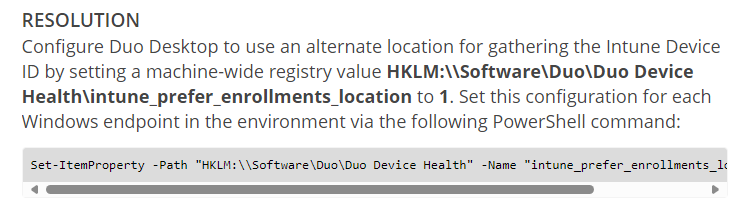
As shown above, DUO is mentioning the fix on its website! Isn’t that easy? We could just configure the alternate enrollment location where DUO needs to find the proper device ID. With this fix, DUO will start looking at the proper Intune device ID and become a trustworthy endpoint again.
Conclusion
Sometimes, activating a license can have a big impact on your organization even without you knowing it. This time, the Intune Suite automatically triggered all devices’ linked enrollment to MMP-C!
Almost if Microsoft is preparing for something….